In May, KrebsOnSecurity broke a story about lax security at a payroll division of big-three credit bureau Equifax that let identity thieves access personal and financial data on an unknown number of Americans. Incredibly, this same division makes it simple to access detailed salary and employment history on a large portion of Americans using little more than someone’s Social Security number and date of birth — both data elements that were stolen in the recent breach at Equifax.
At issue is a service provided by Equifax’s TALX division called The Work Number. The service is designed to provide automated employment and income verification for prospective employers, and tens of thousands of companies report employee salary data to it. The Work Number also allows anyone whose employer uses the service to provide proof of their income when purchasing a home or applying for a loan.
The homepage for this Equifax service wants to assure visitors that “Your personal information is protected.”
“With your consent your personal data can be retrieved only by credentialed verifiers,” Equifax assures us, referring mainly to banks and other entities that request salary data for purposes of setting credit limits.
Sadly, this isn’t anywhere near true because most employers who contribute data to The Work Number — including Fortune 100 firms, government agencies and universities — rely on horribly weak authentication for access to the information.
To find out how easy it is to view your detailed salary history, you’ll need your employer’s name or employer code. Helpfully, this page lets you look that up quite easily (although if you opt to list employers alphabetically by the first letter of the company name, there are so many entries for each letter that I found Equifax’s database simply crashes half the time instead of rendering the entire list).
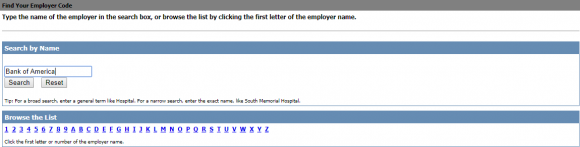
What’s needed to access your salary and employment history? Go here, and enter the employer name or employer code. After that, it asks for a “user ID.” This might sound like privileged information, but in most cases this is just the employees’s Social Security number (or a portion of it).
At the next step, the site asks visitors to “enter your PIN,” short for Personal Identification Number. However, in the vast majority of cases this appears to be little more than someone’s eight-digit date of birth. The formats differ by employer, but it’s usually either yyyy/mm/dd or mm/dd/yyyy, without the slashes.
Successful validation to the system produces two sets of data: An employee’s salary and employment history going back at least a decade, and a report listing all of the entities (ostensibly, the aforementioned “credentialed verifiers”) that have previously requested and viewed this information.
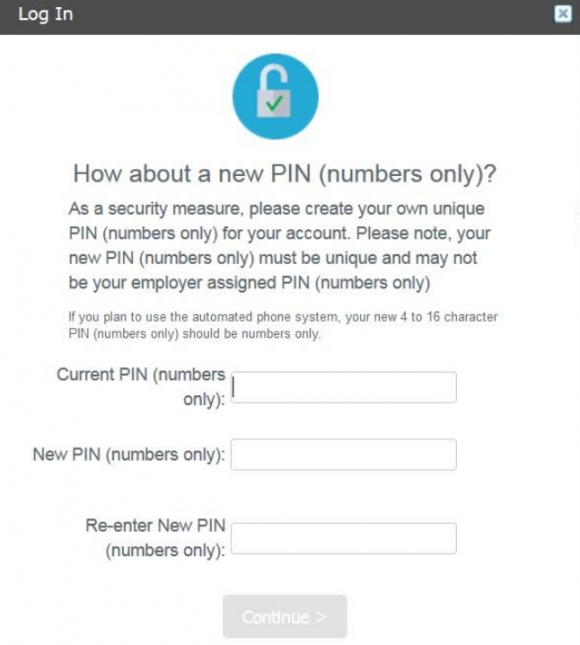
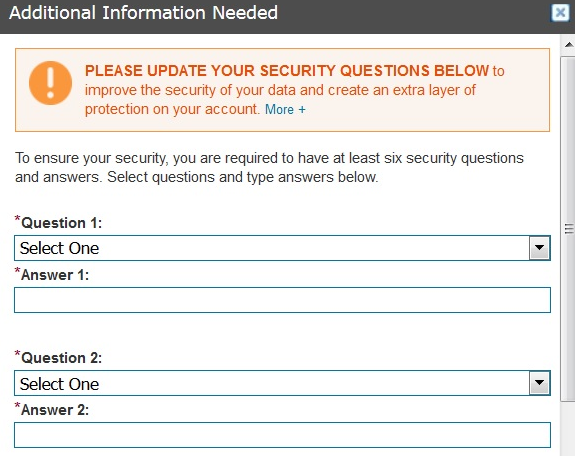
Once you’re successfully “authenticated,” the system asks you to change your PIN to something more secret than your birthday. When the default PIN is changed, The Work Number prompts users to select a series of six challenge/response questions, which Equifax claims will “improve the security of your data and create an extra layer of protection on your account.”
