A new phone-based phishing scam that spoofs Apple Inc. is likely to fool quite a few people. It starts with an automated call that display’s Apple’s logo, address and real phone number, warning about a data breach at the company. The scary part is that if the recipient is an iPhone user who then requests a call back from Apple’s legitimate customer support Web page, the fake call gets indexed in the iPhone’s “recent calls” list as a previous call from the legitimate Apple Support line.
Jody Westby is the CEO of Global Cyber Risk LLC, a security consulting firm based in Washington, D.C. Westby said earlier today she received an automated call on her iPhone warning that multiple servers containing Apple user IDs had been compromised (the same scammers had called her at 4:34 p.m. the day before, but she didn’t answer that call). The message said she needed to call a 1-866 number before doing anything else with her phone.
Here’s what her iPhone displayed about the identity of the caller when they first tried her number at 4:34 p.m. on Jan. 2, 2019:
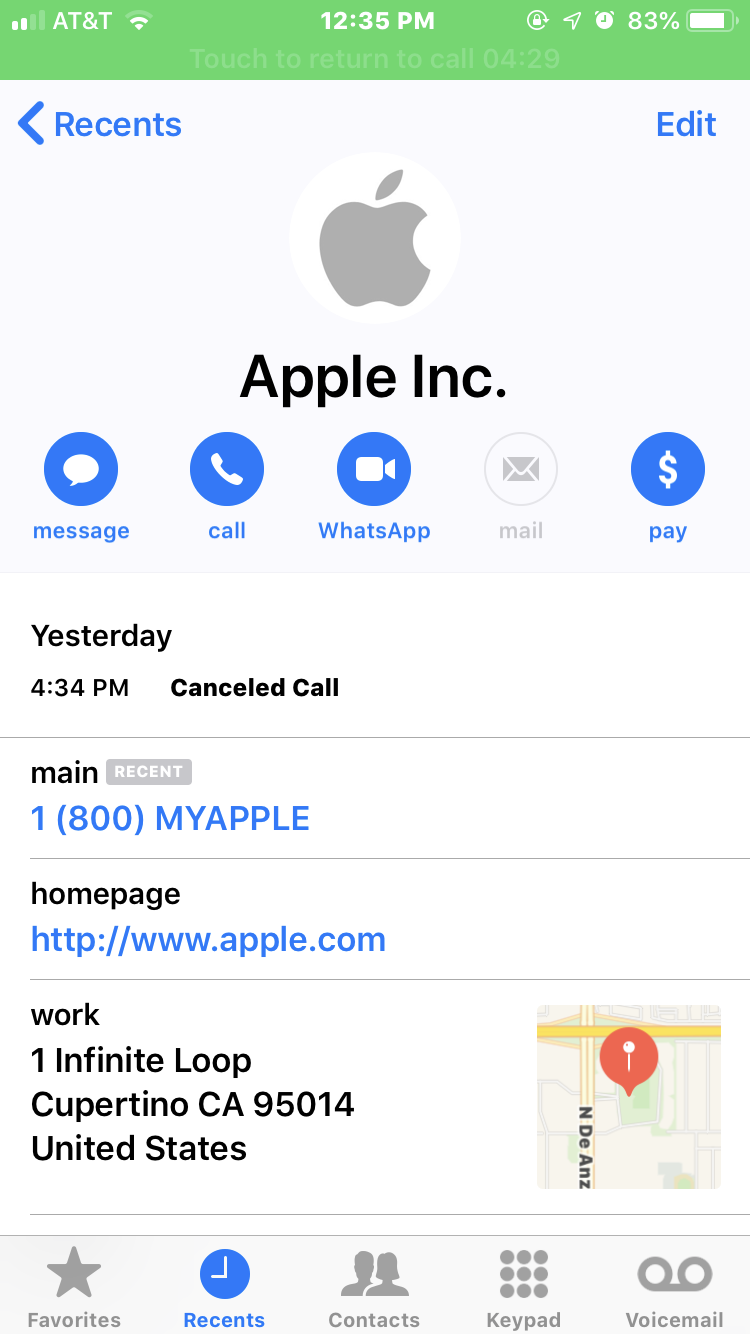
What Westby’s iPhone displayed as the scam caller’s identity. Note that it lists the correct Apple phone number, street address and Web address (minus the https://).
Note in the above screen shot that it lists Apple’s actual street address, their real customer support number, and the real Apple.com domain (albeit without the “s” at the end of “http://”). The same caller ID information showed up when she answered the scammers’ call this morning.
Westby said she immediately went to the Apple.com support page (https://www.support.apple.com) and requested to have a customer support person call her back. The page displayed a “case ID” to track her inquiry, and just a few minutes later someone from the real Apple Inc. called her and referenced that case ID number at the start of the call.
