A U.S. District Court judge in Atlanta last week handed a five year prison sentence to Mark Vartanyan, a Russian hacker who helped develop and sell the once infamous and widespread Citadel banking trojan. This fact has been reported by countless media outlets, but far less well known is the fascinating backstory about how Vartanyan got caught.
For several years, Citadel ruled the malware scene for criminals engaged in stealing online banking passwords and emptying bank accounts. U.S. prosecutors say Citadel infected more than 11 million computers worldwide, causing financial losses of at least a half billion dollars.
Like most complex banking trojans, Citadel was marketed and sold in secluded, underground cybercrime markets. Often the most time-consuming and costly aspect of malware sales and development is helping customers with any tech support problems they may have in using the crimeware.
In light of that, one innovation that Citadel brought to the table was to crowdsource some of this support work, easing the burden on the malware’s developers and freeing them up to spend more time improving their creations and adding new features.
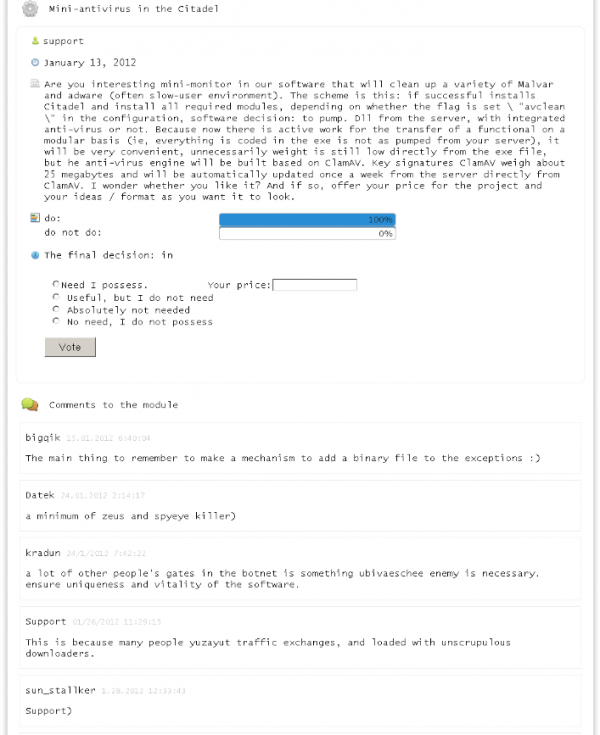
Citadel users discuss the merits of including a module to remove other parasites from host PCs.
Citadel boasted an online tech support system for customers designed to let them file bug reports, suggest and vote on new features in upcoming malware versions, and track trouble tickets that could be worked on by the malware developers and fellow Citadel users alike. Citadel customers also could use the system to chat and compare notes with fellow users of the malware.
It was this very interactive nature of Citadel’s support infrastructure that FBI agents would ultimately use to locate and identify Vartanyan, who went by the nickname “Kolypto.” The nickname of the core seller of Citadel was “Aquabox,” and the FBI was keen to identify Aquabox and any programmers he’d hired to help develop Citadel.
In June 2012, FBI agents bought several licenses of Citadel from Aquabox, and soon the agents were suggesting tweaks to the malware that they could use to their advantage. Posing as an active user of the malware, FBI agents informed the Citadel developers that they’d discovered a security vulnerability in the Web-based interface that Citadel customers used to keep track of and collect passwords from infected systems (see screenshot below).
A screenshot of the Web-based Citadel botnet control panel.
Aquabox took the bait, and asked the FBI agents to upload a screen shot of the bug they’d found. As noted in this September 2015 story, the FBI agents uploaded the image to file-sharing giant Sendspace.com and then subpoenaed the logs from Sendspace to learn the Internet address of the user that later viewed and downloaded the file.
The IP address came back as the same one they had previously tied to Aquabox. The other address that accessed the file was in Ukraine and tied to Vartanyan. Prosecutors said Vartanyan’s address soon after was seen uploading to Sendspace a patched version of Citadel that supposedly fixed the vulnerability identified by the agents posing as Citadel users.

Mark Vartanyan. Source: Twitter.
“In the period August 2012 to January 2013, there were in total 48 files uploaded from Marks IP to Sendspace,” reads a story in the Norwegian daily VG that KrebsOnSecurity had translated into English here (PDF). “Those files were downloaded by ‘Aquabox’ with 2 IPs (193.105.134.50 and 149.154.155.81).”
