Past stories here have explored the myriad criminal uses of a hacked computer, the various ways that your inbox can be spliced and diced to help cybercrooks ply their trade, and the value of a hacked company. Today’s post looks at the price of stolen credentials for just about any e-commerce, bank site or popular online service, and provides a glimpse into the fortunes that an enterprising credential thief can earn selling these accounts on consignment.
Not long ago in Internet time, your typical cybercriminal looking for access to a specific password-protected Web site would most likely visit an underground forum and ping one of several miscreants who routinely leased access to their “bot logs.”
These bot log sellers were essentially criminals who ran large botnets (collections of hacked PCs) powered by malware that can snarf any passwords stored in the victim’s Web browser or credentials submitted into a Web-based login form. For a few dollars in virtual currency, a ne’er-do-well could buy access to these logs, or else he and the botmaster would agree in advance upon a price for any specific account credentials sought by the buyer.
Back then, most of the stolen credentials that a botmaster might have in his possession typically went unused or unsold (aside from the occasional bank login that led to a juicy high-value account). Indeed, these plentiful commodities held by the botmaster for the most part were simply not a super profitable line of business and so went largely wasted, like bits of digital detritus left on the cutting room floor.
But oh, how times have changed! With dozens of sites in the underground now competing to purchase and resell credentials for a variety of online locations, it has never been easier for a botmaster to earn a handsome living based solely on the sale of stolen usernames and passwords alone.
If the old adage about a picture being worth a thousand words is true, the one directly below is priceless because it illustrates just how profitable the credential resale business has become.
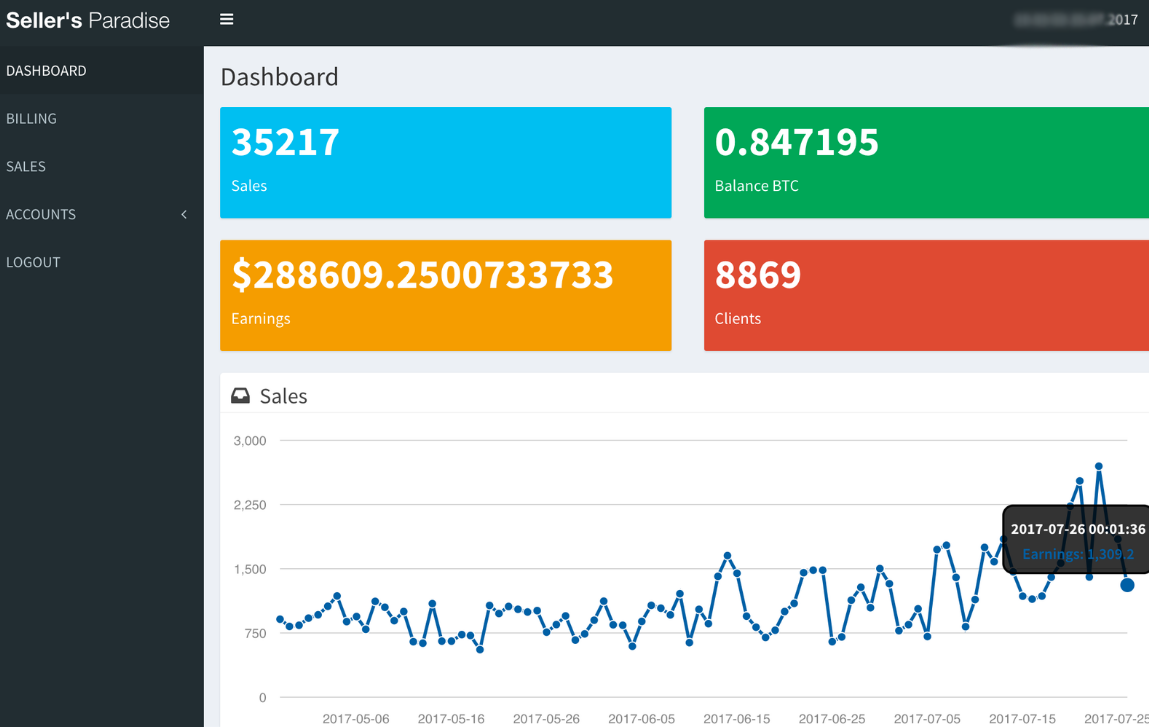
This screen shot shows the earnings panel of a crook who sells stolen credentials for hundreds of Web sites to a dark web service that resells them. This botmaster only gets paid when someone buys one of his credentials. So far this year, customers of this service have purchased more than 35,000 credentials he’s sold to this service, earning him more than $288,000 in just a few months.