Unfortunately, consumers whose employee history is stored by this service effectively have no privacy or security unless they possess both the awareness that this service exists and the forethought to access their account online before identity thieves or others do it first.
The Work Number does allow employers to opt for TALX’s “enhanced authentication” feature, wherein after logging in with your employer ID and PIN (often the last four digits of an SSN plus the birth year), the system is designed to require the requester to respond to an email at a work address or a phone call to a work number to validate the login.
However, I did not find this to be the case in several instances involving readers whose employers supposedly used this enhanced authentication method. In cases where corporate human resources departments fail to populate employee email addresses and phone numbers, the system defaults to asking visitors to enter any email address and phone number to complete the validation. This is detailed here (PDF), wherein The Work Number states “if you do not have the required phone and e-mail information on file, you will be prompted to update/add your phone numbers/email addresses.”
Worse yet, while companies that use this service tend to vary their approaches to what’s required in terms of user IDs and PINs, a great many employers publish online detailed instructions on how to fill out these various forms. For example, the State of California‘s process is listed here (PDF); instructions for the Health Resources & Services Administration (HRSA) are here; employees at the National Institutes of Health (NIH) can learn the steps by consulting this document (PDF). The process for getting this information on current and former UCLA employees is spelled out here. There are countless other examples that are easy to find with a simple Internet search.
Many readers probably consider their current and former salaries to be very private information, but as we can see this data is easily available on a broad spectrum of the working population in America today. The information needed to obtain it has been widely compromised in thousands of data breaches over the past few years, and the SSN and DOB on most Americans is for sale in a variety of places online. In short, if you can get these details from Equifax’s online service, so can anyone else.
Fortunately, you can reduce the likelihood that an acquaintance, co-worker, stalker or anyone else can do this by claiming your own account, changing the PIN and selecting a half-dozen security questions and answers. As always, it’s best not to answer these questions truthfully, but to input answers that only you will know and that can’t be found using social networking sites or other public data sources.
I could see this service potentially helping to create a toxic workplace environment because it offers a relatively simple method for employees to glean data about the salaries of their co-workers and bosses. While some people believe that companies should be more transparent about employee salaries, this data in the wrong hands very often generates a great deal of resentment and hostility among co-workers.
Employers who use The Work Number should strongly consider changing as many defaults as possible, and truly implementing the service’s enhanced authentication features.
October is National Cybersecurity Awareness Month, and as such KrebsOnSecurity will continue pointing readers to similar services that let anyone access your personal data armed with little more than static identifiers about you that should no longer be considered private. Although some readers may take issue with my pointing these out — reasoning that I’m only making it easier for bad people to do bad things — it’s important to understand that knowledge is half the battle: Planting your flag before someone else does is usually the only way to keep others from abusing such services to expose your personal information.
Update, Oct. 9, 10:00 a.m. ET: The Work Number site is currently down for maintenance. A notice on the site says the company took the portal down a few hours after my story was published yesterday, without the usual advance warning the company offers for scheduled maintenance. The notice reads:
“Equifax Workforce Solutions is currently performing maintenance activities that will affect the following applications:
The Work Number EDR”
“We apologize for any inconvenience this may cause, but it is necessary to ensure
that Equifax Workforce Solutions continues to provide you the industry-leading services you
have come to expect.”
Also, several readers pointed out that when they tried the service Sunday evening before Equifax took it down they were asked to answer knowledge-based authentication questions before being able to authenticate to the portal to view their salary history. While this is a welcome additional step, regular readers here know how easy it is for ID thieves to bypass these multiple-guess questions (as the answers usually are available using sites like Zillow and Spokeo, to say nothing of social networking profiles).
Related reading:
–USPS ‘Informed Delivery’ is Stalker’s Dream
–Student Aid Tool Held Key for Tax Fraudsters
–Sign Up at IRS.gov Before Crooks Do It For You
–Crooks Hijack Retirement Funds via SSA Portal
–Social Security Administration Now Requires Two-Factor Authentication
–SSA: Ixnay on txt msg reqmnt 4 e-acct, sry




I really hope there are some repercussions for all of this. I blame Congress for failing to pass legislation to protect people against the stupidity of companies like Equifax. I also wish legislation would be passed to force companies like Adobe and Microsoft to make products that are not in need to constant security patches.
