Panerabread.com, the Web site for the American chain of bakery-cafe fast casual restaurants by the same name, leaked millions of customer records — including names, email and physical addresses, birthdays and the last four digits of the customer’s credit card number — for at least eight months before it was yanked offline earlier today, KrebsOnSecurity has learned.
The data available in plain text from Panera’s site appeared to include records for any customer who has signed up for an account to order food online via panerabread.com. The St. Louis-based company, which has more than 2,100 retail locations in the United States and Canada, allows customers to order food online for pickup in stores or for delivery.
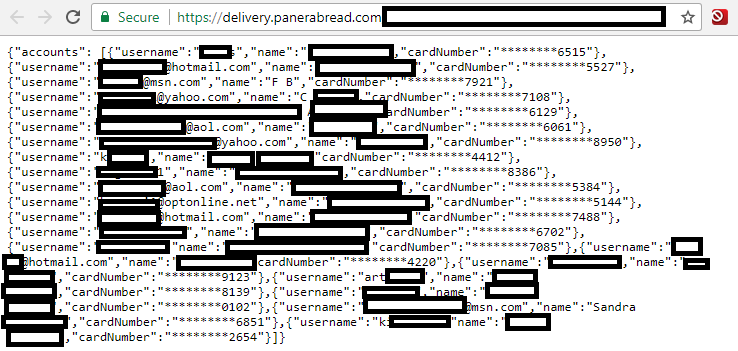
Redacted records from Panera’s site, which let anyone search by a variety of customer attributes, including phone number, email address, physical address or loyalty account number. In this example, the phone number was a main line at an office building where many different employees apparently registered to order food online.
KrebsOnSecurity learned about the breach earlier today after being contacted by security researcher Dylan Houlihan, who said he initially notified Panera about customer data leaking from its Web site back on August 2, 2017.
A long message thread that Houlihan shared between himself and Panera indicates that Mike Gustavison, Panera’s director of information security, initially dismissed Houlihan’s report as a likely scam. A week later, however, those messages suggest that the company had validated Houlihan’s findings and was working on a fix.
“Thank you for the information we are working on a resolution,” Gustavison wrote.
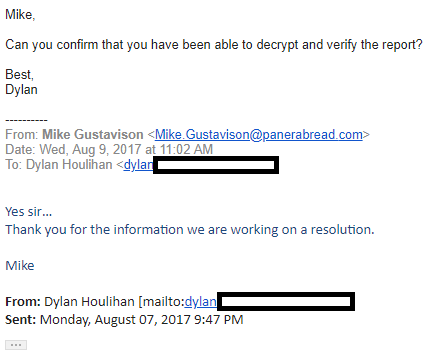
Panera was alerted about the data leakage in early August 2017, and said it was fixing the problem then.
Fast forward to early this afternoon — exactly eight months to the day after Houlihan first reported the problem — and data shared by Houlihan indicated the site was still leaking customer records in plain text. Worse still, the records could be indexed and crawled by automated tools with very little effort.
For example, some of the customer records include unique identifiers that increment by one for each new record, making it potentially simple for someone to scrape all available customer accounts. The format of the database also lets anyone search for customers via a variety of data points, including by phone number.
“Panera Bread uses sequential integers for account IDs, which means that if your goal is to gather as much information as you can instead about someone, you can simply increment through the accounts and collect as much as you’d like, up to and including the entire database,” Houlihan said.
Asked whether he saw any indication that Panera ever addressed the issue he reported in August 2017 until today, Houlihan said no.
“No, the flaw never disappeared,” he said. “I checked on it every month or so because I was pissed.”
Shortly after KrebsOnSecurity spoke briefly with Panera’s chief information officer John Meister by phone today, the company briefly took the Web site offline. As of this publication, the site is back online but the data referenced above no longer appears to be reachable.

Panera took its site down today after being notified by KrebsOnSecurity.
Another data point exposed in these records included the customer’s Panera loyalty card number, which could potentially be abused by scammers to spend prepaid accounts or to otherwise siphon value from Panera customer loyalty accounts.
