LocationSmart, a U.S. based company that acts as an aggregator of real-time data about the precise location of mobile phone devices, has been leaking this information to anyone via a buggy component of its Web site — without the need for any password or other form of authentication or authorization — KrebsOnSecurity has learned. The company took the vulnerable service offline early this afternoon after being contacted by KrebsOnSecurity, which verified that it could be used to reveal the location of any AT&T, Sprint, T-Mobile or Verizon phone in the United States to an accuracy of within a few hundred yards.
![]()
On May 10, The New York Times broke the news that a different cell phone location tracking company called Securus Technologies had been selling or giving away location data on customers of virtually any major mobile network provider to a sheriff’s office in Mississippi County, Mo.
On May 15, ZDnet.com ran a piece saying that Securus was getting its data through an intermediary — Carlsbad, CA-based LocationSmart.
Wednesday afternoon Motherboard published another bombshell: A hacker had broken into the servers of Securus and stolen 2,800 usernames, email addresses, phone numbers and hashed passwords of authorized Securus users. Most of the stolen credentials reportedly belonged to law enforcement officers across the country — stretching from 2011 up to this year.
Several hours before the Motherboard story went live, KrebsOnSecurity heard from Robert Xiao, a security researcher at Carnegie Mellon University who’d read the coverage of Securus and LocationSmart and had been poking around a demo tool that LocationSmart makes available on its Web site for potential customers to try out its mobile location technology.
LocationSmart’s demo is a free service that allows anyone to see the approximate location of their own mobile phone, just by entering their name, email address and phone number into a form on the site. LocationSmart then texts the phone number supplied by the user and requests permission to ping that device’s nearest cellular network tower.
Once that consent is obtained, LocationSmart texts the subscriber their approximate longitude and latitude, plotting the coordinates on a Google Street View map. [It also potentially collects and stores a great deal of technical data about your mobile device. For example, according to their privacy policy that information “may include, but is not limited to, device latitude/longitude, accuracy, heading, speed, and altitude, cell tower, Wi-Fi access point, or IP address information”].
But according to Xiao, a PhD candidate at CMU’s Human-Computer Interaction Institute, this same service failed to perform basic checks to prevent anonymous and unauthorized queries. Translation: Anyone with a modicum of knowledge about how Web sites work could abuse the LocationSmart demo site to figure out how to conduct mobile number location lookups at will, all without ever having to supply a password or other credentials.
“I stumbled upon this almost by accident, and it wasn’t terribly hard to do,” Xiao said. “This is something anyone could discover with minimal effort. And the gist of it is I can track most peoples’ cell phone without their consent.”
Xiao said his tests showed he could reliably query LocationSmart’s service to ping the cell phone tower closest to a subscriber’s mobile device. Xiao said he checked the mobile number of a friend several times over a few minutes while that friend was moving and found he was then able to plug the coordinates into Google Maps and track the friend’s directional movement.
“This is really creepy stuff,” Xiao said, adding that he’d also successfully tested the vulnerable service against one Telus Mobility mobile customer in Canada who volunteered to be found.
Before LocationSmart’s demo was taken offline today, KrebsOnSecurity pinged five different trusted sources, all of whom gave consent to have Xiao determine the whereabouts of their cell phones. Xiao was able to determine within a few seconds of querying the public LocationSmart service the near-exact location of the mobile phone belonging to all five of my sources.
