Your mobile phone is giving away your approximate location all day long. This isn’t exactly a secret: It has to share this data with your mobile provider constantly to provide better call quality and to route any emergency 911 calls straight to your location. But now, the major mobile providers in the United States — AT&T, Sprint, T-Mobile and Verizon — are selling this location information to third party companies — in real time — without your consent or a court order, and with apparently zero accountability for how this data will be used, stored, shared or protected.
Think about what’s at stake in a world where anyone can track your location at any time and in real-time. Right now, to be free of constant tracking the only thing you can do is remove the SIM card from your mobile device never put it back in unless you want people to know where you are.
 It may be tough to put a price on one’s location privacy, but here’s something of which you can be sure: The mobile carriers are selling data about where you are at any time, without your consent, to third-parties for probably far less than you might be willing to pay to secure it.
It may be tough to put a price on one’s location privacy, but here’s something of which you can be sure: The mobile carriers are selling data about where you are at any time, without your consent, to third-parties for probably far less than you might be willing to pay to secure it.
The problem is that as long as anyone but the phone companies and law enforcement agencies with a valid court order can access this data, it is always going to be at extremely high risk of being hacked, stolen and misused.
Consider just two recent examples. Earlier this month The New York Times reported that a little-known data broker named Securus was selling local police forces around the country the ability to look up the precise location of any cell phone across all of the major U.S. mobile networks. Then it emerged that Securus had been hacked, its database of hundreds of law enforcement officer usernames and passwords plundered. We also found out that Securus’ data was ultimately obtained from a California-based location tracking firm LocationSmart.
On May 17, KrebsOnSecurity broke the news of research by Carnegie Mellon University PhD student Robert Xiao, who discovered that a LocationSmart try-before-you-buy opt-in demo of the company’s technology was wide open — allowing real-time lookups from anyone on anyone’s mobile device — without any sort of authentication, consent or authorization.
Xiao said it took him all of about 15 minutes to discover that LocationSmart’s lookup tool could be used to track the location of virtually any mobile phone user in the United States.
Securus seems equally clueless about protecting the priceless data to which it was entrusted by LocationSmart. Over the weekend KrebsOnSecurity discovered that someone — almost certainly a security professional employed by Securus — has been uploading dozens of emails, PDFs, password lists and other files to Virustotal.com — a service owned by Google that can be used to scan any submitted file against dozens of commercial antivirus tools.
Antivirus companies willingly participate in Virustotal because it gives them early access to new, potentially malicious files being spewed by cybercriminals online. Virustotal users can submit suspicious files of all kind; in return they’ll see whether any of the 60+ antivirus tools think the file is bad or benign.
One basic rule that all Virustotal users need to understand is that any file submitted to Virustotal is also available to customers who purchase access to the service’s file repository. Nevertheless, for the past two years someone at Securus has been submitting a great deal of information about the company’s operations to Virustotal, including copies of internal emails and PDFs about visitation policies at a number of local and state prisons and jails that made up much of Securus’ business.

Some of the many, many files uploaded to Virustotal.com over the years by someone at Securus Technologies.
One of the files, submitted on April 27, 2018, is titled “38k user pass microsemi.com – joomla_production.mic_users_blockedData.txt”. This file includes the names and what appear to be hashed/scrambled passwords of some 38,000 accounts — supposedly taken from Microsemi, a company that’s been called the largest U.S. commercial supplier of military and aerospace semiconductor equipment.
Many of the usernames in that file do map back to names of current and former employees at Microsemi. KrebsOnSecurity shared a copy of the database with Microsemi, but has not yet received a reply. Securus also has not responded to requests for comment.
These files that someone at Securus apparently submitted regularly to Virustotal also provide something of an internal roadmap of Securus’ business dealings, revealing the names and login pages for several police departments and jails across the country, such as the Travis County Jail site’s Web page to access Securus’ data.
