A 20-year-old Illinois man has pleaded guilty to running multiple DDoS-for-hire services that launched millions of attacks over several years. The plea deal comes almost exactly five years after KrebsOnSecurity interviewed both the admitted felon and his father and urged the latter to take a more active interest in his son’s online activities.
Sergiy P. Usatyuk of Orland Park, Ill. pleaded guilty this week to one count of conspiracy to cause damage to Internet-connected computers and for his role in owning, administering and supporting illegal “booter” or “stresser” services designed to knock Web sites offline, including exostress[.]in, quezstresser[.]com, betabooter[.]com, databooter[.]com, instabooter[.]com, polystress[.]com and zstress[.]net.
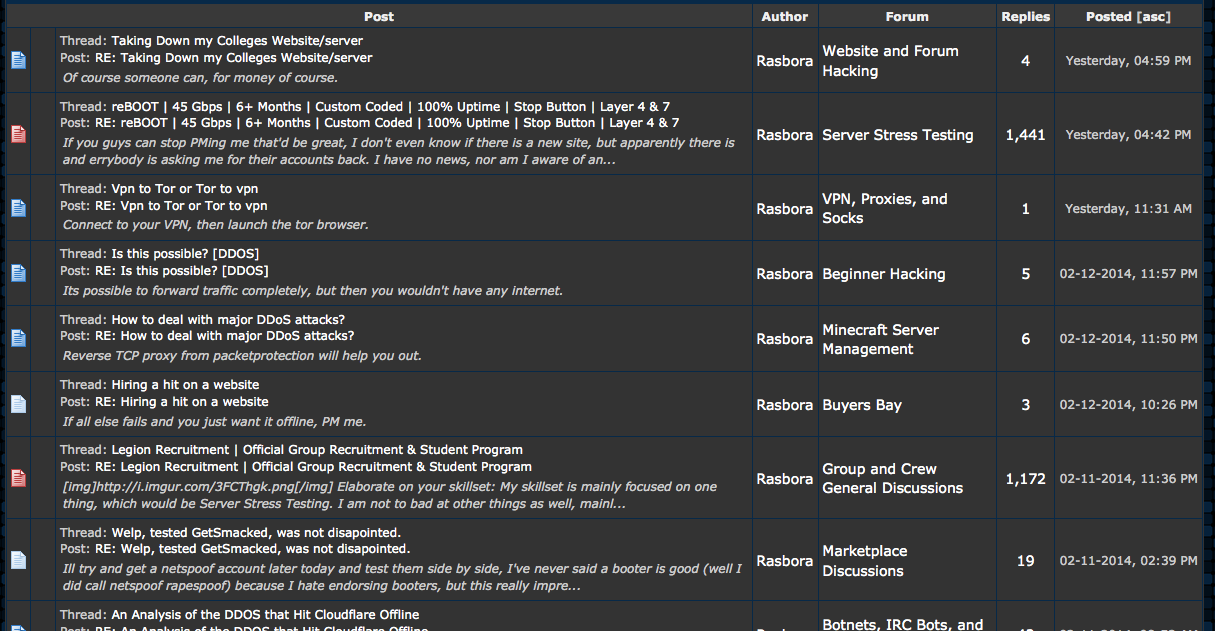
Some of Rasbora’s posts on hackforums[.]net prior to our phone call in 2014. Most of these have since been deleted.
In February 2014, KrebsOnSecurity reached out to Usatyuk’s father Peter Usatyuk, an assistant professor at the University of Illinois at Chicago. I did so because a brief amount of sleuthing on Hackforums[.]net revealed that his then 15-year-old son Sergiy — who at the time went by the nicknames “Rasbora” and “Mr. Booter Master” — was heavily involved in helping to launch crippling DDoS attacks.
I phoned Usatyuk the elder because Sergiy’s alter egos had been posting evidence on Hackforums and elsewhere that he’d just hit KrebsOnSecurity.com with a 200 Gbps DDoS attack, which was then considered a fairly impressive DDoS assault.