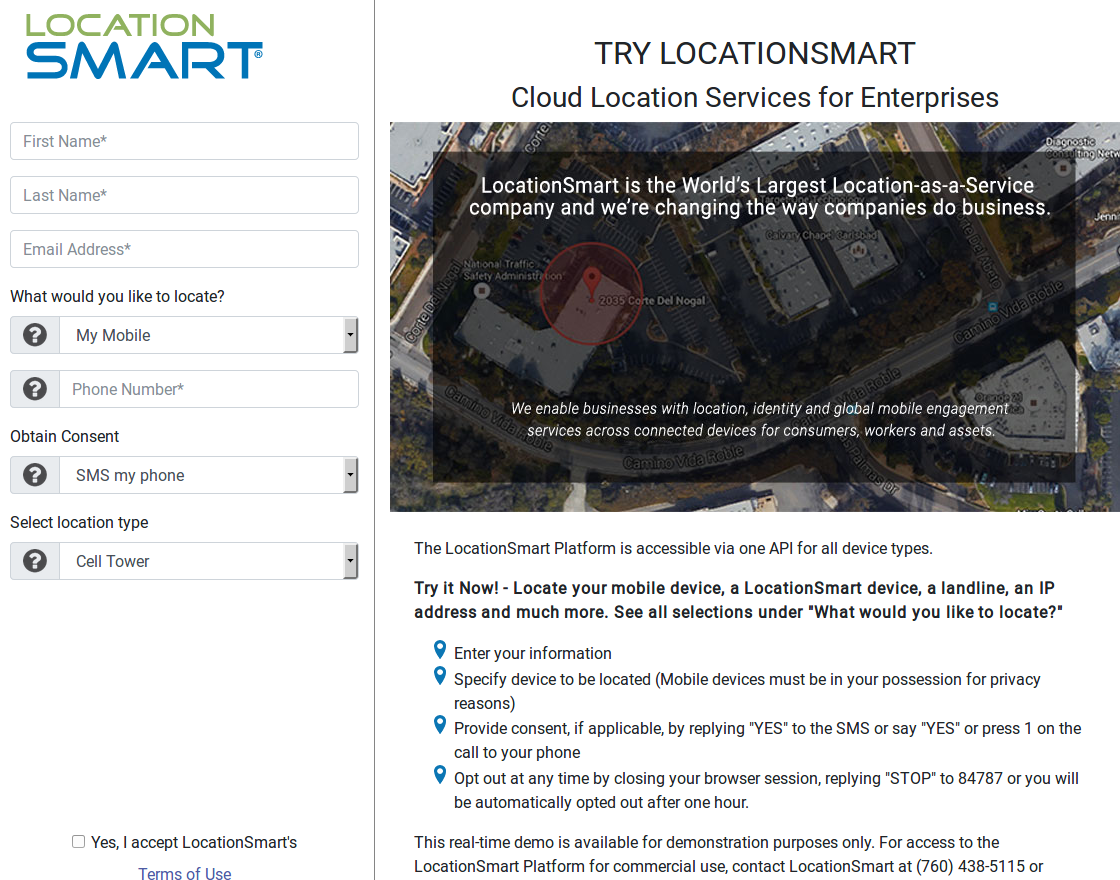
LocationSmart’s demo page.
One of those sources said the longitude and latitude returned by Xiao’s queries came within 100 yards of their then-current location. Another source said the location found by the researcher was 1.5 miles away from his current location. The remaining three sources said the location returned for their phones was between approximately 1/5 to 1/3 of a mile at the time.
Reached for comment via phone, LocationSmart Founder and CEO Mario Proietti said the company was investigating.
“We don’t give away data,” Proietti said. “We make it available for legitimate and authorized purposes. It’s based on legitimate and authorized use of location data that only takes place on consent. We take privacy seriously and we’ll review all facts and look into them.”
LocationSmart’s home page features the corporate logos of all four the major wireless providers, as well as companies like Google, Neustar, ThreatMetrix, and U.S. Cellular. The company says its technologies help businesses keep track of remote employees and corporate assets, and that it helps mobile advertisers and marketers serve consumers with “geo-relevant promotions.”

LocationSmart’s home page lists many partners.
It’s not clear exactly how long LocationSmart has offered its demo service or for how long the service has been so permissive; this link from archive.org suggests it dates back to at least January 2017. This link from The Internet Archive suggests the service may have existed under a different company name — loc-aid.com — since mid-2011, but it’s unclear if that service used the same code. Loc-aid.com is one of four other sites hosted on the same server as locationsmart.com, according to Domaintools.com.