Westby said the Apple agent told her that Apple had not contacted her, that the call was almost certainly a scam, and that Apple would never do that — all of which she already knew. But when Westby looked at her iPhone’s recent calls list, she saw the legitimate call from Apple had been lumped together with the scam call that spoofed Apple:
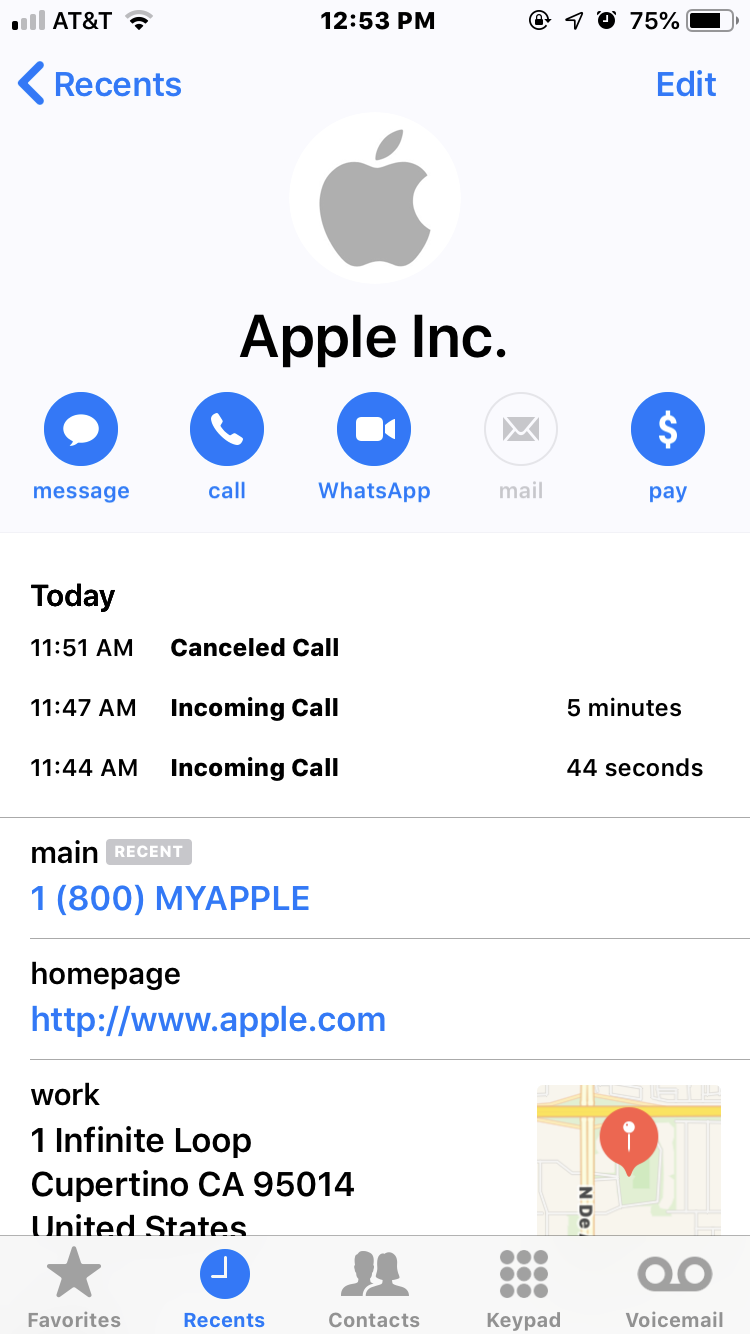
The fake call spoofing Apple — at 11:44 a.m. — was lumped in the same recent calls list as the legitimate call from Apple. The call at 11:47 was the legitimate call from Apple. The call listed at 11:51 a.m. was the result of Westby accidentally returning the call from the scammers, which she immediately disconnected.
The call listed at 11:51 a.m. was the result of Westby accidentally returning the call from the scammers, which she immediately disconnected.
“I told the Apple representative that they ought to be telling people about this, and he said that was a good point,” Westby said. “This was so convincing I’d think a lot of other people will be falling for it.”
KrebsOnSecurity called the number that the scam message asked Westby to contact (866-277-7794). An automated system answered and said I’d reached Apple Support, and that my expected wait time was about one minute and thirty seconds. About a minute later, a man with an Indian accent answered and inquired as to the reason for my call.
Playing the part of someone who had received the scam call, I told him I’d been alerted about a breach at Apple and that I needed to call this number. After asking me to hold for a brief moment, our call was disconnected.
