Identity theft protection firm LifeLock — a company that’s built a name for itself based on the promise of helping consumers protect their identities online — may have actually exposed customers to additional attacks from ID thieves and phishers. The company just fixed a vulnerability on its site that allowed anyone with a Web browser to index email addresses associated with millions of customer accounts, or to unsubscribe users from all communications from the company.
The upshot of this weakness is that cyber criminals could harvest the data and use it in targeted phishing campaigns that spoof LifeLock’s brand. Of course, phishers could spam the entire world looking for LifeLock customers without the aid of this flaw, but nevertheless the design of the company’s site suggests that whoever put it together lacked a basic understanding of Web site authentication and security.
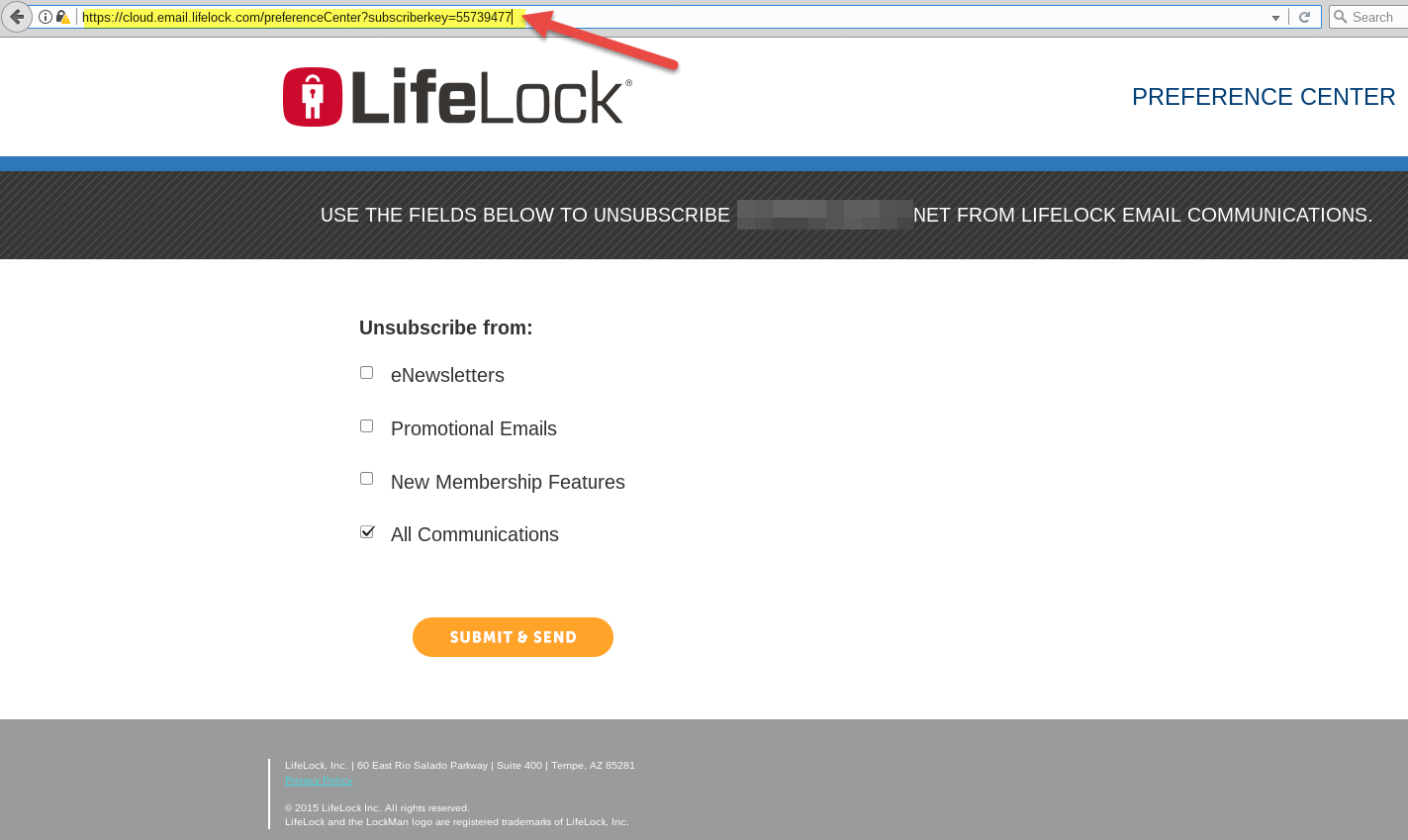
LifeLock’s Web site exposed customer email addresses by tying each customer account to a numeric “subscriberkey” that could be easily enumerated. Pictured above is customer number 55,739,477. Click to enlarge.