LocationSmart’s privacy policy says the company has security measures in place…”to protect our site from the loss or misuse of information that we have collected. Our servers are protected by firewalls and are physically located in secure data facilities to further increase security. While no computer is 100% safe from outside attacks, we believe that the steps we have taken to protect your personal information drastically reduce the likelihood of security problems to a level appropriate to the type of information involved.”
But these assurances may ring hollow to anyone with a cell phone who’s concerned about having their physical location revealed at any time. The component of LocationSmart’s Web site that can be abused to look up mobile location data at will is an insecure “application programming interface” or API — an interactive feature designed to display data in response to specific queries by Web site visitors.
Although the LocationSmart’s demo page required users to consent to having their phone located by the service, LocationSmart apparently did nothing to prevent or authenticate direct interaction with the API itself.
API authentication weaknesses are not uncommon, but they can lead to the exposure of sensitive data on a great many people in a short period of time. In April 2018, KrebsOnSecurity broke the story of an API at the Web site of fast-casual bakery chain PaneraBread.com that exposed the names, email and physical addresses, birthdays and last four digits of credit cards on file for tens of millions of customers who’d signed up for an account at PaneraBread to order food online.
In a May 9 letter sent to the top four wireless carriers and to the U.S. Federal Communications Commission in the wake of revelations about Securus’ alleged practices, Sen. Ron Wyden (D-Ore.) urged all parties to take “proactive steps to prevent the unrestricted disclosure and potential abuse of private customer data.”
“Securus informed my office that it purchases real-time location information on AT&T’s customers — through a third party location aggregator that has a commercial relationship with the major wireless carriers — and routinely shares that information with its government clients,” Wyden wrote. “This practice skirts wireless carrier’s legal obligation to be the sole conduit by which the government may conduct surveillance of Americans’ phone records, and needlessly exposes millions of Americans to potential abuse and unchecked surveillance by the government.”
Securus, which reportedly gets its cell phone location data from LocationSmart, told The New York Times that it requires customers to upload a legal document — such as a warrant or affidavit — and to certify that the activity was authorized. But in his letter, Wyden said “senior officials from Securus have confirmed to my office that it never checks the legitimacy of those uploaded documents to determine whether they are in fact court orders and has dismissed suggestions that it is obligated to do so.”
Securus did not respond to requests for comment.
THE CARRIERS RESPOND
It remains unclear what, if anything, AT&T, Sprint, T-Mobile and Verizon plan to do about any of this. A third-party firm leaking customer location information not only would almost certainly violate each mobile providers own stated privacy policies, but the real-time exposure of this data poses serious privacy and security risks for virtually all U.S. mobile customers (and perhaps beyond, although all my willing subjects were inside the United States).
None of the major carriers would confirm or deny a formal business relationship with LocationSmart, despite LocationSmart listing them each by corporate logo on its Web site.
AT&T spokesperson Jim Greer said AT&T does not permit the sharing of location information without customer consent or a demand from law enforcement.
“If we learn that a vendor does not adhere to our policy we will take appropriate action,” Greer said.
T-Mobile referred me to their privacy policy, which says T-Mobile follows the “best practices” document (PDF) for subscriber location data as laid out by the CTIA, the international association for the wireless telecommunications industry.
A T-Mobile spokesperson said that after receiving Sen. Wyden’s letter, the company quickly shut down any transaction of customer location data to Securus and LocationSmart.
“We take the privacy and security of our customers’ data very seriously,” the company said in a written statement. “We have addressed issues that were identified with Securus and LocationSmart to ensure that such issues were resolved and our customers’ information is protected. We continue to investigate this.”
Verizon also referred me to their privacy policy.
