A Connecticut man who’s earned bug bounty rewards and public recognition from top telecom companies for finding and reporting security holes in their Web sites secretly operated a service that leveraged these same flaws to sell their customers’ personal data, KrebsOnSecurity has learned.
In May 2018, ZDNet ran a story about the discovery of a glaring vulnerability in the Web site for wireless provider T-Mobile that let anyone look up customer home addresses and account PINs. The story noted that T-Mobile disabled the feature in early April after being alerted by a 22-year-old “security researcher” named Ryan Stevenson, and that the mobile giant had awarded Stevenson $1,000 for reporting the discovery under its bug bounty program.
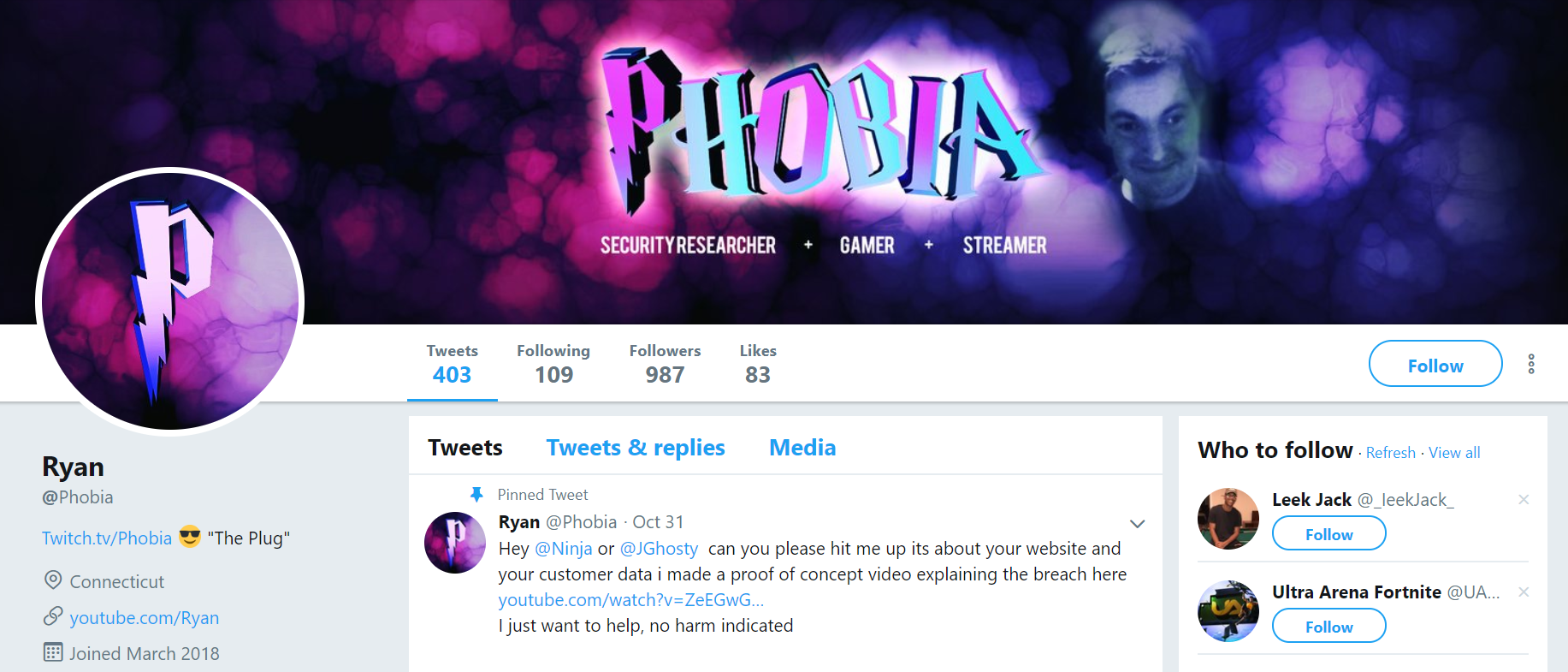
The Twitter account @phobia, a.k.a. Ryan Stevenson. The term “plug” referenced next to his Twitch profile name is hacker slang for employees at mobile phone stores who can be tricked or bribed into helping with SIM swap attacks.
