Equifax last week disclosed a historic breach involving Social Security numbers and other sensitive data on as many as 143 million Americans. The company said the breach also impacted an undisclosed number of people in Canada and the United Kingdom. But the official list of victim countries may not yet be complete: According to information obtained by KrebsOnSecurity, Equifax can safely add Argentina — if not also other Latin American nations where it does business — to the list as well.
 Equifax is one of the world’s three-largest consumer credit reporting bureaus, and a big part of what it does is maintain records on consumers that businesses can use to learn how risky it might be to loan someone money or to extend them new lines of credit. On the flip side, Equifax is somewhat answerable to those consumers, who have a legal right to dispute any information in their credit report which may be inaccurate.
Equifax is one of the world’s three-largest consumer credit reporting bureaus, and a big part of what it does is maintain records on consumers that businesses can use to learn how risky it might be to loan someone money or to extend them new lines of credit. On the flip side, Equifax is somewhat answerable to those consumers, who have a legal right to dispute any information in their credit report which may be inaccurate.
Earlier today, this author was contacted by Alex Holden, founder of Milwaukee, Wisc.-based Hold Security LLC. Holden’s team of nearly 30 employees includes two native Argentinians who spent some time examining Equifax’s South American operations online after the company disclosed the breach involving its business units in North America.
It took almost no time for them to discover that an online portal designed to let Equifax employees in Argentina manage credit report disputes from consumers in that country was wide open, protected by perhaps the most easy-to-guess password combination ever: “admin/admin.”
We’ll speak about this Equifax Argentina employee portal — known as Veraz or “truthful” in Spanish — in the past tense because the credit bureau took the whole thing offline shortly after being contacted by KrebsOnSecurity this afternoon. The specific Veraz application being described in this post was dubbed Ayuda or “help” in Spanish on internal documentation.
Once inside the portal, the researchers found they could view the names of more than 100 Equifax employees in Argentina, as well as their employee ID and email address. The “list of users” page also featured a clickable button that anyone authenticated with the “admin/admin” username and password could use to add, modify or delete user accounts on the system. A search on “Equifax Veraz” at Linkedin indicates the unit currently has approximately 111 employees in Argentina.
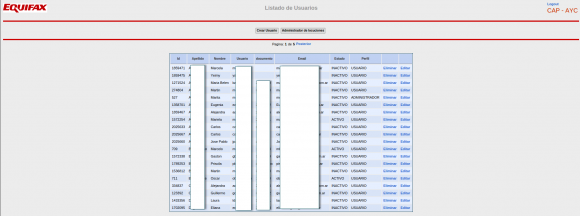
A partial list of active and inactive Equifax employees in Argentina. This page also let anyone add or remove users at will, or modify existing user accounts.
Each employee record included a company username in plain text, and a corresponding password that was obfuscated by a series of dots.
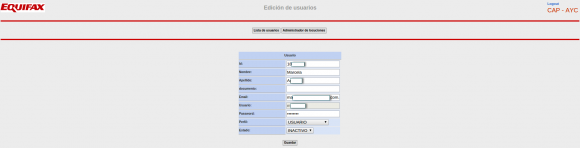
The “edit users” page obscured the Veraz employee’s password, but the same password was exposed by sloppy coding on the Web page.
However, all one needed to do in order to view said password was to right-click on the employee’s profile page and select “view source,” a function that displays the raw HTML code which makes up the Web site. Buried in that HTML code was the employee’s password in plain text.
A review of those accounts shows all employee passwords were the same as each user’s username. Worse still, each employee’s username appears to be nothing more than their last name, or a combination of their first initial and last name. In other words, if you knew an Equifax Argentina employee’s last name, you also could work out their password for this credit dispute portal quite easily.
But wait, it gets worse. From the main page of the Equifax.com.ar employee portal was a listing of some 715 pages worth of complaints and disputes filed by Argentinians who had at one point over the past decade contacted Equifax via fax, phone or email to dispute issues with their credit reports. The site also lists each person’s DNI — the Argentinian equivalent of the Social Security number — again, in plain text. All told, this section of the employee portal included more than 14,000 such records.
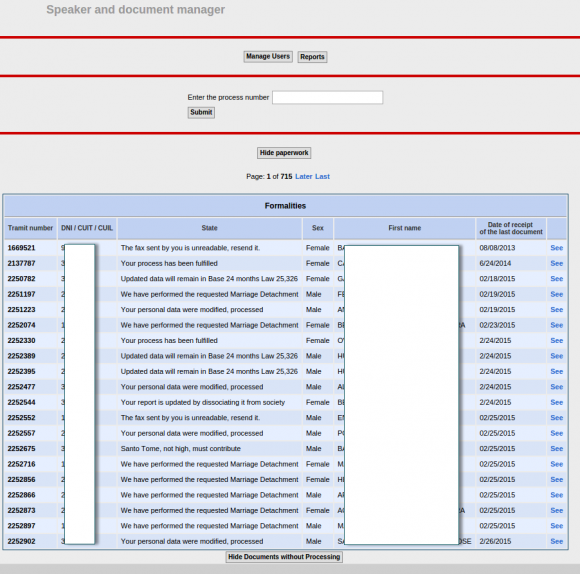
750 pages worth of consumer complaints — more than 14,000 in all — complete with the Argentinian equivalent of the SSN (the DNI) in plain text. This page was auto-translated by Google Chrome into English.