Sprint officials shared the following statement:
“Protecting our customers’ privacy and security is a top priority, and we are transparent about our Privacy Policy. To be clear, we do not share or sell consumers’ sensitive information to third parties. We share personally identifiable geo-location information only with customer consent or in response to a lawful request such as a validated court order from law enforcement.”
“We will answer the questions raised in Sen. Wyden’s letter directly through appropriate channels. However, it is important to note that Sprint’s relationship with Securus does not include data sharing, and is limited to supporting efforts to curb unlawful use of contraband cellphones in correctional facilities.”
WHAT NOW?
Stephanie Lacambra, a staff attorney with the the nonprofit Electronic Frontier Foundation, said that wireless customers in the United States cannot opt out of location tracking by their own mobile providers. For starters, carriers constantly use this information to provide more reliable service to the customers. Also, by law wireless companies need to be able to ascertain at any time the approximate location of a customer’s phone in order to comply with emergency 911 regulations.
But unless and until Congress and federal regulators make it more clear how and whether customer location information can be shared with third-parties, mobile device customers may continue to have their location information potentially exposed by a host of third-party companies, Lacambra said.
“This is precisely why we have lobbied so hard for robust privacy protections for location information,” she said. “It really should be only that law enforcement is required to get a warrant for this stuff, and that’s the rule we’ve been trying to push for.”
Chris Calabrese is vice president of the Center for Democracy & Technology, a policy think tank in Washington, D.C. Calabrese said the current rules about mobile subscriber location information are governed by the Electronic Communications Privacy Act (ECPA), a law passed in 1986 that hasn’t been substantially updated since.
“The law here is really out of date,” Calabrese said. “But I think any processes that involve going to third parties who don’t verify that it’s a lawful or law enforcement request — and that don’t make sure the evidence behind that request is legitimate — are hugely problematic and they’re major privacy violations.”
“I would be very surprised if any mobile carrier doesn’t think location information should be treated sensitively, and I’m sure none of them want this information to be made public,” Calabrese continued. “My guess is the carriers are going to come down hard on this, because it’s sort of their worst nightmare come true. We all know that cell phones are portable tracking devices. There’s a sort of an implicit deal where we’re okay with it because we get lots of benefits from it, but we all also assume this information should be protected. But when it isn’t, that presents a major problem and I think these examples would be a spur for some sort of legislative intervention if they weren’t fixed very quickly.”
For his part, Xiao says we’re likely to see more leaks from location tracking companies like Securus and LocationSmart as long as the mobile carriers are providing third party companies any access to customer location information.
“We’re going to continue to see breaches like this happen until access to this data can be much more tightly controlled,” he said.
Sen. Wyden issued a statement on Friday in response to this story:
“This leak, coming only days after the lax security at Securus was exposed, demonstrates how little companies throughout the wireless ecosystem value Americans’ security. It represents a clear and present danger, not just to privacy but to the financial and personal security of every American family. Because they value profits above the privacy and safety of the Americans whose locations they traffic in, the wireless carriers and LocationSmart appear to have allowed nearly any hacker with a basic knowledge of websites to track the location of any American with a cell phone.”
“The threats to Americans’ security are grave – a hacker could have used this site to know when you were in your house so they would know when to rob it. A predator could have tracked your child’s cell phone to know when they were alone. The dangers from LocationSmart and other companies are limitless. If the FCC refuses to act after this revelation then future crimes against Americans will be the commissioners’ heads.”
Sen. Mark Warner (D-Va.) also issued a statement:
“This is one of many developments over the last year indicating that consumers are really in the dark on how their data is being collected and used,” Sen. Warner said. “It’s more evidence that we need 21st century rules that put users in the driver’s seat when it comes to the ways their data is used.”
