John Gilmore, an American entrepreneur and civil libertarian, once famously quipped that “the Internet interprets censorship as damage and routes around it.” This notion undoubtedly rings true for those who see national governments as the principal threats to free speech.
However, events of the past week have convinced me that one of the fastest-growing censorship threats on the Internet today comes not from nation-states, but from super-empowered individuals who have been quietly building extremely potent cyber weapons with transnational reach.
More than 20 years after Gilmore first coined that turn of phrase, his most notable quotable has effectively been inverted — “Censorship can in fact route around the Internet.” The Internet can’t route around censorship when the censorship is all-pervasive and armed with, for all practical purposes, near-infinite reach and capacity. I call this rather unwelcome and hostile development the “The Democratization of Censorship.”
Allow me to explain how I arrived at this unsettling conclusion. As many of you know, my site was taken offline for the better part of this week. The outage came in the wake of a historically large distributed denial-of-service (DDoS) attack which hurled so much junk traffic at Krebsonsecurity.com that my DDoS protection provider Akamai chose to unmoor my site from its protective harbor.
Let me be clear: I do not fault Akamai for their decision. I was a pro bono customer from the start, and Akamai and its sister company Prolexic have stood by me through countless attacks over the past four years. It just so happened that this last siege was nearly twice the size of the next-largest attack they had ever seen before. Once it became evident that the assault was beginning to cause problems for the company’s paying customers, they explained that the choice to let my site go was a business decision, pure and simple.
Nevertheless, Akamai rather abruptly informed me I had until 6 p.m. that very same day — roughly two hours later — to make arrangements for migrating off their network. My main concern at the time was making sure my hosting provider wasn’t going to bear the brunt of the attack when the shields fell. To ensure that absolutely would not happen, I asked Akamai to redirect my site to 127.0.0.1 — effectively relegating all traffic destined for KrebsOnSecurity.com into a giant black hole.
Today, I am happy to report that the site is back up — this time under Project Shield, a free program run by Google to help protect journalists from online censorship. And make no mistake, DDoS attacks — particularly those the size of the assault that hit my site this week — are uniquely effective weapons for stomping on free speech, for reasons I’ll explore in this post.
Google’s Project Shield is now protecting KrebsOnSecurity.com
Why do I speak of DDoS attacks as a form of censorship? Quite simply because the economics of mitigating large-scale DDoS attacks do not bode well for protecting the individual user, to say nothing of independent journalists.
In an interview with The Boston Globe, Akamai executives said the attack — if sustained — likely would have cost the company millions of dollars. In the hours and days following my site going offline, I spoke with multiple DDoS mitigation firms. One offered to host KrebsOnSecurity for two weeks at no charge, but after that they said the same kind of protection I had under Akamai would cost between $150,000 and $200,000 per year.
Ask yourself how many independent journalists could possibly afford that kind of protection money? A number of other providers offered to help, but it was clear that they did not have the muscle to be able to withstand such massive attacks.
I’ve been toying with the idea of forming a 501(c)3 non-profit organization — ‘The Center for the Defense of Internet Journalism’, if you will — to assist Internet journalists with obtaining the kind of protection they may need when they become the targets of attacks like the one that hit my site. Maybe a Kickstarter campaign, along with donations from well-known charitable organizations, could get the ball rolling. It’s food for thought.
CALIBRATING THE CANNONS
Earlier this month, noted cryptologist and security blogger Bruce Schneier penned an unusually alarmist column titled, “Someone Is Learning How to Take Down the Internet.” Citing unnamed sources, Schneier warned that there was strong evidence indicating that nation-state actors were actively and aggressively probing the Internet for weak spots that could allow them to bring the entire Web to a virtual standstill.
“Someone is extensively testing the core defensive capabilities of the companies that provide critical Internet services,” Schneier wrote. “Who would do this? It doesn’t seem like something an activist, criminal, or researcher would do. Profiling core infrastructure is common practice in espionage and intelligence gathering. It’s not normal for companies to do that.”
Schneier continued:
“Furthermore, the size and scale of these probes — and especially their persistence — points to state actors. It feels like a nation’s military cyber command trying to calibrate its weaponry in the case of cyberwar. It reminds me of the US’s Cold War program of flying high-altitude planes over the Soviet Union to force their air-defense systems to turn on, to map their capabilities.”
Whether Schneier’s sources were accurate in their assessment of the actors referenced in his blog post is unknown. But as my friend and mentor Roland Dobbins at Arbor Networks eloquently put it, “When it comes to DDoS attacks, nation-states are just another player.”