No doubt this is just another scheme to separate the unwary from their personal and financial details, and to extract some kind of payment (for supposed tech support services or some such). But it is remarkable that Apple’s own devices (or AT&T, which sold her the phone) can’t tell the difference between a call from Apple and someone trying to spoof Apple.
As I noted in my October 2018 piece, Voice Phishing Scams are Getting More Clever, phone phishing usually invokes an element of urgency in a bid to get people to let their guard down. If a call has you worried that there might be something wrong and you wish to call them back, don’t call the number offered to you by the caller. If you want to reach your bank, for example, call the number on the back of your card. If it’s another company you do business with, go to the company’s Web site and look up their main customer support number.
Relying on anything other than a number obtained directly from the company in question — such as a number obtained from a direct search on Google or another search engine — is also extremely risky. In many cases, the scammers are polluting top search engine results with phony 800-numbers for customer support lines that lead directly to fraudsters.
These days, scam calls happen on my mobile so often that I almost never answer my phone unless it appears to come from someone in my contacts list. But as this scam shows, even that’s not always a great strategy.
It’s a good idea to advise your friends and loved ones to ignore calls unless they appear to come from a friend or family member, and most importantly to just hang up the moment the caller starts asking for personal information.
Apple has not yet responded to requests for comment.




This sounds like a caller id spoofing incident, where the caller has fraudulently provided the equivalent of Apple’s name and phone number for their call, which is burned into iDevices (and Macs) contacts by default, leading to people getting a call from “Apple.”
However because they were spoofing the legitimate Apple number its likely that any attempt to return the call will end up calling Apple. The scammers control the fake 1-866 or whatever number they’re asking you to call, they don’t control Apple’s actual 1-800 number.
This is part of why I recommend people remove any default contacts on their phones and devices as part of a broader strategy of using as little built-in software as possible to avoid attacks similar to this, which assume you will do nothing except leave everything in place and use all the built-in software.
While the caller id information would still be displayed, it wouldn’t look nearly as convincing because all the burned in contact details would be missing. On the other hand calls from Apple would look the exact same way.
I’m not sure that’s the same thing. The information displayed when the phone rang was the Apple logo and name. I need to double check but I’m not even sure a number showed up. Clicking the “i” for more information next to the number just brought up the data displayed in the screen shot.
SeymourB is right, if one were to spoof the caller-id number of someone in your contacts it would show that contact’s photo and friendly name (in this case the photo is the Apple logo and the friendly name is Apple Inc.). For better or worse the caller’s phone number is not displayed when a contact calls you (and is even somewhat hard to determine in your recent calls list on an Apple device).
I don’t have a contact for Apple in my iPhone either, but I guess it’s possible others do.
It’s added by default to the address book of new MacOS installations. The fact that the URL isn’t https suggests that the contact card has been on the person’s phone for a while — predating Apple’s site going https-by-default.
The contact card you presented (with the same URL, phone number, address and logo) is in my phone as well. I’m pretty sure it’s been in my iCloud contacts list since I first created my Apple ID. I know I never added it, and it’s not part of my GMail contacts (which is my primary contact list).
You say you don’t have this contact. Have you configured your iPhone to pull contacts from your iCloud account?
Another possibility is that it may have been synced from a Mac. It’s been a long time, but I think Mac OS X includes (or once included) this card as a default contact. Since my Mac syncs its contacts list with iCloud, that’s another possible vector for this card.
It’s worth noting that both my card and the one you presented list the “1 Infinite Loop” address, which is no longer correct, but was correct when the card was created (in my case, many years ag0). (Apple’s corporate address is now “1 Apple Park Way”. See https://www.apple.com/contact/.)
Yeah, older timers who used the MobileMe sync service would have the Apple contact force fed to their contacts list. Even deleting it wasn’t permanent.
I had a similar thing happen to me recently, except unrelated to Apple. On my Android, a scammer spoofed AT&T Customer Care’s number (which is a default contact on all AT&T phones) and called my mobile. It automatically seemed weird, so I hung up and let AT&T know about it via their website. AT&T Customer Care and other similar services would never call a customer out of the blue.
I had a problem with forgot my password on a iPhone 7 with sprint service. I tried to explain this with Apple support who remotes to my iPhone and was told to go to the store in which I did. The store encountered the same issue as the Apple support that is on my iPhone. I don’t know much about vulnerabilities but it’s an issue with the “certificates”that I guess verify the device. I’m at a lost as to why Apple feels that the devices are invincible.
Do you have a Mac? Log in to the Guest account (or create a new user, but don’t sign in to iCloud when prompted). Once in, open the Contacts app. Guess what’s there? Yep… a default contact for Apple. Same thing on an iPhone if setting up as new.
This is not much different than earlier in the year when they were spoofing various Apple Store phone numbers.