In a statement provided to KrebsOnSecurity on Friday, LocationSmart said:
“LocationSmart provides an enterprise mobility platform that strives to bring secure operational efficiencies to enterprise customers. All disclosure of location data through LocationSmart’s platform relies on consent first being received from the individual subscriber. The vulnerability of the consent mechanism recently identified by Mr. Robert Xiao, a cybersecurity researcher, on our online demo has been resolved and the demo has been disabled. We have further confirmed that the vulnerability was not exploited prior to May 16th and did not result in any customer information being obtained without their permission.”
“On that day as many as two dozen subscribers were located by Mr. Xiao through his exploitation of the vulnerability. Based on Mr. Xiao’s public statements, we understand that those subscribers were located only after Mr. Xiao personally obtained their consent. LocationSmart is continuing its efforts to verify that not a single subscriber’s location was accessed without their consent and that no other vulnerabilities exist. LocationSmart is committed to continuous improvement of its information privacy and security measures and is incorporating what it has learned from this incident into that process.”
It’s not clear who LocationSmart considers “customers” in the phrase, “did not result in any customer information being obtained without their permission,” since anyone whose location was looked up through abuse of the service’s buggy API could not fairly be considered a “customer.”
Update, May 18, 11:31 AM ET: Added comments from Sens. Wyden and Warner, as well as updated statements from LocationSmart and T-Mobile.




Same company had an “incident” few years ago
https://theintercept.com/2015/11/11/securus-hack-prison-phone-company-exposes-thousands-of-calls-lawyers-and-clients/
Seems like LocationSmart/Loc-Aid/Technocom Corporation have been at it for a while
https://www.technologyreview.com/s/426324/startup-turns-your-cell-phone-number-into-a-location-fix/
https://venturebeat.com/2012/09/13/locaid-launches-internet-and-mobile-location-tracking-service/
https://www.seeker.com/website-finds-your-location-using-phone-number-1765639951.html
FYI At&t used some form of Loca
It appears the free demo has been disabled?
What, you mean just like Brian says in this article?
It’s in the first paragraph of the story…
“The company took the vulnerable service offline early this afternoon after being contacted by KrebsOnSecurity”
DOH ! thanks for bringing that fact to my attention !
Seems like LocationSmart/Loc-Aid/Technocom Corporation have been at it for a while
https : // www technologyreview com /s/426324/startup-turns-your-cell-phone-number-into-a-location-fix/
https : // venturebeat com /2012/09/13/locaid-launches-internet-and-mobile-location-tracking-service/
https//web. archive. org/web/20140320074823/http://www locationsmart. net:80/platform/whylocationsmart/
https : // http://www.seeker.com /website-finds-your-location-using-phone-number-1765639951.html
http : // archive.is / 1hIvv
FYI At&t
uses some form of LocationSmart for entreprise customers
http: // archive.is / JytjI
Congress is clueless.
Feckless, too.
LocationSmart still has the buttons in place on their website but they go through a loop and do nothing. There is no explanation and of course nothing under recent news except for glowing reports of how good they are at finding locations…
WTF, Brian! Why this company even existed?
There are so many providers in this space who have vulnerabilities, stretching back to 2006.
https://publications.parliament.uk/pa/cm200506/cmhansrd/vo060314/debtext/60314-12.htm
“To extend that to adults, The Guardian journalist Ben Goldacre showed recently that someone needs possession of another person’s mobile phone for only a couple of minutes to appear to give the consent required under mobile phone companies’ current procedures. The person he was tracking never got any of the warning messages that were meant to have been sent to her. Even more scarily, a hacker’s website has recently published information telling how to spoof consent without even having to have temporary possession of the target’s phone; all that is needed is the number. If someone has a person’s number, he can track them. It is not a problem. I know where the website is, but I am not going to tell Members. It is possible to track people just through their phone numbers.”
LocationSmart are not unique and I guarantee there are others who can exploited.
Can someone please ensure there are finally consequences for this? The phone providers have had over a decade to resolve these issues and have been well aware of the problems.
