KrebsOnSecurity recently featured a story about a New Mexico man who stands accused of using the now-defunct vDOS attack-for-hire service to hobble the Web sites of several former employers. That piece stated that I wasn’t aware of any other prosecutions related to vDOS customers, but as it happens there was a prosecution in the United Kingdom earlier this year of a man who’s admitted to both using and helping to administer vDOS. Here’s a look at some open-source clues that may have led to the U.K. man’s arrest.

Jack Chappell, outside of a court hearing in the U.K. earlier this year.
In early July 2017, the West Midlands Police in the U.K. arrested 19-year-old Stockport resident Jack Chappell and charged him with aiding the vDOS co-founders — two Israeli men who were arrested late year and charged with running the service.
Until its demise in September 2016, vDOS was by far the most popular and powerful attack-for-hire service, allowing even completely unskilled Internet users to launch crippling assaults capable of knocking most Web sites offline. vDOS made more than $600,000 in just two of the four years it was in operation, launching more than 150,000 attacks against thousands of victims (including this site).
For his part, Chappell was charged with assisting in attacks against Web sites for some of the world’s largest companies, including Amazon, BBC, BT, Netflix, T-Mobile, Virgin Media, and Vodafone, between May 1, 2015 and April 30, 2016.
At the end of July 2017, Chappell pleaded guilty to those allegations, as well as charges of helping vDOS launder money from customers wishing to pay for attacks with PayPal accounts.
A big factor in that plea was the leak of the vDOS attacks, customer support and payments databases to this author and to U.S. law enforcement officials in the fall of 2016. Those databases provided extremely detailed information about co-conspirators, paying customers and victims.
But as with many other cybercrime investigations, the perpetrator in this case appears to have been caught thanks to a combination of several all-too-common factors, including password re-use, an active presence on the sprawling English-language hacking community Hackforums, and domain names registered in his real name. In combination, these clues provide a crucial bridge between Chappell’s online and real-world identities.
A simple search at domaintools.com for the name Jack Chappell and “UK” returns a handful of results, including the domain fractal[dot]hf. That domain was registered in June 2015 to a Jack Chappell in Stockport, using the email address me@jackchappell.co[dot]uk [full disclosure: Domaintools is an advertiser on this site].
Neither domain is online anymore, but a Google search on fractal[dot]hf reveals several mentions of this site on Hackforums — a sprawling English-language forum that until very recently hosted the most bustling open-air market for competing attack-for-hire services.
According to a review of those Hackforums postings, fractal[dot]hf was a free service that allowed users to test the size and impact of any DDoS attack tool — displaying detailed graphs showing how much data a given attack tool could hurl at an intended target. Multiple forum members told interested users that fractal[dot]hf was owned and operated by a friendly and helpful Hackforums user named Fractal.