I hope you missed some sarcasm tags Alan. Counting on the government to solve your problems is no way to live. Hard enough to have them do their jobs on a good day let alone have them do something as outrageous as mandate the technically impossible.
You fool. You rely on the government all the time. You only don’t realize it most of the time because you take it for granted. Just ask the citizens of Puerto Rico who are now victims of the most incompetent and corrupt government in US history, even compared to GWB. You haven’t by any chance voted for the “successful businessman” now running the US into Third World status have you?
Back to data security: Europe has shown the US how to do this right, by establishing legal rights of citizens over their data and fining corporations for violations. They don’t have Equifax and they don’t have the kind of scandals that Americans now seem to be taking granted on a daily basis, because apparently they prefer their government run by the plutocrats instead of regulating the plutocrats.
Starting a response with “You fool” is foolish itself, even more so when the argument you go on to make proves the very point Neil was making.
The important piece here was the line, “Hard enough to have them do their jobs on a good day let alone have them do something as outrageous as mandate the technically impossible.”
Note the “technically impossible” part. Essentially what would happen if legislation was passed requiring code to be perfect before it was sold or distributed, which is the only way to prevent security patches, is no code would ever be sold or distributed, except by charlatans (who don’t care about the law).
It’s a good response to the previous post, which as was noted, was hopefully facetious.
When you begin your retort with “You fool”, you’ve already lost your credibility. Then by injecting inaccurate and inflammatory political commentary into your argument, along with praising the Europe for “showing the US how to do it right”, you’ve lost the argument. If you want to debate politics with like minded autists, head on over to /pol/ on 4chan. This forum is for technology and security. Also, get over it. Trump won. He is your President for the next 7+ years. Make America great again by not posting on here, “TM”.
Please, everyone: Stop feeding the trolls! They are not here to contribute to the discussion, but to muddy it and to divide readers here. I don’t have the time to moderate the increasing number of trollish, OT comments, so please just stop responding to these nitwits. Thank you!
Your idiotic political comments notwithstanding, you’re also wrong about Europe and Equifax:
A. European countries have robust private and public credit-worthiness databases of individuals and corporations. There is great variety in financial information privacy within EU and outside EU among European countries.
See the book “Financial Privacy” by Nicola Jentzsch (2007):
https://books.google.com/books?isbn=3540733787
2. Equifax has about 20 European subsidiaries, including a dozen in Luxembourg alone. You can bet these don’t exist just to shuffle coins around:
https://www.sec.gov/Archives/edgar/data/33185/000003318517000008/a2016exhibit211.htm
So your suggestion? Rely on the market? Go live in a tree? The only real solution is for society to demand the government reign in companies on how they handle data, report breaches, and to hold them civilly and criminally responsible for not doing so. A lack of regulation and enforcement has brought us exactly to where we are. We won’t recover from and prevent its continuation without legislation, enforcement and penalties.
Republicans in Congress are too busy “protecting” fetuses, and their chances for re-election. A tale is told that somewhere way down the list is protecting citizens and the nation.
Can we assume that if the name of the Employer(s) does not come up in the database (https://secure.theworknumber.talx.com/twneeer/PreAuthenticated/EnterEmployerSearchCriteria.ascx?ReturnUrl=%2ftwneeer%2femployee%2fpostauthenticated%2fapplicationsequenceerror.ascx )
that data from that company is not being collected by Exuifax for the specific time period while one worked at that unlisted company?
I do not see any of the companies that I worked at for the last 20 years appear. Am I safe from this ploy?
Good question. I think if the company is not in the system then they are not actively sharing information into that system. Then again, there is the possibility that because it’s Equifax, who has everything and collects everything, like Facebook’s ghost accounts, you probably have a file even if you’ve never worked for a participating company, and if a prospective employer goes looking for it, they’ll find it.