…”location found by the researcher was [xx] miles away”…
Likely dependant on the distance between the tower and phone. One instance of what I was told is that towers are every 3 miles (on average; but, I don’t seem to see them that close).
Last post
not sure if Brian can delete the first one since I made a mistake
LocationSmart has had the information available publically since 2011
https://web.archive.org/web/*/https://instantlocatedemo.loc-aid.com/
Good find. That domain loc-aid.com is one of four others currently hosted on the same server as locationsmart.com
One important point missed. Law enforcement also uses cell phones, and based on what is described here suggests undercover agents can also be easily tracked and are at risk. Joe Citizen tracking is all of us.
My first thought as well. This could really backfire on law enforcement officers .
If a law enforcement officer is working with a CI (confidential informant), the bad guys could track the CI.
Incoming lawsuit lol
The rabbit hole goes even deeper according to comments on Hacker News: https://news.ycombinator.com/item?id=17081684
Many large companies have (anecdotally) been taking advantage of this information for a while now. Hedge funds were mentioned as one example, using this information to track the location of millions of customers to various businesses and using this data to make stock trade decisions.
One thing I wasn’t clear about – did they manage to hack the demo so that the SMS confirmation was skipped?
Yes, this is in the story:
“Although the LocationSmart’s demo page required users to consent to having their phone located by the service, LocationSmart apparently did nothing to prevent or authenticate direct interaction with the API itself.”
Researcher has published details here : https://www.robertxiao.ca/hacking/locationsmart/
I want to know if we can see if they are tracking our personal phones\work phones and if we can opt out. I’m not criminal, but privacy is privacy. If anyone wants my data, get a damned warrant! Document it. They shouldn’t be making money of OUR INFORMATION. Why do we have to just roll over and let them do this?
Tell that to Ajit Pai.
If you want the services for free, such as maps, you’ve opted in. If you want weather, and other apps which use location data. All the privacy terms merge your consent with Google, for instance, with its affiliates, to deliver better ads to you and improve its services.
Thank you for your report. Clear and concise, and raising policy issues that need more than just a moment’s thought.
We have all consented to have our locations tracked to some degree, and emergency 911 service is a critical service.
But when such government agencies as the IRS and OPM, not to mention numerous state and local agencies, fail to take reasonable precautions with our most sensitive information, what incentives do private companies have to do better?
And the less said about Equifax and its affiliates, the better…
And a big thank you to CTIA for LocationSmart
http://archive.is/z1ZnF
http://files.ctia.org/pdf/LOC_AID_Privacy_Guidelines_for_Developers_v3_03_2010.pdf
Before reading this, I’d say nothing would have surprised me… but really?? Mobile phone carriers just let anyone have our location data??
That’s the most f’up part of the story!
We are living in a time where commercial Enterprises are allowed to exploit every bit of information that they can collect about people. And, with current technology let alone technology that is coming forward rapidly, there is almost nothing that people do in their lives now that is not collected. Because the mega corporations and Banks control both parties in Congress and most regulatory agencies, anyone who thinks that this is going to change is dreaming.
Towers were initially installed at five Mile increments. The average cell phone had a range of six miles, to ten miles. That ran too three towers. As we progressed to 3g and beyond, the ranges became shorter, and crowding of the bandwidth became common. And remember part of the problem is every cell phone hunts for a tower to listen for it’s name to be called. Every phone plays tag with the tower. Every tower plays tag with it’s network, etc, etc,… The real question should be, who doesn’t have a record. Remember, you write a check, scan a card, pay cash, all this is sent to a clearing house, a credit agency, a bank, etc etc,etc…and much is sent over phones, and those databases are not always kept or made by the Rhodes scholars, they may be from the pimpley faced kid down the street.
