Deloitte, one of the world’s “big four” accounting firms, has acknowledged a breach of its internal email systems, British news outlet The Guardian revealed today. Deloitte has sought to downplay the incident, saying it impacted “very few” clients. But according to a source close to the investigation, the breach dates back to at least the fall of 2016, and involves the compromise of all administrator accounts at the company as well as Deloitte’s entire internal email system.

In a story published Monday morning, The Guardian said a breach at Deloitte involved usernames, passwords and personal data on the accountancy’s top blue-chip clients.
“The Guardian understands Deloitte clients across all of these sectors had material in the company email system that was breached,” The Guardian’s Nick Hopkins wrote. “The companies include household names as well as US government departments. So far, six of Deloitte’s clients have been told their information was ‘impacted’ by the hack.”
In a statement sent to KrebsOnSecurity, Deloitte acknowledged a “cyber incident” involving unauthorized access to its email platform.
“The review of that platform is complete,” the statement reads. “Importantly, the review enabled us to understand precisely what information was at risk and what the hacker actually did and to determine that only very few clients were impacted [and] no disruption has occurred to client businesses, to Deloitte’s ability to continue to serve clients, or to consumers.”
However, information shared by a person with direct knowledge of the incident said the company in fact does not yet know precisely when the intrusion occurred, or for how long the hackers were inside of its systems.
This source, speaking on condition of anonymity, said the team investigating the breach focused their attention on a company office in Nashville known as the “Hermitage,” where the breach is thought to have begun.
The source confirmed The Guardian reporting that current estimates put the intrusion sometime in the fall of 2016, and added that investigators still are not certain that they have completely evicted the intruders from the network.
Indeed, it appears that Deloitte has known something was not right for some time. According to this source, the company sent out a “mandatory password reset” email on Oct. 13, 2016 to all Deloitte employees in the United States. The notice stated that employee passwords and personal identification numbers (PINs) needed to be changed by Oct. 17, 2016, and that employees who failed to do so would be unable to access email or other Deloitte applications. The message also included advice on how to pick complex passwords:
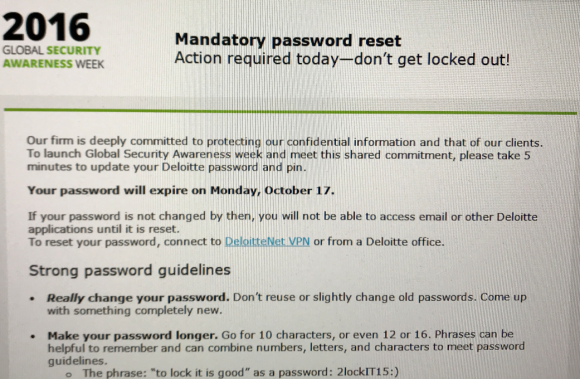
A screen shot of the mandatory password reset message Deloitte sent to all U.S. employees in Oct. 2016, around the time sources say the breach was first discovered.
The source told KrebsOnSecurity they were coming forward with information about the breach because, “I think it’s unfortunate how we have handled this and swept it under the rug. It wasn’t a small amount of emails like reported. They accessed the entire email database and all admin accounts. But we never notified our advisory clients or our cyber intel clients.”
“Cyber intel” refers to Deloitte’s Cyber Intelligence Centre, which provides 24/7 “business-focused operational security” to a number of big companies, including CSAA Insurance, FedEx, Invesco, and St. Joseph’s Healthcare System, among others.
This same source said forensic investigators identified several gigabytes of data being exfiltrated to a server in the United Kingdom. The source further said the hackers had free reign in the network for “a long time” and that the company still does not know exactly how much total data was taken.
In its statement about the incident, Deloitte said it responded by “implementing its comprehensive security protocol and initiating an intensive and thorough review which included mobilizing a team of cyber-security and confidentiality experts inside and outside of Deloitte.” Additionally, the company said it contacted governmental authorities immediately after it became aware of the incident, and that it contacted each of the “very few clients impacted.”
“Deloitte remains deeply committed to ensuring that its cyber-security defenses are best in class, to investing heavily in protecting confidential information and to continually reviewing and enhancing cyber security,” the statement concludes.
Deloitte has not yet responded to follow-up requests for comment. The Guardian reported that Deloitte notified six affected clients, but Deloitte has not said publicly yet when it notified those customers.
Deloitte has a significant cybersecurity consulting practice globally, wherein it advises many of its clients on how best to secure their systems and sensitive data from hackers. In 2012, Deloitte was ranked #1 globally in security consulting based on revenue.
Deloitte refers to one or more of Deloitte Touche Tohmatsu Limited, a private company based in the United Kingdom. According to the company’s Web site, Deloitte has more than 263,000 employees at member firms delivering services in audit and insurance, tax, consulting, financial advisory, risk advisory, and related services in more than 150 countries and territories. Revenues for the fiscal year 2017 were $38.8 billion.
The breach at the big-four accountancy comes on the heels of a massive breach at big-three consumer credit bureau Equifax. That incident involved several months of unauthorized access in which intruders stole Social Security numbers, birth dates, and addresses on 143 million Americans.
This is a developing story. Any updates will be posted as available, and noted with update timestamps.




The Register is reporting that Deloitte basically bent over, pulled down their pants and told the internet to come and have a go.
El Reg article points out – this is much much larger than their email “system.”
Domain controllers w/RDP enabled on public internet, even!
Totally was. Insane but hardly surprising that the company is trying to downplay this as much as it can.
I think many of us would respect a “we done f*cked up on a huge scale” honest approach though, would be refreshing.
