A highly targeted, malware-laced phishing campaign landed in the inboxes of multiple credit unions last week. The missives are raising eyebrows because they were sent only to specific anti-money laundering contacts at credit unions, and many credit union sources say they suspect the non-public data may have been somehow obtained from the National Credit Union Administration (NCUA), an independent federal agency that insures deposits at federally insured credit unions.
The USA Patriot Act, passed in the wake of the terror attacks of Sept 11, 2001, requires all financial institutions to appoint at least two Bank Secrecy Act (BSA) contacts responsible for reporting suspicious financial transactions that may be associated with money laundering. U.S. credit unions are required to register these BSA officers with the NCUA.
On the morning of Wednesday, Jan. 30, BSA officers at credit unions across the nation began receiving emails spoofed to make it look like they were sent by BSA officers at other credit unions.
The missives addressed each contact by name, claimed that a suspicious transfer from one of the recipient credit union’s customers was put on hold for suspected money laundering, and encouraged recipients to open an attached PDF to review the suspect transaction. The PDF itself comes back clean via a scan at Virustotal.com, but the body of the PDF includes a link to a malicious site.
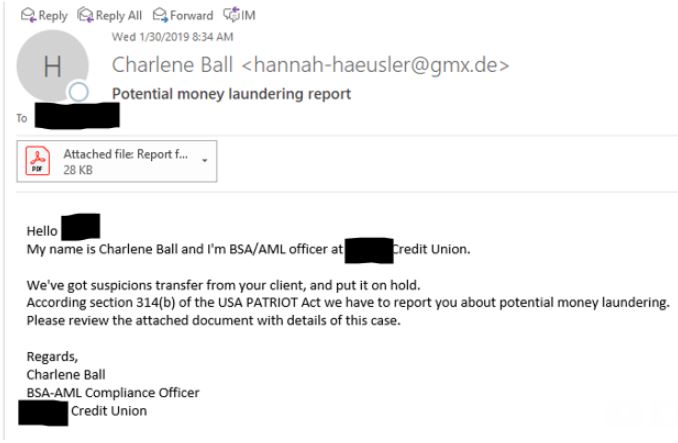
One of the many variations on the malware-laced targeted phishing email sent to dozens of credit unions across the nation last week.
The phishing emails contained grammatical errors and were sent from email addresses not tied to the purported sending credit union. It is not clear if any of the BSA officers who received the messages actually clicked on the attachment, although one credit union source reported speaking with a colleague who feared a BSA contact at their institution may have fallen for the ruse.
One source at an association that works with multiple credit unions who spoke with KrebsOnSecurity on condition of anonymity said many credit unions are having trouble imagining another source for the recipient list other than the NCUA.
“I tried to think of any public ways that the scammers might have received a list of BSA officers, but sites like LinkedIn require contact through the site itself,” the source said. “CUNA [the Credit Union National Association] has BSA certification schools, but they certify state examiners and trade association staff (like me), so non-credit union employees that utilize the school should have received these emails if the list came from them. As far as we know, only credit union BSA officers have received the emails. I haven’t seen anyone who received the email say they were not a BSA officer yet.”
“Wonder where they got the list of BSA contacts at all of our credit unions,” said another credit union source. “They sent it to our BSA officer, and [omitted] said they sent it to her BSA officers.” A BSA officer at a different credit union said their IT department had traced the source of the message they received back to Ukraine.
The NCUA has not responded to multiple requests for comment since Monday. The agency’s instructions for mandatory BSA reporting (PDF) state that the NCUA will not release BSA contact information to the public. Officials with CUNA also did not respond to requests for comment.
A notice posted by the U.S. Treasury Department’s Financial Crimes Enforcement Network (FinCEN) said the bureau was aware of the phishing campaign, and was urging financial institutions to disregard the missives.
Update, 11:13 a.m. ET: Multiple sources have now confirmed this spam campaign also was sent to BSA contacts at financial institutions other than credit unions, suggesting perhaps another, more inclusive, entity that deals with financial institutions may have leaked the BSA contact data.
Update, 5:26 p.m. ET: The NCUA responded and released the following statement:
Upon learning of the recent spear phishing campaign targeting Bank Secrecy Act officers at credit unions, the NCUA conducted a comprehensive review of its security logs and alerts. This review is completed, and it did not find any indication that information was compromised.