“Today’s reality is that DDoS attacks have become the Great Equalizer between private actors & nation-states,” Dobbins quipped.
UM…YOUR RERUNS OF ‘SEINFELD’ JUST ATTACKED ME
What exactly was it that generated the record-smashing DDoS of 620 Gbps against my site this week? Was it a space-based weapon of mass disruption built and tested by a rogue nation-state, or an arch villain like SPECTRE from the James Bond series of novels and films? If only the enemy here was that black-and-white.
No, as I reported in the last blog post before my site was unplugged, the enemy in this case was far less sexy. There is every indication that this attack was launched with the help of a botnet that has enslaved a large number of hacked so-called “Internet of Things,” (IoT) devices — mainly routers, IP cameras and digital video recorders (DVRs) that are exposed to the Internet and protected with weak or hard-coded passwords. Most of these devices are available for sale on retail store shelves for less than $100, or — in the case of routers — are shipped by ISPs to their customers.
Some readers on Twitter have asked why the attackers would have “burned” so many compromised systems with such an overwhelming force against my little site. After all, they reasoned, the attackers showed their hand in this assault, exposing the Internet addresses of a huge number of compromised devices that might otherwise be used for actual money-making cybercriminal activities, such as hosting malware or relaying spam. Surely, network providers would take that list of hacked devices and begin blocking them from launching attacks going forward, the thinking goes.
As KrebsOnSecurity reader Rob Wright commented on Twitter, “the DDoS attack on @briankrebs feels like testing the Death Star on the Millennium Falcon instead of Alderaan.” I replied that this maybe wasn’t the most apt analogy. The reality is that there are currently millions — if not tens of millions — of insecure or poorly secured IoT devices that are ripe for being enlisted in these attacks at any given time. And we’re adding millions more each year.
I suggested to Mr. Wright perhaps a better comparison was that ne’er-do-wells now have a virtually limitless supply of Stormtrooper clones that can be conscripted into an attack at a moment’s notice.

A scene from the 1977 movie Star Wars, in which the Death Star tests its firepower by blowing up a planet.
SHAMING THE SPOOFERS
The problem of DDoS conscripts goes well beyond the millions of IoT devices that are shipped insecure by default: Countless hosting providers and ISPs do nothing to prevent devices on their networks from being used by miscreants to “spoof” the source of DDoS attacks.
As I noted in a November 2015 story, The Lingering Mess from Default Insecurity, one basic step that many ISPs can but are not taking to blunt these attacks involves a network security standard that was developed and released more than a dozen years ago. Known as BCP38, its use prevents insecure resources on an ISPs network (hacked servers, computers, routers, DVRs, etc.) from being leveraged in such powerful denial-of-service attacks.
Using a technique called traffic amplification and reflection, the attacker can reflect his traffic from one or more third-party machines toward the intended target. In this type of assault, the attacker sends a message to a third party, while spoofing the Internet address of the victim. When the third party replies to the message, the reply is sent to the victim — and the reply is much larger than the original message, thereby amplifying the size of the attack.
BCP38 is designed to filter such spoofed traffic, so that it never even traverses the network of an ISP that’s adopted the anti-spoofing measures. However, there are non-trivial economic reasons that many ISPs fail to adopt this best practice. This blog post from the Internet Society does a good job of explaining why many ISPs ultimately decide not to implement BCP38.
Fortunately, there are efforts afoot to gather information about which networks and ISPs have neglected to filter out spoofed traffic leaving their networks. The idea is that by “naming and shaming” the providers who aren’t doing said filtering, the Internet community might pressure some of these actors into doing the right thing (or perhaps even offer preferential treatment to those providers who do conduct this basic network hygiene).
A research experiment by the Center for Applied Internet Data Analysis (CAIDA) called the “Spoofer Project” is slowly collecting this data, but it relies on users voluntarily running CAIDA’s software client to gather that intel. Unfortunately, a huge percentage of the networks that allow spoofing are hosting providers that offer extremely low-cost, virtual private servers (VPS). And these companies will never voluntarily run CAIDA’s spoof-testing tools.