It is not clear yet exactly how many Panera customer records may have been exposed by the company’s leaky Web site, but incremental customer numbers indexed by the site suggest that number may be higher than seven million. It’s also unclear whether any Panera customer account passwords may have been impacted.
In a written statement, Panera said it had fixed the problem within less than two hours of being notified by KrebsOnSecurity. But Panera did not explain why it appears to have taken the company eight months to fix the issue after initially acknowledging it privately with Houlihan.
“Panera takes data security very seriously and this issue is resolved,” the statement reads. “Following reports today of a potential problem on our website, we suspended the functionality to repair the issue. Our investigation is continuing, but there is no evidence of payment card information nor a large number of records being accessed or retrieved.”
Update, 8:40 p.m. ET: Almost minutes after this story was published, Panera gave a statement to Fox News downplaying the severity of this breach, stating that only 10,000 customer records were exposed. Almost in an instant, multiple sources — especially @holdsecurity — pointed out that Panera had basically “fixed” the problem by requiring people to log in to a valid user account at panerabread.com in order to view the exposed customer records (as opposed to letting just anyone with the right link access the records).
Subsequent links shared by Hold Security indicate that this data breach may be far larger than the 7 million customer records initially reported as exposed in this story. The vulnerabilities also appear to have extended to Panera’s commercial division which serves countless catering companies. At last count, the number of customer records exposed in this breach appears to exceed 37 million. Thank you to Panera for pointing out the shortcomings of our research. As of this update, the entire Web site panerabread.com is offline.
For anyone interested in my response to Panera’s apparent end-run around my reporting, see my tweets.




May we retire the expression “takes very seriously” because it is used constantly and clearly almost never meant?
I agree; it is actually an insulting term now, as far as I’m concerned!
With all due respect (where applicable) our nation’s IT infrastructure seems worse that the aging physical infrastructure.
It use to be “breech of the month”, but now it’s breech of the week”.
It took a lot of school shootings to get people seriously mobilized, and I hope we don’t have to reach the same level of crisis (given that the data breech harm is not nearly on the same level of seriousness) before serious actions are taken about this.
I am a self-taught Internet consultant, but even to me it seems we don’t have a clue on how to provide clients & users with some REAL measure of safeguards.
Come on, it’s not that hard to protect stuff if you really think about it. And it’s REALLY simple to create ways to be alerted instantly or as soon as the data is being abused if there is a breech. I would love for some expert to contact me and explain what their excuses are for allowing this to happen over and over again.
Actually it’s ‘Breach’ of the week.
Everyone understood what he meant, Name. You must forgive persons who do not have an excellent command of the English language; teachers don’t how can you expect the general public to?
The commentary should be directed towards Panera, not someone who ineloquently commentsc
Contrary to what you are implying, Chris Nielsen has an excellent command of the English language and needs no forgiveness at all. I do agree his minor spelling error should have been overlooked, especially in these days of autocorrect or autoerror as the case may be.
Was the breach limited to registered accounts, or does it also include past orders from people who made online orders as a guest but never created an account?
Actually, it is “that hard”. And it takes more than an 8-5 grunt who couldn’t care less.
It takes someone who can think like a penetrator/malefactor and someone who understands tome of the mechanisms to counter this.
MBAs and recent CS grads to not need to apply. Get 10-20 years of fending off attacks from multiple vectors. If you can stand the heat, apply to be in this kitchen.
But we all know that the corps don’t want to pay for competence.
“new CS grads need not apply” I’m a security engineer and haven’t even graduated fully. Don’t judge someone by their college education, judge them by their actual skills.
p_down, you seem to have completely misread what roger tubby wrote, if you think he was saying that a college education is what matters instead of skills and experience.
This is disgusting. “Career change strongly suggested” disgusting.
They only take it seriously when the threat of publication is on the menu. Good on Houlihan for going to a relevent media outlet with his experience!