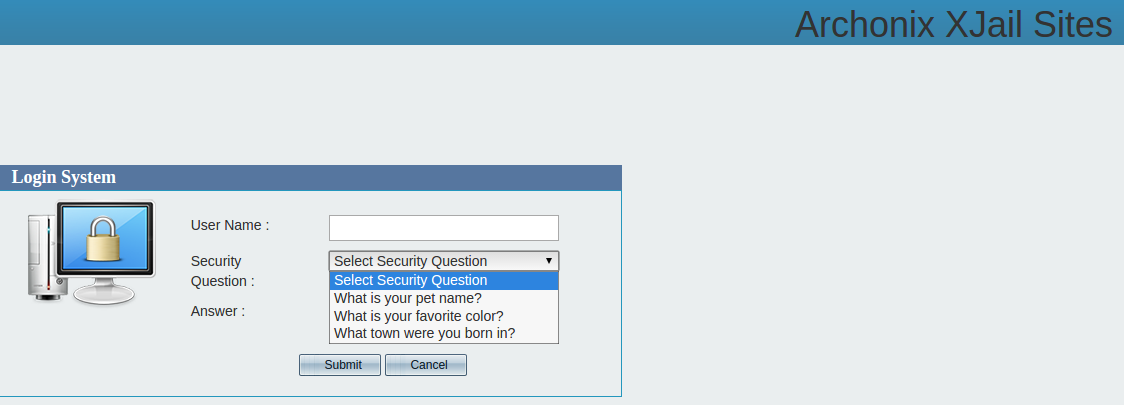
Check out the screen shot below. Notice that forgot password link there? Clicking that prompts the visitor to enter their username and to select a “security question” to answer. There are but three questions: “What is your pet’s name? What is your favorite color? And what town were you born in?” There don’t appear to be any limits on the number of times one can attempt to answer a secret question.
Given such robust, state-of-the-art security, how long do you think it would take for someone to figure out how to reset the password for any authorized user at Securus’ Travis County Jail portal?
Yes, companies like Securus and Location Smart have been careless with securing our prized location data, but why should they care if their paying customers are happy and the real-time data feeds from the mobile industry keep flowing?
No, the real blame for this sorry state of affairs comes down to AT&T, Sprint, T-Mobile and Verizon. T-Mobile was the only one of the four major providers that admitted providing Securus and LocationSmart with the ability to perform real-time location lookups on their customers. The other three carriers declined to confirm or deny that they did business with either company.
As noted in my story last Thursday, LocationSmart included the logos of the four carriers on their home page — in addition to those of several other major firms (that information is no longer available on the company’s site, but it can still be viewed by visiting this historic record of it over at the Internet Archive).
Now, don’t think for a second that these two tiny companies are the only ones with permission from the mobile giants to look up such sensitive information on demand. At a minimum, each one of these companies can in theory resell (or leak) this information and access to others. On 15 May, ZDNet reported that Securus was getting its data from the carriers by going through an intermediary: 3Cinteractive, which was getting it from LocationSmart.
However, it is interesting that the first insight we got that the mobile firms were being so promiscuous with our private location data came in the Times story about law enforcement officials seeking the ability to access any mobile device’s location data in real time.
All technologies are double-edged swords, which means that each can be used both for good and malicious ends. As much as police officers may wish to avoid the hassle and time constraints of having to get a warrant to determine the precise location of anyone they please whenever they wish, those same law enforcement officers should remember that this technology works both ways: It also can just as easily be abused by criminals to track the real-time movements of police and their families, informants, jurors, witnesses and even judges.
Consider the damage that organized crime syndicates — human traffickers, drug smugglers and money launderers — could inflict armed with an app that displays the precise location of every uniformed officer from within 300 ft to across the country. All because they just happened to know the cell phone number tied to each law enforcement official.
Maybe you have children or grandchildren who — like many of their peers these days — carry a mobile device at all times for safety and for quick communication with parents or guardians. Now imagine that anyone in the world has the instant capability to track where your kid is at any time of day. All they’d need is your kid’s digits.
Maybe you’re the current or former target of a stalker, jilted ex-spouse, or vengeful co-worker. Perhaps you perform sensitive work for the government. All of the above-mentioned parties and many more are put at heightened personal risk by having their real-time location data exposed to commercial third parties.
Some people might never sell their location data for any price: I suspect most of us would like this information always to be private unless and until we change the defaults (either in a binary “on/off” way or app-specific). On the other end of the spectrum there are probably plenty of people who don’t care one way or another provided that sharing their location information brings them some real or perceived financial or commercial benefit.
