A Moscow court this week convicted and sentenced seven hackers for breaking into countless online bank accounts — including “Paunch,” the nickname used by the author of the infamous “Blackhole” exploit kit. Once an extremely popular crimeware-as-a-service offering, Blackhole was for several years responsible for a large percentage of malware infections and stolen banking credentials, and likely contributed to tens of millions of dollars stolen from small to mid-sized businesses over several years.

Fedotov, the convicted creator of the Blackhole Exploit Kit, stands in front of his Porche Cayenne in an undated photo.
According to Russia’s ITAR-TASS news network, Dmitry “Paunch” Fedotov was sentenced on April 12 to seven years in a Russian penal colony. In October 2013, the then 27-year-old Fedotov was arrested along with an entire team of other cybercriminals who worked to sell, develop and profit from Blackhole.
According to Russian security firm Group-IB, Paunch had more than 1,000 customers and was earning $50,000 per month from his illegal activity. The image at right shows Paunch standing in front of his personal car, a Porsche Cayenne.
First spotted in 2010, BlackHole is commercial crimeware designed to be stitched into hacked or malicious sites and exploit a variety of Web-browser vulnerabilities for the purposes of installing malware of the customer’s choosing.
The price of renting the kit ran from $500 to $700 each month. For an extra $50 a month, Paunch also rented customers “crypting” services; cryptors are designed to obfuscate malicious software so that it remains undetectable by antivirus software.
Paunch worked with several other cybercriminals to purchase new exploits and security vulnerabilities that could be rolled into Blackhole and help increase the success of the software. He eventually sought to buy the exploits from other cybercrooks directly to fund a pricier ($10,000/month) and more exclusive exploit pack called “Cool Exploit Kit.”
As documented on this blog in January 2013 (see Crimeware Author Funds Exploit Buying Spree), Paunch contracted with a third-party exploit broker who announced that he had a $100,000 budget for buying new, previously undocumented “zero-day” vulnerabilities.
Not long after that story, the individual with whom Paunch worked to purchase those exclusive exploits — a miscreant who uses the nickname “J.P. Morgan” — posted a message to the Darkode[dot]com crime forum, stating that he was doubling his exploit-buying budget to $200,000.
In October 2013, shortly after news of Paunch’s arrest leaked to the media, J.P. Morgan posted to Darkode again, this time more than doubling his previous budget — to $450,000.
“Dear ladies and gentlemen! In light of recent events, we look to build a new exploit kit framework. We have budgeted $450,000 to buy vulnerabilities of a browser and its plugins, which will be used only by us afterwards! ”
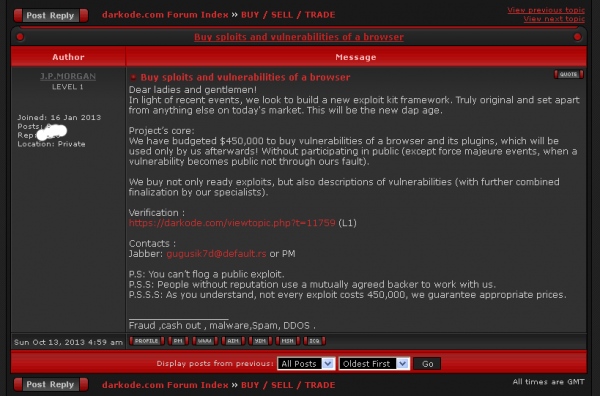
J.P. Morgan alludes to his former partner’s arrest, and ups his monthly exploit buying budget to $450,000.
The Russian Interior Ministry (MVD) estimates that Paunch and his gang earned more than 70 million rubles, or roughly USD $2.3 million. But this estimate is misleading because Blackhole was used as a means to perpetrate a vast array of cybercrimes. I would argue that Blackhole was perhaps the most important driving force behind an explosion of cyber fraud over the past three years. A majority of Paunch’s customers were using the kit to grow botnets powered by Zeus and Citadel, banking Trojans that are typically used in cyberheists targeting consumers and small businesses.