There are other online employment verification systems that companies use, but work number is the most popular. If you work for the government you are not on work number. If you work at a large multistate company you probably are on work number. If you work for a smaller company you most likely are not on work number. Most employers do not use a salary pin key, which is the safer option. I’m not going to go into it’s default settings. Rule of thumb, I’d call your current and previous employers and ask. I’d put a credit freeze on all three bureaus. Save your pin info. Most states have it set to free or 10 bucks per trade line, but you can look up that info. Work number to my knowledge has no opt out. But, hey try calling and asking cause previous employment income breakdowns shouldn’t be needed. Only current and to be honest half the time it’s inaccurate. HR should fill out the Fannie Mae employment verification anyways. I think it’s abour time for the Cfpb and the irs to have a baby and call it the one credit bureau to rule them all and ditch these private business bureaus where the consumer is a product to be bought and sold.
As usual Brian, a great and very informative article. I followed your guidelines and got as far as the pin entry. The birth date information didn’t work, however the “forgot your pin” link allowed me change it with minimal information. These Equifax clowns really do not have a clue. We would love to hear about your thoughts on the Smith testimony before the senate banking committee and if you think that our illustrious congress is going to step up and get these clowns under control.
You were luck (or unlucky) as the case may be. I could not get the right format for my employer’s PIN nor could I re-set my PIN. By evidence of my employer even being in the database and me getting that far means a bruteforce attack be levied upon the site, even with the laughable 3 tries and your out per session.
Well that was frighteningly easy to get access to. I have reset my PIN based on my previous employers code. Several of the pop-up windows complained that Flash was not installed but redirected to non-Flash pages.
I’m happy to see my current employer does not use the system.
Off topic bit, is this story laughable, unbelievable, can’t fix stupid, or what….
https://www.fbo.gov/index?s=opportunity&mode=form&id=ea6f7d2c319f384e03e24ba0bdfad389&tab=core&_cview=0
Transaction Support for Identity Management, awarded to Equifax….?!
IDK…..
Sad but true. Re-surfaced in the news a couple of days ago. It was sole-source as well. But it’s OK – Congress is right on top of this (sarcasm). Frpm 10/3/17 Politico:
“Lawmakers on both sides of the aisle blasted the IRS decision.”
“The IRS defended its decision in a statement, saying that Equifax told the agency that none of its data was involved in the breach and that Equifax already provides similar services to the IRS under a previous contract.”
“Reps. Suzan DelBene (D-Wash.) and Earl Blumenauer (D-Ore.) separately penned letters to IRS Commissioner John Koskinen demanding he explain the agency’s rationale for awarding the contract to Equifax and provide information on any alternatives the agency considered.”
“I was initially under the impression that my staff was sharing a copy of the Onion, until I realized this story was, in fact, true,” Blumenauer wrote.”
That should make you sleep easier.
The IRS justification for going through with it?
“IRS chief John Koskinen argues that the circumstance was unavoidable. Not awarding the contract, he writes, would have prevented thousands of hurricane victims from obtaining much needed…. tax information.”
…and adversely effect his ‘investment’ in EFX
I should also note that the change confirmation email from Talx is terribly generic, giving no indication of who it is from or what it is about other than the sender domain of Talx.com. No mention of “TheWorkNumber.com” used in the site URLs. The EV SSL certificate identifies the site as Talx Corporation, but that is only seen on the MAIN site https://www.theworknumber.com/, not on the login pages which are on https://secure.theworknumber.talx.com/ with only a standard SSL certificate
Example email:
From: “pim confirmation”
To: “Lastname, Firstname”
Date: 8 Oct 2017 15:57:06 -0500
Subject: Personal Information change notification
Firstname Lastname has made changes to the following Personal Information fields:
User Email
MSG ID: Pd999Xxxf4-9999-99c9-a000-00000000bb
For what it’s worth, Norway already has a government website designed for people to be able to look up anyone’s salary.
I’m continually surprised that salary information is considered sensitive. As a federal government employee, my salary is a matter of public record and is easily obtained through the Internet, knowing nothing more than my name and my work location:
https://www.fedsdatacenter.com/federal-pay-rates/
Maybe the secrecy about salary is the REAL problem here?
Salary secrecy is likely one method private employers yse to suppress wages.
Most people in the private sector know what they’re worth, but some people are better negotiators and get a better salary.
I’m not one of those people but I’d rather my coworkers not know exactly what I make. Or marketing people at Nissan. Or any number of nefarious actors out there. My salary, my personal info.