“I am writing you after our phone conversation just to confirm that you may call evening time/weekend to talk to my son Sergio regarding to your reasons,” Peter Usatyuk wrote in an email to this author on Feb. 13, 2014. “I also have [a] major concern what my 15 yo son [is] doing. If you think that is any kind of illegal work, please, let me know.”
That 2014 story declined to quote Rasbora by name because he was a minor, but his father seemed alarmed enough about my inquiry that he insisted his son speak with me about the matter.
Here’s what I wrote about Sergiy at the time:
Rasbora’s most recent project just happens to be gathering, maintaining huge “top quality” lists of servers that can be used to launch amplification attacks online. Despite his insistence that he’s never launched DDoS attacks, Rasbora did eventually allow that someone reading his posts on Hackforums might conclude that he was actively involved in DDoS attacks for hire.
“I don’t see what a wall of text can really tell you about what someone does in real life though,” said Rasbora, whose real-life identity is being withheld because he’s a minor. This reply came in response to my reading him several posts that he’d made on Hackforums not 24 hours earlier that strongly suggested he was still in the business of knocking Web sites offline: In a Feb. 12 post on a thread called “Hiring a hit on a Web site” that Rasbora has since deleted, he tells a fellow Hackforums user, “If all else fails and you just want it offline, PM me.”
Rasbora has tried to clean up some of his more self-incriminating posts on Hackforums, but he remains defiantly steadfast in his claim that he doesn’t DDoS people. Who knows, maybe his dad will ground him and take away his Internet privileges.
I’m guessing young Sergiy never had his Internet privileges revoked, nor did he heed advice to use his skills for less destructive activities. His dad hung up on me when I called Wednesday evening requesting comment.
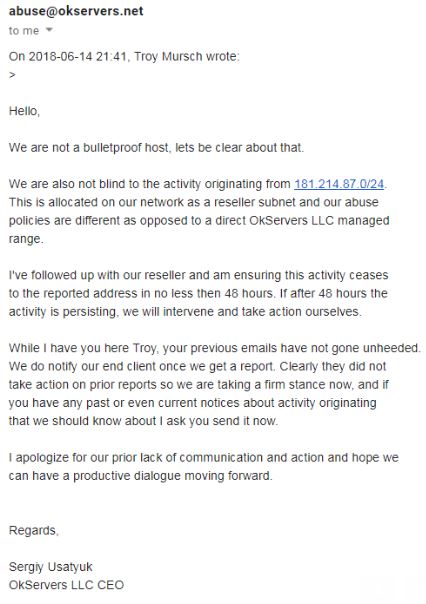
Court documents (PDF) related to his case indicate Sergiy Usatyuk and an unnamed co-conspirator earned nearly $550,000 launching some 3.8 million attacks through their various DDoS-for-hire services. The government says he ran the booter services through a Delaware corporation called “OkServers LLC,” which routinely ignored abuse complaints and as such effectively operated as a “bulletproof” hosting company — despite Sergiy’s claims to the contrary.
Here’s Sergiy’s response to multiple abuse complaints about OKServers filed in the summer of 2018 by Troy Mursch, chief research officer at Bad Packets LLC.
Sergiy’s guilty plea comes amid a major crackdown by the FBI and the Justice Department on booter services and their operators. In December 2018, the DOJ brought charges against three men as part of an unprecedented, international takedown targeting 15 different booter sites.
According to the government, the use of booter and stresser services to conduct attacks is punishable under both wire fraud laws and the Computer Fraud and Abuse Act (18 U.S.C. § 1030), and may result in arrest and prosecution, seizure of computers or other electronics, significant prison sentences, and a penalty or fine.