Likewise, AT&T has recognized Stevenson for reporting security holes in its services. AT&T’s bug bounty site lets contributors share a social media account or Web address where they can be contacted, and in Stevenson’s case he gave the now-defunct Twitter handle “@Phoobia.”
Stevenson’s Linkedin profile — named “Phobias” — says he specializes in finding exploits in numerous Web sites, including hotmail.com, yahoo.com, aol.com, paypal.com and ebay.com. Under the “contact info” tab of Stevenson’s profile it lists the youtube.com account of “Ryan” and the Facebook account “Phobia” (also now deleted).
Coincidentally, I came across multiple variations on this Phobia nickname as I was researching a story published this week on the epidemic of fraudulent SIM swaps, a complex form of mobile phone fraud that is being used to steal millions of dollars in cryptocurrencies.
Unauthorized SIM swaps also are often used to hijack so-called “OG” user accounts — usually short usernames on top social network and gaming Web sites that are highly prized by many hackers because they can make the account holder appear to have been a savvy, early adopter of the service before it became popular and before all of the short usernames were taken. Some OG usernames can be sold for thousands of dollars in underground markets.
This week’s SIM swapping story quoted one recent victim who lost $100,000 after his mobile phone number was briefly stolen in a fraudulent SIM swap. The victim said he was told by investigators in Santa Clara, Calif. that the perpetrators of his attack were able to access his T-Mobile account information using a specialized piece of software that gave them backdoor access to T-Mobile’s customer database.
Both the Santa Clara investigators and T-Mobile declined to confirm or deny the existence of this software. But their non-denials prompted me to start looking for it on my own. So naturally I began searching at ogusers-dot-com, a forum dedicated to the hacking, trading and sale of OG accounts. Unsurprisingly, ogusers-dot-com also has traditionally been the main stomping grounds for many individuals involved in SIM swapping attacks.
It didn’t take long to discover an account on ogusers named “Ryan,” who for much of 2018 has advertised a number of different “doxing” services — specifically those aimed at finding the personal information of customers at major broadband and telecom companies.
In some of Ryan’s sales threads, fellow forum members refer to him as “Phob” or “Phobs.” In a post on May 27, Ryan says he’s willing to pay or trade for OG accounts under the name “Ryan,” “Ryans”, “RS,” “RMS” or “Stevenson” on any decent sized popular Web site. “hmu [hit me up] in a pm [private message] to talk,” Ryan urged fellow forum members.
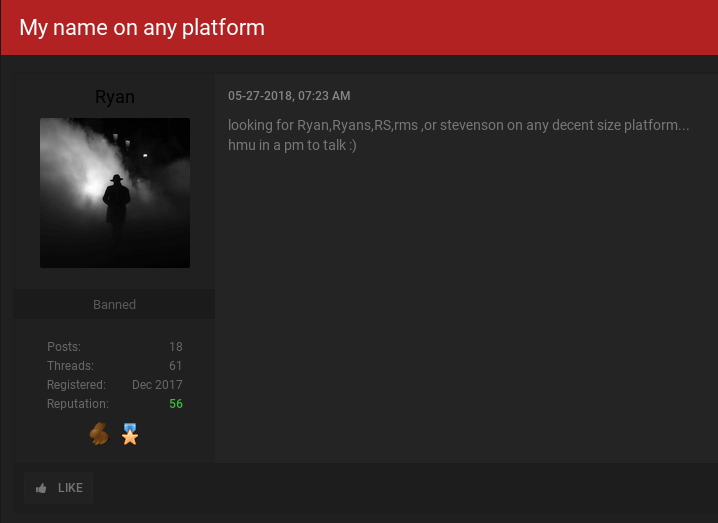
The OG User forum account “Ryan” asking fellow members to sell or trade him any major Web site account name that includes the OG username “Ryan” or “Stevenson.”
I found that as late as June 2018 Ryan was offering a service that he claimed was capable of “doxing any usa carrier,” including Verizon, AT&T, Sprint, T-Mobile, MetroPCS and Boost Mobile.