The image shown above is the wholesaler division of “Carder’s Paradise,” a bustling dark web service that sells credentials for hundreds of popular Web destinations. The screen shot above is an earnings panel akin to what you would see if you were a seller of stolen credentials to this service — hence the designation “Seller’s Paradise” in the upper left hand corner of the screen shot.
This screen shot was taken from the logged-in account belonging to one of the more successful vendors at Carder’s Paradise. We can see that in just the first seven months of 2017, this botmaster sold approximately 35,000 credential pairs via the Carder’s Paradise market, earning him more than $288,000. That’s an average of $8.19 for each credential sold through the service.
Bear in mind that this botmaster only makes money based on consignment: Regardless of how much he uploads to Seller’s Paradise, he doesn’t get paid for any of it unless a Carder’s Paradise customer chooses to buy what he’s selling.
Fortunately for this guy, almost 9,000 different customers of Carder’s Paradise chose to purchase one or more of his username and password pairs. It was not possible to tell from this seller’s account how many credential pairs total that he has contributed to this service which went unsold, but it’s a safe bet that it was far more than 35,000.
[A side note is in order here because there is some delicious irony in the backstory behind the screenshot above: The only reason a source of mine was able to share it with me was because this particular seller re-used the same email address and password across multiple unrelated cybercrime services].
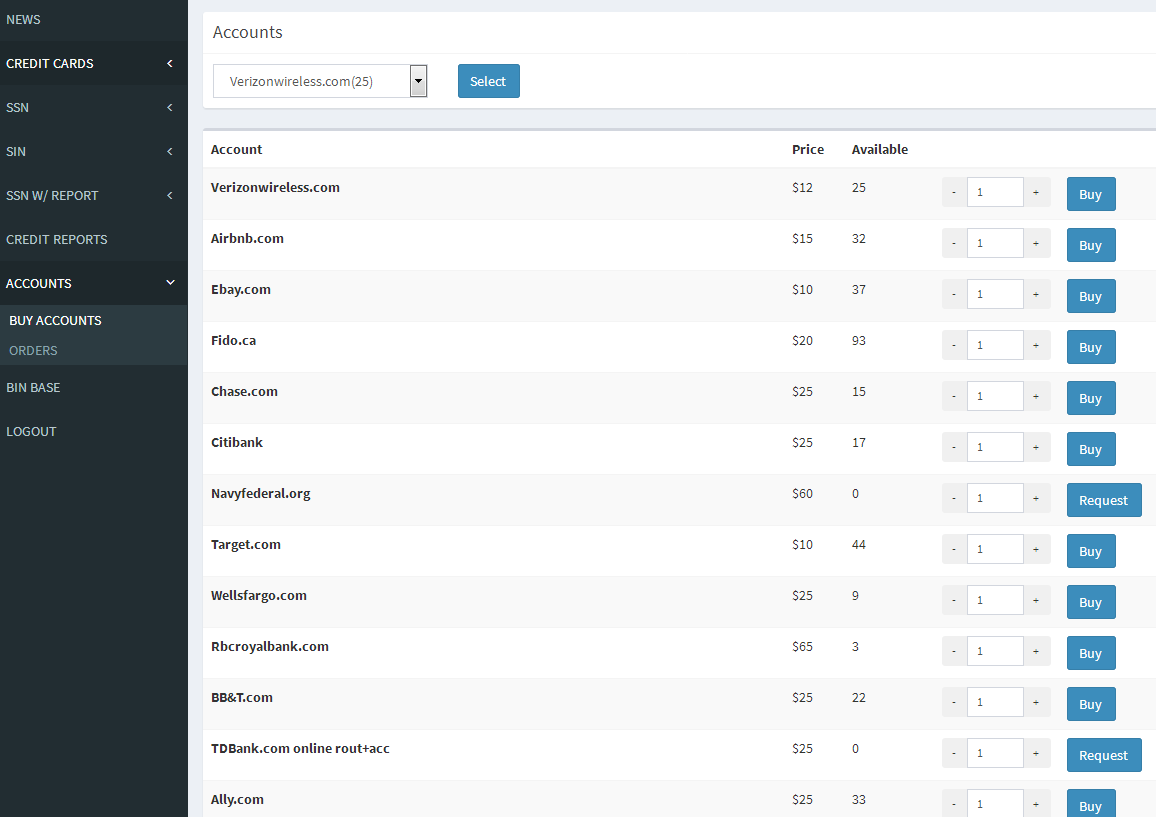
Based on the prices advertised at Carder’s Paradise (again, Carder’s Paradise is the retail/customer side of Seller’s Paradise) we can see that the service on average pays its suppliers about half what it charges customers for each credential. The average price of a credential for more than 200 different e-commerce and banking sites sold through this service is approximately $15.