Pictured above is a redacted screen shot of one such record (click the image to enlarge). Notice how the format of the link in the browser address bar ends with the text “subscriberkey=” followed by a number. Each number corresponds to a customer record, and the records appear to be sequential. Translation: It would be trivial to write a simple script that pulls down the email address of every LifeLock subscriber.
Security firm Symantec, which acquired LifeLock in November 2016 for $2.3 billion, took LifeLock.com offline shortly after being contacted by KrebsOnSecurity. According to LifeLock’s marketing literature as of January 2017, the company has more than 4.5 million customer accounts.
KrebsOnSecurity was alerted to the glaring flaw by Nathan Reese, a 42-year-old freelance security researcher based in Atlanta who is also a former LifeLock subscriber. Reese said he discovered the data leak after receiving an email to the address he had previously used at LifeLock, and that the message offered him a discount for renewing his membership.
Clicking the “unsubscribe” link at the bottom of the email brought up a page showing his subscriber key. From there, Reese said, he wrote a proof-of-concept script that began sequencing numbers and pulling down email addresses. Reese said he stopped the script after it enumerated approximately 70 emails because he didn’t want to set off alarm bells at LifeLock.
“If I were a bad guy, I would definitely target your customers with a phishing attack because I know two things about them,” Reese said. “That they’re a LifeLock customer and that I have those customers’ email addresses. That’s a pretty sharp spear for my spear phishing right there. Plus, I definitely think the target market of LifeLock is someone who is easily spooked by the specter of cybercrime.”
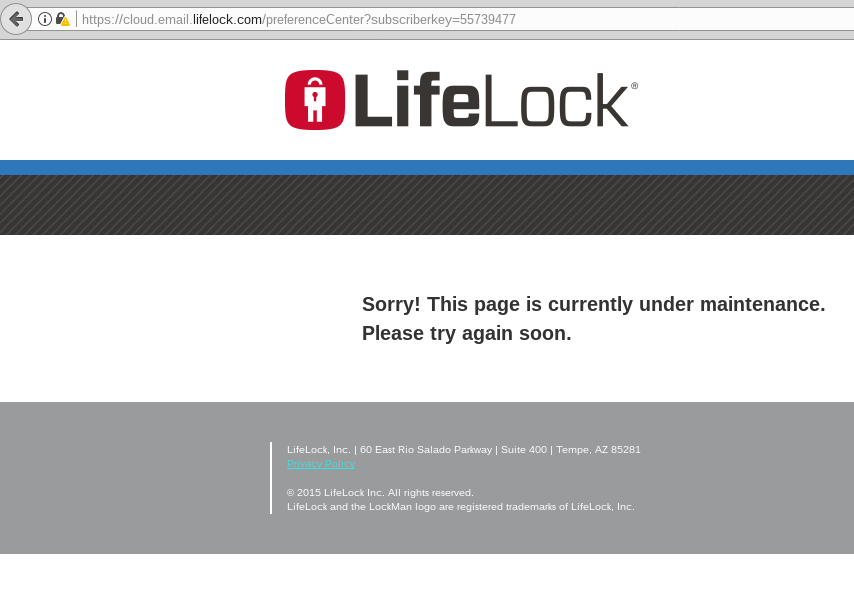
LifeLock’s Web site is currently offline.