The point is, for many of us location privacy is priceless because, without it, almost everything else we’re doing to safeguard our privacy goes out the window.
And this sad reality will persist until the mobile providers state unequivocally that they will no longer sell or share customer location data without having received and validated some kind of legal obligation — such as a court-ordered subpoena.
But even that won’t be enough, because companies can and do change their policies all the time without warning or recourse (witness the current reality). It won’t be enough until lawmakers in this Congress step up and do their jobs — to prevent the mobile providers from selling our last remaining bastion of privacy in the free world to third party companies who simply can’t or won’t keep it secure.
The next post in this series will examine how we got here, and what Congress and federal regulators have done and might do to rectify the situation.
Update, May 23, 12:34 am ET: Securus responded with the following comment:
“Securus Technologies does not use the Google tool, Virustotal.com as part of our normal business practice for confidential information. We use other antivirus tools that meet our high standards for security and reliability. Importantly,Virustotal.com will associate a file with a URL or domain merely because the URL or domain is included in the file. Our initial review concluded that the overwhelming majority of files that Virustotal.com associates with www.securustech.net were not uploaded by Securus. Our review also showed that a few employees accessed the site in an abundance of caution to verify that outside emails were virus free. As a result, many of the files indicated in your article were not directly uploaded by Securus and/or are not Securus documents. A vast majority of files merely mention our URL. Our review also determined that the Microsemi file mentioned in your article is only associated with Securus because two Securus employee email addresses were included in the file, and not because Securus uploaded the file.”
“Because we take the security of information very seriously, we are continuing to look into this matter to ensure proper procedures are followed to protect company and client information. We will update you if we learn that procedures were not followed.”




What the carriers are doing with location data is really ugly. But…there is always a but…as bad as the cell phone issue is check out Amazon’s facial recognition “service” being marketed to LE! Its name is Rekognition. Really scary stuff for everyone’s privacy and civil liberties. Check it out here at… https://www.theverge.com/2018/5/22/17379968/amazon-rekognition-facial-recognition-surveillance-aclu
That’s not a “but” as much as an “and”.
Another reason, on top of the big steaming pile of reasons, you will never get me into a self-driving car. (And I felt that way BEFORE Fate of the Furious came out.)
That is an extremely paranoid stance to take against self-driving cars.
Actually, it’s perfectly reasonable. Given that Verizon are selling *actual precise location* data, why not Tesla, or Ford?
I think cars are already being tracked by things like GM’s OnStar.
Even if you haven’t signed up for the service, the equipment is in your car ready to be activated remotely.
This is stunning. I sincerely hope that this get addressed quickly by those in authority before it is abused any more than it already has been.
Thank you for bringing this to light, Brian. While this news carries a dark undertone, I’d much rather be aware of it than living in ignorance.
You must live somewhere in the European Union where they take personal privacy seriously. because in the United States nothing will be done by the paid, corrupt members of Congress. In the United States the people’s representatives are owned by the carriers spoken about in the article and other wealthy corporations. They will not allow a law to be passed that restricts their “right” to sell your information.
The situation will never change in the current environment because the companies will never give up the income stream and all regulations are evil.
My view exactlyd We are all f***ed.
How about just using a cellphone with a removable battery? There are plenty of them available – and mine is running the latest Android security updates.
Pop out the battery if you don’t want to be tracked.
Yeah, that makes sense. Disable the device I use to stay in contact so no one illegally tracks my location…
Great article
thankful for you Brian, and the way you bring these hugely significant issues to light. this stuff is so scary 🙁
This is not good at all. You mentioned ‘stalkers’ as a potential threat– I would suggest one more– unfortunately.
This is a ‘sexual-predators’ “dream come true”. Internet chat-rooms / Social Media are already a problem –with luring the innocent into traps. With this– they wouldn’t even need to contact and lure their victims– but just hunt them down using their own phone.
You cannot speak of such when you look like bruce mcarthur
Turn your phone off when not using it and buy this:
SILENT POCKET PATENTED FARADAY CAGE BAGS, CASES AND WALLETS THAT BLOCK ALL WIRELESS SIGNAL.
https://silent-pocket.com/
It is worth the cost…
Or just wrap it in a bit of al-foil instead, for free! I don’t understand these “phone blocking” things, but I suppose that the sheeple will fall for anything these days.