A member of the family just got one of those, pretending to be calling from a big city Apple Store. Funny you should mention that.
Reminds me a fake call I recently got from “Internet Service Provider” telling me that my internet will be disconnected if I don’t speak to the technician. Audio here: https://clyp.it/dco33x2x
Priceless!
Isn’t this just a matter of the caller spoofing the caller ID so that it appears to come from Apple, as there is only the single phone number associated with the contact. My guess is that Ms Westby already had the contact for Apple stored (maybe by default with a new phone), and it just recorded the call history. Otherwise, how else are you proposing that the contact information was entered on her phone? The scam is then simply getting people to call back on the other 866 number.
I just checked on my iPhone and I do not have a default contact from Apple.
My iPhone does have a default contact from Apple. It is identical to the one you show in your report (including the missing “s” after http). So, I think Donder is correct. It looks like a standard caller ID spoof that caused her iPhone to display an existing Apple contact that was already on her phone. This is pretty devious. It takes advantage of what is in the victim’s contacts to make the attempt look significantly more realistic.
You probably overlooked it.
Think about it: the Caller ID protocol doesn’t allow for presenting this kind of information. Neither does FaceTime. It’s literally technically impossible to happen any other way than what others explained here: this is a run of the mill Caller ID spoof and *your phone* filling in the details.
Same goes for call history: you got a call from (as far as your carrier and your phone know) from Apple. *Of course* it’s together with other calls using the same number in history.
I know for a fact that caller ID can be spoofed; I was involved in a criminal case where a phone harassment took place.
Nobody’s saying it can’t. What they’re saying is that the information being presented, as a whole, is not doable withing caller ID specifications. These are blanks that Apple is filling in based on the spoofed number.
The only way to have one is to create a contact from a call – i. e., a user action. There’s no good reason to create a contact called Apple Tech Support…
Of course there’s a good reason. some people actually do call Apple tech support. I called my contacts entry Apple Care, though, but the effect is the same.
Why would you ever call Apple from a contact and not the website to get the latest number? A phone number in the contacts could be years old and out of date.
In short, because any 800 number that a major company has ever given out should never be abandoned (until the company goes out of business).
It’s like abandoning a web site (Brian has written examples of this). And somehow expecting that a phisher will not snap up the domain.
People will call numbers that they have recorded, and reasonably or not will expect to be connected to that same company.
This isn’t quite the same thing as moving offices. Sure, companies will physically move, and people may send letters to old addresses (I’m sure there are stories, possibly even here) of mail sent to old addresses (past the mail forwarding date) resulting in interesting outcomes, but people tend to be a bit more cautious about snail mail (because it’s harder to cache an address, short of a rolodex).
Note: phone numbers like Apple Care are vanity numbers:
1-800-MY-APPLE (1-800-692-7753)
There’s no way Apple would give up that number.
As mentioned in the article, scammers are using search engine manipulation to get their own fake numbers in the top Google/Bing results.
It may be that different handsets/telcos may preload the contact, or not. Doesn’t show up in my contact list neither.
You would, if you had synced a MobileMe (.mac, .me) account or had the early iphones, then kept it in your contacts all these years.
Back then, they (“Apple, Inc.”, and “Apple Support”) were included as example contacts.
I looked back at my old iphones and it’s there, along with the carrier’s customer service number, in each of them.
I never would’ve added “Inc.” on my own, I’m too lazy. So definitely Apple put it there.
Just checked and can confirm that I too have the default Apple contact but because I am in the UK it shows a UK telephone number, a UK address and a UK support website (without the “s”). I know I have never contacted Apple and did not knowingly enter these details. I have now deleted the record.
I have been receiving 2-3 of these Apple phishing emails a day for a while now.
I just now received two emails; one was the above article from Krebs, the other was another Apple phishing email.
Relentless.
Carry on, Krebs!
I got an iTunes subscription phishing email yesterday. I don’t even own an iPhone. The links went to a host in Singapore. For yucks I went on a Linux box and entered the top level of the link. My Pi-hole blocked the domain. I did a ping to make sure the server was up.
The email is already deleted. Host was unifiedlayer.
You don’t need an Apple device to buy music or movies or TV shows from iTunes. There’s a version of the iTunes app for Windows. I don’t think there’s a version for Android but I believe there is an Android version of the Apple Music streaming app.
In other-wards don’t trust anyone on the phone with a Indian accent
The call to mjc775 above is a machine (which I hear regularly) so making judgements about accents is no defence.
This is the thing I hate the most about these scammers. I talk to nobody that has an Indian accent except for these people (a dozen times a week). How can that not rewire me to be suspicious of Indians in general?