Misconfigurations like the one described above are some of the most common ways that companies leak customer data, but they’re also among the most preventable. Earlier this year, KrebsOnSecurity broke a story about a similar flaw at Panerabread.com, which exposed tens of millions of customer records — including names, email and physical addresses, birthdays and the last four digits of the customer’s credit card.
Update, 7:40 p.m.: Corrected the number of LifeLock subscribers based on a 2017 estimate by Symantec.
Update, July 26, 7:32 a.m.: Symantec issued the following statement in response to this article:
This issue was not a vulnerability in the LifeLock member portal. The issue has been fixed and was limited to potential exposure of email addresses on a marketing page, managed by a third party, intended to allow recipients to unsubscribe from marketing emails. Based on our investigation, aside from the 70 email address accesses reported by the researcher, we have no indication at this time of any further suspicious activity on the marketing opt-out page.




The online service “LifeLock”, is just website marketing B.S. that real doesn’t do much to protect your identity
Well, my friend, that’s what sells today, BS. Guess the goodwill Symantec paid when purchasing LifeLock now partially has evaporated. If only it could be written down (which it cannot under GAAP US). I’m more old style. I google myself on a regular basis, got an edgy one man show e-mail provider, no 2FA BS, just plain old pwd manager, no smartphone. But yes, I also use the cloud, only in a “special” way. On the other side, I pay every yr quite a lot for my encryption software. Has worked for me up to now.
This ID protection stuff is a meme anyway, but it also takes off in Europe.
Gordon, apparently you don’t understand two-factor Authentication among other things. It is the best technology to reduce your security surface area from attacks.
The screen capture also reveals that the Lifelock website is not fully secured, despite having the https prefix. As I just learned, getting rid of http images, scripts and includes can be a massive headache.
Yeah, I fought a bit of a battle when we upgraded exchange and they had a logo going over http. I didn’t care about the logo really, but I want users to be vigilant about secure sites and you can’t exclude your own.
Been there and done that with implementing SSL on our corporate website recently. Needed to check every single page for https breakage. BTW, Google Chrome developer tools were a Godsend in this endeavor to catch everything on the page in one fell swoop…
You know what else I noticed about the “LifeUnlock” website from your screenshots, Brian? That they have a misconfigured TLS certificate on the site 🙂
So if I were a customer, it’d make me think twice before signing up for any of their services. It doesn’t seem like they know what they are doing over there 🙂
“LifeUnLock” – LOL!! 😀
What specific content needs to be secure for an unsubscribe page?
It’s not as though it shows an account number or customer’s maiden name. The only private info is an email address and that doesn’t need to be transmitted securely.
This article by Troy Hunt pretty much sums up why having HTTPS for everything is good: https://www.troyhunt.com/heres-why-your-static-website-needs-https/
I appreciate the information!
https://www.nj.com/news/index.ssf/2016/05/couple_tried_to_buy_mercedes_with_stolen_id_cops_s.html
This story is from May 10, 2016. I’m not sure how it’s relevant to this post.
Did you read the article? Describes how an 86K loan was stopped by LifeLock – for all those criticizing it as ineffective.
My credit report freeze would also have stopped such a loan, and it didn’t come with a monthly charge.
Exactly. After the OPM breach I froze my credit based on Brian’s guidance and didn’t worry about it. I don’t want monitoring to tell me after the fact, I want it stopped. I know it works pretty well because the one time I applied for credit since then was a real pain because of how locked down I have it.
A freeze is not hack-proof. It’s a road bump that can be easily circumvented with a forged signature on a letter or a little social engineering with a customer service representative.