Indeed, fifteen bucks is exactly what it costs to buy stolen logins for airbnb.com, comcast.com, creditkarma.com, logmein.com and uber.com. A credential pair from AT&T Wireless — combined with access to the victim’s email inbox — sells for $30.
The most expensive credentials for sale via this service are those for the electronics store frys.com ($190). I’m not sure why these credentials are so much more expensive than the rest, but it may be because thieves have figured out a reliable and very profitable way to convert stolen frys.com customer credentials into cash.
Usernames and passwords to active accounts at military personnel-only credit union NavyFederal.com fetch $60 apiece, while credentials to various legal and data aggregation services from Thomson Reuters properties command a $50 price tag.
The full price list of credentials for sale by this dark web service is available in this PDF. For CSV format, see this link. Both lists are sorted alphabetically by Web site name.
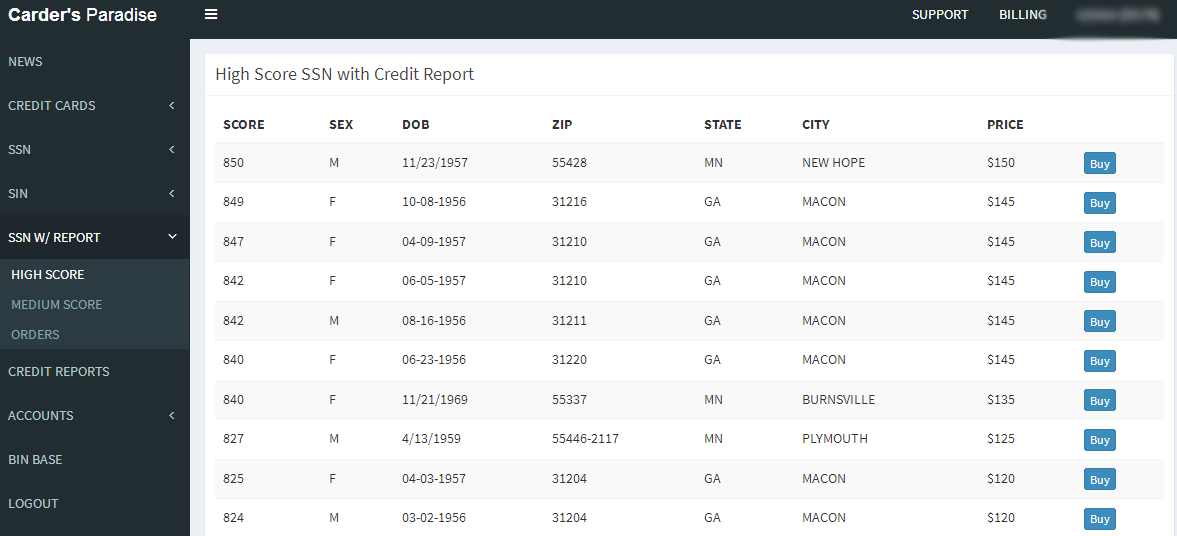
This service doesn’t just sell credentials: It also peddles entire identities — indexed and priced according to the unwitting victim’s FICO score. An identity with a perfect credit score (850) can demand as much as $150.