A cellular network is shaped like a honeycomb. Phones do not have range. Towers are not methodically placed 3 miles or 5 miles apart. The center of a cell would determine the range to the next tower. Stating that all have 3 to talk with. Yes if it is a 3 sector site meaning antennas on xyz. The range of any cellular network varies based on many factors. Equipment type purpose of said site. Such as one inside a building wouldn’t have 3 neighbors. In some cases not even designed to hand off outside of the building. Handsets are very low powered today. As well as a cell site compared to analog technology.
Regardless the varied distance of this report doesn’t justify the hideous abuse of our data. The system they are pulling all thus data from was intended to provide E911 services. Not allow stalkers and what ever lurk after you.
This data dump is a violation of so many laws! And to top it. We actually pay for this. Look at your cellphone bill. E911 charges fund this company.
A warrant is required to track a cell phone! Flat out!
I’ll only address your last line, because I am tired.
Unfortunately, a warrant, signed by a judge, upon a sworn affidavit of probable cause, is not required to track a cell phone.
The courts and Congress have said a subpoena or law enforcement request is sufficient.
The wireless carriers don’t challenge the subpoenas and affidavits, anyway. They also do not check if they are authentic or notify customers that their information was given to law enforcement.
Why? Because the courts and Congress haven’t told them it’s necessary.
Unfortunately, you are wrong. A handheld cell phone has a limited range. Cell phone towers have a limited reception area. And structures, and landformations limit reception. Even sat phones loose reception. The best example, take a cell phone and go six miles off a coast line, then try your map application. It won’t work unless you are on a vessle with a repeater. Second best example, get on a airplane without a repeater and fly over 30k feet. No reception. Or take a hike in the Rockies, away from the main roads. One side of a mountain you can call, the other is a problem. And even with a sat phone, that tree or hill that cuts you off from the sky cuts your reception. For us city dwellers. Even the streets downtown can be problematic. The reflections off the structures can throw you from tower to tower changing your call routing. And for clairity, still cannot beat the old hard wire.
And, another bit. I live in the Midwest, it’s storm time. The sirens are not individual ly powered. Tornados frequent the area. And counties around here utilize a 911 system of location tracking. My local police cannot track a 911 to my location, without a warrant, but they can warn me of inclimate weather. Because every phone on a certain tower in this county, phones home, to say I’m here, in this area. Use this tower to call me. This is done by the phone, it doesn’t matter, attached Verizon, t mobile, they tick a tower in this area, you get the warning.
You want no more of this? A good use of tax dollars.
I thought EMS alerts were pushed to active phones on the cell towers, not run through a database to find which ones were there. That would seem to add multiple points of failure. I’d like to think you’re wrong about the execution can anyone else detail?
I called my carrier to protest and request to opt out of their data sharing arrangement. Verizon tech support is claiming that this information is only shared with third parties if you’ve signed up for their family location tracking service. Conveniently, I have not, so nothing to worry about!
And then, to make sure you’re secure, they’ll help you *turn off GPS* and *sign out of your apple or google maps app*.
Yeah. I didn’t really figure tech support would understand how much information a time-pressed programming team will open up to a ‘trusted partner’ with a big wallet. I did hope they could tell the difference between them sharing my tower based data with insecure third parties, and how I use it for my own purposes.
Turning off GPS only disables location tracking for apps.
Your phone and ISP always know where you are and you cannot stop it.
I have verizon and have had everything i can disabled since day 1. This demo worked based on my cell towers and my phone number it pinpointed down to about 100 feet from where i was at tbe time. What the tech support peoole said is bullsh*t they lied to you ☹.
Yeah, I figured.
Brian : exploit or no exploit, why does this company have this data at all? Isn’t that the bigger story ? I feel like that was glossed over.
I totally agree, first we seem to forget that telecom provider can track you anywhere, any time. Second, why are they allow to share that data without my approval.
Glossed over, really? I spent two days quizzing the mobile providers and the companies involved about this and got very little response (which is included as an entire subsection of the article).