Investigators would learn that Vartanyan was a Russian citizen who’d grown up in Ukraine. At the time of his arrest, Mark was living in Norway, which later extradited him to the United States for prosecution. In March 2017, Vartanyan pleaded guilty to one count of computer fraud, and was sentenced on July 19 to five years in federal prison.
Another Citadel developer, Dimitry Belorossov (a.k.a. “Rainerfox”), was arrested and sentenced in 2015 to four years and six months in prison after pleading guilty to distributing Citadel.
Early in its heydey, some text strings were added to the Citadel Trojan which named Yours Truly as the real author of Citadel (see screenshot below). While I obviously had no involvement in writing the trojan, I have written a great deal about its core victims — mainly dozens of small businesses here in the United States who saw their bank accounts drained of hundreds of thousands or millions of dollars after a Citadel infection.
A text string inside of the Citadel trojan. Source: AhnLab




Wow that CitadelComment_ASCII variable looks like at least like a shot over the bow, or at worst, a direct threat. What’s your take on that comment, Mr. Krebs?
I strongly suspect that this whole article IS Brian’s response to that comment. 🙂
When they invoke my name, usually they either want my attention or they want me to know I have their attention.
It’s up to them if they get your attention.
It’s their choice to be thieves. Anyone that thinks they can continuously commit crimes in a digital world and not get caught are just…. might be smart technically, but are dumb morally/ in life.
Security teams don’t want attention from Brian and cyber criminals do want attention. Strange world
That’s pretty funny, Brian. you must be doing something right!
Idiot couldn’t even bother himself to use Tor…
BK forgot his closing paragraph:
“So, to anyone else writing malware, this is how you let your guard down and get caught. Learn from how these guys got engineered by the FBI so that you don’t.”
I’m just teasing. Years ago, I noticed on the news how the reporters would explain what the criminals did that got them caught. When reporting a bank robbery, they blatantly laid out the minute details of how the robbers were tracked down, etc. It struck me as training for how not to get caught for future criminals. That doesn’t exactly apply in this case because the criminals must market their malware by providing support. The FBI just followed the breadcrumbs from there. If you don’t provide support, criminals won’t want your malware. I love the irony that the very feature necessary to make your malware more popular also provides the route for your personal demise. With as much work as these guys have to do, why not just get an honest job that you can go home from?
“If you don’t provide support, criminals won’t want your malware.”
Why not just use the malware yourself to make a few million, then lay low for five years or so? You could work on making the malware better over that time and then hit again for twice as much. You could also do smart things to avoid getting caught…like, stay off social media, use Tor and Tails, not get cocky and arrogant, etc. These idiots make it too easy for the FBI!
Or, they were using Tor/Tails/whonix/etc and were caught by a NSA 0day?
I mean… the silk road guy using is own name / keeping logs of his conversations, the second silk road guy using is own name, Alphabay (dead) guy was using is real identity too to buy is server,
etc etc.
Are they all dumb or what?
I don’t know. Maybe.
But it can also be a NSA 0day at work. 🙂
(I don’t know actually, don’t listen to me)
I am a big fan, but I have to say now that I’ve been reading your blog for several years. You sound a lot like American cops. “We’re the good guys! We got the bad guys!”
Is there room in this fundamentalist view for an ethical hacker? Because you almost never paint hacking in a positive light. Almost never … I should say ‘never.’ I have never read you say a single good thing about any hacker, ever. In my view, my being able to make such a categorical, generalized statement means that you’re simply not looking for the hackers that are doing positive things, and so you’re proceeding as if there aren’t any.
I would like to challenge you to find one hacker you think is doing some good in the hundreds that are plain thieves. Even John Wayne wasn’t as fundamentalist as you.
https://en.wikipedia.org/wiki/Aaron_Swartz
We tried for YEARS to get the press and public to use “cracker” for this type of crook and save “hacker” for its original meaning of “someone who explores tech.”
We failed. It’s sad. Get over it.
“He says, Don’t you worry about Thieves’ Guilds, This is all what you have to do, you walk along the Streets at Night, shouting, It’s Twelve O’clock and All’s Well.
I said, What if it is not all well, and he said, You bloody well find another street.”
Hmm? I’d swear I’ve read Brian giving credit to “white hats” for all kinds of good works. He may not use the term “ethical hacker”, but it was understood by me anyway.
Last time I checked ethical hackers didn’t install malware on people’s systems and drain their bank accounts.