I am not racist. I am a white guy with a black adopted daughter (Yeah, I know that’s not proof), but really I LIKE most foreigners and races and even some of my redneck neighbors. I grew up in California and love Mexican Americans, but I just have an uneasy feeling when I hear an Indian accent.
I am not polite to these guys when they call. That bothers me, too, because I used to always go out of my way to be polite to people on the phone, no matter what.
Or maybe I’m just getting grumpy in my old age. That could have something to do with it.
I actually speak to real MS agents (solicited via the Office 365 portal) and some of them really do have Indian accepts. Worse, they often have cross-talk in the background.
And yes, these solicited calls mean that MS really is calling me.
Bottom line: the scammers sound like they’ve done a reasonably good job of emulating these call centers.
FWIW, for MS, the most important things to remember are:
1. use a modern.ie VM instead of giving them access to real hardware (this makes it easier to hide your stuff since it isn’t there in the first place)
2. the only address you should ever visit is https://support.microsoft.com/help — they give you a 6 digit code. If they *ever* tell you to go somewhere else, scream, then hang up, then reach out to Microsoft via some other means. According to web.archive.org, that url has been in use since at least 2011: http://web.archive.org/web/20111128024550/http://support.microsoft.com:80/help
The spammers and scammers are intolerable. There is not much point in blocking or reporting those calls since the phone numbers are likely fake. If a spam text includes a URL, I will forward that to VZW spam reporting.
It’s about to the point where I am going to get a burnable flip phone for voice and text messaging. If the bad guys start calling or texting that number, then as Seth Meyers would say, “Ya Burnt!”
I don’t even think a burner phone would work at this point! Last night I received a spam call on the On-Star phone number linked to my vehicle. I seriously could not believe it. As long as there is any type of phone number they will find it!
The telemarketers just bulk dial an entire range of numbers (e.g. (123) 456-**** ) without concern for whether or not a number is associated with a customer.
Since they’re probably using hacked phone switches, they can have their software place millions of calls. Their software will ignore the ones that can’t be complete (e.g. invalid numbers), the rest will go through, and the cost will be billed to whatever company they hacked.
“place millions of calls”
As I commented in another article. They can call my phone all they want; doesn’t ring on my end with the No-Ring app I installed. As I don’t use my number for incoming business unless I initiate the contact, I have very little need to have someone I don’t know calling me=No Ring for people I don’t know.
I am in agreement with what others are saying about this being caller ID spoofing and the number matching the default Apple Inc. contact. The default Apple Inc. contact comes from the iCloud address book so if you do not have iCloud enabled in your contact groups, you won’t see the contact listed. I always delete the Apple Inc. contact when I get a new phone or reset my phone to factory default. I also have told my elderly parents to never trust anyone calling them stating they are with any computer related company.
I just called the 866 # that Brian referenced. They kept hanging up on me. Finally, one of them stayed on and asked for the email address i use for my icloud account. I gave him an old Yahoo account that is still used, however, he kept telling me the address was no good? He finally just hung-up.
” and most importantly to just hang up the moment the caller starts asking for personal information.”
no, no and more no. Waste their time as much as
possible.. If everyone did this they would find
another scam.
“Hang on, I wrote that down somewhere. I can’t unplug my phone or it will die. Can you look up the price of a new battery while I go look for that info you need?”
*starts watching TV*
There’s a guy on YouTube (Kitboga) who’s a genius at trolling scammers and wasting their time. https://www.youtube.com/watch?v=poUws4y6vro is one example.
Interestingly I had four entries in my iPhone contacts for Apple. One, as mentioned here in the article. Which seemingly gets created by default somehow. One for a personal contact, the person of whom worked for a cosmetics company and there’s no way I would have thrown this person into such a contact myself. Another for Linode. And another for HandCent. Two companies. Again, there’s no way I would have nowingly created such contacts. So it raises a big question about how contacts could be created unknowingly. It’s possible I did something boneheaded unknowingly myself. But this was very weird to find.
I’d say the scam leverages the fact this contact somehow exists for a majority of iPhone users. It’s an trusted identity scam with the 866 number a redirect based on (1) establishing (fraudulent) trust and (2) some sense of urgency.
I never answer unexpected calls – that way they don’t know my number is valid. I have very very few robo calls as a result – in fact I can’t remember the last one I had. Voice mail will give you away though, better to never set it up.
Yes I have a normal life and am not completely isolated in a bubble; my phone is just a tool, and I used it to call out – incoming calls are strictly my own business.
Don’t you have voicemail?
If you don’t answer and the call rings thru to your voicemail, it has the same net effect of validating a live line.
Also, dead lines usually result in a system response that indicates that status.
Or am I missing smth?
So if the scammers called at 4:34 PM the day before, why is it shown as a canceled call rather than a missed call?