For more about Paunch, check out Who is Paunch?, a profile I ran in 2013 shortly after Fedotov’s arrest that examines some of the clues that connected his online criminal persona with his personal social networking profiles.
Update, 1:42: Corrected headline.




As my grandpa used to say, “Couldn’t happen to a nicer guy!” And in Russia, of all places!!
So what changed that they decided to sacrifice him and leave a hundred others operating in the open?
Paunch helped a lot of different crime gangs. Some of those guys were Russians targeting Russian banks and Russian account holders. The old “don’t poop where you eat” golden rule I guess still applied in his case.
Was wondering about that.
It would have been a pleasant surprise if Russian courts had taken action on account of crimes against non-Russians.
What do you bet his job in the penal colony will be to spread malware to explicitly non-Russian targets?
Probably forgot to pay bribes the right official, or maybe he didn’t pay enough!
Spot on.
By “penal colony” they mean “working for the Russian government’s cyber espionage service.”
Not bloody likely.
QUITE bloody likely.
Don’t think for a second we wouldn’t do the same thing.
Enjoy Siberia.
Does Black Hole have any relation to BlackPOS?
No. Completely unrelated.
Honestly, I couldn’t care less about Dmitry “Paunch” Fedotov.
My interest is more about the software. It sounds to me like these things can be filtered out easy enough with the host file or even maybe noscript. I also wonder about the websites that end up hosting this mans code. The way I see it, the people running these websites either did not know (because of carelessness or neglect) or they did know this was going on (letting it happen out of malice or financial gain).
Either way, these are websites that should be avoided and filtered out (no matter what they are). This is where end user responsibility comes in. This is also where a competent (on-site) IT department is needed for business networks. The problem is though, that it’s all being shifted to the cloud and given to someone else to manage……which is exactly how Mr. Fedotov is so capable of doing what he did in the first place.
Lock your footlocker!
You are correct, to a certain extent, when it comes to blocking plugin-based exploits, and no script plus disabling Java/flash/etc.
That said, it’d behoove you to understand the economics and dynamics a bit. Low-hanging fruit is often favourable to exploit (at all points of the exploit chain), however, especially when it comes to the user side of the equation where persistent installs are often considered best (especially as traffic and installs are often sold on). At a minimum it buys those who commit bank frausd time to cash out, and for those who sell or do click fraud pure income. Similarly, ransom ware often isn’t the first he of a kit-owned machine.
Not sure you realize a lot of sites load third party content. That and using off the shelf software with known or unknown exploits often garners most of the upper end exploited sites. Currently a lot of kits are using bro wser and flash exploits
Sorry. Spell check and a mobile device. As I was saying, it is rather hard to completely exploit-proof oneself but not impossible to exploit*kit*- proof oneself. This is because almost without exception there are no 0days used and when they are (eg early 2011 w/blackhole, or as with cool, they do not live long and get patched quickly. Zero days generally aren’t wasted this way. Which is to say if you use Firefox and let it auto update and you change the less privaxy-fruendly hidden options you are probably safe, with Java and flash off and no script with a self-curated whitelist … but not totally. Recall the third party issue. Get adblockplus or similar and your risks decrease on this front. Make sure not to block only the ads.
All this said html5 , fonts, browsers themselves are all open season and various things DO take TIME to patch. Usually a kit that’s *good* by criminal standards will push an exploit out before a patch. One thing Paunch did via his subscription model was precisely this, and it is one reason he was so successful – and other kits have come to borrow the model.
Btw bear in mind that in general absent 0 or 1-day type exploits (which is to say unknown or known but no patch avail yet) the exploit success rate for these sorts if kits hovers around 8-18%. 10-12% is/was fairly common. Even when the unpatched stuff was used 23-53 was about as good as it got — which is to say they are dangerous but even at the worst of times not everyone got bit even when they were attempted at. Most of the ones that did were, as usual, IE on Windows.
Anyway things have changed a bit since Paunch was involuntarily retired. You should ask Mr. Krebs to write about that.
