Your mobile phone is giving away your approximate location all day long. This isn’t exactly a secret: It has to share this data with your mobile provider constantly to provide better call quality and to route any emergency 911 calls straight to your location. But now, the major mobile providers in the United States — AT&T, Sprint, T-Mobile and Verizon — are selling this location information to third party companies — in real time — without your consent or a court order, and with apparently zero accountability for how this data will be used, stored, shared or protected.
Think about what’s at stake in a world where anyone can track your location at any time and in real-time. Right now, to be free of constant tracking the only thing you can do is remove the SIM card from your mobile device never put it back in unless you want people to know where you are.
 It may be tough to put a price on one’s location privacy, but here’s something of which you can be sure: The mobile carriers are selling data about where you are at any time, without your consent, to third-parties for probably far less than you might be willing to pay to secure it.
It may be tough to put a price on one’s location privacy, but here’s something of which you can be sure: The mobile carriers are selling data about where you are at any time, without your consent, to third-parties for probably far less than you might be willing to pay to secure it.
The problem is that as long as anyone but the phone companies and law enforcement agencies with a valid court order can access this data, it is always going to be at extremely high risk of being hacked, stolen and misused.
Consider just two recent examples. Earlier this month The New York Times reported that a little-known data broker named Securus was selling local police forces around the country the ability to look up the precise location of any cell phone across all of the major U.S. mobile networks. Then it emerged that Securus had been hacked, its database of hundreds of law enforcement officer usernames and passwords plundered. We also found out that Securus’ data was ultimately obtained from a California-based location tracking firm LocationSmart.
On May 17, KrebsOnSecurity broke the news of research by Carnegie Mellon University PhD student Robert Xiao, who discovered that a LocationSmart try-before-you-buy opt-in demo of the company’s technology was wide open — allowing real-time lookups from anyone on anyone’s mobile device — without any sort of authentication, consent or authorization.
Xiao said it took him all of about 15 minutes to discover that LocationSmart’s lookup tool could be used to track the location of virtually any mobile phone user in the United States.
Securus seems equally clueless about protecting the priceless data to which it was entrusted by LocationSmart. Over the weekend KrebsOnSecurity discovered that someone — almost certainly a security professional employed by Securus — has been uploading dozens of emails, PDFs, password lists and other files to Virustotal.com — a service owned by Google that can be used to scan any submitted file against dozens of commercial antivirus tools.
Antivirus companies willingly participate in Virustotal because it gives them early access to new, potentially malicious files being spewed by cybercriminals online. Virustotal users can submit suspicious files of all kind; in return they’ll see whether any of the 60+ antivirus tools think the file is bad or benign.
One basic rule that all Virustotal users need to understand is that any file submitted to Virustotal is also available to customers who purchase access to the service’s file repository. Nevertheless, for the past two years someone at Securus has been submitting a great deal of information about the company’s operations to Virustotal, including copies of internal emails and PDFs about visitation policies at a number of local and state prisons and jails that made up much of Securus’ business.

Some of the many, many files uploaded to Virustotal.com over the years by someone at Securus Technologies.
One of the files, submitted on April 27, 2018, is titled “38k user pass microsemi.com – joomla_production.mic_users_blockedData.txt”. This file includes the names and what appear to be hashed/scrambled passwords of some 38,000 accounts — supposedly taken from Microsemi, a company that’s been called the largest U.S. commercial supplier of military and aerospace semiconductor equipment.
Many of the usernames in that file do map back to names of current and former employees at Microsemi. KrebsOnSecurity shared a copy of the database with Microsemi, but has not yet received a reply. Securus also has not responded to requests for comment.
These files that someone at Securus apparently submitted regularly to Virustotal also provide something of an internal roadmap of Securus’ business dealings, revealing the names and login pages for several police departments and jails across the country, such as the Travis County Jail site’s Web page to access Securus’ data.
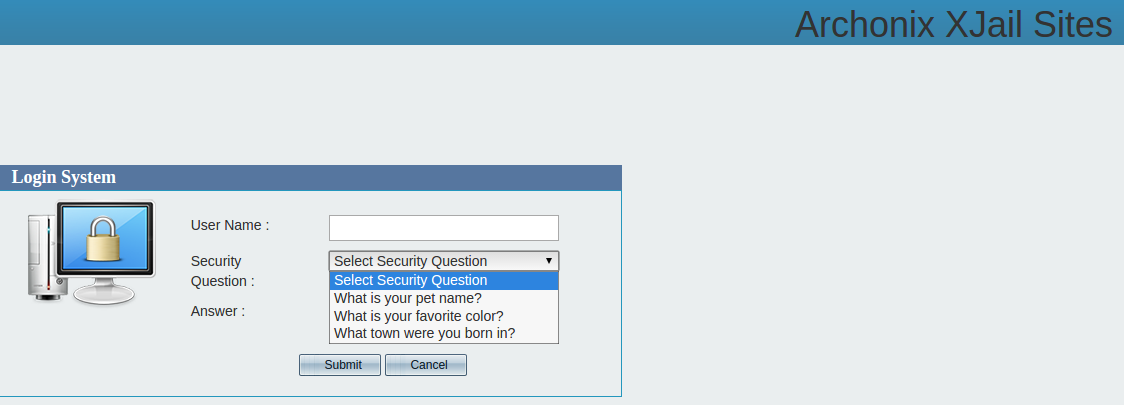
Check out the screen shot below. Notice that forgot password link there? Clicking that prompts the visitor to enter their username and to select a “security question” to answer. There are but three questions: “What is your pet’s name? What is your favorite color? And what town were you born in?” There don’t appear to be any limits on the number of times one can attempt to answer a secret question.
