Equifax Inc. said today an investigation into information stolen in the epic data breach the company disclosed on Sept. 7 revealed that intruders took a file containing 15.2 million UK records. The company says it is now working to inform 693,665 U.K. consumers whose data was stolen in the attack.
 Previously, Equifax said the breach impacted approximately 400,000 U.K. residents. But in a statement released Tuesday, Equifax said it would notify 693,665 U.K. consumers by mail that their personal information was jeopardized in the breach. This includes:
Previously, Equifax said the breach impacted approximately 400,000 U.K. residents. But in a statement released Tuesday, Equifax said it would notify 693,665 U.K. consumers by mail that their personal information was jeopardized in the breach. This includes:
-12,086 consumers who had an email address associated with their Equifax.co.uk account in 2014 accessed.
-14,961 consumers who had portions of their Equifax.co.uk membership details — such as username, password, secret questions and answers, as well as partial credit card details — accessed
-29,188 consumers who had their drivers license numbers accessed
-637,430 consumers who had their phone numbers accessed
The numbers include data that Equifax held on U.K. consumers as far back as 2011, the company said. Equifax did not say whether any of the above-mentioned data was encrypted.
Meanwhile, the U.K.’s National Cyber Security Centre is warning residents to be on their guard against phishing attacks made to look like communications from Equifax about the breach.
“Another risk to UK citizens affected by this data breach is that they could be on the receiving end of more targeted and realistic phishing messages,” the NCSC wrote. “Fraudsters can use the data to make their phishing messages look much more credible, including using real names and statements such as: ‘To show this is not a phishing email, we have included the month of your birth and the last 3 digits of your phone number’. These phishing messages may be unrelated to Equifax and may use more well known brands. It is unlikely that any organisations will ask their customers to reset security information or passwords as a result of the Equifax breach, but this may be a tactic employed by criminals.”
ANALYSIS
Equifax has been widely criticized for continuously bungling their public response to this still-unfolding data disaster, and today’s update about the extent of the breach in the U.K. was no exception. The Equifax Web site that hosts today’s press release serves “mixed content,” meaning it includes elements that are served over both encrypted and unencrypted pages. The practical effect of this varies depending on which browser you’re using, but some browsers will display a security warning when this happens.
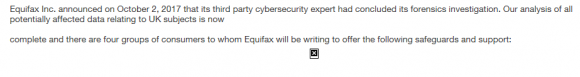
That mixed content error may have something to do with a missing image in the press release. That press release was supposed to include an image that breaks down what exactly was stolen from U.K. residents — as detailed in the bulleted list above — but apparently the graphic was either removed or moved pre- or post-publication. Here’s what the press release looks like in Firefox (Equifax still hasn’t fixed this):

In Chrome:
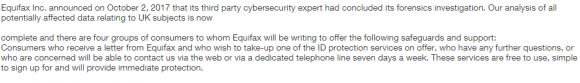
In Internet Explorer:
It’s fairly terrifying when you realize that a company which can’t even issue a press release without managing to omit the most important piece of information in it wields so much power over consumers. Nothing says ‘we care about your security and privacy’ like a message which warns “you got hacked!” and then fails to tell you what that actually means.
I’ve been spending quite a bit of time looking at Equifax’s various Web properties over the past few weeks and I have to say it gets scarier the more I look. First it was the discovery that Equifax’s consumer dispute portal in Argentina was protected by nothing more than the username and password “admin/admin.” It’s worth noting that, as mentioned countless times by Equifax’s former CEO in front of several congressional committees last week, the breach of sensitive data on 145.5 million Americans began with lax security at just such a dispute portal (the company declined to say which).
Earlier this week I pointed out that the company’s TALX Web site made it trivial to find the salary history of large chunk of the American population, armed with nothing more than someone’s date of birth and Social Security number (both data points, by the way, that were stolen on 145.5 million Americans, thanks to Equifax). The company responded by taking the site offline a few hours after that story ran on Sunday. That site is still “under maintenance,” according to Equifax.