A determined thief can arrange a loan for a “frozen” account in less than 2 weeks.
By the time you figure out that your credit file has been unfrozen, it’s too late.
I’ve never trusted that company since I found out one of the originators was a crook. He left day to day operations, but I still didn’t like the advertisements, or anything else about this company. I wouldn’t touch them with a 10 ft pole. Why am I not surprised they, or Symantec, could care less about security!!?? I agree with the comment from ‘The Sunshine State’, I feel exactly the same. Just a lot of marketing and blow hard hot air from Life-Lock (what a joke).
Take a look at the news article above – $86K Mercedes loan stopped, and crooks caught, by a LifeLock alert.
You work there or something?
Just a member, who’s not a fan of ignorance. I’ve gotten alerts 30 seconds after opening a new credit card – it works for me.
My credit card company also noticed when someone was using my credit card without my authorization. They phoned me up to ask about it, then reversed the charge. They did that for free. So what is lifelock doing that is above and beyond?
You honestly don’t get the difference between fraudlent charges on an existing card and a NEW card open fraudlently in your name?
Your bank won’t call you about that – neither will a new bank opening an account you know nothing about…
He better hope he’s not a lifelock employee, or Brian just got a lead on another story from his weblogs about yet another company trying to use straw men to block criticism.
Personally I think Lifelock and the other predators that try to hack senior brains should be taken out behind the shed by the FTC.
Screenshots are from 2015, so I would assume this (if at all) happened in 2015. Why its being reported now? Clickbait article?
Screenshots are from 2015? How do you figure? I took them both today myself.
A quick glance and saw copyright 2015 – lol
That may suggest this problem has been around since that long, but it has nothing to do with when the screenshot was taken.
means they probably have not bothered to update the site or even check on its security since 2015! boy that should be a big red flag that their website is crap if they haven’t changed it since 2015!
The date on a webpage copyright notice is irrelevant. The assertion of a copyright for unremarkable generic Web content is irrelevant, too.
It’s about as meaningless as the shopping center signs announcing “we are not responsible for parking lot damage,” when they damn sure are. It’s a scare tactic, nothing more.
Yeah, I’m not sure what a page content copyright has to do with how well the site itself is secured. Wait … actually, I am. Nothing.
Images can be easily forged. Do you want one with your profile pic on it?
LOL that was really funny
And most of the dunces that fall for these types of services are prime for hacking in any case – just saying.
Herr derr,
“may have”
“could”
Sounds like a bunch of scaremongering clickbait to me. Everyone wants fame, or at least 15 minutes of it. So they “discover” some obscure detail and blow it way up out of proportion. Attention seeking. What about feeding hungry kids? No 15 minutes of fame there.
It’s newsworthy because a company like this shouldn’t be making such Internet Security 101 mistakes, and the fact that they did in this case raises legitimate questions about whether they take user account security seriously.
You think that people that discover security flaws and report them to companies instead of finding a way to exploit them and steal money from people are “attention seekers” looking for 15 minutes of fame? Um, ok.
It wasn’t blown way out of proportion, it was responsible disclosed. Mistakes like this are both common and preventable. If one person sees an article about this Life Lock issue and decides to validate their configuration then it’s a win.
“So they “discover” some obscure detail and blow it way up out of proportion.”
If you honestly think that the vocation of breaching information systems is constitutionally obligated to stop at some threshold of obscurity for reasons I can’t possibly process, I’m wondering if I need to pray for you.
And bear in mind here, I’m not even religious.
Misconfiguration?
Mr. K., you make this sound like some trivial and quickly correctable mistake by a systems administrator rigging a server.
This is no misconfiguration. This is a fundamental programming error.
This is the intentional use of an easy-to-guess long-lived secret to access personal information. How can programmers working for a security service not know they should use hard-to-guess access tokens (long random strings of letters, maybe) that immediately expire when they are used?
