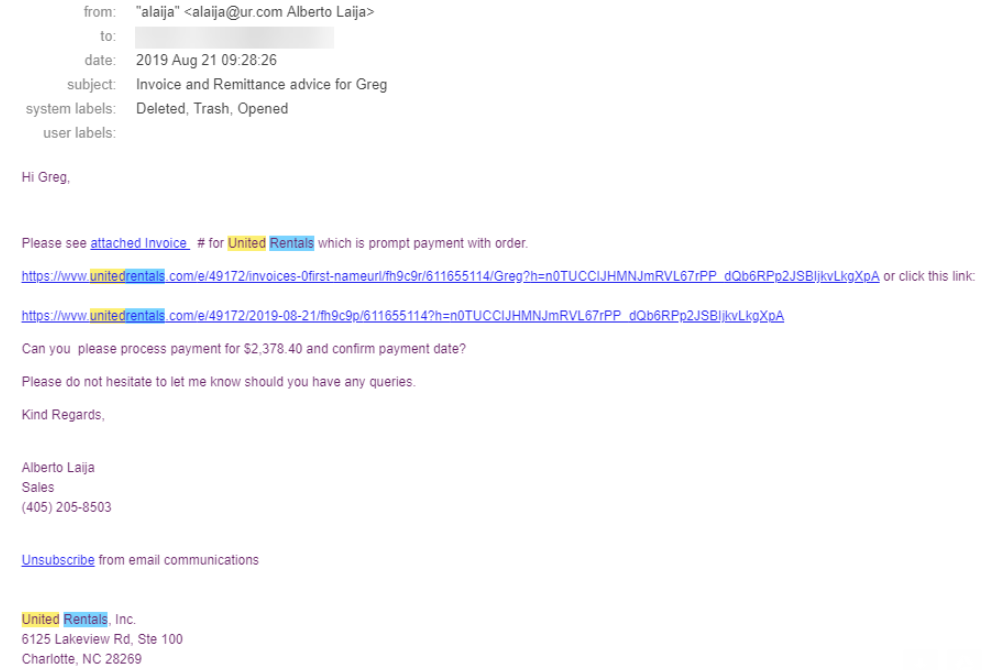
Many companies are now outsourcing their marketing efforts to cloud-based Customer Relationship Management (CRM) providers. But when accounts at those CRM providers get hacked or phished, the results can be damaging for both the client’s brand and their customers. Here’s a look at a recent CRM-based phishing campaign that targeted customers of Fortune 500 construction equipment vendor United Rentals.
Stamford, Ct.-based United Rentals [NYSE:URI] is the world’s largest equipment rental company, with some 18,000 employees and earnings of approximately $4 billion in 2018. On August 21, multiple United Rental customers reported receiving invoice emails with booby-trapped links that led to a malware download for anyone who clicked.
While phony invoices are a common malware lure, this particular campaign sent users to a page on United Rentals’ own Web site (unitedrentals.com).
In a notice to customers, the company said the unauthorized messages were not sent by United Rentals. One source who had at least two employees fall for the scheme forwarded KrebsOnSecurity a response from UR’s privacy division, which blamed the incident on a third-party advertising partner.
“Based on current knowledge, we believe that an unauthorized party gained access to a vendor platform United Rentals uses in connection with designing and executing email campaigns,” the response read.
“The unauthorized party was able to send a phishing email that appears to be from United Rentals through this platform,” the reply continued. “The phishing email contained links to a purported invoice that, if clicked on, could deliver malware to the recipient’s system. While our investigation is continuing, we currently have no reason to believe that there was unauthorized access to the United Rentals systems used by customers, or to any internal United Rentals systems.”
United Rentals told KrebsOnSecurity that its investigation so far reveals no compromise of its internal systems.
“At this point, we believe this to be an email phishing incident in which an unauthorized third party used a third-party system to generate an email campaign to deliver what we believe to be a banking trojan,” said Dan Higgins, UR’s chief information officer.