While Equifax has stressed that it will offer free credit monitoring services to victims of its own breach, it is still using the entire incident to drive traffic to areas of its consumer business that make the company oodles of money, such as “FREE* credit report & score” services for only £14.95 per month. It’s impossible to understand how Equifax could fail to notice the atrocious optics here, unless of course it really doesn’t care.
By the way, if you’re somehow just tuning in to news about this breach, don’t sweat it: Here’s a Q&A that explains what’s at stake and what you should do.




Great article , Thanks !
Even though I am not surprised ab0ut this story or the way it is going (Thank you Brian for the continuing updates) you can’t help but be flabbergasted with it even so..
Keep up the good work here and keep the tweets coming..
I think it’s safe to assume that pretty much anything Equifax had was taken; regardless of what they’ve reported.
I wonder how many of their IT staff have been offshored and/or replaced by H1-B visa slaves…
More than likely it’s not that their IT was offshored, but more that they just consider IT a drain to profits, which are much better spent on executive perks and bonuses. There are probably very good administrators and other staff members in their IT group, they just don’t have the ability to make the decisions and actions necessary to give the company any degree of security.
Hopefully, stories like this will urge Congress into acting on companies like Equifax, though at this point I don’t see any real reason why they should even be allowed to stay in business if this is the manner they protect their assets, which are OUR personal information.
I’m curious but too lazy to search….. do the British have the same sort of credit bureau freeze option as Americans?
Secondly — and off-topic — might we get a Krebs perspective on the allegations found in today’s NYT about Kaspersky Labs hacking the US for Russia, and will any previous KOS articles need to be updated?
No credit freeze option in the UK so with all this information floating about not long until it’s commonplace for someone to take out a line of credit in your name 😐
Thank you for the answer, mace.
The UK is still in the EU (European Union). I would hope that this will be the start of that whole industry being regulated. EU data protection laws coming into force next year require websites and companies to clearly explain to end users their rights relating to their data (as per http://ico.org.uk/media/for-organisations/documents/1624219/preparing-for-the-gdpr-12-steps.pdf , page 4, step 4)
– to be informed what my data will be used for
of access to all my data
– to rectification (data will be corrected if not accurate or outdated)
– to it being erased
– to it’s strict processing
– to data portability
– to object to how it’s being used
– not to be subject to automated decision-making, including profiling
Yet in the case with the 3 big credit score companies, the user seems to have no rights about how their data is used: the user is the commodity being sold. Reform is way overdue.
More pay-to-play protection? This rogue entity should be shut down and those involved fined and imprisoned for ten-years minimum. However, everybody goes home. Sloppy business as usual.
It’s shocking to see how incompetent E****** is.
But let’s not heap all the blame on IT (tho they deserve the lion’s share). The Communications/PR staff is pathetic if their handling of press releases, website postings and customer communications is this bad.
Of course, they’re likely handicapped by E******’s lawyers, who are surely blocking any meaningful actions in order to do everything they can to protect the company from taking any responsibility whatsoever.
What a pathetic collection of incompetents…
Given the quality of the Equifax response so far, I wonder if there _may_ be a further discrepancy in the numbers.
The UK’s National Cyber Security Centre issued an updated release yesterday identify 15.2 million records. Whilst one record may not necessarily equate directly to one consumer, the discrepancy is rather large.
https://www.ncsc.gov.uk/news/ncsc-advice-equifax-customers-0
“Equifax has today confirmed that a file containing 15.2m UK records dating from between 2011 and 2016 was attacked in the cyber incident that took place in May 2017”
Steve,
That NCSC alert and a link to it are included in the story.