Who is the Defense Criminal Investigative Service? Seems like they are always mentioned whenever the FBI does something big on cyber.
https://en.wikipedia.org/wiki/Defense_Criminal_Investigative_Service
Let me Google that for you! LOLOLOL
The Defense Criminal Investigative Service is the criminal investigative arm of the Office of the Inspector General, U.S. Department of Defense. DCIS protects military personnel by investigating cases of fraud, bribery, and corruption; preventing the illegal transfer of sensitive defense technologies to proscribed nations and criminal elements; investigating companies that use defective, substandard, or counterfeit parts in weapons systems and equipment utilized by the military; and stopping cyber crimes and computer intrusions.
pretty cool … I guess part of DoD?? – here is something else I found on them they have Special Agents … who knew!?!?
https://www.dodig.mil/Components/DCIS/Becoming-a-Special-Agent/
DCIS Special Agents
DCIS special agents are entrusted to perform criminal and civil/administrative investigations involving companies, persons and property affiliated with the DoD pursuant to Federal Statues and applicable DoD Directives. Special agents conduct arrests, searches, and seizures in accordance with the U.S. Constitution, pertinent laws, regulations, directives, and court decisions, including the collection and preservation of physical and digital evidence. Special agents analyze allegations, complaints, referrals, and investigations to identify issues and the type of evidence needed to properly address each matter. Special agents interview witnesses, suspects, and others, and can appear as a witness before Grand Juries, trial courts, or other legal proceedings. The duties of a special agent requires intensive investigations often worked in cooperation with multiple agencies. Special agents prepare comprehensive investigative reports in order to present complex findings in a clear, logical, and impartial manner. Special agents comply with all existing agency policies and procedures, including the use of force policy, pertaining to use of assigned firearms.
signal6 — Let me Google that for you!!!
https://en.wikipedia.org/wiki/Defense_Criminal_Investigative_Service
yw
Let me Google that for you! HAH
The Defense Criminal Investigative Service is the criminal investigative arm of the Office of the Inspector General, U.S. Department of Defense. DCIS protects military personnel by investigating cases of fraud, bribery, and corruption; preventing the illegal transfer of sensitive defense technologies to proscribed nations and criminal elements; investigating companies that use defective, substandard, or counterfeit parts in weapons systems and equipment utilized by the military; and stopping cyber crimes and computer intrusions.
pretty cool! Apparently they are part of the DoD? Also they have Special Agents too – who knew!!??
(copied from a jobs website)
DCIS Special Agents
DCIS special agents are entrusted to perform criminal and civil/administrative investigations involving companies, persons and property affiliated with the DoD pursuant to Federal Statues and applicable DoD Directives. Special agents conduct arrests, searches, and seizures in accordance with the U.S. Constitution, pertinent laws, regulations, directives, and court decisions, including the collection and preservation of physical and digital evidence. Special agents analyze allegations, complaints, referrals, and investigations to identify issues and the type of evidence needed to properly address each matter. Special agents interview witnesses, suspects, and others, and can appear as a witness before Grand Juries, trial courts, or other legal proceedings. The duties of a special agent requires intensive investigations often worked in cooperation with multiple agencies. Special agents prepare comprehensive investigative reports in order to present complex findings in a clear, logical, and impartial manner. Special agents comply with all existing agency policies and procedures, including the use of force policy, pertaining to use of assigned firearms.
Sad. I wonder if the dad was just naive and believed his son’s lies (such as “But dad, this is just a stranger, I don’t do that!”) despite the evidence (these people and teens doing this don’t get $550k in a couple years without having stuff like fancy cars and apartments), or if the dad was actively getting kickbacks.
Either way he had a chance a year before the period he was convicted of, to have an intervention and stop his son’s activity, keep his son out of jail and without a conviction. And he DIDN’T TAKE IT. That’s a failure of parenting.
@Somguy
“…Court documents (PDF) related to his case indicate Sergiy Usatyuk and an unnamed co-conspirator earned nearly $550,000…”
I wonder whether that “influenced” his father’s reluctance to intervene…
…or whether he might even be the unnamed co-conspirator.
It’s honestly not that difficult to hide cybercrime from your parents. It’s not like he’s coming home reeking of weed or drunk.
From the article, it does seem the dad really didn’t do much at all. He seemed concerned initially, but I think once that money started rolling in (there’s no way that kid would have been able to successfully hide that amount of money), the dad had a hand somewhere in it.