United Rentals would not name the third party marketing firm thought to be involved, but passive DNS lookups on the UR subdomain referenced in the phishing email (used by UL for marketing since 2014 and visible in the screenshot above as “wVw.unitedrentals.com”) points to Pardot, an email marketing division of cloud CRM giant Salesforce.
Companies that use cloud-based CRMs sometimes will dedicate a domain or subdomain they own specifically for use by their CRM provider, allowing the CRM to send emails that appear to come directly from the client’s own domains. However, in such setups the content that gets promoted through the client’s domain is actually hosted on the cloud CRM provider’s systems.
Salesforce told KrebsOnSecurity that this was not a compromise of Pardot, but of a Pardot customer account that was not using multi-factor authentication.
“UR uses a third party marketing agency that utilizes the Pardot platform,” said Salesforce spokesman Bradford Burns. “The third party marketing agency is who was compromised, not a Pardot employee.”
This attack comes on the heels of another targeted phishing campaign leveraging Pardot that was documented earlier this month by Netskope, a cloud security firm. Netskope’s Ashwin Vamshi said users of cloud CRM platforms have a high level of trust in the software because they view the data and associated links as internal, even though they are hosted in the cloud.
“A large number of enterprises provide their vendors and partners access to their CRM for uploading documents such as invoices, purchase orders, etc. (and often these happen as automated workflows),” Vamshi wrote. “The enterprise has no control over the vendor or partner device and, more importantly, over the files being uploaded from them. In many cases, vendor- or partner-uploaded files carry with them a high level of implicit trust.”
Cybercriminals increasingly are targeting cloud CRM providers because compromised accounts on these systems can be leveraged to conduct extremely targeted and convincing phishing attacks. According to the most recent stats (PDF) from the Anti-Phishing Working Group, software-as-a-service providers (including CRM and Webmail providers) were the most-targeted industry sector in the first quarter of 2019, accounting for 36 percent of all phishing attacks.
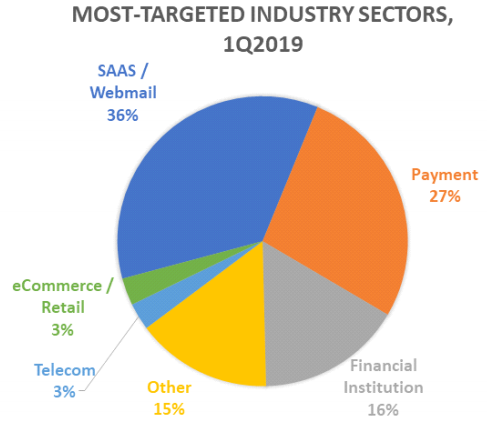
Image: APWG
Update, 2:55 p.m. ET: Added comments and responses from Salesforce.




This article doesn’t even make sense. Salesforce doesn’t just “have access” to Pardot accounts. The end-client, in this case UR, would have to GIVE them access to their Pardot account, and that would be clearly visible in the audit trail in Pardot.
Moreover, Pardot isn’t an “outsourced” service. It’s a marketing automation tool that end-users use for their own marketing purposes. Whether UR outsources their marketing to a third-party firm and THAT third-party then uses Pardot is an entirely difference scenario than the one described in this article.
Article makes perfect sense.
Pardot is email marketing service owned by Sales Force. All on needs to do is to get hold of UR’s dedicated domain used for email marketing.
What are tie security controls in an email marketing service? Practically none.
Except the emails could *easily* have been generated as a result of UR not having appropriate user access controls in place for Pardot. If someone compromised one of UR’s Pardot accounts, the emails, landing page, etc. could have been sent directly through the end-user’s (UR’s) account without Salesforce ever having been compromised. It’s a bit of a leap to say that Salesforce/Pardot was compromised here.
Stephanie, it is a leap that United Rentals seems to be making, and it’s a perfectly rational one at that. For the record, Salesforce initially said they would get back to me, but despite repeated requests to respond to this open question, they have chosen silence.
Cloud providers need to stop accommodative security which doesn’t follow standards.
Enterprises need to really get people who has in-depth knowledge of security. All encryption for confidentiality, integrity and non-repudiation is not the same, all key management is not the same and all TLS connections does not provide the level of security needed for data-in-motion.