FYI the avg or even above avg user will fail with no script or get frustrated with it. Advocating it in an IT dept for company wide roll out is only good til you realize people will just click whatever they need to (as in allow all globally) to watch stupid videos and read crap they should not at work anyway (like gossip sites).
And that’s how people get owned. It only takes one user.
ublock origin is a godsend for endpoint protection. It will please users with decluttered sites, and protect them from the most common malware vector at the same time.
Indeed. I rolled out Flashblock to a couple individuals who were prone to not only getting infected but having a massive fit when they did. Explained that it was there for their protection, all they had to do was click on a flash object to get it to work which is trivially easy to do for videos and the like since they’re the huge thing in the center of the screen.
I revisited them a couple weeks later and they had enabled all flash objects on all websites because some inane cat video on some random wouldn’t play. On a workplace system. Yeah, I don’t understand how they still have a job either.
So far my luck with adblock is better, but a few people spazzed out and blanket-enabled all ads because apparently they can’t do their jorb without ads, and the sky will fall this second if they have to learn something new – even if it will stop them from getting infected yet again, which not only stops them from getting ads, but also forces them change all their passwords – and they absolutely loathe doing that.
PS: I am one of the good guys, for the record.
I do understand and appreciate your views here.
As for 3rd party what-not:
I would not suggest noscript for company used really (more for home users). I don’t use it but it seems all the rage. But then, I don’t rely on IE either. I can say for sure that making use of the host file will block all kinds of things (including 3rd party ads and scripts). Moving that list into a server that replaces the router (which is a setup that would certainly help in a company setting) makes it so that every computer/device on the network receives the benefits. The only problem that this creates is that so many websites will move their CSS, various graphics, and other pieces of their site to these vary same places that I end up filtering out. The result is often a broken website. The thing is, it breaks because of what the website owners/management/IT dept. do with it, not because of what I do for self protection.
As for the economics of it all:
I have very little interest in the games played across corporate offices. Particularly when it comes to the crazyness of how things get budgeted. It’s all a necessary evil I guess but my head for numbers just wasn’t born for for all that. The way I see it, buying another company is an obvious “NO” when you can’t even afford new ladders for your technicians. But whatever.
I just think it is more efficient for a company to block websites like Facebook from anything on the network at the router level than to install monitoring software on every one of the 300 computers in the office. These machines are so much more powerful that they are being used to do. It’s a shame. I can’t justify writing up a new girl for deleting a very important file off the server when that file was never given proper permissions that would have prevented her from deleting it. I wonder if anyone has ever calculated how much time gets lost because of the 500 emails that result from one persons’ idiotic comment one the first email? There are so many things and yet the activities of people like Paunch gets so easily overlooked. It’s maddening how much utter waste goes on.
Alot of (read: most) sites nowadays load Co tent from third parties dynamically. Sometimes you’ll want some of that and sometimes not. A good example of dubious ness is cloudflare. But going at it from a blacklist perspective is like an AV approach: you only get what’s known, and often not til it is already too late.
There are ways around your ideas. I have seen them in action. I used to be more gungho on nids and ids myself. IMHO most businesses should be following a limited white listing approach. It won’t protect everything but it’d certainly improve productivity. That said stuff always gets through if someone wants it to enough. IMHO focusing on IP egress limitation should be the #1 concern for many businesses. Ditto preventing connectback mechanisms (eg block ports. Won’t stop http and udp tunneling but easy to implement and free to do).
Every company has different needs tho. Ac
Oops. Accounting and financial businesses especially have different tolerances than, say, education or healthcare or a place that handles no PII but maybe some IP. I really haven’t seen any solutions that can deal with a user that refuses to comply or a company (most of them) thats too open to letting the user make choices. Too many people have mobile data. Too many places allow users to use laptops they use at home. Things spread.
Two words: Network shares.
Sorry if my commenting is a bit pedantic. Its late and this device isn’t easy to post with :).
Not a viable solution. Great for the ultra paranoid or someone with great opsec and completely committed to being secure.