I worked in Deloitte UK IT until 5 years ago and we had multifactor. In fact the internal security challenged us on everything we did, it was hard work but now I guess I know why! Wy to go USA
When I was at D. there was a Cyber Vault to handle all admin and service account passwords. Many regarded this as a joke and kept local copies of the passwords. Add to this the complexity of systems making a standard password reset cycle beyond impossible. It was easier to just fudge the books.
It would be interesting to know how many of these big breaches are the result of attackers using social engineering / insider threats vs. solely technical vulnerabilities.
It doesn’t matter how many controls you have in place if your administrators give away their passwords/information. Most places I would imagine don’t have 2FA enabled on every single system.
Then you have the problem of management and executives accepting amounts of risk that should never realistically be accepted. Can a CIO/CISO/CTO of a large company really be knowledgeable about the state of InfoSec at large as well as in his particular company? The ones I’ve talked to have somewhat detached from reality and only think “big picture” (usually how to cut costs and make more profits) – they don’t really care what you think (or know) is a real threat until their job is at stake.
We have technology that can provide 2FA to every user on every system, application, server, device, router, etc. We have the technology to Vault and randomize every single admin password, and have them used on a sign-out basis, log everything they do with it, and expire passwords after every single use. Sadly most companies don’t take this seriously until they get bit in the A$$ or are taking years to implement the most basic safeguards while they put themselves at risk.
“It would be interesting to know how many of these big breaches are the result of attackers using social engineering / insider threats vs. solely technical vulnerabilities.”
Here’s one insight Kyle. http://breachlevelindex.com/assets/Breach-Level-Index-Report-H1-2017-Gemalto.pdf There is a pie chart on the rt side about 1/3 of the way down, another about 1/2 way down.
There a bunch of sites that list various breach information, who did it, how it was done, type of info stolen. The list is endless!
More break down of info: http://www6.gemalto.com/breach-level-index-2017-h1-report?utm_medium=press-release&utm_campaign=bli-lp-report
Data Records Lost or Stolen Since 2013, 9,053,156,308
http://breachlevelindex.com/
https://digitalguardian.com/blog/history-data-breaches Site has an image about 1/2 way down with some stats on the type of breach.
https://www.privacyrights.org/data-breaches can be searched by way of various parameters but the CSV download doesn’t work.
https://en.wikipedia.org/wiki/List_of_data_breaches has a large list but I generally avoid WrongOpedia
I’ve found a lot of info the past two weeks but generally only saved the pie charts or graphics not the whole web page, so I can’t give you all the URL’s.
Everyone did freeze their credit info with the big 4 as well as (especially!) Chex Systems right?
Is their job really ever at stake though?
Worst case scenario seems to be a golden goodbye and a decent reference for the next employer.
Microsoft used to brag about the fact that Deliotte was using Office365. I guess that will stop.
Deliotte likely didn’t want to pay for the complete (expensive) o365 licence. As a result no 2 step verification from Microsoft. I read that in the UK they had 2SV. However the main admin account on O365 remained unprotected by 2sv.
I guess that is one the reasons that I like G Suite for enterprises. Google takes security seriously. They give everyone 2sv for free in their licence. Google gives partners a fee to give security workshops to customers to explain how to apply security measurements.
I’m sys admin at a small media company. We don’t deal with people’s data, have less than 20 users and I use 2FA on everything that supports it. Why don’t bigger companies in charge of other people’s data feel like 2FA isn’t necessary or too much work? It doesn’t solve everything but if someone tries logging in, if nothing else I will know it from the codes being sent for 2FA.
Because you’re a sysadmin at a small media company, and have no idea what the complexity is of pushing out something like Office 365 throughout an entire global conglomerates infrastructure. When you’ve dealt with enterprise, maybe you can open your mouth.
You took the time to take a cheap shot at a guy working at a small company yet you still didn’t answer is questions about why large companies might not use 2FA. This tells me you that you obviously don’t know yourself. Stop being so personal about it and provide some useful input instead of cheap shots.
Heard yesterday that their ISO 27001 implementation (scope: ‘confidential client data’….no joke!!!) is globally managed by an unexperiened UK freelancer…. way to go!
So my question is: A client of ours engages Deloitte to examine/audit my security to see if it is up to the client’s standards. Deloitte collects data from me about my security efforts and prepares a report for my client about me (and presumably all my client’s other third-party vendors.) Is all that data about our security efforts now exposed too? I fear it is.
https://www2.deloitte.com/content/dam/Deloitte/global/Documents/About-Deloitte/gx-FactsSheetforGlobalWebsite-cyber-attack.pdf
https://www2.deloitte.com/content/dam/Deloitte/global/Documents/About-Deloitte/gx-FactsSheetforGlobalWebsite-cyber-attack.pdf
Your site has good content. Thank you
I’ve worked for and with Deloitte. Their internal security is weak, to say the least. They also have a tendency to give their clients “good news,” even when other security audits demonstrate contrary evidence. It’s a strange culture at Deloitte; the only truly “matrixed” framework I’ve seen in terms of internal security. When a Managing Partner tells you he’s not the boss – you are…. there’s something off; it’s called deferred responsibility.
Deferred responsibility means, “if stuff goes sideways, it’s your fault, not mine.”
This is what happens when so called consulting (service like hospitality) companies like Deloitte, Ernst & Young, Accenture, Bain Capital, Booz Allen, etc. hire cheap inexpensive labor (labor that will work for 16-18 hours for the price of 8-9 hours) with no experience, promote them in 2-3 years, inflate their egos and make them the most immoral workers on the face of earth. Also, a bigger issue with Deloitte has been outsourcing to India in their USI department.
There must be full security rules followed in order to avoid such kind of things to happen. Hope it happens and the Internet will be more secure.