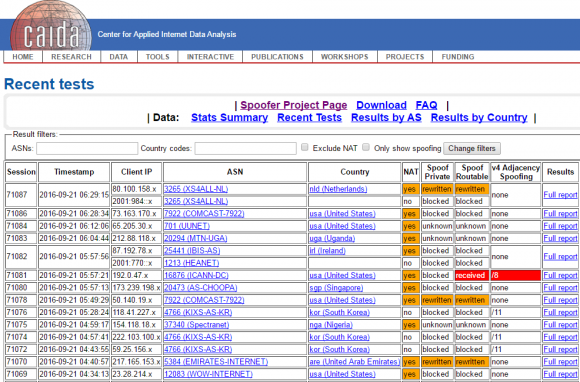
CAIDA’s Spoofer Project page.
As a result, the biggest offenders will continue to fly under the radar of public attention unless and until more pressure is applied by hardware and software makers, as well as ISPs that are doing the right thing.
How might we gain a more complete picture of which network providers aren’t blocking spoofed traffic — without relying solely on voluntary reporting? That would likely require a concerted effort by a coalition of major hardware makers, operating system manufacturers and cloud providers, including Amazon, Apple, Google, Microsoft and entities which maintain the major Web server products (Apache, Nginx, e.g.), as well as the major Linux and Unix operating systems.
The coalition could decide that they will unilaterally build such instrumentation into their products. At that point, it would become difficult for hosting providers or their myriad resellers to hide the fact that they’re allowing systems on their networks to be leveraged in large-scale DDoS attacks.
To address the threat from the mass-proliferation of hardware devices such as Internet routers, DVRs and IP cameras that ship with default-insecure settings, we probably need an industry security association, with published standards that all members adhere to and are audited against periodically.
The wholesalers and retailers of these devices might then be encouraged to shift their focus toward buying and promoting connected devices which have this industry security association seal of approval. Consumers also would need to be educated to look for that seal of approval. Something like Underwriters Laboratories (UL), but for the Internet, perhaps.
THE BLEAK VS. THE BRIGHT FUTURE
As much as I believe such efforts could help dramatically limit the firepower available to today’s attackers, I’m not holding my breath that such a coalition will materialize anytime soon. But it’s probably worth mentioning that there are several precedents for this type of cross-industry collaboration to fight global cyber threats.
In 2008, the United States Computer Emergency Readiness Team (CERT) announced that researcher Dan Kaminsky had discovered a fundamental flaw in DNS that could allow anyone to intercept and manipulate most Internet-based communications, including email and e-commerce applications. A diverse community of software and hardware makers came together to fix the vulnerability and to coordinate the disclosure and patching of the design flaw.
 In 2009, Microsoft heralded the formation of an industry group to collaboratively counter Conficker, a malware threat that infected tens of millions of Windows PCs and held the threat of allowing cybercriminals to amass a stupendous army of botted systems virtually overnight. A group of software and security firms, dubbed the Conficker Cabal, hashed out and executed a plan for corralling infected systems and halting the spread of Conficker.
In 2009, Microsoft heralded the formation of an industry group to collaboratively counter Conficker, a malware threat that infected tens of millions of Windows PCs and held the threat of allowing cybercriminals to amass a stupendous army of botted systems virtually overnight. A group of software and security firms, dubbed the Conficker Cabal, hashed out and executed a plan for corralling infected systems and halting the spread of Conficker.
In 2011, a diverse group of industry players and law enforcement organizations came together to eradicate the threat from the DNS Changer Trojan, a malware strain that infected millions of Microsoft Windows systems and enslaved them in a botnet that was used for large-scale cyber fraud schemes.
These examples provide useful templates for a solution to the DDoS problem going forward. What appears to be missing is any sense of urgency to address the DDoS threat on a coordinated, global scale.
That’s probably because at least for now, the criminals at the helm of these huge DDoS crime machines are content to use them to launch petty yet costly attacks against targets that suit their interests or whims.
For example, the massive 620 Gbps attack that hit my site this week was an apparent retaliation for a story I wrote exposing two Israeli men who were arrested shortly after that story ran for allegedly operating vDOS — until recently the most popular DDoS-for-hire network. The traffic hurled at my site in that massive attack included the text string “freeapplej4ck,” a reference to the hacker nickname used by one of vDOS’s alleged co-founders.
Most of the time, ne’er-do-wells like Applej4ck and others are content to use their huge DDoS armies to attack gaming sites and services. But the crooks maintaining these large crime machines haven’t just been targeting gaming sites. OVH, a major Web hosting provider based in France, said in a post on Twitter this week that it was recently the victim of an even more massive attack than hit my site. According to a Tweet from OVH founder Octave Klaba, that attack was launched by a botnet consisting of more than 145,000 compromised IP cameras and DVRs.