Security Researchers are essentially ethical hackers. There are plenty more people doing ethical hacking, but when you turn your exploits into financial gain, it ceases to be ethical.
My stories on these guys are almost certainly colored by the countless stories I’ve written about their victims, mostly small businesses that lost hundreds of thousands or millions of dollars and had zero hope of seeing that money again, all because of a Citadel infection.
Many, many peoples lives and businesses have been ruined by the activities of the men named in this story — who basically provided tech support to criminal hacking groups that were stealing, using and selling employee VPN credentials and certificates from countless companies.
“zero hope of seeing that money again, all because of a Citadel infection ”
Why ?
It’s not their fault. The bank and insurance should cover that.
I know it’s cracker gospel to claim credit card fraud is essentially victimless, in that only big banks suffer, but in my experience my small business had to eat virtually every disputed charge — even ones I knew had been valid. (I owned an adult newspaper, so we were regularly hit with “I have no idea, honey” chargebacks when someone’s spouse decided to go through the credit card statement.) Officially, I could have gone after the customer who had placed the order, won a judgement against them, and then worked through the various methods open to me to collect – which would have cost multiple times the loss in time and effort. What I did instead is toss the chargeback into an ever-thickening file, knowing that a certain percentage of our more-shady clientele would eventually forget just who it was they had defrauded and return to buy another ad — which I would consider selling them once their account was current.
But the banks never ate a cent of that fraud. Instead, they stood to *make* money, either by increasing our transaction fee should we ever incur an ‘excessive’ number of chargebacks or by assessing penalties should a large-enough chargeback — possibly one against a charge processed months earlier — push our account balance into the red.
Finally, an enlightening comment. I was a wholesaler to retailers. The banks constantly cheated them out of reimbursements for card fraud. I always think of one case in which a young man came in and had full photo id, fully valid Visa cc & sale was correctly approved by the bank. My customer thought something was fishy, so helped the customer to his car, and wrote down his plate #. Three months after the sale, visa took back the money from the retailers acct. He then called the relevant visa ofc 89 times & was always put off. He went to the police with the plate #, found the parents, threatened charges & collected his money – but not from Visa.
He will serve 5 years. And after he live nice relaxed life.
that how it goes and how it is jail sentence is just like job.
Nice Job Brian…Take that photo twitter photo and hang it like a deer mount above the fireplace.
Still the sentencing of 5yrs for half a billion dollars in financial losses still seems like the punishment doesn’t fit the monetary crime. What’s the likelihood he’ll actually server the full sentence and not go right back to this when he’s out. These jail sentences are too soft and continue to send the wrong message.
While hanging up a poster such as that, one might as well overlay the image of a scope reticle centered on his face too! LOL!
Mike, there is no parole in the Federal Prisons. He’ll serve the five.
Just FIVE years? He will be out in two. Just in time to dive into the Windows 11 release.
Any cyber crime should have mandatory 10-years or more.
Not for fed: Federal incarceration doesn’t have parole. He’s stuck there for effectively the full time. And I doubt the Feds are going to let him have external computer access.
Federal incarceration does have “time off for good behavior”. See here: https://www.bop.gov/policy/progstat/5884_003.pdf
However, if you get administrative charges against you for screwing up, they can take that good time back. That used to not be the case – once you got the good time, you kept it. But they changed that. And it’s hard to NOT get charged with administrative violations over five years.
He will do 51 months and 10 days if he is a model prisoner. A mere slap on the wrist!
Who else could it be 😉 Of course, it’s a Russian hacker. Is there anything else that that country provides? (OK, dictators, vodka and mail order brides, but still…)
The sad truth is that this guy is probably glad to get out of Russia for the next 5 years. We should’ve sent him to Gitmo. Let’s see how he’d like that.
And what exactly USA provides to the world ? Accept blood firsty Presidents – dictators who like to bully , rob and steal from weaker nations .
As the US is progressing fast in genderism, gayrights, falling birth rates and affirmative action for maroding minorities financed by lobby groups Russia and China stepped ahead in quantum encryption outputting the most sophisticated virus so far with auto updating high-speed code making it impossible to hack or decipher. Whilst US is busy discussing banning white people from universities the digital mayhem is closing in on a USA paralyzed by liberal poison.
Russian vodka is crap.
After a long time I can read a story about FBI putting in practice their mission statement.
Hopefully not the last.
Good read, Krebs
Brian, where does he serve his (up to) 5 years? Maximum security? Medium? Or just Camp Fed?