Jorge Speranza, manager of information technology at Hold Security, was born in Argentina and lived there for 40 years before moving to the United States. Speranza said he was aghast at seeing the personal data of so many Argentinians protected by virtually non-existent security.
Speranza explained that — unlike the United States — Argentina is traditionally a cash-based society that only recently saw citizens gaining access to credit.
“People there have put a lot of effort into getting a loan, and for them to have a situation like this would be a disaster,” he said. “In a country that has gone through so much — where there once was no credit, no mortgages or whatever — and now having the ability to get loans and lines of credit, this is potentially very damaging.”
Shortly after receiving details about this epic security weakness from Hold Security, I reached out to Equifax and soon after heard from a Washington, D.C.-based law firm that represents the credit bureau.
I briefly described what I’d been shown by Hold Security, and attorneys for Equifax said they’d get back to me after they validated the claims. They later confirmed that the Veraz portal was disabled and that Equifax is investigating how this may have happened. Here’s hoping it will stay offline until it is fortified with even the most basic of security protections.
According to Equifax’s own literature, the company has operations and consumer “customers” in several other South American nations, including Brazil, Chile, Ecuador, Paraguay, Peru and Uruguay. It is unclear whether the complete lack of security at Equifax’s Veraz unit in Argentina was indicative of a larger problem for the company’s online employee portals across the region, but it’s difficult to imagine they could be any worse.
“To me, this is just negligence,” Holden said. “In this case, their approach to security was just abysmal, and it’s hard to believe the rest of their operations are much better.”
I don’t have much advice for Argentinians whose data may have been exposed by sloppy security at Equifax. But I have urged my fellow Americans to assume their SSN and other personal data was compromised in the breach and to act accordingly. On Monday, KrebsOnSecurity published a Q&A about the breach, which includes all the information you need to know about this incident, as well as detailed advice for how to protect your credit file from identity thieves.
[Author’s note: I am listed as an adviser to Hold Security on the company’s Web site. However this is not a role for which I have been compensated in any way now or in the past.]




You should be ashamed of yourself.
Hacking a web portal for illegal entry is not something to be proud about.
I’m sure this article will expose more about you & Hold SecureLess than it will Equifax.
Blah Blah Blah
Seriously …. its these folks hacking and publishing results. This was not even a hack … thats the point they are making. They left the portal open to the entire world using the default username password.
You are right, he should have waited for someone with malicious intent to steal the data and use it for identity theft rather than finding it and reporting it…
Please don’t comment on things you do not understand.
Off-topic, perhaps, but my family has a new pet troll at home, and we aren’t sure what to feed it. Or whether to feed it at all.
they basically left the front door wide open. The disaster was imminent.
J. Minitera – really! Please don’t talk about something that you don’t understand crap about.
Thanks Brian,
I hope you were successful in helping these people before it was too late.
In the US I have to prove a viable password policy that is enforced.
When it comes to Equifax, irresponsible is as irresponsible does.
“Chief Financial Officer John Gamble sold shares worth $946,374 and Joseph Loughran, president of U.S. information solutions, exercised options to dispose of stock worth $584,099. Rodolfo Ploder, president of workforce solutions, sold $250,458 of stock on Aug. 2”
All claim they knew nothing of the breach.
Do U.S. information solutions differ fundamentally from lax international security audit standards?
Did they really not inform the CFO of a tsunami financial event?
Sick’em SEC.
As a business user of Equifax’s UK SOAP interface I was supplied with an extended security header. I asked Equifax for the SALT, concatenation and encryption to produce the NONCE field and they had no idea of what I was talking about. I later found that I could connect with just my 5 digit username and no security fields. I also found there was no lockout to prevent brute force attacks. They have been aware of this wide open access for nearly a year and now ignore my emails. Luckily for UK citizens we found a significant portion of their data is very dated.
https://www.freeze.equifax.com/Freeze/Freeze.htm only giving options to lift a freeze. There is no option to place a freeze. Is there another site or some way to get Equifax to fix their site?
Great one, thanks! 🙂
Hi there,I read your new stuff named “Ayuda! (Help!) Equifax Has My Data! — Krebs on Security” regularly.Your humoristic style is awesome, keep it up! And you can look our website about daily proxy.