I don’t know what it will take to wake the larger Internet community out of its slumber to address this growing threat to free speech and ecommerce. My guess is it will take an attack that endangers human lives, shuts down critical national infrastructure systems, or disrupts national elections.
But what we’re allowing by our inaction is for individual actors to build the instrumentality of tyranny. And to be clear, these weapons can be wielded by anyone — with any motivation — who’s willing to expend a modicum of time and effort to learn the most basic principles of its operation.
The sad truth these days is that it’s a lot easier to censor the digital media on the Internet than it is to censor printed books and newspapers in the physical world. On the Internet, anyone with an axe to grind and the willingness to learn a bit about the technology can become an instant, self-appointed global censor.
I sincerely hope we can address this problem before it’s too late. And I’m deeply grateful for the overwhelming outpouring of support and solidarity that I’ve seen and heard from so many readers over the past few days. Thank you.




Smells more like a group, like those behind ZeroAccess.
According to Paloalto data they are highly active.
How does Google’s Project Shield prevent this from happening again?
None can take down google for sure!
In response to “How does google help?”
There’s an old joke about how does Google tells if it is being DDOS’d?
But seriously, how does it tell?
Answering my own question, this fron engadget:
From a technical perspective, Project Shield lets those who sign up use Google’s domain name servers rather than their own. After that, traffic coming to the site is routed through an intermediate, Google-owned intermediate “reverse proxy” server that can filter out malicious traffic. How exactly that’s done wasn’t specified, as Google doesn’t want to give attackers any idea of how it defeats their attempts.
I guess we will soon learn if Google’s reverse proxy server really works.
Not knowing the specifics, I foresee the reverse proxy server won’t stand. If portions of the google network are affected, that server eventually has nothing to operate on. Portions of country-regional networks have been clogged before by DDOS, let alone Internet providers DDOSed.
Have to agree. It is a shame that there is zero responsibility taken by the vast majority of hardware manufacturers and too often even less taken by the consumer.
I had typically laid a lot of the blame very squarely with ISPs who I think have a huge capability and duty of care in respect to better stopping the bad data and connections, so it was interesting to see some of the reasons they may struggle to do so.
As you say though, with something growing at the size at which connected IoT devices are and with too many ungovernable places on the net, it will be near impossible to get a grip of this escalating issue.
Will be interesting to se how Project Shield stands up to the next onslaught.
Can’t really blame the consumer. They are constantly bombarded with marketing telling them that IoT is the next big thing and that it’s all perfectly safe (like the internet marketing in the 1990s). Can’t really expect the consumer to be a technical expert.
True that, I don’t expect them to be experts, but if I liken it to cars and I am no mechanic but there is expectation upon me to undertake due diligence, check the tyre pressures, tread, lights etc. and I think hiding behind the excuse that it is too technical in this the digital realm is both lazy and dangerous.
If you have an IP camera, internet connected, smart TV, NAS, I think you should understand for your own sake things like changing baked in passwords etc.
I don’t expect the ‘normies’ to be setting VLANs and firewall rules to block certain traffic etc and keep the good away from the bad, but we have to start somewhere and we all should be responsible for our own devices to a greater or lesser extent.
I hear you though, baby steps.
The most significant and thought-provoking piece I’ve read in months. Thank you, Brian. And thank you for your dedication and hard work.
We dont allow cars on public roads with no brakes or headlights, and cops are supposed to write tickets for excessive polluters. We dont allow buildings to be occupied if they dont meet safety codes. We dont allow companies to dump toxic waste into air, creeks and streams. Why dont we have legislation that prevents access from/to ISPs who spew out such junk? Why dont we cite individuals who do the network equivalent of driving around on half inflated bald tires in a clunker spewing smoke? If the ISPs start being blocked by law, they will get the point real quick when it hits them in the wallet.
@doc ” Why dont we have legislation that prevents access from/to ISPs who spew out such junk?”
Who is the “we” to whom you refer? Any individual nation is just one country among many that have an internet infrastructure. As such, there is no effective way to regulate ISPs in countries outside of any one nation’s regulatory purview. Many of those countries have no special interest in stopping this type of activity and in fact may well be playing a complicit role.
While your point is valid, there is no centralised legislative body that can cover the entire internet, there is no harm, and indeed potentially some benefit, in starting somewhere.