“All I need is the number,” Ryan said of his customer data lookup service, which he sold for $25 per record. “Payment BTC [bitcoin] only.”
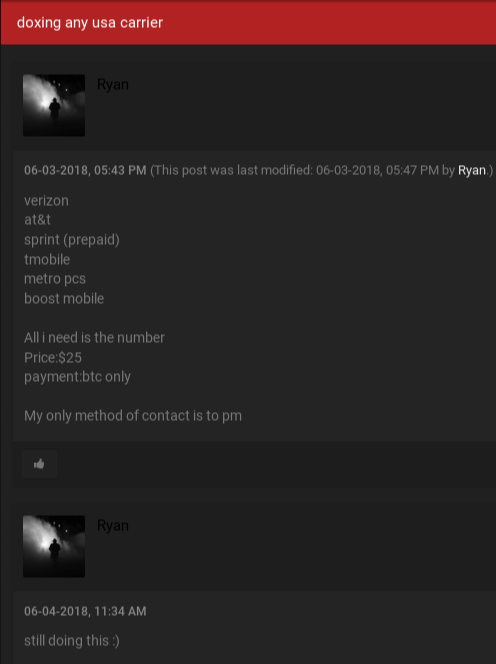
For $25 per record, Ryan offered fellow ogusers members the ability to look up customer records tied to any customer of the major U.S. mobile providers.
Very similar offerings were made by Phobia’s alter ego “AOLer” on the sprawling English language online hacking community Hackforums.
I first encountered Stevenson several years back while trying to work out who was responsible for calling in a phony hostage situation and sending a heavily armed police force to our Northern Virginia home in 2013. In a follow-up to that story, Stevenson admitted that he was responsible for the high-profile hack against Wired reporter Mat Honan, who documented how a hacker named Phobia had deleted his Google account and remotely erased all data from his iPhone, iPad and MacBook.
Going by the nickname “Phobiathegod” at the time, Stevenson was then part of a group of young men who routinely hijacked OG account names on Microsoft’s Xbox gaming platform, often using methods that involved tricking customer service people at the target’s mobile provider into transferring the victim’s calls to a number they controlled.
Fast forward to today, and Phobia’s main Twitter account (pictured at the top of this post) includes the phrase “the plug” next to his profile. In SIM swapping circles, a “plug” is hacker slang for an employee at a mobile phone store who can be bribed, tricked or blackmailed into assisting with an unauthorized SIM swap.
Reached via instant message on LinkedIn, Stevenson acknowledged running the ISP doxing services, but said his account on the OGusers forum was since banned and that hardly anyone took him up on his offer anyway.
“I shouldn’t have made the threads even though no one really asked for anything,” he said. “I’m on the good side. But its almost 2019 and I need to find a new hobby I can’t be bothered to look for breaches/vulns, haven’t got 1 job offer or recommendation yet.”
Asked about “the plug” reference in his Twitter profile, Stevenson suddenly stopped replying. Not long after that, the @Phobia Twitter account was deactivated.
Stevenson denied being involved in SIM swapping attacks, but it is clear Phobia was fairly tight with many people who are or until recently were at the center of this scene. In July 2018, authorities in California arrested 20-year-old Boston resident Joel Ortiz for allegedly conducting dozens of fraudulent SIM swaps and stealing at least $5 million worth of cryptocurrency from victims.
Like Phobia, Ortiz had a presence on OGusers and had acquired some of the most OG social media accounts available, including the Twitter and Instagram account names with the number zero (@0), and the OG Youtube accounts “Joel” and “X”.
On Oct 27, 2017, the Youtube account “Joel” published a 4-minute video of Stevenson dancing to a popular rap song in front of the camera. On July 5, 2018, just days before Ortiz was arrested, the Twitter account “0” gave a shout out to @Phobia on Twitter suggesting Phobia was actually tweeting using Ortiz’s “0” account.




The latest Reply All podcast episode, #130 The Snapchat Thief, is about SIM swapping and the OGUsers. It has been eye-opening getting a peek into this subculture. If you have been putting off doing a 2fa security audit for yourself, then now is the time to do it.
The summary you described leaves out the second half of that podcast, where it’s revealed that the theft had nothing to do with OGUSERS or SIM swapping.