The most recent information available indicates the campaign extends beyond credit unions to other parts of the financial sector.
The NCUA encourages all credit union staff to be wary of suspicious emails, and credit unions may report suspicious activity to the agency. Additional information about phishing and other information security concerns is available on the agency’s Cybersecurity Resources webpage.
Also, the Treasury Department responded to requests for information about this event, stating:
FinCEN is aware of the phishing attempts and we’re examining the circumstances. There is no indication that any FinCEN systems were compromised.
Here is some information on 314(b) from our website
Note that the 314(b) system is designed so that individual compliance officers (registered with FinCEN) can find and directly contact each other. It provides no access to any type of broad financial database.
Original story: The latest scam comes amid a significant rise in successful phishing attacks, according to a non-public alert sent in late January by the U.S. Secret Service to financial institutions nationwide. “The Secret Service is observing a noticeable increase in successful large-scale phishing attacks targeting unsuspecting victims across industry,” the alert warns.
The Secret Service alert reminds readers that we in the United States are entering tax season, which typically brings a large spike in scams designed to siphon personal and financial data. It also includes some helpful reminders, including:
-Never click on links embedded in emails or open any attachments from unknown or suspect fraudulent email accounts.
-Always independently verify any requested information originates from a legitimate source.
-Visit Web sites by entering the domain name yourself (for sensitive sites, preferably by using a bookmark you created previously).
-If you are contacted via phone, hang up, look up the number for the institution at that institution’s Web site, and call back. Do not give out information in an unsolicited phone call.




Has anyone been able to examine the PDF?
I have not, although I will say that the email itself is a dead giveaway of a malicious file. That said, I’m definitely interested to see exactly what the file does.
We received several of these also. When I (managing Email security – reviewing blocked Emails) noticed them having attached files with our staff’s name in them I notified the effected department incase any of them slipped by. Fortunately our filters are very robust and none did. But we are now on even a little higher alert for this crap than the standard “everything is potentially on fire” alert that is status quo.
People who are stupid enough to open up a PDF file from a unknown person and or source should not be using email until proper security training is provided
That’s my opinion, and I’m sticking to it ! LOL
Go further!
Folks shouldn’t click links or open any file from anyone, if it’s unexpected, without checking if it’s safe.
And if they don’t know how to check, they should seek training.
Why not just get rid of people using email, and move everyone over to a more secure encrypted messaging systems that does not use attachments.
Ha. It *is* possible to go too far further.
That email is laughable. If anyone actually fell for that they need to be fired. No one would ever cite the provision when reporting a suspicious transaction nor would they advise or report about it to anyone but the required authorities. Thats not how AML works.
That was my exact thought too!
This does raise an interesting question: how is that these spoofers master the complexities of cybercrime and yet so clumsily tip their hand with basic errors in language and syntax.
I’m assuming it’s the same reasoning behind 419 scams also having terrible spelling/grammar mistakes. If you’re still going to click the link/attachment after all the spelling and grammar mistakes, you’re probably also going to run whatever file they ask or fill in whatever credentials they want to phish.
If the scammers ever discovery Grammarly, we’re all screwed.
I agree. Very bad if this happens.
What you may not be considering is whether the recipient speaks American English as their native language. Many years ago I was taught a lesson about my own biases. I had the same thought and could not figure out why some people were falling for those emails.
It turned out they were H1B employees (from other countries) and the grammar did not look all that odd to them.
Working in software and security for hundreds of different FI’s, I am very curious about how the list of BSA Officers was obtained. Best guess is that either someone was very dedicated and amassed the list from hours of googling, leaked from the inside from a larger FI, or there is simply some online resource that tracks that info that I am unaware of. However, while no bank is perfect, I doubt any FI would allow such a thing to exist.
More likely some conference company got breached and lost the list of attendees.
Can confirm it’s not just Credit Unions. Our BSA Officers received that email. (Bank / FDIC) We suspect the contact information was taken from the FinCEN 314(b) contact list.
I assume these are the people behind “know your customer.” Though well intentioned, the conversations these people start to “know you” are so transparent.
Gmx is a well known source of spam,and not a likely address for US bank email to originate.
Is this actually a PDF file, or an executable file with a PDF icon? Hard to tell from the screenshot. And if it is a PDF, what is the payload? Does it contain a link to a malicious site?