The more countries pass relevant legislation, the more global pressure can be brought to bear on those who haven’t, and indeed potentially levels of distrust can be placed on transit links (by relevant transit providers) sourcing in countries without such legislation, e.g. maybe depriortising and throttling such traffic.
Perhaps if the responsible ISPs stopped sending traffic to the irresponsible ones and instead returned a message to the sender of the request explaining why they weren’t doing business with the irresponsible ISP the irresponsible ones would loose customers and go out of business or mend their ways.
@Harry, couldn’t agree more. New laws are not the answer here, although that is exactly what we will eventually get to address this issue if the industry players don’t step up and tackle this problem themselves.
A good read and a very important topic. ISP’s certainly have a need for focusing on all of this and so do end users. It is time for the average person to start learning how to take responsibility for their equipment. This affects us all and too many people are still refusing to deal with that flashing 12:00.
One thing is for certain….
This is not going to get fixed by doing any one thing.
The majority will auto update, but that seems to do nothing as these issues ARE getting worse. There are things that ‘updates’ don’t fix.
A very big part of this can be quite easily handled via the HOST file. But even that is not enough. I am setup to filter out over 260,000 websites. Much of this includes advertising. Many people will rely on noscript and that’s fine but only to a point. Most of that type of thing has it’s week point in the fact that what is allow to pass through can easily be bought and sold.
Everyone from ISP’s to webmasters to company board rooms and all the way down to the typical end user NEEDS to understand that these machines are going to do what they are told to do. If you decide not to control them, someone somewhere will.
——————————————-
“If you choose not to decide, you still have made a choice”
“I am setup to filter out over 260,000 websites. Much of this includes advertising”
That’s a different problem since those hosts (your list is mostly domains) are not attacking you. since you are not accepting incoming connections. Nor was Krebs attacked by those domains or IPs, it was mostly NAT’d IPs attacking him.
All these devices are ‘calling home’. It would be easier to remotely commandeer them using this function. The app that comes with a DVR does not connect through the IP given to the customer but rather the website of the camera manufacturer. It would be the same with everything else.
Hosts is only for outgoing connections.
If someone gets into a camera (which probably doesn’t have an accessible hosts file in the first place, and doesn’t stop anyone from getting inside), they can direct it to spam someone else with packets… which is apparently what happened in this attack.
I never said anything about Hosts files ‘on the camera’. That would be ridiculous. Infact, the only reason to deal with the host files on any individual device within the network is if that is the only device on the network. Even then this really is not very efficient.
I’m talking about doing it at the router level. I’m talking about redirecting things to 127.0.0.1 for any device on the network with just one entry per website/IP.
It is NOT just for outgoing. It works quite well for incoming data (or would-be incoming data).
If I’m not wrong, you were target of smaller attacks after a story about vDos, but massive attack started a few hours after BackConnect story.
Also, applej4ck and his affiliates were script kiddies who used mainly DNS amplification attacks. They didn’t have a botnet.
I’m not defending script kiddies, neither blaming BackConnect… I have no proof for anything. But I’m suspicious…
Good to see you back online Brian.
We had an attack of nearly 300gb on the server, only to find out after some hours of hard work the attack was raised. Much like the case Schneider wrote about.
anyways, nice to reach the blog again.
Isn’t building cyberweapons and counter tools our current non-visual cold war already?
Also I was wondering; Last piece someone replyed about a honeypot, since you are a face – you’re a target, can’t you use that position to blacklist ‘m all?
Guess an armed response would be a fun next thing.
As one of your many loyal readers, I’m simply very glad to see you are back online.
The one thing I don’t get is why risk collateral damage to large portions of the Internet? Just because you wanted your site available 100% 24/7, the entire Internet had to suffer collateral damage?
It’s nice to wave the “freedom of speech” idea, but at the end of the day, even if the blog was down, the data still exists on Google cache or Wayback machine. Was it that important to keep the site up, wasting millions of dollars, and slowing down the Internet, just to prove a point?
Brian, you should’ve assumed responsibility, and understand that at some point, cutting your loses and leaving the table is a mature thing to do. This is not the war between the Rebels and the Empire, it’s just a couple of pimpled-faced kids taking down your site, along with half of the Internet. Was it really a battle for “free speech”?
So, we should just sit back and let hoodlums ruin the internet? That sounds like a great idea. Oh wait, that’s what we’re already doing. Cowardice is never a good thing, and what you’re advocating is just that.