The point here is not so much knowledge of your salary, but more than this now serves as a targeting list. The data breach gives everything the hackers need to automate the collection of the salary details for the PII they stole. That data combined tells them that Person X who makes $200K a year is perhaps a better target than Person Y who makes $20K a year. What’s more, it very well could be exposing Federal employees who work in sensitive fields (i.e. their neighbors and colleagues don’t know they are Federal employees).
Only one of my previous employers appeared in the list and I couldn’t get in with any PIN format. Seems they woke Gus up to come in on a Sunday and turn this off.
Still, this cannot possibly be called incompetence. Equifax seems to WANT to be breached so they can make money off the fallout. That’s the only way to explain this.
Regarding Equifax looking to profit off all this, I keep thinking the same thing. But then I always come back to “never attribute to malice that which is explained by stupidity.” Either way, (facepalm).
How Equifax Is ‘Making Millions of Dollars Off Its Own Screwup’
http://fortune.com/2017/10/04/equifax-breach-elizabeth-warren/
Easy as pie. Thanks Brian. Look up for former employer code, DoB as PIN gave me access to former employer’s site info for me. Changed default PIN and six nonsense security question answers. Appreciate your investigative journalism. Once again, Brian, kudos!
You do realize, I hope, that you are training folks to enter personal data into websites they gave never heard of, based on a single scary article… While I understand the goal of showing folks how to close holes they’ve never heard of, I would be much happier if you could somehow coordinate this with other respected authorities so we could authenticate it.
I respect your reputation, but that really shouldn’t be enough by itself. Someone could have fed you bad info, or spoofed your site. _Anything_ on the web needs to be treated with some skepticism.
I think that Brian’s reputation is well more than enough to trust the links he has.
You haven’t been around here long if you believe that someone ‘feeding’ him bad info would ever make it into one of his articles. That’s a laughable idea.
BTW, the news cycle is generally one blogger makes some garbage up then everyone reports it as truth. I’m not sure what secondary outlets you could use to ‘verify’ some info, anyway, when Brian’s reputation is pretty much at the top of the food chain when it comes to this stuff.
Felix,
This isn’t a new site or service. It’s been around for many years, and this isn’t the first time someone has called attention to it.
https://www.nbcnews.com/technology/exclusive-your-employer-may-share-your-salary-equifax-might-sell-1B8173066
I’m guessing you’re not a regular reader here, or you would know I don’t just go around pointing people to visit random sites and enter personal data.
Wonderful. My employer has at least used something other than my DOB as a PIN. It’s not my “payroll number,” either. I haven’t tried my employee number because three strikes and out. I’ll try it tomorrow.
found former employer but could not get in. tried both dob formats. no go. so either my employment is before the existence of talx or my old employer used a different pin format. scary.
Wow, some of those pages have meta tags from Visual Studio 2003:
meta name=”GENERATOR” Content=”Microsoft Visual Studio .NET 7.1″
Equifax is aptly named. Your facts are equally available to anyone who wants to steal it.
I wish congress critters would read Krebs on Security and get regulating mad. Unfortunately we have the best congress money can buy, and certain companies that are almost unregulated have done the buying.
If equifax sold information like I think they did and tried to cover it up by selling social security numbers by allowing it to look like a security breach not only should they be prosecuted but I am willing to file a class action lawsuit and sue the hell out of equifax for breach of duty. Anyone else feel that way. They have to come to justice.
I agree!
I’m too late trying, it seems. The website is down for “maintenance” now. I don’t have much hope it will be accessible (by me) when it comes back up.
Unrelated thought: if Equifax has a service where employers can report salary information (without knowledge or consent of employees – grrrr!), I’d have to assume TransUnion or Experian might also. Anybody know anything about that?
Why wait for that? The fact that they were completely unprepared to respond to a breach is unforgivable, given the data they manage.
The Talx site for looking up your employer’s Work Number says:
“Important System Maintenance Notice
We are currently completing system maintenance in the area you tried to access.
We apologize for any inconvenience but we believe that proper system maintenance is critical to bring you the industry-leading service you have come to expect. We will return to business as usual very soon.”
Wonder what they’re up to?
Interesting that it says ‘scheduled maintenance’. Scheduled when, 10 minutes after this article was posted?
“Counting on the government to solve your problems is no way to live.”
And yet literally just about everyone everywhere does that, and it works to some degree. What’s your alternative?
Magic rhetorical bootstraps? More tax cuts for the 1%?
Libertarian anti-legalism neckbeards have no solutions.
Reagan-bathtub conservatives have no solutions.