How can this not have turned up during Symantec’s examination of Lifelock’s assets before the dropped more than two gigabucks on the company?
Are Symantec’s merger/acquisition team gonna be sent back to Infosec school?
symantec bought a lemon and they probably did not even kick the tires to see how unsecure this lemon was.
I don’t know about fundamental programming error. I would call it more of a misconfiguration. You can’t really send out expiring tokens in the context of unsubscribe button in emails. That’s not really practical. A simple quick fix is to have the user have to enter their email address to unsubscribe instead of just displaying it. There are obviously more things to do to be more secure and these people should know better and be held to a higher standard than everyone else when it comes to cybersecurity but it’s not like this is a fundamental problem with all of their programming. It’s a simple fix. It does make you wonder what other bad practices and lazy coding they have under the hood though.
Leaving out the token entirely sounds like a good idea.
Allowing Converting sequential numbers into easy-to-access info is press-worthy, though, even if I hope that livelock wants more than the account number and the email address if someone calls them and wants to reset the password.
But the incident makes me think if using consecutive numbers for all clients might not have been a bad practice to begin with. Even if many firms do so. The next question would be: if all customers they keep records of have consecutive numbers: Does that hint towards that they keep permanent records of any ex-client? Are they allowed to do so for >5 Years?
I now definitively want a true random 512bit customer number.
+1
It was a fundamental programming error; more specifically an application design error. They have to include some sort of identifier in the link they send out in the email. Their error was in choosing an easily guessable identifier. They can’t require authentication to identifier the user, because they need to allow for non-customers (who’s emails have presumably been used in error).
That email campaign was run on the exacttarget salesforce cloud platform.
The knobs exist there for security to have been enabled…so at issue is some symantec project manager not bothering probably because he/she assumed that the cloud unicorns and pixies would rain security dust on it. ‘Cus Cloud!
Har, Har, two top security pirates met their match. LifeLock and $ymantec are scammers.
Consumer advocate Clark Howard has always been
critical of Lifelock and I have always respected his opinions and
advice.
Cool. I get paid minimum wage, and I’m glad Nathan Reese exposed this flaw from otherwise ignorant members prior to informing LifeLock. Now I can expect to field calls from abusive LifeLock members about this tomorrow from clock in to clock out. Thanks, bro.
You’re going to blame the person who found the problem and fixed it responsibly for you getting lots of calls? Be mad at the person who let the flaw exist to begin with.
Many people forget that the poor person at the telephone hasn’t anything to do with the cause of the problem.
Like I say, not everyone is the a+ student. Some are good at tests, some forget how write their name the day after they learned cursive. And not everyone learned proper programing at Charlie’s muffler shop. So, yup, cool. Nice catch. That’s why there needs to be peer review. To catch what the others forgot,
LifeLock has a history of making little mistakes here and there:
December 2015:
LifeLock will pay $100 million to settle contempt charges from the Federal Trade Commission.
In 2010, the FTC alleged that LifeLock made deceptive claims when promoting its identity theft protection services. LifeLock paid a $12 million settlement that prohibited it from making misleading claims and required it to better protect its customer’s personal information.
But in July 2015 the FTC claimed the company was in violation of that settlement by continuing to make false claims about its services.
The agency also alleged that from October 2012 to March 2014 the company didn’t create and maintain a comprehensive information security program to protect customers’ personal data, including Social Security and bank account numbers.
I got somewhere around ten bucks due to that settlement. Never paid for a LifeLock subscription, just had a free one paid by someone else who had a breach.
Thanks Steve for your research that flavored Kreb’s excellent narrative.
“we have no indication at this time of any further suspicious activity on the marketing opt-out page.”
translation….although the application has been in production for 2 years, our logs go back 1 month and we found no evidence in them of suspicious activity.
https://www.wired.com/2010/05/lifelock-identity-theft/
(Yes, it’s an old article; but with all the LifeLock vitriol in the comment, I was just surprised no one’s brought it up.)