I do command Mr Houlihan for being a responsible citizen. I do wonder moving forward if future concerned citiziens should dangle the prospect of publication if no action is taken within a reasonable amount of time. Obviously it didn’t need to drag on for eight months, when in the end it was taken care of within a day. Hopefully nobody with nefarious intent had access.
As a concerned citizen, I would argue that that it is better to go to the media directly, instead of the company, so as to avoid being easily prosecuted for violating the CFAA… However I am just a concerned citizen who’s watched far too many talks, rather than an actual lawyer (who, coincidentally, offers even more protection, and could contact the company involved on their client’s behalf)
Who is responsible for the eight-month lapse that was fixed in hours once a phone call was made?
The same Mike Gustavison who was a Senior Director of Security Operations at…Equifax (2009-2013): https://www.linkedin.com/in/mike-gustavison-b020426/
The same guy who “…At Panera, Mike and his team have created a layered defense strategy from an internal and external perspective…. Leveraging Akamai (Edge and WAF products) was a key element for Panera’s external defense strategy to enable visibility and proactive response to current risks in the wild. This allows for quick reaction, priceless metrics, and significant insight into activities that are occurring against digital properties.”:
https://www.eiseverywhere.com/ereg/popups/speakerdetails.php?eventid=126042&language=eng&speakerid=339242&
….and the plot thickens. (Brian needs to step up his research game 😉 Nice catch!
I’d imagine Brian is trying to avoid looking like a shill for advertising every Tom, Dick, and Harry that is in the security game. Besides, that really shouldn’t be the thrust of any story like this.
Too funny…listing perimeter security implemented at the organization…or is it.
Mr. Gustavison didn’t happen to work at the DNC by any chance, did he?
You know it was more than just that, birthdays, etc. https://pastebin.com/21H28TA1
Isn’t telephone and last four enough to add a new card to anyone’s Amazon account and then do an ‘account recovery’ to pown it?
That is infuriating. Eight months. In this day and age, someone who would dismiss anything like that. Heads should roll. I go to Panera about once a week and won’t spend a dime there after this.
Sure you will, because if you stop supporting every company that’s ever been breached, you’ll just sit at home in the corner.
Hey this is my totally secure corner. Go find your own. =)
The article states “Panera takes data security very seriously” but that’s always after the fact with any website breach.
“Resolved” is an interesting choice of words. Does this mean the current issue is resolved and a new one is out there (i.e. they just renamed the webpage to something new)? Why was the data available in plain text anyway? Will Panera explain why this data was published via a website (i.e. who were the legitimate consumers of the data)?
“Our investigation is continuing, but there is no evidence of payment card information nor a large number of records being accessed or retrieved.”
My guess is there is no evidence because there is nothing in place to log and collect any possible evidence.
How True. How True.
Ray,
How sad, how very sad. I used to work for an employer who would never fix a noticeable problem stating, “…the customer will probably never notice it.”
I used to wonder, after the customer DID notice it and DID want it repaired, why it was that there was never enough time [or desire] to fix the problem when it was manageable, but there was ALWAYS enough time to fix the problem after the customer rebuked the owner.
Eventually, the company went out of business…the offended customers never returned…funny that.
Bad news travels v-e-r-y fast, Panera.
It appears to me that in breaches like this, the company people that are notified are not the people that need to be notified. Too often nothing is done. Perhaps the security people that are notified do not act because they do not want to be faulted by management. However, if you are able to find someone in top management to notify, they might not understand the importance of the notice. What is to be done?
The whole “take[s] data security very seriously” thing is almost always linked to “if it’s about to be shown to a large audience”. It’s really incredible the amount of businesses that will either ignore reports of security issues, or even deny the issue exists, and not bother to fix anything until it’s going to be published.
This looks like another reason to avoid using these convenient order-0nline systems.
I leave my credit card number on line as little as possible. To my knowledge, only PayPal has it. Perhaps Amazon, as I don’t recall a way to opt out of storing it.
I’m not immune to these “loyalty” deals. But what I do is buy gift cards and put the balance on the app. I won’t plug the coffee shop, but the gift cards themselves are discounted, so you save twice.