Next time, actually listen to the whole thing before wasting space.
Rude. The Reply-All episode DID go into the underground culture of Sim-Swapping. Nothing said about the episode was in accurate.
I loved the episode of Reply All that discussed SIM swapping and other attack vectors for stealing people’s “OG” usernames on various platforms.
@Readership1 was a dick to you in his reply, the story on Reply All did discuss SIM swapping and the username “Lizard” was targeted as “OG”, so don’t listen to them at all.
One would think that Readership1 is one of those script-kiddies that steals and sells OG Accounts and is pissed that Reply All was encouraging people to beef up their security making steeling credentials/account names more difficult.
Just sayin…
@lizard wasn’t targeted. It was picked by an automated script, along with many others, at random because they were in a dictionary list and had a weak password.
The perpetrator didn’t buy, sell, or discuss the account on any forum. SIM swapping played no role in the account takeover.
And the podcast didn’t explain how to prevent account takeovers. It’s not a security lesson. It briefly told the story of how a fearful journalist took anti-doxxing precautions.
Next time you open your mouth, think first.
I was also going to give a shout-out to the excellent “Reply All” podcast which discussed this issue in its latest episode. While SIM swapping didn’t take a role in the takeover of the particular “lizard” account, it was still discussed.
Not sure what Readership1’s issue is (too literal?), but I think most people would enjoy the podcast, as it’s very relevant.
Nice job Brian!
It’s wonderful how bad some hackers are at opsec. They think they can hide in the shadows, yet they leave many bread crumbs for someone to follow. Boom, sunlight.
Come on “Phobiathegod” real , now tell me this guy doesn’t have a problem with narcissism.
He gives my home state of Connecticut a real bad name
I’m a “Old Gangster Nutmegger” ! LOL
“…the mobile giant had awarded Stevenson $1,000 for reporting the discovery under its bug bounty program.”
SO WOW, MUCH MONEY
You know, something tells me that some of those “security researchers” out there are kind of “double agents,” if you know what I mean.
Although, a thousand dollar reward paid by T-Mobile may be to blame for that as well. It’s such a shame that companies don’t realize the potential cost of those security holes (I.e zero days.) And T-mobile is far from being alone. Apple doesn’t even have a paid bug bounty program, while some companies actually keep their software under tight lock and threaten researchers with law suits. (Example: automobile companies.)
Many people now days live off from fraud and scams.
I guess its way more soft then drug dealing.
What else people can do to make money since they have no education. The only way is fraud, first fraud.. If they are dissiolined and not waste their money then they save some capital and make their own business. Legit business… Or they open some business and on the side they do little bit fraudng.
So… are we to take away that bug bounty payments are a leading indicator of illegal activity? Maybe we should ban paying researchers for proactively reporting problems then?
How in the world did you come to this conclusion?
Jcran — don’t you think people who call themselves “security researchers” should be held to account for this kind of behavior?
Absolutely and sorry you had to go through the situation at your house.
My key point is labeling him (leading with) him as a “bug bounty hunter” can be misleading. As you point out, you just as easily call him a “security researcher” or “independent” and stretching that a bit further – you might as well just label him a “twitter user”.
Maybe there’s nothing bigger/better to tie him to, and i get the need to label him to make it relevant to folks, but he certainly was not acting on behalf of a bounty program when conducting criminal activity, and i worry the uneducated reader ends up thinking bug bounty activity leads to criminal behavior. No. Poor moral choices lead to criminal behavior. He made bad choices independently, and that has nothing to do with the bug bounty situation, in which he presumably made GOOD choices.
At the end of the day, it’s the criminal behavior here that needs highlighting, and i accept and acknowledge your point that calling the criminal behavior out as unacceptable and illegal is a step in the right direction.
By the way, you can see in my screenshot of his twitter profile that he calls himself a security researcher. I put the term in quotes for hopefully obvious reasons.
or maybe this potential side effect of a bug bounty program is simply showing that any payments made ought to be done in such a manner that a ‘security researcher’ must show some real location & ID – to establish a record of accountability which other researchers such as Brian could access? If so, then a industry-wide set of standards ought to be established & adopted for the administration of bug bounty programs
The platforms (BC, H1, Synack) already have much of this in place, however it’s not public (nor do i think it should be). Think about the extreme privacy implications.