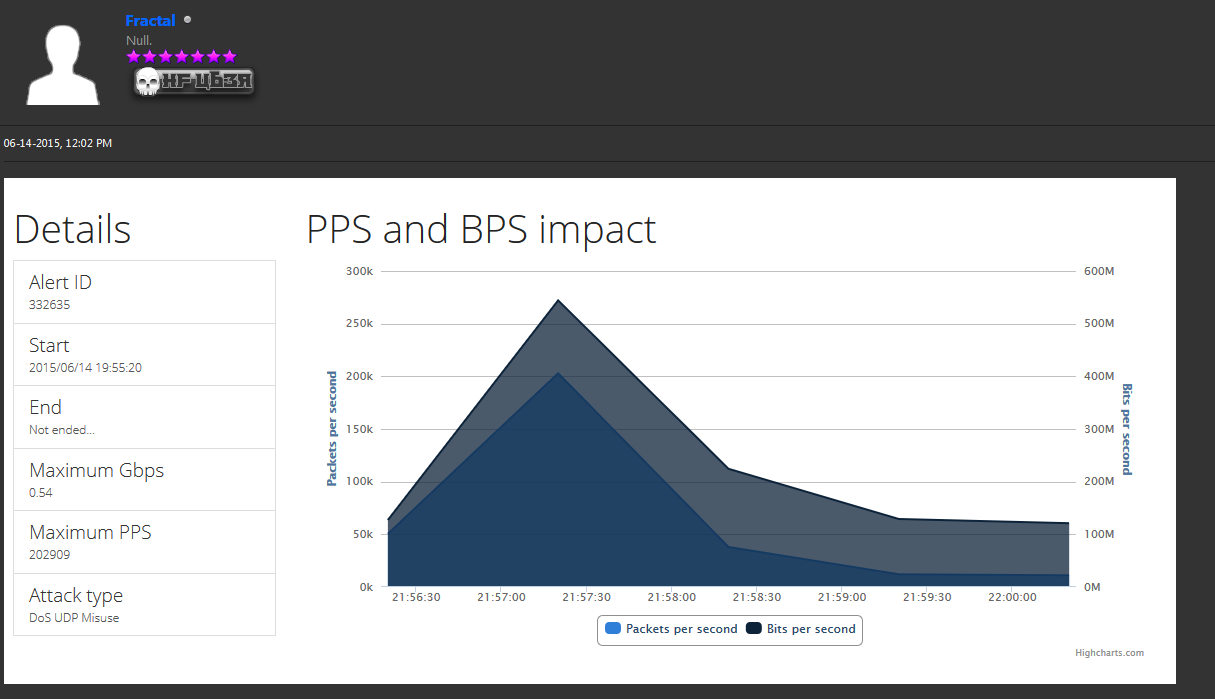
A screenshot of the user Fractal advertising his service for measuring the size of attacks. Fractal posted this graphic to illustrate the power of an IRC-based botnet that was being sold on Hackforums in mid-2015.
Perhaps unsurprisingly, there was a very active user on vDOS who went by the same Fractal nickname, using the password “HelloWorld1998” and email address smellyjelly01@gmail.com.
The above-mentioned domain Jackchappell.co[dot]uk appears in the leaked vDOS payments database, which states that a PayPal account tied to the email address “paypal@jackchappell.co[dot]uk” was one of several PayPal accounts used to launder customer payments for online attacks.
As noted in my June 2017 piece Following the Money Hobbled vDOS Attack-for-Hire Service, vDOS was forced to round-robin customer PayPal payments through a series of accounts after academic researchers began signing up for a variety of attack-for-hire services (including vDOS) and then reporting to PayPal the email addresses tied to accounts being used to receive payments.
The paypal@jackchappell.co[dot]uk address was linked to a vDOS user account called “portalKiller” which used the password “HelloWorld8991.” Note that this password is very similar to the one used by the vDOS user Fractal — only the numbers at the end of the password have been reversed (1998/8991).
Portalkiller changed his password several times during his time on vDOS, and one of the passwords he used was “Smith8991.” An Internet search on this password turns up an account in the user database that was hacked and posted online from a similar attack-for-hire service previously run by a hacker group known as the Lizard Squad. The email address tied to that account? Smellyjelly01@gmail.com.
From reviewing Fractal’s posts and reputation on Hackforums it appears that on Dec. 28, 2015 his account received praise and positive reputation points (similar to eBay’s user “feedback” system) from M30w and AppleJ4ck, the nicknames used by the alleged co-founders of vDOS.
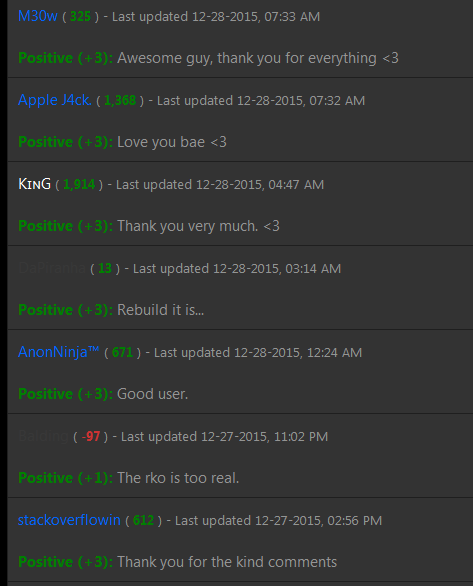
Positive reputation points awarded to Chappell by the co-owners of vDOS, who used the aliases “M30W” and “AppleJ4ck.”