I remembered the CEO having his identity stolen after he plastered his SSN everywhere advertising their services. I also always had to laugh at their free shredder they would give you if you signed up, so that you could securely dispose of your personal papers – except that it looks like it is “shredding” it into 1/2″ strips, which is only minimally more secure than just tossing the papers. If a company advertising security is giving away that kind of shredder as security, I don’t think they understand what security is. To quote my son, “How are they even still in business?”
LOL Lori, your son’s question is awesome. Really, after all those years, hundreds of $$ Millions, why do people keep being ignorant and still keep paying them?
I find this hilarious. I’ve only ever had a LifeLock account due to a the OPM breach and the free subscription from that. I always figured it was mostly worthless, except perhaps as a form of insurance for after you get your identity stolen.
The person who designed the site lacked basic knowledge or were security corners cut in order to make life easier for C levels? Let’s all pretend that doesn’t happen for a minute and then realize that yes, yes it does :-/
well, darn.
even if it was a third party lifelock is still responsible
Symantec needs to monetize each customer for about $500 just to break even. I do not grasp the business elements here, and do not like any thoughts as to what Symantec may be up to.
Personally I do not understand why people even pay for such service. Everything they monitor you can monitor yourself.
Remember you have to provide LifeLock with detailed information such as SSN, account names etc.
It’s like putting all your eggs into one basket (LifeLocks basket).
No thank you for 30 bucks a month.
Does anyone know the name of the third party? thanks
Does anyone have the name of the 3rd party company? Thanks
I meant to reply to you and accidentally replied as a new comment.
Looks like they are using a Salesforce IP block (according to ARIN). I guess the “third party marketing firm” was Salesforce? If not that’s probably where they keep their database of users.
Didn’t see this before I posted a similar response. Yes, this is Salesforce and it’s an ExactTarget program they started in the early 2000s. As you might guess, a lot of people use this service. I wonder if this was a bug across all of their clients.
You should review webcam privacy covers like this one from http://www.privacyideserve.com
Looks like their response is out:
https://www.symantec.com/blogs/feature-stories/how-symantec-resolved-issue-involving-lifelock-marketing-opt-out-page
I’ve been a Lifelock member for over a year and get breach updates a week or two earlier from both Experian and CreditKarma. I can only hope my Lifelock dues are worth their lawyers if ever needed. Otherwise my membership has been a waste so far.
Michelle, I represent the leader in the IDTheft Protection industry. We also have lawyers that you can use for anything you need, not just IDTheft, and 24/7/365. Check us out! We might also save you some money! My contacts are on the website. Feel free to call if you have any questions!
They still have some work to do. https://www.ssllabs.com/ssltest/analyze.html?d=cloud.email.lifelock.com
Looks like they are using a Salesforce IP block (according to ARIN). I guess the “third party marketing firm” was Salesforce? If not that’s probably where they keep their database of users.
DNS lookup for that domain reveals the third party was ExactTarget (unless they updated that DNS since the story… unlikely). ExactTarget is a huge email marketing firm that was bought by a little company named Salesforce, so if this is/was a bug across all of their clients, this is a much bigger story than just LifeLock.
Lifelock preys on the ignorant. I’d love to know where their “facility” in their ad is located:
https://www.bing.com/images/search?view=detailV2&ccid=SXe7k8r5&id=17EC0F5266D99D17D974D581E52FCF0BE2338149&thid=OIP.SXe7k8r55V7hIc7ZJmJtXwHaEK&mediaurl=http%3a%2f%2fimage.cdn.ispot.tv%2fad%2fAIIX%2flifelock-fix-it-large-7.jpg&exph=562&expw=1000&q=lifelock+ad&simid=608042194771509255&selectedIndex=57&ajaxhist=0
But I already know the answer. It doesn’t. Just like all those company ads showing techs in front of wall sized transparent computer screens. As if…