When people who are clued up on tech scams are almost getting fooled, there really is no chance for the average person to not get scammed. I give advice to family members how to check for scams but when it’s getting this clever, I can’t blame them if they fall for it which is so frustrating as you constantly need to tell them how now to look for updated scams. More needs to be done to stop this or really damper the efforts. However everytime you call out a scam, the scammers just evolve.
I suspect elder abuse victims probably make up the majority of payouts. I know a victim recently scammed from a fake Apple call.
The victim is well passed retirement age and freaked out that Apple called him. The scammer then emailed the victim an official-looking fake Apple email after the victim divulged his email address when asked. The victim told me this convinced him the caller was really from Apple.
The victim then gave the caller remote access to his Mac and allowed the scammer to activate online banking for him since he wasn’t enrolled at the big national bank he used. The scammers tried to transfer money out but failed because the bank flagged it as suspicious. The scammer also got at least one credit card number but the credit card company blocked attempts to charge it.
**********************
ELDER ABUSE VICTIMS ignore numerous giant red flags.
**********************
For example…
After failing to take money from his bank and credit card, the scammer looked up the victim’s physical address on a map after the victim divulged it. The scammer then directed the victim to the nearest large regional grocery store chain to buy $2,000 worth of Google Play gift cards so the victim could read the serial numbers to the scammer over the phone.
The checkout clerk at the first grocery store told the victim he was being scammed because the store sees lots of victims try to buy hundreds or thousands of dollars worth of gift cards. The clerk even called over the manager, who tried to dissuade the victim from buying the cards. The victim told me this.
So the persistent victim went to another grocery store (same chain)!!!
The cooperating grocery store only had low-value Google Play gift cards under $30, but the caller/scammer told him they would do. So the victim bought $2,000 worth of low-value Google Play gift cards and read serial numbers to the scammer over the phone.
About 4-5 hours later, the victim called me and left a message that he thought he may have been scammed. He still wasn’t certain! I called him back and told to hang up and call his bank to shutdown all his accounts. He did this. He told me some of the gory details and I deduced others the next day.
Life Pro Tip: when someone, especially a aged retired person, tells you he or she has been scammed, don’t exclaim shock, e.g., “You what!? You gotta be kdding! Oh my god! Jeeeeez!” I started to do that but noticed right away he shrunk (on the phone) in humiliation so I stopped. It takes a lot of self-discipline to not show your shock in cases like this. I read a few years ago that it’s common for elder abuse victims to feel so embarrassed after they realize or suspect they’ve been scammed that they never tell anyone, including police.
So the next day, the victim drove over a hundred miles to my place with his laptop. With the Internet disabled, I examined the browser history starting with period after the initial call. It included taking the victim to a remote access software site, coinbase.com and a bank’s enrollment page. The victim filled in more details about what happened on these sites.
I examined the Mac including hidden files and removed the nothing-special remote access software and scanned the browser and Mac with various software tools installed from a USB flash drive and took screen shots of the browser history before clearing it. I cleared temp files, etc. (If it were a Windows PC, I would have erased the whole thing or replaced the hard drive or junked it if it were several years old.) Since I didn’t see any download or browser history for downloads other than the remote access software and didn’t see any macOS record of anything else installed after the remote access began, I deemed the Mac safe enough for non-banking, non-tax, non-credit card online use, which the victim didn’t do anyway. I probably should’ve erased his Mac and restored from his TimeMachine backup, but I told the victim if anything suspicious happened on his laptop after that, he should call me and we’ll do the big wipe and restore.
Using my computer, we changed his email password and hopefully all the other passwords he used. On his Mac, we changed his user account password.
The scammer called back while I worked on the victim’s disconnected Mac. I did my best to guilt-trip him, asking him if he believed in evil (he said he did) then telling him he’s evil etc, but I also encouraged him to lead a revolution against the caste system because it’s so unjust, assuming from his accent that he was in India. We yelled at each other and I hung up. If he recorded my voice, it wouldn’t have done him any good (probably) since he didn’t know anything about my identity, e.g., email, name, phone number.
I then spent around an hour with the victim using my computer, not his, to sign up for credit freezes I’d learned about from KrebsOnSecurity years ago and printed the resulting important info and put in a folder for him to take:
Equifax
https://www.freeze.equifax.com/Freeze/jsp/SFF_PersonalIDInfo.jsp
Experian
https://www.experian.com/freeze/center.html
Innovis
https://www.innovis.com/personal/securityFreeze
Transunion
https://www.transunion.com/credit-freeze/place-credit-freeze2
ChexSystems
https://www.chexsystems.com/web/chexsystems/consumerdebit/page/securityfreeze/placefreeze/
NCTUE National Consumer Telecom and Utilities Exchange
(National and some state options)
http://www.nctue.com/Consumers (“security freeze”)
https://www.exchangeservicecenter.com/Freeze/jsp/SFF_PersonalIDInfo.jsp
The next day the victim changed his phone number and the day after met with his bank to get new account numbers for everything.