Given such robust, state-of-the-art security, how long do you think it would take for someone to figure out how to reset the password for any authorized user at Securus’ Travis County Jail portal?
Yes, companies like Securus and Location Smart have been careless with securing our prized location data, but why should they care if their paying customers are happy and the real-time data feeds from the mobile industry keep flowing?
No, the real blame for this sorry state of affairs comes down to AT&T, Sprint, T-Mobile and Verizon. T-Mobile was the only one of the four major providers that admitted providing Securus and LocationSmart with the ability to perform real-time location lookups on their customers. The other three carriers declined to confirm or deny that they did business with either company.
As noted in my story last Thursday, LocationSmart included the logos of the four carriers on their home page — in addition to those of several other major firms (that information is no longer available on the company’s site, but it can still be viewed by visiting this historic record of it over at the Internet Archive).
Now, don’t think for a second that these two tiny companies are the only ones with permission from the mobile giants to look up such sensitive information on demand. At a minimum, each one of these companies can in theory resell (or leak) this information and access to others. On 15 May, ZDNet reported that Securus was getting its data from the carriers by going through an intermediary: 3Cinteractive, which was getting it from LocationSmart.
However, it is interesting that the first insight we got that the mobile firms were being so promiscuous with our private location data came in the Times story about law enforcement officials seeking the ability to access any mobile device’s location data in real time.
All technologies are double-edged swords, which means that each can be used both for good and malicious ends. As much as police officers may wish to avoid the hassle and time constraints of having to get a warrant to determine the precise location of anyone they please whenever they wish, those same law enforcement officers should remember that this technology works both ways: It also can just as easily be abused by criminals to track the real-time movements of police and their families, informants, jurors, witnesses and even judges.
Consider the damage that organized crime syndicates — human traffickers, drug smugglers and money launderers — could inflict armed with an app that displays the precise location of every uniformed officer from within 300 ft to across the country. All because they just happened to know the cell phone number tied to each law enforcement official.
Maybe you have children or grandchildren who — like many of their peers these days — carry a mobile device at all times for safety and for quick communication with parents or guardians. Now imagine that anyone in the world has the instant capability to track where your kid is at any time of day. All they’d need is your kid’s digits.
Maybe you’re the current or former target of a stalker, jilted ex-spouse, or vengeful co-worker. Perhaps you perform sensitive work for the government. All of the above-mentioned parties and many more are put at heightened personal risk by having their real-time location data exposed to commercial third parties.
Some people might never sell their location data for any price: I suspect most of us would like this information always to be private unless and until we change the defaults (either in a binary “on/off” way or app-specific). On the other end of the spectrum there are probably plenty of people who don’t care one way or another provided that sharing their location information brings them some real or perceived financial or commercial benefit.
The point is, for many of us location privacy is priceless because, without it, almost everything else we’re doing to safeguard our privacy goes out the window.
And this sad reality will persist until the mobile providers state unequivocally that they will no longer sell or share customer location data without having received and validated some kind of legal obligation — such as a court-ordered subpoena.
But even that won’t be enough, because companies can and do change their policies all the time without warning or recourse (witness the current reality). It won’t be enough until lawmakers in this Congress step up and do their jobs — to prevent the mobile providers from selling our last remaining bastion of privacy in the free world to third party companies who simply can’t or won’t keep it secure.
The next post in this series will examine how we got here, and what Congress and federal regulators have done and might do to rectify the situation.
Update, May 23, 12:34 am ET: Securus responded with the following comment:
“Securus Technologies does not use the Google tool, Virustotal.com as part of our normal business practice for confidential information. We use other antivirus tools that meet our high standards for security and reliability. Importantly,Virustotal.com will associate a file with a URL or domain merely because the URL or domain is included in the file. Our initial review concluded that the overwhelming majority of files that Virustotal.com associates with www.securustech.net were not uploaded by Securus. Our review also showed that a few employees accessed the site in an abundance of caution to verify that outside emails were virus free. As a result, many of the files indicated in your article were not directly uploaded by Securus and/or are not Securus documents. A vast majority of files merely mention our URL. Our review also determined that the Microsemi file mentioned in your article is only associated with Securus because two Securus employee email addresses were included in the file, and not because Securus uploaded the file.”