Surprised that the point of VirusTotal’s storing and making all files available is not getting more attention. Yes, they do admit this, but it’s buried halfway through a page of text linked in 8pt font at the bottom of the upload page:
“The contents of submitted files or pages may also be shared with premium VirusTotal customers.”
That seems extremely shady.
Why is that shady? The presumption is that VirusTotal is receiving viruses from “the wild.” They share those with anyone interested in analyzing/defeating viruses. I see nothing wrong there, so long as idiots don’t share confidential information instead of viruses.
Not just malware – bear in mind how many malicious files out there arrive packaged as Microsoft Office documents. I’ve seen people submit really sensitive files “just to check” because they thought something had started crawling their computer and infecting with malicious office macros.
VirusTotal is a great service for the money… just be careful that what you submit isn’t sensitive, because it might as well be public at that point.
There are not just sharing the files with viruses. They are sharing virus free files. I see no justification for that .
Your premise is wrong because “Absence of evidence is not evidence of absence”
As such just because virustotal (and the scanners it uses) did not detect any malware does not proof that it doesn’t contain any malware.
This would only work if virustotal would have a 100% guarantee to detect any past, current and future malware to be ever conceived.
This is quite well known in the Security world. Anyone working in Security who is not aware of this, shouldnt be working in Security.
Well this comes to mind,more and more each day!
https://www.youtube.com/watch?v=ygLg-7G0Xp0
Will the circus ever leave town?
What about the 1984 Super Bowl commercial introducing Macintosh computers…chilling.
https://www.youtube.com/watch?v=2zfqw8nhUwA
There is a new movie out called ANON and everything is recorded and filed by everyone’s eyes…frightening.
“What is the air speed of an unladen swallow?”
African or European?
You must be a king, Greg. You have to know these things when you’re a king.
“Right now, to be free of constant tracking the only thing you can do is remove the SIM card from your mobile device never put it back in unless you want people to know where you are.”
Ummm… I do believe that just powering one’s cell phone down and leaving it like that until needed works pretty well to avoid most location tracking too. That’s what I do anyway. Doing this also has the added benefit of preserving the battery charge, and perhaps also lengthening the battery life.
And anyway, after the Snowden revelations, who wants to walk around all day long with both a camera and a microphone, both of which could perhaps be live at any moment? (Although as Snowden pointed out, you may *believe* that you’ve powered down your phone, but maybe it only appears that way.)
If you are REALLY skittish about all this stuff, I just saw an advertisement last night for a clever product I’d never heard of before. It’s a thing called a “Faraday Bag”. Google for it. Clever. I wish I had thought of that!
Oh the conspiracy of eliminating the removable battery design.
Thanks for a great article, as usual.
One question: If you use an old mobile phone (not a smart phone) which can only do voice calls and sms’s (mainly) – and has no GPS – will that provide more security?
Is it new enough to have a SIM card? If so…. nope.
The location data isn’t coming from the phone apps or operating system. It’s coming from your mobile provider – they are using data based on which cell towers your phone connects to and how strong your signal is (therefore how far away your phone is) from each tower.
Thanks. Yes, I am aware of the cell tower connection information system but thought it might be less accurate than the GPS information smart phones provide. Please also see next comment here.
The tower-triangulation method is considerably less accurate than the embedded GPS receiver method of locating a handset.
That doesn’t mean it makes your location hard to get, though.
And, of course, the mobile phone system simply doesn’t work without tower-proximity detection features. The network needs to know where to send incoming calls, and it uses tower-proximity detection to do that.
So, if there’s a fix to this problem, it has to be a regulatory fix. And in 21st century USA, that seems unlikely.
Thanks. Thought as much. I’ll stick to my practice, similar to the one mentioned in the following post, to keep my old ‘dumb’ phone off most of the time. I don’t believe it is able to send info about location when it is turned off (as smart phones have).