Then again, freedom of speech is a wonderful thing.
I respect you even more for the statement below.
Walking off the table would only postpone the collateral damage.
It’s better that they’ve taken down your site than some major e-commerce provider or critical infrastructure. Maybe such threat here and now will wake up somebody?
Anyway – such attack was like Judgment Day in the Terminator movie – it was inevitable (speaking Arnold’s voice 🙂 )
I think this will be MY response if this same thing happens to Facebook.
What about Google or Microsoft’s website? This same thing could just as easily happen to the Apple app store. What will the response be if the CNN site goes down? or Bloomberg or Slashdot or arstechnica? What if this had happened to the Clinton campaign website?
Ya know, we all saw the frenzy that took place when the playstation network went down.
You are a fool if you think this is just about Brian Krebs.
So Daniel, if a crook found out your address and came round every day to dump manure on your lawn, would you sell your home, just to protect your neighbours from the smell? Even if you knew that this crook would most likely move on to one of those neighbours as their next target? Wouldn’t you try your best to defend against the attack, and then try to alert people to the underlying problems that let the crook carry out the attack and made it difficult to defend against?
Great krebsonsecurity is back up. There needs to be a clear path IoT device manufactures take to get every IoT device certified to be secure. DDoS attacks will continue to grow in size and scope and lives will be lost. Brilliant idea on forming a NP 501(c)3 – I would support & promote. I think this would work thru a kickstarter and you would get great support.
keep up the great reporting – don’t let the thugs deter you!
Scott
http://www.hackedagain.com
Scott, why not require a certification similar to the FCC certification required by devices that use wireless communications? It would only be in effect for the United States but it would be an improvement.
Enabling DDOS by cultural standard of “Thoughtless Plug n Play”
Glad to see you back also. I would think after all this time, folks would know that the failure to participate in voluntary remediation of the problems you have discussed will eventually result in legal compulsion from lobbyist-owned government agencies. The final result of the latter remedy always tends to be worse than the disease.
Build a wall, a firewall!
We (USA, as a society) and maybe even humans as a civilization, have some standards about censorship: anything political is OK to talk about, facts are OK to talk about, falsehoods that cause panic are not OK to assert as true. Yes, we argue about borderline cases, but I think we can agree there’s some almost universal standards.
Before The Internet, only governments and the very largest companies could censor things.
The Internet has allowed single, regular humans, like Brian Krebs and all of us with web sites, to be our own publishers. It’s allowed all of us to have the reach of newspapers and tee vee stations. The Internet has also allowed single, regular humans the power to censor. That power hasn’t been used very much until recently.
We’ve seen that governments and large companies don’t want to give up their role as sources of information. Clearly, they won’t want to give up their role as censors, either.
I’m pretty sure that we (as a civilization of humans) can figure out standards of behavior around individual censorship, just like we’re figuring out standards around universal publishing. What worries me is the collateral damage that governments and large companies will cause trying to re-assert themselves as censors. That will cause some ugly problems.
Run-Brian-Run
A man is not done, until he stops trying.
As long as you can breath and move,never, ever stop.
Chase them into the sea!
Many thanks.
C/od
Hello again, thanks Brian for all the work you put in for us, you too Google for the hosting.
This could be easily solved if ISPs started cutting people off if they’re participating in an attack, whether they know they are or not. Of course, such a thing won’t happen unless their are financial or legal penalties for not doing so. In fact, with more and more ISPs embracing usage caps and overage fees they have more reason than ever not to do that.
While Brian Krebs doesn’t fault Akamai for its decision to pull the plug on protecting his web site and let his site go unprotected “for business reasons”, I’m not sure if I can be so generous. Akamai had a huge potential marketing opportunity to publically claim that they’re the ones who kept krebsonsecurity.com up and running when the bad guys wanted it brought down.
But instead Akamai chose to cut and run.
We should all keep this in mind when choosing the partner to protect our businesses.
It looks very bad for Akamai, they did the wrong thing and chose to drop him. A large percentage of Security Professionals read Kreb’s blog and certainly would make anyone think twice.. pay $200,000 to mitigate with Akamai or go with Google for free!
Exactly.
If Akamai had definitively promised Krebs the same level of protection as paying customers, but for free, then perhaps they would be in the wrong here. But that doesn’t seem to be the case.
You think that “Akamai had a huge potential marketing opportunity”, but surely it is for them to judge the costs & benefits of any marketing opportunity, and it makes no sense to judge anyone harshly for not taking up such an opportunity.