And of course this service also offers the ability to pull full credit reports on virtually any American — from all three major credit bureaus — for just $35 per bureau.
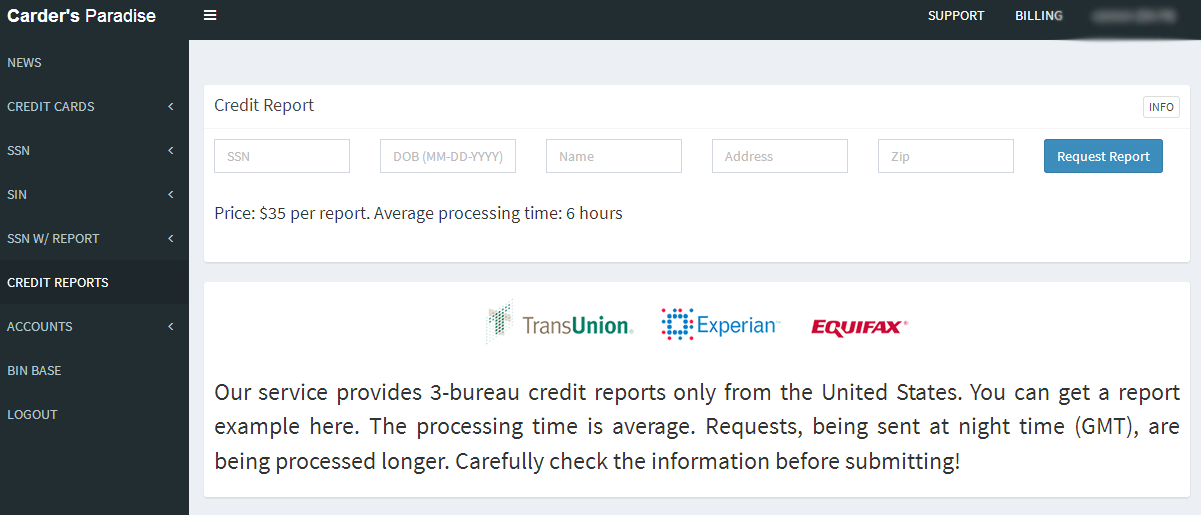
It costs $35 through this service to pull someone’s credit file from the three major credit bureaus.
Plenty of people began freaking out earlier this year after a breach at big-three credit bureau Equifax jeopardized the Social Security Numbers, dates of birth and other sensitive date on more than 145 million Americans. But as I have been trying to tell readers for many years, this data is broadly available for sale in the cybercrime underground on a significant portion of the American populace.
If the threat of identity theft has you spooked, place a freeze on your credit file and on the file of your spouse (you may even be able to do this for your kids). Credit monitoring is useful for letting you know when someone has stolen your identity, but these services can’t be counted on to stop an ID thief from opening new lines of credit in your name.
They are, however, useful for helping to clean up identity theft after-the-fact. This story is already too long to go into the pros and cons of credit monitoring vs. freezes, so I’ll instead point to a recent primer on the topic and urge readers to check it out.
Finally, it’s a super bad idea to re-use passwords across multiple sites. KrebsOnSecurity this year has written about multiple, competing services that sell or sold access to billions of usernames and passwords exposed in high profile data breaches at places like Linkedin, Dropbox and Myspace. Crooks pay for access to these stolen credential services because they know that a decent percentage of Internet users recycle the same password at multiple sites.
One alternative to creating and remembering strong, lengthy and complex passwords for every important site you deal with is to outsource this headache to a password manager. If the online account in question allows 2-factor authentication (2FA), be sure to take advantage of that.
Two-factor authentication makes it much harder for password thieves (or their customers) to hack into your account just by stealing or buying your password: If you have 2FA enabled, they also would need to hack that second factor (usually your mobile device) before being able to access your account. For a list of sites that support 2FA, check out twofactorauth.org.




Excellent research and article Brian. Your efforts are much appreciated by all of us.
More and more, I am beginning to despise logon/password credentials.
Wait for SQRL! https://www.grc.com/sqrl/sqrl.htm It’ll change the world!! (I hope) 🙂
A lot of websites in China already use this sort of system for logins using a smart phone, such as with WeChat/QQ. I don’t know anything about how secure the back end might be.