Comments in the leaked vDOS databases also suggest Chappell was for a time one of several trusted administrators and/or support personnel of the service. vDOS routinely banned accounts for members who shared their logins, or who logged on via virtual private network (VPN) services to anonymize their connections, but many members ignored this advice.
For example, in one support ticket dated March 13, 2016, a vDOS subscriber named “Bears” who had his account banned pleaded with the administrators to reactivate (or “unban”) his account.
“Hi jeremy pls unban hi p1st i love you hi AJ i love you hi fractal i love you hi whoever else is support is swagdaddy still support?” Bears pleads.
Ironically, both of Chappell’s accounts on vDOS — Fractal and portalKiller — were ultimately banned, the latter supposedly for flouting vDOS’s no-VPN restrictions. In one customer support ticket, portalKiller explains the reason for his use of a VPN: He routinely used a VPN so that he could tunnel his connection to the United States and watch the U.S. catalog of Netflix videos.
“Account Banned’,85801,’portalKiller’,’Hi, My account was banned a couple of days ago for logging in from a VPN. Let me explain, the 82.132.234.244 IP is not a VPN it is my mobile provider (O2), which is not a proxy/VPN. The second IP was a mistake I made, I logged out and logged back in from my normal IP (81.103.71.50) after I noticed my VPN was on (I use it for Netflix). I really want you to re-consider my ban. Thanks, portalKiller.”
Fractal also was eventually banned from using vDOS, although it’s less clear why that account was banished. Perhaps Chappell no longer offered the ability to help the other vDOS administrators launder funds, or maybe he had a falling out with M30W/p1st and AppleJ4ck.
Chappell did not respond to requests for comment. His sentencing has been delayed several times since his guilty plea; it is currently slated for December 2017.
Chappell’s guilty plea reminds me that there are many others who helped launder funds for vDOS that are in all likelihood similarly exposed. Stay tuned for more updates on that front.




Good read
I cant get past “AppleJ4ck” and “Jack Chappell”
Chappel Jack…
i know allegedly different people but still oddly similar…
https://vdos-s.co/
is it possible that the service came back ?
One falls and another will take it’s place. Always. Just another copycat at best.
it is related to strong-stresser.com, direct link on the footer was added between may and september 17.
some advertising started 18.10.2017 with the nicks
Welsh92Kloster
neville07welsh
Kloster88Rosendal
..looks a bit like name reuse to me
Another ginger in trouble.
Good move
Thanks for sharing this hot scoop on vDOS and Jack Chappell.
$600,000 in two years is a lot of money! While vDOS may no longer available, it may motivate someone else to create another DDOS program to do what vDOS did. I feel some details are better left out when reporting hacking stories.
Important questions to consider:
1.) Is the hacker made a hero?
2.) Did he benefit from the time he was a hacker?
3.) Does the article offer a solution to the problem?
$600,000 in two years is a lot of money…. but it’s not profit. It’s revenue. He was probably spending a fortune on server costs and chargebacks via paypal, not to mention, I’m sure it was not only 1 person involved. The profits were most likely split.
So at best, he would have been making $70k-100k a year. He was breaking the law to get to that as well…
What an idiot this guy is and all the others that have been caught because of simple mistakes that could’ve been avoided if they had 0.000001% of a brain. These guys think they’re so smart because they can MEMORIZE (bold that for me krebs, thanks) programming languages or something about computers, yet that always have terrible opsec. Terrible opsec shows that you lack a brain. And who would use any service, created to be used illegally, that doesn’t allow you to use a VPN? Idiots