From the story:
“The PDF itself comes back clean via a scan at Virustotal.com, but the body of the PDF includes a link to a malicious site.”
What about a printed attendee list from an anti-money laundering conference or similar event? I’ve seen financial services events where that’s included, either online or printed. Someone could have picked the list up, received it from an insider, or dumpster dived at the location where it was held.
We received the email as well at our institution and we are not a Credit Union. We also believe that data has left FinCen and its most likely the 314(b) contact list. Bad news for FinCen. Only 314(b) members are being targeted.
I’m in agreement with Andrew. I received this email and I am not the BSA officer. Although I am on the FinCEN 314(b) contact list.
Not associated with any financial institution myself.
1. “Bank Secrecy Act (BSA) contacts responsible for reporting suspicious financial transactions that may be associated with money laundering. U.S. credit unions are required to register these BSA officers with the NCUA.” Rhetorical: Where’s the NCUA report going, that may be leaking data? FinCEN?
2. Seems NCUA is headquarters for additional orgs. Physically segmented networks?
https://en.wikipedia.org/wiki/Credit_Union_National_Association#Employees_and_locations
One of our clients got just such an email.
I’ve trained all the staff to pass suspicious email over to us for review and never “just open” attachments.
This one client contacted their contact at the Treasury Department and they noted they’ve received several complaints about the same thing. We had it flagged as spam with our secure mail processor and they confirmed within 2 hours the found several other like spam messages.
As stated above, not only Credit Unions were affected. I received the phishing e-mail. I am a BSA Officer at a community bank and I am a 314(b) registered participant.
The Source needs to learn how to use google, as the information is freely available via Linkedin. Just jump to around page 10 and you’re no longer looking at BSO jobs, you’re looking at resumes. From there, it’s not hard to figure out email addresses.
https://www.google.com/search?q=%22bsa+officer%22+site:linkedin.com
I think that’s possible a search of LinkedIn could be a source in some cases, but many credit unions have only 1 BSA officer while the NCUA would require 2 contacts. So, it wouldn’t explain how both contacts at a single credit union would get the email when only one would list BSA officer on their resume. Secondary contacts are frequently upper management that don’t fill any BSA officer duties other than supplying a contact.
Though, with the comments it looks like it’s targeted 314b contacts rather than BSA officers. Credit unions usually have the BSA officer fill that role, which is why they received the email. Larger financial institutions that would have these roles separated were the key to narrowing this down.
cool story bro, but I know people that it was sent to that are retiring soon, have no resume out there for over 10 years, and no linkedin account.
It’s good to know banks are affected to. I saw some chatter about these emails only from credit unions myself, but nothing from the banking forums. Even though the emails are pretty obvious, I’m more worried about where the contact list came from. These contacts aren’t readily available publicly.
It’s about time that the internet protocols were beefed up to further minimize email scams/spoofs.
I really like this suggestion: “Never click on links embedded in emails”
Do they realize that 90% of legitimate emails (including the mailing list notification from Brian Krebs that we used to get to this article) contain a clickable link?
Just because an email has a link, doesn’t mean you need to use it. I have bookmarks for most of the sites that I regularly visit, including this one. I never use the embedded link, ever.
While an email return address can be spoofed, it’s a huge red flag and alarm bells when a link is included in a email, or attachment, that is not from a familiar return address and from someone unknown to the receiver. This phishing email rang both bells
Dennis, you must not have read the rest of the sentence in that recommendation:
“from unknown or suspect fraudulent email accounts.”
Yeah… well… Not exactly related to this story, I have an open dispute with AmEx about a probably-innocent duplicate charge. I received email that looks like it really came from AmEx and says, “An important message is ready for you to view in the American Express Secure Message Center. To protect your privacy, please follow this secure link to log into your account and view this message. [link redacted]
Needless to say, I haven’t clicked any links, and there is no “Message Center” link when I log in to my AmEx account. It’s impossible to talk to a human being about this.
If it’s a fake, it’s a good one. If it’s real, they’re teaching their customers bad habits.
The Amex secure message center was robed in 2014. The email you got is fake.
Call them. The number is on your bill and the back of your Amex card.
*removed
From a friend at the National Credit Union – Information Sharing and Analysis Organization (NCU-ISAO): they saw this last week and got some partner reports that led them to send out an alert.
How much more terrifying would scammers be if they didn’t make grammar mistakes?