Although SQRL could be helpful in some use cases, where identity assurance is necessary I feel it falls a little flat.
Many crucial use cases require identity assurance: “the ability for a party to determine, with some level of certainty, that an electronic credential representing an entity (human or a machine) with which it interacts to effect a transaction, can be trusted to actually belong to the entity.”
https://en.wikipedia.org/wiki/Identity_assurance
I do not have a strong belief that SQRL can effectively address identity assurance requirements for many organizations or purposes… yet.
SQRL probably could achieve the identity assurance requirements if the model provided a method/capability of third party verification of the claimant identity, but from what I can determine SQRL is focused on avoiding that kind of thing.
I see SQRL as a great idea, but only one aspect of a very complex problem.
Surely, a site can use SQRL for login and then verify the user’s identity in a conventional way such as via credit card if it needs to.
“Plenty of people began freaking out earlier this year after a breach at big-three credit bureau Equifax jeopardized the Social Security Numbers, dates of birth and other sensitive date on more than 145 million Americans. But as I have been trying to tell readers for many years, this data is broadly available for sale in the cybercrime underground on a significant portion of the American populace.”
I think the “freaking out” justifiably came from the realization that if one’s complete personal data hadn’t previously been available to such sites, it was probably much more likely to be so after the completely inexcusable Equifax fiasco.
Meh. *IF* the data was stolen by or has made its way into the hands of people who would sell it to fraudsters, the worst it would do for most people is refresh the data on them that is already for sale on cybercriminal shops like the one in this post.
Interesting article. It is surprising that Amazon credentials were sold for a much more cheaper rate than Frys, since crooks have pretty much known for years that it’s possible to SE Amazon into sending replacements for expensive items or refunds in the form of gift cards.
Well, I think it’s important to keep in mind that this dark web site is one of many, and that they all have different prices for things. It could be that Seller’s Paradise has a fair number of customers who are looking to buy frys.com accounts, and so they have increased the price as the demand has increased. But again, that’s speculation.
Brian, my Macbook was accessed by an unauthorized person while getting fixed at a 3rd party Apple supplier. This person changed my passwords for numerous financial websites. I quickly updated those said passwords, but wondering if there is a way I could find out if my credentials are being sold online? Thanks for any input.
Frys could be popular to buy crypto-mining rig components…
I’m guessing that Frys must have an easy method to purchase gift cards. Gift cards can be re-sold for hard cash.
Fry’s also sells name-brand large appliances, which are both valuable and extremely easy to resell.
Exactly. What would be really interesting to know is the success rate of the credentials.
Brian does “Carder’s Paradise” have an Amazon style rating system for stolen credentials? I would think the reviews would be an interesting if not amusing read.
I second that request. I imagine a certain percentage of these credentials are already void by the time they get sold, and that percentage only goes up for every day that goes by.
So do the sellers offer a guarantee or return policies? I know, right? I’m shaking my head as I write this…
If I am remembering correctly, one of Brian’s previous posts on dark web sites that sell cards and related data the sellers do offer some sort of guarantee on the stolen cards. They also sell them by zip/postal code so that the buyer can “buy/shop” local with a better chance of going undetected by Issuers. I slight digression from the topic at hand but you get my point. These guys are running serious businesses with all the same concerns and business practices of legitimate businesses so it wouldn’t surprise me if they had customer testimonials.
I like that I’m able to share Brian’s articles with my parents who are VERY far from the internet generation. The same threats I have warned them about for years are suddenly real when they read one of these articles. Much appreciated.
It’s not clear if they are selling Dropbox creds with clear text passwords or hashed passwords.
Because if the Dropbox passwords are from the 2012 breach, the passwords taken were hashed and salted with bcrypt, at worst some older ones were hashed with SHA-1.
VB – I’m going to guess you missed the part about how most of these credentials are being sold into the service for resale by people running large botnets of hacked computers. Those botnets are powered by malware that completely subverts the security of the Web browser on the infected PC, such that any usernames and passwords submitted on a Web login form get stripped out *prior to being encrypted as part of the browser session*.
Hence, what’s being sold here are credentials stolen directly from bot-infected computers — not credentials stolen en-masse from some public data breach at a big company.