“Because we take the security of information very seriously, we are continuing to look into this matter to ensure proper procedures are followed to protect company and client information. We will update you if we learn that procedures were not followed.”




We talk here about two different things and I am not sure whether removing the SIM card is the solution. First, we got the data that goes to Google. That data is generated using the cell’s accelerometer and magnetometer. If the cell is in flight modus and later on turned online again, the data is sent in a batch to Google. Whether that can be prevented by switching the cell off unfortunately has not been discussed in the research paper “PinMe: Tracking a Smartphone User around the World”. I also doubt whether removing the SIM card would prevent a batch data transfer upon reloading the SIM card.
The second issue is much simpler and revolves around the cell searching the nearest tower. Here, even if you remove the SIM card, the cell still will search for the nearest tower, since the IMSI number of the cell rather than the SIM card is relevant. Also, switching off the cell or even removing the battery (provided that works at all with a smartphone, which in most cases it will not) does not help. All cells have a built-in backup battery and hence will continue searching for the nearest tower. The only way to prevent this is to switch off your cell and put it into a “cell phone signal blocker pouch” (basically a Faraday cage). It costs some $2 (sorry: $20 is a rip-off).
So, for the cell tower, a solution is available. However, if you insist on having a smartphone, there is no way you can prevent real time tracking by Google (probably also by Apple for iOS). Consequently, the best solution is having a dumb / feature phone and a signal blocker pouch.
If you live in certain countries, you can get voicemail notifications of your cell on your pager and call back from a landline or from a feature phone. That, obviously, is the most elegant solution to the data-tracking problem.
Thanks.
That’s (almost) the way I use it (switching off the (dumb) phone, and checking the voice mail notifications at intervals). The “cell phone signal blocker pouch” idea is new to me – I’ll consider using it 😉
Bryan – I don’t think you’ll convince Congress to take any action until it can be shown that the privacy issues directly affect them as well. Case in point the revelation of fake comments on the FCC’s net neutrality rule affecting Senators Merkley and Toomey recently. If any researchers with access to leaked data were to identify tracking data for specific lawmakers or their families, and present it to them (discreetly and privately of course) in a format they can understand, it just might jump-start a discussion.
Sadly I doubt that would work for some congresscritters. They would scream “fake news!” or “hackers!” and demand the appropriate TLA start an investigation… into you.
Not too long ago I saw a video of a congresscritter pursued down a hallway and stairwell to try and discuss something he was involved with and all he did is run faster while yelling “fake news!” over and over like that was a valid response. He even answered “fake news” to the question “why are you running?”
Unfortunately it appears that some parts of the country no longer want to elect adults to represent them in congress.
Oh no, they’ve already done that before. I forget which congress critter did, but props to them for actually looking into how they were tracked and complaining. Didn’t do any good but..
If your European, whos “roaming” in any of these networks, they can get nice court battle in context of GDPR.
I often get lots of spam calls right after I pick up my phone and start changing locations. I wonder if spammers were automating this.
https://www.zerohedge.com/news/2018-05-23/more-police-state-surveillance-courtesy-pentagon
Yes you are the product …… of your environment.
Sentence is broken: “The problem is that as long as anyone but the phone companies and law enforcement agencies with a valid court order can access this data…”
Probably meant to say that anyone – not only the cops – can access this data…
Latest Google phones such as the Pixel 2 have a SIM built-in that you cannot remove. You can add another SIM, but you won’t be able to remove/disable the internal one.
If you really want to fly under the radar, turn the phone off (just to save battery, but we know it’s not really off), and wrap it in a Faraday bag. Just make sure any companions traveling with you do the same, and you have an older vehicle without any tracking devices.
In the UK the equivalent to LocationSmart is a company called Pageone (pageone.co.uk/lbsterms), owned by Capita Plc, which kindly sells our mobile location to third parties on our behalf.
Hey Brian – From LocationSmart’s website.. News/ patent for its product. Comeplete lie! I don’t recall being able to manage the selling of ‘my’ location data by my carrier! I signed up for cell service…not selling of my personal location 24/7…When will this erosion of basic privacy rights end?
“The location management system provides these mobile users with a comprehensive understanding of the location permissions and notifications and hence the location transactions associated with their wireless device and with the ability to manage it in a way that makes sense for their personal or business needs. ”
http://patft.uspto.gov/netacgi/nph-Parser?Sect1=PTO2&Sect2=HITOFF&p=1&u=%2Fnetahtml%2FPTO%2Fsearch-bool.html&r=1&f=G&l=50&co1=AND&d=PTXT&s1=9,832,633.PN.&OS=PN/9,832,633&RS=PN/9,832,633
If cell providers are selling location data, and every kid today has a cell phone, how is this not a COPPA violation:
https://www.ftc.gov/tips-advice/business-center/guidance/complying-coppa-frequently-asked-questions#Geolocation%20Data
Selling user data to third party sources is not acceptable. Because they might not know how these third parties use the data.