I can’t wait for the hack details to be released.
That seems like a lot of aggravation. Honestly, I really couldn’t care less about regular old credit card fraud. I’m not liable for anything, they send me a new card and life goes on. I’ve had to replace one of my credit cards twice in the past year, it’s annoying, but since you’ll never know where the breach came from there isn’t much you can do. You don’t use your card online, but it could just as easily be stolen at a physical store. If you’re saving money great, but otherwise you’re just adding a layer of complexity to your life for no real benefit.
On Amazon, I have changed my curent/working credit card # to an expired card #.
Which web sites keep track of these corporate breaches? Here is Wikipedia’s: https://en.wikipedia.org/wiki/List_of_data_breaches
Where are others?
You can use https://haveibeenpwned.com/
I’m pretty sure Brian has a list somewhere, but https://oag.ca.gov/privacy/databreach/list is pretty good. A number of other states have lists too…
I’m sure Panera will “take data security very seriously” when the lawyers start circling overhead.
I hope Panera’s CIO and other key IT staff will soon be filing for unemployment. Meanwhile, I can think of many alternatives to Panera that likely “take data security very seriously.”
Panera didn’t have any comment on the number of accounts potentially impacted. I went with what the incremental numbers suggested. After my story runs, Panera gives a statement to Fox News saying it’s only limited to 10k accounts.
FWIW, they haven’t fix the actual problem still, and customer records are still exposed. And it’s way more than 10,000. At the very least it’s 500,000.
under maintenance 8:30pm.
I just have one question: How does a security professional take so little interest in an issue that is placed in front of him for months? WTF! I understand the fact that he may not have been so smart to identify the issue, but not fixing it after someone else finds it for him? The guy is supposed to have years of experience. How does an idiot become the man in charge? I should have switched careers long ago. Maybe it is not too late. Where do I start reading? I am pretty sure I can replace a few of these dickheads.
I’m not an “expert” but 10k seems like a lot to me.
Why don’t these fools encrypt the data?
I’m not an “expert” but 10k seems like a lot to me.
Also,why don’t these fools encrypt the data?
They probably couldn’t encrypt the data like you are thinking. (Easily)
This is clearly some type of API that shouldn’t be accessible to the internet. It is querying a backend database which is storing this data. The two options would have been to restrict the API with some type of authentication or alternatively not include the capability of doing this call externally. Either way, they were not following security best practices.
Who gives their birthday to Panera? Does it get you a free sandwich or something? Not worth it, obviously.
I think its usually a bakery item, so you could, in theory, get a piece of cake. Although I don’t believe I’ve ever seen cake there. But you could get a birthday bearclaw.
I gave Panera a fake birthday so I’m always surprised when it rolls around. I always record the day I give sites so I could find out if it was needed for security purposes, but its not like I look at that info regularly so I never remember until it shows up out of the blue.
So, yeah.
August 18, 2016, Getting free food from Panera Bread (MyPanera Rewards) https://www.adamlogue.com/getting-free-food-from-panera-bread-mypanera-rewards-fixed/
Wait, Mike Gustavison has worked for Panera Bread between Jun 2013 – Present. Repeat offender.
He’ll get fired, hired by the next company who will have a customer data leak.
We need to go back to paper, applications, the problem is the technology all our info is out there
Bank Advertisement: “Go paperless and be automatically entered to win $250,000!”
Bank customer to Bank: “I’m unable to enter information to select paperless options”
Bank: “We apologize. That part of our site is briefly unavailable (real speak: the past 24 hours). Please try again later (and again, and again, and …). Thank you for your patience.”
Bank customer: “Yes, but this has happened repeatedly”
Bank: “We’re unaware of an prior similar incidents. Please clear your browser history (the final, standard insult to injury simpleton solution).”
Bank customer: “Hmmm … how can I be assured of adequate online security if your bank is unable to do something as basic as maintaining a fully functional website or any part of the site?”
Or, in the actual case of DirectTV:
-Go paperless, and pay your bill automatically every month via direct deposit.