Another elder abuse case was pretty outrageous. A widow in her mid-70s widow fell for fake online boyfriend scams and lost a total of about $19k USD, including at least one bank transfer to China I saw. The adult daughter called me for help with her victim mom, who still thought the online boyfriends had been real. There were probably 20 RED flags in this one. Even the victims’ aged friends tried to warn her but she said they were just jealous because she had a much younger boyfriend. The daughter had to call a doctor to figure out how to stop the mom from gleefully giving away her money to scammers. I don’t know what happened after that. The scammer(s) had created at least one new email address for the victim to use in order to prevent the family from interfering by checking the mom’s email. The scammer also texted the victim using SMS and various smart phone apps he talked her through setting up on her smart phone. The grown daughter’s goal was to take away the smart phone and give her mom a flip phone with a new phone number after hopefully finding a doctor to issue an order to allow this type of intervention.
I have numerous other stories of smaller scams — $250 and $500 — retired people fell for online and the phone that included victims giving the scammers remote access!
Really, no one should answer unsolicited phone calls or reply to unsolicited texts or email directly. Elder abuse victims typically ignore numerous huge red flags.
Props for all you did to educate that person, lend technical assistance and share the story with us. The elderly are victims to so many scams already, but their attack surface rises exponentially when they connect without proper education. Please, please please, if any has gifted a connected device to elderly parent, relative or friend (or anyone for that matter), make sure they have a good awareness of the criminals waiting to take advantage of them and how to protect themselves online from these people.
Does anyone know of a good, no nonsense cybersecurity and scam avoidance primer that could be given to elders that they’d read and take seriously? This feels like a situation where an ounce of prevention is worth a pound of cure, especially when the scammed elders won’t get help even after being scammed – had one of these in my own life and it was only a casual mention that led me to deduce it. Elder had an online auction account compromised and seemed to treat it as “broken, need to switch to a new one” rather than recognizing as fraud and a potential attack vector for identity theft.
When I was working at Symantec, one of the field engineers published this https://www.symantec.com/about/newsroom/press-releases/2006/symantec_1109_01 Its aimed at teens, and probably showing its age now, but us old folk like to feel young sometimes 🙂
I am not sure if this tip actually works or not, as I heard it from a colleague. The idea is that if your voice-mail message starts with the standard tones indicating a disconnected line (just a 1 second pre-roll) — then followed by your own voice as a normal recorded welcome message — the tone will immediately disconnect the automated spam callers and rob-callers, and possibly list your number as ‘disconnected’. A disconnect line sound can be downloaded here: https://www.youtube.com/watch?v=NI_wyiY4vyk
I received a similarly spoofed call from ‘Spectrum’ a couple days ago, offering to lock in lower rates for life. I asked the guy if I could be sure he was from Spectrum, and he said to check my caller id, which did say spectrum and it was the legit number. I told the guy that is easy to spoof, and he hung up on me.
When I called Spectrum, the person who answered said I was the second person that day to call about the scam.
I consider myself pretty aware about these scams, but this one seemed legit, and even as I was questioning the guy, I had doubts that it was a scam.
“If you want to reach your bank, for example, call the number on the back of your card”.
I predict supply-chain involvement in the card production process where that number is made to point to the spoofers.
just simple spoof of apples genuine support number to get around your guard
apple has always included a contact with their own info but if you had iphone for years you probably got rid of it at one point and importing your current contacts every time you get new phone
if you just return the call you receive from you would be save &contact apple – scam rely on you calling number left in voicemail
I have been forwarding all Indian based scammers over to Lenny the virtual chat bot designed to waste their time. Its amazing how many will fall for this and talk to Lenny for an extended time.
https://toao.net/595-lenny
Lenny even has his own YouTube channel
https://www.youtube.com/playlist?list=PLduL71_GKzHHk4hLga0nOGWrXlhl-i_3g
Criminals never sleep They Work hard to film new ways.
the system isa vulnebre. system isa seal… fraudsters scammers just like the rats who Take food IF its left.
we all member when was the bank7ng trojan times.
Old school times like Zeus botnets.
Yes tht all cost US a lot.
but Now we see banking system Speciallly in United Kingdom is wellll improved Against key loggers and trojan.
so as we see Now fraudsters commiting fraudlent activity until, the system is so secure that there is no ways to commit identy, theft or any fraudlend activity.
its Long way but one day we Will have Order out of Chaos.
You could imagine my “surprise” to see this article (great read and information, thank you Mr. Krebs!) after receiving a similar attempt.