Quite easy to hide when it looks like the DoJ seized most of it. So the kid didnt spend it on much. He kept it hidden.
That’s a good point, I think it was a matter of time either way. It’s just a shame he was given the chance on several occasions and didn’t take it.
It’s a bit unfair to blame the dad here. The kid was 15 when Krebs talked to him, and for all we know the dad might have grounded him until he was 18 and kept him locked in the basement without internet access. But once he turned 18, it’s out of dad’s hands. Sometimes good parents raise kids who do bad things. It’s not the dad’s fault.
I’m a parent, and a darn good one. But don’t try to hold me responsible for anything my adult children do.
ZDNet has a few more details on his arrest, including how his IP address was tracked: https://www.zdnet.com/article/operator-of-eight-ddos-for-hire-services-pleads-guilty/
Waitaminute….
“At the time of his arrest, US prosecutors seized 10.74 bitcoin (worth $542,924 at the time) from Usatyuk’s account, which they believed he made from running the eight DDoS-for-hire portals.”
There’s NO TIME at which bitcount has been with $50,000 each.
Peak was about $20k
https://en.wikipedia.org/wiki/History_of_bitcoin
Zdnet looks to have it wrong, is that what’s in the press release too?
I believe those sites long accepted other forms of payment, most especially PayPal and Google Wallet. I don’t think the bitcoin seized was meant to represent the totality of their earnings.
ZDNet tried to paraphrase the court documents and failed. Here’s what they really stated:
“The forfeitable property includes, but is not limited to, the following:
1. $542,924 in United States currency, including approximately 10.74059929 Bitcoin, representing the gross proceeds of the offense alleged in this Criminal Information obtained by the defendant;”
I believe that’s stating they seized cash/cash accounts + Bitcoin.
Ah, so reporter not doing his research adequately, which is a frequent occurrence nowadays in media.
Except for people like Brian Krebs, he’s meticulous in his research and links source documents when possible and other information, and I really appreciate his diligence.
Thanks for checking the source documents and explaining that with your comment.
This guy is just a 20 years old low life miscreant , now going to do hard time locked up in federal prison
Isn’t that sad? At 20 years old, the whole life ahead of him and throwing it away on something so stupid…
To men, that kid’s dad is equally responsible and seems like a real “winner”. So, failed parenting on his end.
While an unpopular opinion, I ‘ve long believed that parents should be held more responsible for their minor children’s actions.
Yep, and in a case like this where the father was warned about his sons behaviour, he should be facing lots of charges, joint enterprise, aiding and abetting, enabling, etc etc, there areots of laws I should think he could be charged with, even with the usa’s and some states strange ideas of law and/or justice..
“minor” “earned nearly 550k” “OkServers LLC CEO”
Darn. I’m in the wrong business.
So the DOJ press release and this article fail to mention how much prison time he is going to get.
Does anyone know?
He has not yet been sentenced, and there has been no mention of any sort of plea arrangement. The press release states only that he has pleaded guilty to the charges.
It’s one of those situations again when they come to this country and think that they can keep on doing what they were up to in their homeland. Notice that there’s rarely any American names involved in any of these stories that Brian reports about. Sad. Because this guy could’ve earned a good living had he gone to the good side.
Where does it say he or his father are immigrants?
And for that matter, are “Tyler Barriss”, “Casey Viner” and “Shane Gaskill” American enough names for you? Those are the three who were found guilty of the Swatting that turned deadly.
Like Squanto, Sequoyah or Sacajawea? You should get a real American name, Dennis,
@bofo
“result in arrest and prosecution, seizure of computers or other electronics, significant prison sentences, and a penalty or fine”
Still feel like you’re in the wrong business?
I propose the creation of the Internet Darwin Award, for individuals removing themselves from the Internet through their own actions.
This guy knew that his cover was blown in 2014. His response was to change is hacker aliases. My guess is that law enforcement had a laser dot on this guy’s forehead since 2014 and it was just a matter of time before they pulled the arrest trigger.