We CAN have a government that mandates security practices for personal information vendors, yes we can. It’s not even that hard. Stop pretending nothing ever works. Wrong!
Teeth. Fines. Rigorous enforcement. REGULATIONS. Yes, we expect the government to solve some problems.
All we have to do is STOP SELLING OUT TO DEREGULATOR FRAUDS, people selling a small government that does nothing and upholds no standards ARE WISHFUL FOOLS who should be forced to live elsewhere and be as lawless as they wish there.
But here? WE WILL HAVE REGULATIONS. Anyone NOT on board with the rule of law, GTFO now please. Last chance.
Security doesn’t fail this bad in a vacuum, it was allowed to.
Too big to fail does NOT apply to data brokers who can’t even change their VPN passwords from admin/admin.
If we want to pretend no standards can be enforced and nothing can ever work, that’s nihilism. That’s giving up.
Teeth, spoken like a true Democrat.
Spoken like somebody with a functioning brain. Is “true Democrat” the American synonym for “not dumb”?
Whoever, spoken like a true-believer Rethug.
The problem with politicians solving problems is they don’t have any particular skill or experience in solving these problems.
The only reason they’re in the position to “solve problems” in the first place is they managed to convince, conspire with, or coerce enough people to give them money, so they could become politicians.
The only solutions they will come up with are those that will line their pockets.
They don’t work for the people. They work so the people will continue to give them money.
So let’s get this straight, pretty much this company has had a major breach, or worse, orchestrated a black market sale or transfer of data and marketed it as a breech and I’m suppose to go check at Equifax and give them more information, and now do it again?
Sorry, but this just seems stupid. If we can’t fully understand the loss, transfer, or sale of data and the infrastructure still most likely is insecure and still comp’d, why would you keep using their site and provide information they maybe didn’t have or get?
The whole damn company should be in prison, particularly the whole executive board. Some folks in the Whitehouse need fired and jailed too.
*Subtle reminder, our chief of staff just had to mention credit ratings disappearing in Puerto Rico to affect their bond market. Think about the consequences of that in the US.
Looks like they’ve took the site down
https://www.talx.com/maintenance.asp
.asp? Not .aspx? Is that web site REALLY just a .asp web site?
Yep, still down (12pm EST). And oh neat-o — yet another obscure domain name “talx.com”… Go Equifax go!!!
And http://www.talx.com redirects to http://www.equifax.com/business/manage-my-workforce, which won’t load.
Yup, in “maintenance mode”.
I tried to access https://secure.theworknumber.talx.com/popups/findEmployer.aspx?searchcriteria= and it seems to have been taken offline. I guess that’s good news.
Well, it would appear that your articles are continuing to do good work, because the sites in question have been pulled down for “maintenance”. Thank you, as always, for shedding light on issues we all need to be aware of in order to protect ourselves!
The Work Number has been around for many years. I first heard of it over 7 years ago when I began my federal employment. Krebs knows what he’s talking about here.
I was able to access the site before it went down for “maintenance”. All I needed was my employee code and my social! The user ID was my social and the PIN was the last four of the social! That is truly unacceptable in my opinion. Once in though you had to verify some things pertaining to your credit history for added verification. This adds very little to security as the answers could be easily guessed. Also, at the time I got it, they were allowing you to reset your PIN using both letters and numbers from 4 – 16 characters.
I bet they took the site down once they found all the traffic was coming from Krebs site! Good work Brian!
Both the Equifax sites linked in the article are displaying “Important System Maintenance Notice
We are currently completing system maintenance in the area you tried to access.
We apologize for any inconvenience but we believe that proper system maintenance is critical to bring you the industry-leading service you have come to expect. We will return to business as usual very soon.
Please see http://status.equifaxworkforce.com for further updates.”
At this point, I guess I’m glad it is offline, but they should be taking forensic images of everything involved in this and looking for MORE breaches based on the access granted by the site in the article. “fixing” the security at this point is a bit like closing the barn door after the horse has bolted.
Seems to be down for Maintenance now… hmmm…
Great report Brian. Looks like they posted on Oct. 3rd that the system would be taken down for maintenance on Oct. 14th. I think it is very telling that the site is now down for maintenance 5 days early and within 24 hours of your article.
With Equifax being revealed as a house of cards, I wonder what the other 3 CRAs (including Innovis) are doing now? Are they also scrambling to “fix” their systems before they are exposed themselves, or are they feeling vindicated? Time will tell.