My scenario starts with a call on December 17, 2018 at 6:54pm CST from (800) 531 8722, picked up since it was from my bank (USAA) and calls from them around holidays and/or travels were not rare. The call started with routine greetings and information, the man identified himself as Alex or Alexander (iirc, but I’ll call him Alex) who’s a member of USAA’s Fraud Prevention Team. Alex blew past the required initial identification and authentication part of the phone conversation (first immediate red flag to me) with an increasingly urgent cadence. He informed me that “they” have picked up 2 fraudulent charges in Florida and noted that I was on “their” record as residing in Texas, I replied with no more than a “yes” and sprinkled a few who/what/where/when/how questions (while also verifying my account activities, no activities matched what he told me…weird).
Alex adds a few “relevant” information and, finally, gets to the reason for his efforts: he needed me to tell him my pin to quickly close out my debit card and expedite a new one. Now, there are two distinctive pins, one is an account verification pin (used on the initial ID and Auth) and the second being my debit card pin. As y’all might have guessed, Alex explicitly asked for my Debit Card pin. At that point my goal was to see how patient Alex would be and what other BS he could create on the spot. Ultimately, Alex abruptly hung up after telling him to stay on the line while I renew my own debit card and for him to verify I’ve done it correctly. He did try to pull my pin a handful of times, but unfortunately for Alex it was a waste of time.
Although this attempt didn’t work out for Alex (and for his “team”), I can see how this playbook might work. Spoofed phone number from legitimate org., a real person talking with similar script, and creating a urgency to an already stressful situation. People should understand how organizations perform their identification and authentication over the phone or at the very least hang up if there’s any doubt to the legitimacy and call the organization to verify their need to call you.
It occurs to me on reading this thread that the recent developments in ACD / call queuing where you’re invited to leave a callback number create a tricky social risk – our financial service providers are starting to train us to expect calls from them, not the other way around.
Not only that, it’s made me biased against Indians calling me. They NEVER, legitimate or not, get the benefit of the doubt; they’re a scammer until proven otherwise, and I never give them the chance to prove it.
A good call queueing system will provide a caseID for identification/authentication for the callback. Got to have pen and paper handy before making the call. Ideally it would not use letters at all as “e c b t v” etc and “8 A H” sound a lot alike if there is ambient noise present, and that’s just English for English-speakers.
In Westby’s story, she went online to Apple’s website and got a caseID there.
Scammers might start putting a caseID in their spam, to appear legitimate, and as the target might call back from a number not in their outgoing call database.
Tangential, but sorta related . . . A.I. is getting foxier:
https://www.zerohedge.com/news/2019-01-02/ai-program-taught-itself-how-cheat-its-human-creators
This could become a powerful tool for the scammer-industrial complex.
Caller ID is spoofed because there is nothing requiring anyone to comply. Anyone with a SIP trunk can impersonate just about anything. None of this is new, as frankly ISDN in the 1990’s had this problem too.
The cost per minute at the wholesale level to call the USA from anywhere on the internet is fractions of a penny per minute. This includes many countries that have no extradition treaties with the USA.
There are thousands of carriers worldwide. In order to effectively block all of this a new standard would need to be created. This will take years. Newer video conferencing solutions like Facetime have checksums, but most corporate PBX’s live 10-15 years minimum.
The younger generations simply don’t talk on the phone. Voice as we know it is dying. It’s not that they’re targeting seniors….People under the age of 30 do not answer the phone unless it’s someone they know does not text message.
The reality is that the USPS may outlive ma-bell long term. Carriers like AT&T, Verizon, Sprint, etc are going to make money regardless. In the end, whether the data packet is voice, text, or youtube…They’re getting paid.
Very informative column. I will forward a link to everyone I know to using an iphone.
DanG , makes a good point about the hundreds of SIP trunk online services and caller ID spoofing. Just google SIP or go to Wikipedia and you can see the SIP trunkers spread across the globe. The doesn’t include the software packages that can be used. It is a danger because it is the heart of Swatting scams that police fall for and Brian Krebs has experienced. Note that Caller ID is not the same and actual phone billing records.
There is a Truth in caller ID act of 2010 which is supposed to stop call ID spoofing. It doesn’t. Ironically, there is a Law Enforcement loop-hole which allows Law Enforcement to use caller ID spoofing yet, they get scammed by the same trick. I can only shake my head at the whole mess.
perfect security relies on you making 1 of 2 choices…
1. never install an app and never click a link
or
2. make like “Hotel Califonia”.. You can come any time you like but you can never leave. That is, block all exits.
A nefarious entity using an asterisk box can accomplish such spoofing. The caller ID can be changed on the fly.
Are all the calls from someone with an Indian accent?