-Hey, we know you’re paying your bill which is the same every month via direct deposit, so we’ll sneak in this notice that if you don’t tell us not to in a couple of months, we’ll start billing you $80 a month for the NFL all channel access plan. Don’t worry, doing nothing is exactly what we want you to do. Thanks for using auto-bill pay.
I’m pretty sure that I’ve seen Nigerian fraud scams that are more honest and straightforward than DirecTV’s billing system.
DirecTV are downright thieves.
I would never go to Panera bread… don’t even want to go there. Bad bad place
All I want to know is how I can sue them! How dare they keep this from the public for 8 months. I use their website almost every week. Nothing was said. $hame on them. My security is in jeopardy. Those high and might a-holes always sugar coat everything. Can you say “CLASs ACTION Law suit”? SIGN ME UP. All I can say is rat bastards! You know how hard it is to clear your name when this happens? Well you will!!!!
You forgot to light the dumpster on fire and push it into the intersection while screaming “Save the beavers!”
Settle down there Catherine. The class action lawsuit will be coming soon enough, but all you’ll get out of it is a year of free credit monitoring and 2 free sandwiches. 😉
This is NOT full blown identity theft. They have your name (publicly available), address (publicly available), email address (available to anyone you’ve ever sent an email to). The only interesting pieces of information are your phone number (which a LOT of people have) and the last 4 of your credit card (which has limited value). No one is going to be able to take out a mortgage in your name with just a name address and phone number.
This IS a bad situation, but there have been many other high-profile breaches lately that I would be much more concerned about. (and my data is probably in the Panera breach, but I never set up an account, I always ordered as a guest, so I don’t know for sure, but I’d assume it is.)
I’m more concerned about their head-in-the-sand attitude and the lying, than the small amount of truly personal data they have on me. I would like to see the people involved punished severely for their denials and lies more than their technical incompetence.
Lots of breeches occur due to technical errors, but the good companies, fess up right away, and are transparent about what happened and how they are going to fix it (and then actually do fix it). That is what makes or breaks the public perception of the event, how you deal with it afterwards. Of course gross negligence doesn’t help your case, and Mr. Gustavison seems to be lax in his understanding of how to handle security incidents, but honest mistakes do happen, this case was just not one of them.
Haha. Best part is their tweet earlier today. “Stay cool.”
https://twitter.com/panerabread/status/980882626792783877
Having worked in IT security for an international restaurant chain, unless CC#’s were disclosed, this is a low item on their enterprise risk register.
Never cared for the place…even less now.
I wondered why I and many others are getting 2 weeks of free bagels.
When someone says: “It’s really quite easy to protect data”, they clearly have no actual technology job worth keeping. Literally, my entire job every day is to prove how weak networks are, and to prove how no matter how much money you spend, you will always have a network that is vulnerable. So, you say it’s not hard to protect a network or data, but I care to disagree. Today alone, I used a simple pass the hash attack to query a SQL database on a customer network using. They have PKI and OTP token-based 2FA. We did this as a proof of concept for their IT department. A single email, one click, or one redirect. That’s all it takes. You say its easy, but I can assure you that these technology professionals are not taking this lightly. The answer is never to avoid the hack. When you focus your efforts trying to avoid the hack, you miss the point entirely. Limit what data can be leaked. Limit the impact a hack will have. That’s the right answer. If the CC# didnt get out, and the HR records didnt leak with SSN’s and payment accounts, or bank account numbers… Then who cares if they got your Panera reward card number, and email address? Maybe a telephone number? … Who cares? You think they couldn’t just buy that from someone? Anthem, Target, Pentagon, Home Depot, EquiFax, local banks the world wide…. This is a nothing breach so far. Who gives a crap that some email addresses leaked? Not one person with a brain.
“Panerabread.com Leaks Millions of Customer Records”
Having been to a Panera exactly once, I’m amazed that they had millions of customers.
How would I know if my account is hacked? Will Panera notify me.
There is 0% chance that the entire DB wasn’t scraped via these endpoints by at least one actor