@DeeAitch – IMO Brian knows how to write something intrinsically designed for people who would wish to read it rather than just “a piece” – The fact that he does so and puts it out for free without paywall to end readers says a lot to me about his intentions. Plus he’s put himself out there to be targeted by the goon squad, as documented in entertaining detail.
So a deserved golf clap! Jolly good Brian.
Look up NavyFederal.com and all their ATM’s/branches seem to be in the Hayward stretch – and if you know Fry’s they’re all in the San Jose – Concord – P.alto corridor. Hmm.
Very interesting article !
I have had my credit reports locked since 2007, always used unique usernames, email addresses (thanks to an email hosting provider I use), and passwords generated on a Linux system with a TRNG using cat, tr, and cut so I can audit the tools to make sure everything is exactly as I would assume.
Now that I read this article, I would love to do an audit, but I have no idea how to find there nefarious sites and/or if accessing information about myself, given it involves payments for illegal services, is even legal.
If you could consider doing a post some time about doing an audit and its legal implications, I would appreciate the information greatly.
I noticed that peoples names are being hacked and used buy some company to send out unwanted emails that want the end user you to open the email because you are familiar with the name so you would open it thinking its from your relative or best friend? Facebook refuses to listen to me, all the TV and Radio news refuses to mention it? Can you help?
I’m all for using a password manager. Trouble is, few password managers are really secure. Last Pass for example is often recommended but definitely not safe to use. I published an in-depth analysis a while ago under https://security.stackexchange.com/a/137307. Since then, more security issues have been reported, again affecting the same weak spots.
An offline password manager like KeePass is much easier to secure but not too comfortable to use. I suspect that people will often install one of the browser extensions available for KeePass integration. I looked into two of those – one was fairly basic and secure, the other more extensive and likely not safe to use.
So it’s not really clear how a “mere mortal” is supposed to choose a good password manager that won’t expose you to the risk of leaking all passwords at once. Maybe I should look into Dashlane, haven’t heard about that one before.
KeePass has had issues just like many other password managers. LastPass, unlike a lot of other software companies responds to security issues pretty quickly. If you use a password manager and 2FA on sites that allow it you will be in pretty good shape. Of course someone can always pop your PC/browser or whatever and steal what you are entering, but at that point you are owned. It doesn’t matter if you type your passwords from memory or use a manager. For most people KeePass being offline only is a serious issue because the average person will not back it up.
LastPass is good at PR, that’s it – you seem to have bought it. Their incident response mostly consists of downplaying the issue, that’s far from ideal.
2FA won’t help you if the browser extension is vulnerable and leaks all data to arbitrary websites after you already authenticated.
That would indeed be true, but once you use the token for the 2FA, it will not work again for the same authentication. So even if they do have the password, without a way to get that token to proc again and go to them before you use it, it is useless.
I would imagine a large part of the price variance on these (like Fry’s vs Amazon – as people have noted) is based on the presence or lack thereof of 2-factor authentication in addition to other account security checks/notices. As such, a more expensive, less secure account may have a higher “success” rate than several [potentially] more secure accounts.
I’m curious why Amazon credentials are not more of a focal point. There are simple merchandise scams of course, but it seems to me that the real criminal money, especially these days, is in getting someone’s Amazon account, setting up AWS, and mining bitcoins. I got hit with an absurd $6700 bill which happened from redirections from a manipulated search engine result for “aws” (browser logs reported). (N.B. never click on a search engine link if it’s important.) Why would criminals go through that trouble when they can buy credentials so cheap and Amazon does so little to cap such absurd use?
Thanks to you Brian for great reporting!
Cxed —
Can you provide a few more details?? Sounds fairly important to other readers…. Brian? Future article?
“They are, however, useful for helping to clean up identity theft after-the-fact.”
Just an editor’s note: you don’t hyphenate commonly used prepositional phrases such as “after the fact” when used this way. The phrase is hyphenated when the whole phrase is used as an adjective, such as, “an after-the-fact explanation.” It gets hyphenated as an adjective because its normal, non-hyphenated use is adverbial.
Awesome Article Brian!!! I search but didn’t found the site which you posted here. how to experience with my own eyes?any address?
Must be 18+