What I take from your comment is that ‘no good deed goes unpunished’, and that I should be very wary of being kind to others, because there is always the possibility of some kind of complication, and there will always be people like you ready to pounce.
Had Akamai told Brian Krebs from the outset that they could not offer their services pro-bono then I could respect that. This situation is no different than a big law firm taking your case then dropping you half way through the trial because it was uneconomical.
“Akamai rather abruptly informed me I had until 6 p.m. that very same day — roughly two hours later — to make arrangements for migrating off their network. ”
That’s a very irresponsible company if I may say so. The billon dollar company could have at least given him a few days to sort alternative arrangements out & if they did I don’t think they would even be this discussion.
This is Not a mission critical site, whereas I would expect other Akamai customers might have some of those.
Me thinks Paul is a class-action attorney.
That’s a bit of an odd comment.
I was simply questioning Akamai’s actions.
How about litigation against one or all of RIRs ? They must have some responsibility to protect IPs from being stolen by other AS’ ?
I’m happy that you never replied to CloudFlare’s offer to help, but now I’m worried that you are no longer in a position to criticize Google, should the situation arise. Google can be sneaky. Don’t take my word for it (although I have experience in this area), just ask anyone in Europe.
At the same time, I have to admit that if you have something to say that you feel is worthwhile, you have to let the googlebots crawl all over your pages, 24/7. Otherwise nobody will find you.
A question on behalf of the consumer who wants to be both informed and responsible:
Is there a site or other resource that lists which CPE devices are known to known to be vulnerable, or known to *not* be vulnerable (or what steps could be taken to mitigate those vulnerabilities)? I do not for one moment want any device within or at the border of my network to be responsible for attacks on another party.
As Brian pointed out in the post, there really isn’t any testing facility with capabilities similar to the UL (Underwriter’s Laboratory). There are projects out there, DD-WRT for routers comes immediately to mind, that commit to providing alternative, open source, software which are kept up to date for known security flaws. Of course using a (small) computer with a pretty bulletproof operating system is an alternative as well. An appliance which is what a router is, in practice.
The full name, Underwriter’s Laboratory, immediately underscores the driver for safety, the insurance industry. For now, they are uninvolved in most issues surrounding computer, application, and network security. I fully expect this to change if covered targets become a problem. They also have deep, deep pockets to pay lobbyists. I seriously doubt it will be a pleasant process for anyone involved in the industry when/if insurers take an interest.
You probably meant to link to https://jigsaw.google.com/projects/#project-shield instead of https://jigsaw.google.com/vision/ (Project Shield link in the 7th paragraph of the article)
SO glad your back on line! Your reporting in invaluable. And a BIG thank you to Google.
Now I just need to find a product of theirs I can use so I can reward them with my patronage.
P.S. This situation got me off my ass to purchase a subscription to my local news paper, I hope more will do the same. They need the support and we need them!
Hi Brian, nice to see you back online.
My input to this discussion would be to urge the major ISP’s, those who are proud to achieve that status, to implement solid best practices to prevent misuse of the internet.
A Free Internet is a place without this kind of violence, Just like the real world should be without violence… Self respecting ISP’s should be able to achieve this because economic powers are better in reaching their goals then political.
First off a big thank you, Brian, for continuing to put yourself out there and take risks on our behalf. Continue to be careful out there though.
As a guy who has a business developing sites on WordPress (WP), and 40 of them we also secure, backup and defend, I have seen first-hand the almost unbelievable assault on these sites (and WP sites overall) which happen on a daily basis. To say I’ve grown weary of these skirmishes and battles is an understatement.
Then two years ago I co-founded an IoT conference (IoTFuse) and entered in to a world with a dizzying array of insecure devices as you describe. From established companies to startups, security is just a checklist item instead of a priority and, thankfully, security has become THE hot topic at IoT conferences around the world.
Your clear belief in coalitions of the powerful internet companies to work together on mitigation solutions is spot-on. None of the rest of us can solve these problems. Plus, others like the NSA exploit rather than assists (or leads) in plugging holes or actually defending our nation. Same with other nation-states and those making money from exploits so the trend-line is clear: cyber attacks are only going to increase.
Let’s hope strategic internet orgs get together before those attacks grow exponentially and some specific attack doesn’t hobble the internet for days before taking action.
IoT’s will never be secure because they are managed by digibetes, normal people who just want to enjoy the luxury of IoT’s. They say security is not there business! I can’t blame them for this attitude.