I’m not sure that helps, unless you keep it turned off and you are absolutely sure nothing is being transmitted in “sleep mode”, like a lot of modern cell phones do. I say this because the police tell me all phones made after the frequency change that came out with 2 or 3G (don’t remember which one); they needed a way to track all phones calling in to 911.
I only use my “dumb” phone for emergencies, so it is shut completely down with all services shut down to prevent sleep mode leakage. My battery lasts forever that way, I hardly ever have to charge it up; so I’m confident that it doesn’t send location data while it is off. Since I hardly ever fire it up – I doubt much of my data is out there; especially since I am parked out in the middle of nowhere when I actually use it.
Thanks. Yes, I’m doing about the same, so it seems it gives some security at least.
In theory Airplane mode with a modern phone should work well enough.
Of course, it makes it a pretty lame phone if you want to receive inbound communications…
Well, I don’t mind the phone being “lame” 😉 I rarely use the phone for incoming messages (except a very few necessary sms from the post office and the like). Email is quite enough for incoming messages (for me). Gives more peace 😉
Not in this story, and perhaps it’s such a basic concept that KoS readers don’t need it repeated: knowing a mobile fone’s location is essential for any mobile fone service to work. What’s at issue is service providers monetizing that knowledge. If what you have is a “smart” fone, providing updated location-specific advertising is part of the service provider’s revenue stream.
“All technologies are double-edged swords, which means that each can be used both for good and malicious ends.” It’s a hard sell convincing folks who’ve chosen to rely on mobile fones for identity confirmation (2FA) or electronic payments to forgo these conveniences. Indeed, some consider what are merely conveniences to be necessities.
As others have noted, turning off your fone may be the only way to prevent cell towers from monitoring a fone’s location; and as other others have also noted, “off” may not truly mean “off”.
Near-term, I see little hope of either regulatory or legislative relief. If you don’t want to be tracked, repeating other comments: keep your fone “off” and bagged. Also, don’t use the wheel. Or fire.
purchased a BLU SMART PHONE.
cannot remove battery as it is integrated into phone.
if i remove SIM CARD will this prevent anyone from knowing my location ?????????????
THANKS
Pretty radical, but yeah, that should work. One static snap and your SIM card might get bricked though; be sure and carry it in one of those plastic shipping containers made just for that. Once you have it back in the phone, that part of your activity would continue to be recorded
Technically the answer is “no”, although it would mostly work, it’s also an inefficient and inelegant, and of course risky solution to a simple problem.
You want Airplane mode.
Technically a cell phone w/ the cellular modem on can still talk to the cellular network. When a cellular modem connects to a network, it generally provides two pieces of ID, an IMEI (roughly tied to the cellular modem) and the IMSI (roughly tied to the SIM card).
Normally when we talk about phones and tracking, we are talking about phone numbers. Phone numbers are loosely coupled to IMSIs — but, a carrier can map a number to multiple IMSIs if it likes (this service is called “clone SIMs”, although they’re not actually technically clones, each have their own IMSI, it’s just magic managed by the operator — roughly call forking).
And, technically, the cellular network doesn’t deal in phone numbers, it deals in IMEIs and IMSIs, and those can be tracked, because that’s how the system actually manages call delivery. When you set up a cellular subscription (see the recent article about SIM swaps by T-Mobile), you’re arranging for the carrier to map a phone number to an IMSI so when the network sees the IMSI it can deliver calls for that number to it.
Anyway, there’s a reason that we talk about IMSI catchers.
In the US (and I believe Canada, but not necessarily in all countries), it’s possible to dial 911* with a phone that has no SIM.
More importantly, to the question at hand, the network does know about IMEIs (and when it takes that SIM-less 911 call from a phone, it will be using it).
I don’t think that a SIM-less phone will normally broadcast its IMEI outside of the case when you make that emergency call, and presumably in that case, you actually do want 911 to find you. But, that is technically “tracking” your phone w/o a SIM (even if it’s an incredibly rare case, and not something you should rely on — if you know where you are and can inform 911 when you call, you absolutely should, relying on e911 to find you is risky, e.g. if your phone’s battery dies or your phone fails for some other reason).
* note: 112 is the global emergency number and would work in your cell phone in the US or Canada too, but, if the country you’re in doesn’t require this feature…
I wish this was not old news. The data has been available to pay for play people for awhile
I am surprised Brian that you still use Android (or at least I think you did based on one of your old articles.)