Thank you for your excellent reporting, Brian. I am leaving a donation for your work shortly, as I hope others will do. We can’t count on the government to protect us and certainly not the corporations operating these schemes. I just froze all 4 of the credit bureaus my spouse and myself (you have to do both if applicable! And your kids). It was not hard to do, it took under 60 minutes all together. Most just ask if for SS# and address and birthdate. TransUnion required a log-in to be created and charged $10. Experian charged $5. I gritted my teeth and paid the fees. Equifax was free. Innovis asked if I was a victim of ID theft or not. Figuring we are ALL victims now, I checked YES and was not asked for any documentation of theft, nor charged a fee. Total cost for 2 people: $30. Each agency gives you a pin number to use for locking/unlocking in the future. Don’t lose it.
I would like to know if anybody has received a letter from Equifax informing them that they are a victim of the breach.
Anybody?
They promised the US, UK and Canadian governments that they would do this. I assume Americans will come first – 143 million letters. That will take some time. Followed by 700,000 Brits, followed by 8,000 Canadians, followed by some unknown number of Brazilians. Some guy in the mail room at Equifax had better get this right or he will be blamed as the single point of failure in their latest attempt at dealing with the public at large.
No letters yet among the people I know who were affected.
I’m in the UK and had an Equifax account in 2015, and thought it’d be worth logging in and changing my password (OK, the horse has bolted, but nevertheless).
I couldn’t recall my existing password on Equifax’s site, so went through the “change password” process. But this process only requires the entry of information that apparently was already stolen by the hackers !
For example, there’s no step where a confirmation link is sent to the previously known email address. They do inform you via email afterwards that the password has been changed, but then it’s too late if it was being done by someone unauthorised.
I think this just underlines how lousy Equifax’s diligence was and still is in this area.
Brian,
The Experian credit bureau *still* allows anyone to reset your credit freeze PIN using your DOB and SSN (which were leaked). https://www.experian.com/ncaconline/freezepin
Doesn’t that invalidate the whole concept of credit freeze?
Should we avoid freezing our credit at Experian?
Can you contact them and talk some sense in their thick head?
Even though the pin can be reset with DOB and SSN, I think its still worth the 5-10 minutes and $10< fee to do so.
To me what you are saying makes perfect sense, and it definitely lessens the effectiveness of the freeze. However, in order to avoid being the low hanging fruit in this situation, making an identity thief go through a few extra steps may be enough of a deterrent to make them choose a different target.
Unfortunately, at this point I think these companies are fully aware that this is a broken system. But they will continue to do things the same way until the punishment for leaking sensitive information outweighs the costs associated with properly securing our information.
Hi Fred, I froze all 4 bureau files. Rather than take the chance that the one I “didn’t” freeze is the one that gets used. I also would inquire about a lawsuit against Experian if someone else unfreezes my files. The suit would claim poor security on Experian’s part allowed the hack of my account and in light of all that is going on, I think I’d have a good case.
As to Leo’s question. I read an article two days ago that said Equifax would notify people but the article implied that it would be those whose dispute info was leaked (or something other than the main hack) that would be notified. So far I’ve gotten no ltr from Equifax telling me I was involved in the breach. They still haven’t confirmed my freeze at Equifax by mail either.
I’m more worried about my ID being used this tax season. We have over three months to go till the usual Jan 31 filing time (although many people file earlier). How ’bout the IRS giving “all” of those who’ve previously filed taxes a IP pin number? For paper and online filing.
Even if the IRS must get approval from Congress to do so, it’ll be way cheaper to give everyone a pin now versus paying billions out in fraudulent tax refunds which they (we!) do every year.
The great coverage on this is very much appreciated Krebs. If only more people understood the morality and ‘negligence’ involved in all this. Seems more likely the Federal gov is just going to bail them out and excuse their ‘negligence’ which is clearly criminal and should spell the end of their business as it exists today… You had one job Equifax… One job.
its,obvious.fact.that,carders,crooks.doing.rather,credit.based,jobs,instead-of-stealing.obvious.