The manufacturers of IoT’s are incompetent or unwilling to secure their goods.
They can only be forced to good conduct by governments.
If the misuse of IoT’s has unwanted effects on the service of ISP’s then they should act! The ISP’s however choose to ask Protection Money…
IMHO the only way you could enforce a saver internet is if governments are willing to force ISP’s into good conduct. The manufacturers of ISP materials will follow because they want to sell… Governments are always making the playfield on which we citizens are living. Only they can make the difference.
The argument for governments to act is that a saver internet is a good defense against cyber wars…
It is good to hear that Google does such things. This is a matter of principle and, with Google’s vast resources, your valuable web site should be around for the foreseeable future.
First of all I am happy that Krebs on Security is back online and I hope it stays this way.
Regarding Akamai I fully understand as a commercial business you cannot risk affecting paying customer and losing serious money just to look good, at least not for a longer period and with Google doing the job for free I see this as a happy ending, and Google engineers can test their systems in real world attacks.
In my view the costs of doing business is increasing all the time, you need to secure your network against all kinds of intrusions and against DDOS attacks, and all is not cheap and not always working.
My private conclusion is to rely on the internet as little as possible, I even have a stash of cash at home just in case the ATM’s go down.
The Internet – never boring….
When my home page failed to load the other day (krebsonsecurity.com), I pondered the cause, perhaps my ISP was having issues. Alas, your site was hammered. So happy you are back!
Something critical is missing from the conversation. As members of the connected revolution we all are either part of the problem or part of the solution. There is no middle ground! Unless individual users take security more seriously, the openness and freedom that has been maintained for so many years is deeply threatened. The threat is not by Nation States or script kiddies, it is clearly death by a thousand cuts because we, the users are allowing apathy to rule.
Virtually all effective security that is “baked” into the internet is developed, or improved and maintained by the community. Open source operating systems, IDS, threat databases and the like are more stable, reliable and cleaner because of the constant dedication of very skilled coders and researchers who collectively comb through millions of lines of code every day & night finding security vulnerabilities and fixing them.
John Q Public’s eyes are a glaze when even the prospect of network security is pondered. Asking them to actually pry their wallet open to contribute to the further development of really good behavior based security software is, in their minds absurd. They still suffer from Normalcy Bias; because is hasn’t happened to them, the threat must not be real. In fact, I believe they hear internet security as just noise, it just does not resonate.
While certainly threat actors are omnipresent, believing that legislation, fines, or any kind of government intervention would be beneficial is a bit like letting the fox into the hen house. Besides, want to screw something up? Just let Uncle Sam get his grubby fingers involved.
Nation States are undeniably linked to some (RSA, Juniper) back doors and can effectively hack systems in the manufacturing and logistics processes. With the proliferation of $5 Raspberry PI, it now costs almost nothing to create private robotic networks. Think of it, for a stipend of only $1M, you can have 200,000 node botnet. Instead of driving around and dropping flash drives in parking lots, you just drop a computer in the mail and convince the masses to connect. At present, it is estimated there are more than 10 Billion connected devices. Each one a target and a threat!
“The only thing necessary for the triumph of evil is for good men to do nothing.”― “Whilst men are linked together, they easily and speedily communicate the alarm of any evil design. They are enabled to fathom it with common counsel, and to oppose it with united strength. Whereas, when they lie dispersed, without concert, order, or discipline, communication is uncertain, counsel difficult, and resistance impracticable.” —Edmund Burke
You may be thinking if I cut my finger I bleed jade in color? Being in the trenches with users’ lack of interest gives me immense fear and trepidation. I’m convinced the great society is headed for drama, trauma and chaos like we’ve never seen before if we do not band together and form a National Human Firewall.
Stay focused my friends!
E2
In 1997, ISPs suddenly discovered that their customers email was being blocked if they had their SMTP servers set as open relays by many other ISPs. The Googles and Akamais and other providers could fix this by shaming the non BCP38 compliant into BGP never-never land instead of allowing this internet feces to continue. The internet needs to grow up and get out of this “Wild West” stage and those folks that -could- fix it need to get involved in helping the community.
Welcome back! And what a quick return that was! As you see, there are ways to mitigate these attacks. What disturbed me most is that the two israeli kids walked away free (on bail or what?) with the wagging finger of some invisible cop telling them to lay off the inderwebs for the next weeks? How scary for those kids and their fans….?*not*