What is equally terrifying is the number of people in positions of responsibility who don’t recognize poor grammar when they see it 😉
@gmx.de – Seems legit
There are some 3rd party companies that collect this information too. Accuity is one. And I doubt NCUA was the source if banks are getting the emails also.
@vb: yup
@Dennis: legitimate email links often have tracking preloads, which you can see by hovering over the link in most mail clients.
I am interested in sandboxing this email and determine as much information as possible. If any affected or not have an original email that I can look and inspect would be appreciated by sending it to the email jark18@lavabit.com
Thank you.
In addition:
“A BSA officer at a different credit union said their IT department had traced the source of the message they received back to Ukraine.”
I’m not asking too much by asking to see which Ukraine network, “email header”, and body of message links. Further “international diplomacy” could be extended with that information.
My direct view of many instances of spam from Ukraine are that their message body links have an abundance of assocation with .RU networks and registrars–tracking back further.
NOTE that this article is incorrect. It states that the USA PATRIOT Act requires FI to appoint “at least two” – this is completely untrue. You are only required to appoint at least ONE person for 314(a) purposes and participation in 314(b) information sharing (which is what this article refers to) is only voluntary and if you do choose to participate, then you only have to list one point of contact.
Nonetheless this is very concerning – but please do your research before posting articles.
Yeah, I think that part of the article regarding two required contacts might have stemmed from the NCUA’s CALL Report Profile instructions that’s linked in the article (called mandatory BSA reporting instructions above). The instructions require a primary and secondary Patriot Act contact, while third and forth contacts are optional.
Correct. It came from the CALL report profile published by the NCUA
NCUA CALL Report Profile Instructions: https://www.ncua.gov/files/publications/regulations/credit-union-profile-form-instructions-4501A-9302017.pdf
Mandatory Roles
The Mandatory Role page identifies seven mandatory roles that each credit union must have assigned to a contact. These include:
• Call Report Contact
• Profile Information Contact
• Primary Patriot Act Contact
• Secondary Patriot Act Contact
• Third Patriot Act Contact (Optional)
• Fourth Patriot Act Contact (Optional)
• Primary Emergency Contact
• Secondary Emergency Contact
• Information Security Contact
NCUA will not release this information to the public.
Mandatory Role Information
Provide contact information for the mandatory roles. An individual with a mandatory role may also be identified on the Contacts, pages 13 – 18. However, these contacts must also be identified on the Mandatory Role page:
Patriot Act Contacts – Provide an email address where information can be sent directly to the primary and secondary contact persons. The third and fourth Patriot Act contacts are optional. In the event the credit union has one e-mail address, this information should be treated as confidential and provided only to credit union individuals responsible for Bank Secrecy Act compliance. Credit unions may provide personal e-mail addresses if the credit union does not have an organizational e-mail address. Updates to the Patriot Act 314(a) point of contact are provided to FinCEN on a bi-weekly basis. Depending upon when the updates were made, it could take up to three weeks for the changes to take effect. If you have any questions, contact your NCUA district examiner or respective State Supervisory Authority.
Banker, please see my comment in response to yours. And thanks for not being a jerk about it.
Can anyone confirm if the subject or sending domain changes? I’ve run some message traces for a couple of financial institutions and don’t see any matches or anything similar but was wondering if the details changed. The BSA’s don’t recall getting any suspicious emails around that date and a search doesn’t flag anything obvious.
The PDF attachment in the email contains a link to a likely malicious URL but the file itself does not appear to have any payload.
In the one our FI received did not have a malicious payload. Just a phishing link.
Another give-away, people in the credit union industry do not use the word “client”. “Member” is part of our DNA. As soon as I hear the slip I know that individual is not one of us.
I did not receive the message and I am the BSA officer.
I hope nobody fell for that considering the terrible attempt to sound English – replete with spelling mistakes and pathetic grammar.
Your post-publication updating using evidence identified and enhanced after publication to tighten your analysis gives me hope. It’s an established fact that the majority of readership will only be cognizant of what is described in the first publication of a story. When a journalist persists despite this knowledge and seeks to improve later readers understanding shows the resiliency of the journalistic process. Information evolves around facts and the press’ job is to illuminate that for their readership. This article is an example of that. Thank you for your efforts, they can help us all understand why reality-based journalism is important and why rejecting ‘enemy of the people’ labels is important.