There are a ton of Android apps that collect location information and share with their developers. iOS is not 100% secure but is much more restrictive and better at privacy out of the box than Android.
If you’re that concerned about location privacy, consider the apps and devices you use. The carriers selling your data is just scummy and unavoidable. They should be only using it to improve the network.
Potentially a silly question – but doesn’t airplane mode (assuming it does as promised) also stop the mobile provider knowing your location?
The only way (really!) … The only way to get a business’ attention is to restrict their revenue stream. That means not using a service that does nefarious things with your data. Not enough people are willing to part with their smart phones, or tablets, or Face Breach, but the only language business understands is profit.
Silence is concurrance.
And you were nagging about the GDPR … This is just why the EU tries to protect its citizens by installing such a law.
I see that in the UK mobile network provider O2 has set up a company called Weve who provide the Weve Locate service to advertisers touting “The UK’s only telco-powered data offering” and “Powered by O2, we start with 23 million real people to make up our data foundation.”
Fortunately the UK has regulation that stops them doing anything unpleasant with it. Or even storing it, without consent.
Thank goodness for GDPR!
“…for many of us location privacy is priceless because, without it, almost everything else we’re doing to safeguard our privacy goes out the window… It won’t be enough until lawmakers in this Congress step up and do their jobs — to prevent the mobile providers from selling our last remaining bastion of privacy in the free world to third party companies who simply can’t or won’t keep it secure.”-Krebs on Security
I agree.
This is a location data laundering circle with ATT, Verison in the loop and using an end-run to skirt legal warrants. I would have guessed that these 4 huge phone companies would have violated some actual law or administrative procedure under the FCC.
All politicians, doctors, lawyers, judges, auditors, National Guard persons and probably their families are being sold out.
Unfriendly, countries and criminal enterprises could easily use this data location information to harm Americans. I would guess that this could be a huge national security issue. Why hasn’t the congress acted to stop the real time and historical location data from being sold?
“turn your phone off when not using it and buy this: SILENT POCKET PATENTED FARADAY CAGE BAGS, CASES AND WALLETS THAT BLOCK ALL WIRELESS SIGNAL.”- cal west
Good idea.
“wrap it in a bit of al-foil instead, for free!”- Dave Horsfall (who’s not afraid to use his real name)
That is also a good idea. How thick should the aluminum foil be? I just tried three wraps my cell phone with thin aluminum foil and my cell phone still can get calls inside of the metal foil.
I too would have guessed that the FCC had rules against such promiscuous use this information, but under the current leadership (a former carrier executive) the FCC has no interest in enforcing rules that would slow down the money stream.
And as for congress, their donors (of whom I expect all these companies are…) are more important than J.Q. Public.
Unless some members of Congress, or maybe one of the phone companies’ executives or Board of Directors is victimized, they’ll carry on doing what they’re doing.
I’d be very surprised if this Congress does anything useful about it.
put ur phone in a faraday cage when not in use
As usual, knock Android. You forgot to knock apple as well. It’s not one manufacturers problem. All phone oses have the same problem. It’s not one carrier, but all carriers. It’s not one software problem, it’s all software. And don’t forget the updates changing your security settings. They all do it. And, it’s been around for a while, both apple and Ms ce were accused of tracking in the 90’s. And phones were getting hacked back when we had pay to use phone booths. Same as now.
Turning off location services will not prevent the telcos from locating your position. The cell signal itself can be used to find your position.
(By the way, this information was included in the article you’re commenting on.)
Mobile phone companies: the stalker’s friends.
Question for consideration: Could location be considered an authentication factor? Is “where you are” something you are? For sure location is personally identifiable information.
Perhaps an alternative to removing the SIM card would be to use a EU provider that has to obey to GDPR (the “transaction” should still be considered to be in the EU) and a virtual local phone number, like a Google voice.
@Brian: is this common in other countries (ex.: Canada)?
You could set it up on your home wifi network, connect via vpn, and route calls and texts that way. Super inconvenient PITA, but realistically, as long as you’re carrying it, you’re relying on someone’s promise not to do something profitable.