Time will tell what’s really going on here, but I think it’s safe to assume that the privacy policies that customers “opt-in” to just by virtue of using a mobile phone from one of these major providers gives the carriers legal leeway to do this. IANAL, but since every mobile provider that gave a statement mentioned they won’t do this without customer consent — and because it seems unlikely any of the people on whom I tested this had knowingly given consent to do this (they are all security experts) — that seems like a safe assumption.
The phone companies have previously been fined for inappropriate use/exposure of customer information. Given LocationSmart’s response regarding “geo-relevant promotion”, are they providing plausible deniability for the phone companies to profit from geo-tracking? How is the FCC responding?
Brian: speaking of which, I’m happy to be a guinea pig if you need another in the future. I generally have two phones on distinct carriers (and would be happy to pick up a SIM on another for testing).
Not glossed over, but I do agree *that* is the real question. That data brokers lose data is a sad reality, but should surprise nobody. After all, we are not their customers. That they then resell it to others and don’t check privacy or legal policies is also something I’m not surprised with. And those resellers will also lose more data.
But why does LocationSmart has *real time* access to all four national providers in the first place. Why!? Is this the outsourcing of legal requirements?
Also, how do they get ‘my’ email? And even though it is rare, I believe it is still possible to get a mobile phone subscription without email. Or is the form in which you enter the email, just to get the user to enter the email (data mining), instead of acting like verification?
In Nederland the sleepwet will become active, if this is included, big brother will be watching you 24/7
More “head-slap” continuing…..
Hi Brian,
My provider, US mobile, claimed in their support chat that they did not provide information to LocationSmart. Here’s what they wrote:
> Me: Can you unequivocally confirm that companies like LocationSmart cannot and did not access the information of US mobile customers?
> Noor: That’s right. They did not.
Can you confirm that? It seems fishy, since they go through T-mobile for actual service.
Do you really think a low-level support chat person knows anything about this? I doubt it either way.
“Can you confirm that? It seems fishy, since they go through T-mobile for actual service.”
Ask for where it’s located in written policy/Terms of Service/Privacy Policy…since it’s “taken seriously”(TM).
This is like an NSA wet dream.
So what, ISP’s were just handing over bulk data on everyone to third parties? Or does this exploit something like a phone to IP number lookup, or what?
In the industry’s defense, it’s good if your whereabouts are known . . . because fraudulent banking activity can be detected when a flag is raised if you are outside your usual location . . . your car is stolen, it might be found . . . or you drive off a cliff, you might be found sooner than later . . . All the location-based services we enjoy depend on our consent, such as maps and directions, targeted ads [honesty, I prefer them], and you can see where the uber driver is . . . Law enforcement can track truant students. It’s overall better, IMO. Plus, it’s cloud-based, and not based on your GPS, so your battery isn’t getting drained.
Microsoft’s Next Big Challenge? Location, Location, Location
http://fortune.com/2017/11/28/microsoft-azure-cloud-location-services
I translate the response from the company this way:
“Gee! We’re really very sorry to learn that someone (anyone) was able to gain unauthorized access to all of the great masses of insidious and invasive personal location data that we collect WITHOUT PAYING US FOR THE PRIVILEGE. We will definitely fix that right away!”
(To think that any of the crummy companies involved in these nasty games, including but not limited to the carriers, are going to stop selling this data to the highest bidder until legislation forces them to stop is just ludicrous. Data is the new oil.)
test
What happened to my long, beautiful comment?
Let the industry know your location!
Location is cloud-based, not draining your phone’s battery running your GPS.
It would help you find a loved one, if that one drove off a cliff, sooner than later.
The Authorities can track truant students, stolen cars, and prevent bank fraud.
You alredy enjoy maps, directions, weather, and watching where the Uber is on its way to you.
This is missing from my previous comment:
The security is likely to be high. It is good this exploit was discovered, and I think LocationSmart responded fast! because the major companies who might profit from this cloud technology will protect their interests and (2) are nervous of bad publicity, like this story gives. IMO