Hi,
I fell on this story on Twitter (no harm, thanks) and it looks very interesting.
What I am still trying to understand is who is paying for taking some sites down, since he was not doing that for “fun” only.
For example in 2014 he launched an attack on Krebsonsecurity. Did you manage to know if he was doing that to test his knowledge or if someone wanted to harm you specifically.
thanks
As i understand it, the attack on Krebs was just to show the mods of the forum that he was worthy of being part of their community, a sort of rite of initiation.
As for other websites, there are plenty of people who’d be willing to pay for that. Maybe you want to knock a competitors website offline at a critial point in time to drive traffic to your business, maybe you want to make sure that you win a fight in a video game (either for prestige, for monetary gain or simply out of rage) and so you pay someone to know their internet off, etc.
I remember when the original article came out, and I figured things wouldn’t end well with the father’s attitude. It actually made me quite angry at the time.
Thanks for following up on this Brian! One of the most frustrating things about most media sites is they never follow up on what they report.
Seems like a smart fellow who just needs some compasion. But with the police, it’s always LOCK EM UP. Prison will make him a criminal. He can probably TEACH others a lot of useful skills. But the prosecutors just want to GET him. What a shame. Who among us has not made a mistake?
spoken like someone who’s involved in the same thing. this kid had many chances to stop what he was doing. he didn’t. how many mistakes did he make? ask the 3+M people who were on the receiving end of his attacks over 5 years. sorry, but try and shift the blame if you want, but you can’t put this down to overzealous prosecutors.
“Spoken like someone who’s involved in the same thing…”
What an asinine comment.
A person gives an opinion and you accuse him/her of being a criminal?
I hope you itch in places you can’t scratch.
Seems that hit a real nerve with you, readership1. Perhaps the comment mirrored your own reflection….
“Prison will make him a criminal.” he already is that. it’s time people started recognizing ddos for what it truly is: a crime. if i rob your house and get caught and convicted, i’m a criminal. ddos is just another crime, but without justice there are no consequences.
@WUTSINTERWEB
Dude, he’s already a criminal. The only thing he could perhaps teach others at this point is how to not get caught the same way he was. In the end, anyone doing this type of stuff from Western countries will be caught, if you make yourself too big of a target and PITA to others.
Oh yeah, wonder if he and Dad were filing their income taxes properly?
This argument could apply back in 2014, but he did get all the clear warnings and exposition back then about the “mistake” and still knowingly continued to press on. He could have chosen back then, after being caught for the initial offences, to teach others a lot of useful skills – but he chose that he’d prefer getting lots of other people’s money and going to jail for that.
I’ve never made a “mistake” that earned me more than 500k USD.
Thanks for copying Wikipedia for me, I already know the basic information about the DCIS. I was wondering if Brian knows more about them than a copy of their mission statement reposted on Wikipedia.
It’s not related to this attack, but in 2000 I was watching the Tigger Movie with my 4-year-old daughter. I was paged out of the theater because the website of the company I worked for came under DDOS attack, and I was the network engineer on-call. I still remember my daughter saying “Daddy we’re missing the movie”.
DDOS attackers are criminals. In addition to the financial toll they also inflict a human toll on the white-hat defenders.
I know that’s part of the job, and part of the reason I got paid. But every time I think about a black-hat hacker I think about The Tigger Movie.
I can be persuaded that DDOS creates frustration, unnecessary labor costs, and interference with authorized access to computer resources.
I can be persuaded that DDOS represents unauthorized access to computer resources.
I might even be convinced that DDOS is a crime.
But pulling a child out of a movie for work is the result of terrible planning, not DDOS!
Next time, bring your mom or sister, in case you have to run. Haha.
You really are a tool, that is all.
Odd, unless I scanned it too quickly, the DOJ press release says nothing about restitution, fines, or prison time. That’s odd for a DOJ release.
Also, only one count. This is odd unless the kid flipped and has become a cooperating witness.
There is more to this.
And with a name like Sergiy, it leads back to some part of Putin’s Russian Mob.