But, for typical web use, most people don’t have the patience to deal with it and it won’t be used. Not to mention, nothing protects you against a less cautious friend that you allowed to use your computer.
An unbreakable safe that keeps me from accessing my valuables isn’t that useful to me, despite the fact that it completely protects my valuables. Valuables are only useful if I can access them. And if I can, so can someone else.
What are you talking about?
i he got arrested,coz they touched russina own banks, reason to 2 flashhy, did he he legal business on the side to lounder money? i think no and thats the problem ,his face is not happy as we see he earn alot money but question isit worted? coz police can take from you that money so easily,- many many criminals in reallity had millions or even more,butthis money all configated,and the criminal after jail is left with nothing- thats reallity in this days and so on anywyas life works by kabalistic rules,its means nothign comes from nothign,and somebody always will pay price ,and it must be the humen been,as we know that materialistic reality can exist only if the soul is suffering, money is made if soul strugling,
So one can’t make money unless one is nihilistic and feels miserable? That’s a pretty depressing worldview.
BTW agree that Russian banks contributed but think he was going to get busted even if not. His stuff was too central to too many peoples businesses and I imagine the pressure on Russia was phenomenal.
Mr. Krebs – your banner ads still offer your book for pre-order? Maybe time to change that GIF? 🙂
http://krebsonsecurity.com/b-book/1.jpg
http://krebsonsecurity.com/b-book/1.jpg
Still no SSL btw?! :-/
Start SSL has SSL certs for free.
ssl for a blog imo is not as important as you are only reading / not giving out data.
*sigh* … enforcing https (TLS) would allow the user to verify the certificate for the site is issued to the site/site owner. Otherwise there are numerous (usually involving MitM) attacks to feed you content you DON’T want from an intercepted version of this site. Nevermind, continue browsing willy nilly, I hope you use FF + NoScript, etc.
In the “end” it does not matter. This crook is now off the streets – for now, but the damage is done, and will continue to be done as others fill his shoes.
Crooks in Russia haul in some massive cash. It does not mean they give some or all to the government, its a commodity that allows a country to still function.
Russia and China will continue to tap funds to stay afloat as long as the valve remains unguarded. Billions in losses seems to be child’s play for the US Government. I have wondered in the past, if these funds were not available to 3rd world countries, we’d probably hand it to them in some sort of UN fashion anyway.
Take down one crook and three eager ones are now willing to do the sane thing. Some better than the last others, with reckless abandon.
Prison system in Russia is lets say – have many holes in it which you can EXPLOIT- if you have the right amount of cash – Its the same business model – holes /money/exploit . Im sure he will be just fine .
Why not just cane and castrate cyber-crooks…that might get their attention. Or course all the bleeders would cry about the inhumanity of it. Desperate times require desperate measures.
They are all idiots.
What is the main rule?
The rule is – Do not work in the country where you live.
I just re-read the research on paunch and followed the link to the porsche forum, where he complained that his jackets zipper scratched the steering wheel. he must be really overweight! great research Brian! I guess he got busted first for screwing with russian banks and got a light sentence, now he got a better deal. 7 years? he will come out as воры в законе with the right tattos…
One of the more important things about this may be that legal penalties, across widely disparate criminal justice systems, are beginning to align. I present some evidence for this at http://fubarnorthwest.blogspot.com/2016/04/blackhole-crimeware-creator-gets-7-years.html.
My take is that a crime committed over a network is no longer a slap-on-the wrist affair, regarded as trivial in comparison to a physical crime, and this will eventually be a game-changer. Not soon, but legal systems should follow the times; attempting to lead offers too many opportunities for abuse.
You’re giving the US too much credit for parity. When/if he ever winds up in the grips of America, the sentencing will be more in the ~15-20 year range, probably. I’ve come to see the rule of thumb as ‘elsewhere, 1/4-1/3 the sentence’ (though sometimes the US pounds people with 10+x the sentence they’d get elsewhere), but it varies. I will grant that it is a bit higher than usual for Russia, though.
TIL you can ” … purchase new … security vulnerabilities”. This industry is truly innovative.