Non-public bounty programs commonly do require things like real name, id verification and even background checking
My take:
It only shows that the capabilities to do good can also do bad stuff…
Sad to hear that some prefer to ‘paddle along two rivers’ as we used to say…
Some amount of hard time is what he doubtlessly deserves, but probably not what he’ll get (probation plus a hefty fine is my guess).
nice! have to start reading these again lol. They should put these guys on a payroll. 1000 dollars? What is that gonna do… I’ve talked to alot of great bug bounty hunters online and they all tell me the same thing. They won’t hire me, they don’t give me any money for finding bugs. peanuts. but ya its the whole culture on both sides that just create sociopaths especially when they get them young. There is still a cold war going on too.
The sense of entitlements and disregard for the severity of the situations or treatment of the physical vs digital realms as something different.
Basically its like lord of the flies and 15 year olds are in charge of society now. Literally. In the late 90s and early 2000s the internet was still run by adult American and British Mommys and Daddys. Now its run by immature trolls and other countries inciting them.
Can you see the reflection in society? Its because they one and the same.
Heads up, “the plug” in hip hop culture is usually a reference to someone who supplies drugs, eg, “the plug just re-upped”. The definition in this article is likely incorrect.
Right. That’s why Phobia has friends like @Plugwalkjoe who chides Phobia and his Team Hype friends for dropping valuable methods for hacking accounts.
https://twitter.com/CoolItsConvict/status/1045849836124278785
Sorry, I’m just trying to note where the term came from. As someone who knows the origin and hears it constantly in rap music dating back to early 2000’s, your description seemed a bit off as I read. I’m not doubting that this is the term they use to refer to someone who has things to offer, just that your definition of the raw term wasn’t spot on. It’s origin is not exactly hacker-slang, moreso something inherited from rap culture. My intentions weren’t to insult your work or anything and I apologize if that’s how it seemed.
Yeah, you must be right. There’s no way a term’s meaning can change based on context or with time. . .
Apologies for the multi-comment, “plugwalk” is absolutely a reference to this song, which is a rap song that uses the term to refer to a drug dealer… https://www.youtube.com/watch?v=ToY6sjSV8h8
The term “plug” replaced “connection” which is an older term for a supplier in drug dealer parlance. Fraudster borrow heavily from drug dealer terms as many of them are former dealers. The term “plug” in fraud always refers to some sort of insider who facilitates crimes. Im not very familiar with sim swapping but I believe BK is probably correct in thinking they use it to mean their specific type of insider. But keep in mind that there are various types of “plugs” for various types of fraud/cybercrimes…
I don’t agree with what he has done and it’s completely wrong. As there should be consequences for breaking the law.
Although, what you’re doing is much worse. You’re essentially preying on an autistic and mentally unstable man who has the moral compass of approximately a seventeen year old. But I’m sure you took the time to research and investigate that right?
With mental health as hot topic in today’s day and age, it’s pertinent for journalists to get a clear and full picture about the person they are writing about.
Here’s a tip: you’ve got the who, the what, the when, the how –but you didn’t get the why. Why was he doing all this?
Some quality journalism right here folks.
How is it you know so much about the ‘person of interest’ and what are your sources of this knowledge?
Seems to me you have a vendetta against this journalist and are trying to discredit him.
Why?
So Krebs should have found and contacted this guy’s physician before publishing his story?
It sounds like you know Ryan pretty well. Why or how would Krebs know what you seem to claim to know? Should he ask every person who appears to be involved in making it easier for others to commit cybercrimes whether they have any diagnosed developmental disorders? And if so, should that disqualify them from being written about?
What percentage of people who commit crimes in general do you imagine *don’t* have some kind of mental illness? I suppose we should just give all of those people a pass as well? Or is it because we’re talking about online hacking that Ryan deserves a break, despite apparently tons of examples of him continuing his activities over many years?
You can’t use mental health to excuse criminal behaviour. Lock them up!!
Actually, yes you can. The criminal justice system accounts for it, too.