More importantly, while behind bars, is he barred from having online access — so he can stay current on all the latest hacking tips and techniques?
That depends on his classification level, which depends on many factors including the severity of the crime, whether violence was involved in the crime, etc.
My guess is he’ll be in medium security to start, and toward the end of his sentence, depending on his behavior in prison, he’ll be transferred to a camp.
It’s hilarious how these guys, no matter how smart, get busted because they allow some IP address that is directly connected to them to be discovered.
I mean, the FIRST thing a hacker should do is make sure ANY email or IP address ever involved with his hacking has absolutely NO connection to his real identity.
Laziness gets you every time.
Interesting that the FBI and other police agencies were able to pull this off without compromising secure communications systems or encryption backdoors.
Interesting, again a crucial part was to enter into a commercial relationship with the bad actor . What I’d like to see next is greater co-operation from the payments system providers, without warrants, each provider is perfectly entitled to chase the train of bad money, and a warrant can follow in due course.
I don’t understand why these guys don’t use VPN to mask their real IP address…
Or do these forums ban users who log in from different IP all the time? But then, they could just set up their own VPN using a bullet proof server.
Just seems like a really silly way of getting caught.
Interesting that they followed the IP address and not the money. One would assume that transferring money through banks leaves easily traceable… traces.
Exactly. It’s a mystery to me why these easy to follow money trails don’t lead to the arrest of the bad guys at least 90% of the time. Somebody out there isn’t doing their job.
The funniest part in the whole story that his father is PIMP in Ukraine: http://forum.zabor.zp.ua/forum/viewtopic.php?p=385913#p385913
Wondered how the victims ever got their money back?
Punishment makes money money clean. all this hackers works under fsb. And fsb work together with cia. Their end goal is nwo
For all these people tracked back to IP addresses, I have to ask: why aren’t they using TOR? Or at least a couple of anonymizing proxies? Is it just hubris? Or are those technologies much less valuable than I have been led to believe.
I know there are web bugs they can use to infect browsers and track TOR users, but that’s still an extra step. Same for proxies since that would require extra subpoenas.
I don’t think we should overrate the capacity of Russian cyber-criminals by thinking they are super-geniuses that cover every single angle and create the perfect crime. They are just a bunch of people who happen to live in a jurisdiction that grants them impunity in most cases for cyber-crimed committed outside of their borders.
Wow, US playing the world police game again. Disgusting how a man can be extradited from the other side of the world to go to jail in a country he probably never has even been in. Absolutely unethical.
Unethical??? Perhaps if he wasn’t targeting customers, users and banks in the USA he would still be happily sitting at home with a glass of vodka and watching I Love Svetlana reruns. Cmon, does hypocrisy run deeply in your family?
Absolutely pissweak.
11 million victims, $500,000,000 in theft, average of $50 per victim.
That should be 1 months jail, x11 million, to be served consecutively.
Cyber thieves will not take the justice system seriously until it treats them seriously.
Too bad tough talk is what Americans are best at.
And locking up people – some guilty, some innocent, but mostly poor and minority – for a long time. Look how that has made Americans safer. Grow up folks and face reality.
“mostly small businesses that lost hundreds of thousands or millions of dollars and had zero hope of seeing that money again, all because of a Citadel infection”
Why ?
It’s not their fault. The banks and insurance should cover that.
This money is allready somewhere eastern european mafia pockets.
Thank you for the nice & very informative post.
I happen to know this hacker very well. The reason he did not hide his IP was that he was a small fish doing ordinary tech support. No identity theft, no money except $15 per hour for his freelance work. He’s a hard working programmer that took on the wrong job and did not understand the seriousness of it. 5 years is a very long sentence for doing tech support on the wrong project. Unfortunately FBI any many others needed a bad guy, so that is what Mark is portrayed to be.
That’s probably why he only got 5 years.
He was pulling in a minimal amount of cash, but the overall effect of citidel was millions of dollars lost from businesses.
Some people on here are saying he should have got 20 years and that seems unfair because in reality he just made it available and admittedly did aid other criminals, but in the end he’s the small fish that did the least. The people the FBI should be going after is everyone who used citidel and fucked over a multitude of people that owned a business and never got acquainted with the tech side enough to protect against something like that. Honestly I wouldn’t be surprised if they took his contacts and are tracking them now, maybe leading up to getting the actual big fish crime bosses.
Five years is a slap on the wrist for such a disruptive white collar crook – 15-20 would be my minimum sentence.