And yet they still lock them up, either in a mental health institution or in a normal jail. Regardless, Brians reporting wasnt preying upon some poor man with mental health issues. If this guy is committing crimes, the police or FBI will look into it, he’ll still get charged, and then as you say, the criminal justice system will take into account any mental health issues there may be. Having mental health issues doesnt mean you dont get arrested, indicted and/or convicted of crimes you commit, but it might mean the sentence is more lenient.
To have such a vast information of knowledge there’s no doubt that he knew his actions were highly illegal. No, if’s, and’s, or but’s regardless of his mental state.
Why are you even here reading this Security Blog if that’s what you think?
excellent work as usual Brian. I remember the wired story and specifically cite it often as to why SMS based 2fa is a big red flag.
it’s worth noting that in rap/hip-hop culture a plug or the plug refers to a drug dealer’s supplier, or any supplier of goods/wares to people participating in illicit activity. ( it’s a status symbol like a boss or someone with unique abilities who is to be respected/protected , in their culture ). example; hey I have a plug on (getting) stolen cigarettes. bob is my plug .
Unsure why so many are calling this a bad read.. Great work Brian regardless of what others are saying. Recently picked up your book! Can’t wait to read!
It seems like “Phobias” has some resentment towards the professional information security community for not giving him a job.
As a thought exercise, what are the most likely outcomes which will happen if a MFA/2FA account has successfully been taken over by an adversary?
Examples:
-Even from an Administrative Panel, an account cannot be accessed without a ‘Token’
-Password is reset, but the MFA/2FA flag is still set
-Password is reset, and the MFA/2FA flag has been removed
Brian, while I enjoyed the article, sometimes your pieces just seem to end without much fanfare? Its not like your wasting ink here, would a summary or wrap up paragraph help tie up your points? You just end this point by point article in calling out this guy as a bad guy, and you end with a reference to a video of him posted on YouTube and a reference he may have been tweeting on another account. What are you suggesting the cops or companies do with with him? Is there a larger issue to address with the bug bounty programs we should engage in? Or, anyone good or bad can call themselves a “Security Researcher” as cover.
Journalists who veer off into policy and opinion are gambling with their relevance, respect, and credibility.
When you make your living off facts and a reputation for truth, it’s folly to squander it over thoughts that may sound idiotic sometime in the future.
Especially that BK is self-employed, he’s got to think carefully before opining on stuff that could alienate readers, sponsors, and bookers.
A story like this needs no policy recommendations. Just facts.
KOS is right not to editorialize this one. Leave the idiocy to the rest of us.
Ricafort is a bug hunter, a name given to a particular breed of do-good hackers who search for vulnerabilities in the software built and owned by some of the world’s largest tech companies before they can be exploited by bad guys. They don’t do it for free, of course: many companies pay (and sometimes pay pretty well) for submissions that help companies shore up the code their business depends on. There’s enough of this going around that being a bug bounty hunter is something of an emerging occupation.
http://whatstatus.co
Technology advancement is rapidly bringing changes to public transportation. In the current year 2018, rapid adoption of on-demand service platforms to manage transportation services is in trend and its urge is going to increase in years to come.
Visit:https://cabstartup.com/key-trends-in-public-transit-services-for-2018-and-beyond/
Excellent article. Thank you for finding these dots and putting them together. Maybe it will help law enforcement nail one of these criminal bottom-feeders who prey on society. We can hope.
Actually, “Ryan Stevenson” does have a job now: staying out of jail.
OMG that video!! LMAO!! Whiskey Tango Foxtrot?!
They don’t do it for free, of course: many companies pay (and sometimes pay pretty well) for submissions that help companies shore up the code their business depends on. Ricafort is a bug hunter, a name given to a particular breed of do-good hackers who search for vulnerabilities in the software built and owned by some of the world’s largest tech companies before they can be exploited by bad guys.
They don’t do it for free, of course: many companies pay (and sometimes pay pretty well) for submissions that help companies shore up the code their business depends on. Ricafort is a bug hunter, a name given to a particular breed of do-good hackers who search for vulnerabilities in the software built and owned by some of the world’s largest tech companies before they can be exploited by bad guys.