One more thing, organizations needs stop listening to application developers on security. Calling an secure API is not real security. I have worked and still working in the cyber security space and have not seen a single developer with in-depth app security knowledge.
Great article on the subject of “Phishing” and “social engineering”
Oh, this is so true. The company I work for uses this cloud based accounting software that allows login passwords with just 4 letters. Also stores them in plaintext (they can email you the password in clear text as “forgot my password” feature.) Obviously has no 2FA and I just discovered today that small and capital letters in login passwords don’t matter.
When I tried to address it with high ups in the company I was told that it’s ok, as otherwise employees will have a hard time remembering passwords. I also tried to contact that Cloud based company directly and it turns out their strategy to fixing security holes is to try to intimidate whoever brings it up to their attention. After my call, the owner of that company contacted my boss and tried to fire me, then threatened them with a lawsuit. So yeah, I’m sure this is not just a single company that does this kinda stuff ;(
Keep a diary of notes on these kinds of communications; keep the notes in a matter of fact tone, so that it doesn’t read as prejudicial. That way, if you are fired for incorrect causes, you have a good defense in a court case. If permitted, it might even be wise to print screen shots of email communications relevant to the facts. A good security operator such as yourself relies on a good reputation – don’t let anyone compromise that. Good luck, and God speed!
That’s a very scary story, Dennis. You’ve done the right thing to try to bring this to the attention of the companies.
I suggest you keep meticulous records of your interactions for possible use in lawsuits; particularly if the company you work in is compromised because of their non-existent security policies.
In addition to contemporaneous notes, depending on your state of residence, it is legal to make one party consent (i.e. from you) recordings of conversations. It may seem dishonest, but otherwise it’s just your word against someone else.
Don’t do it if you haven’t researched the law, because you may be committing a crime yourself.
IIRC, text transcriptions are legal everywhere; however I’m not sure if you have to declare it was from a recording without someone’s consent. I seem to remember that even police cases were legal that way. As long as the device is on your person, or within arm’s length, it may be permitted. Phone conversational recordings with a intermittent beep are considered consent to record in most states as well, but that would be strange in a work environment, unless it is already an administrative oversight practice.
This is the kind of thing where giving @Brian enough information and letting him do the reporting is probably the safest way for you to help the industry.
Direct whistleblowing isn’t safe. Reporters otoh can get results.
If anyone is particularly curious about the malware used, it was a very new Trickbot variant. At the time of submission, it was picked up by only 10 AV engines on VT.
SHA1: 2da82b8e0ca7b4c82ff651cef93cd8fa402304c7
If we are to assume that the CRM was compromised, the attacker used two valid UR employee identities. The question remains then, would replies be filtered back through the CRM prior to hitting the actual users inbox, enabling the attacker to redirect replies without them reaching the reply-to user? The from and reply-to didn’t match, but, the addresses were both valid UR sales employees.
Now upwards of 50 show positive
https://www.virustotal.com/gui/file/68a40d5a27ad560bd664d2002dbb848535186d87dca675b51b13a2c8a3c58b9c/detection
50+ positive now on VT
A client of mine got these e-mails, seven employees total. All had subject lines personalized with their first names.
What is the significance of the “wVw” in “wVw.unitedrentals.com” in the emailed link? Are there any legitimate URLs that contain “wVw” instead of “www” ? Thanks.
When I initially saw that, I assumed it was because someone had hijacked the company’s DNS and added a cleverly crafted subdomain. But it turns out UR created that themselves several years ago for the purposes of marketing.
That’s so shady. Wow.
Seems as if they tricked their own employees into thinking this subdomain was http://www.unitedrentals.com just for marketing purposes!
What a smart idea.
If the services are secured with device independent authentication then the users accounts can’t be can’t be compromised by credential stealing malware. Its really tiresome to continue to hear about these disasters when there are easily implemented solutions to put an end to them.
I don’t understand Salesforce here. Silence??
Me thinks, at best, Brian might have stirred the pot with Salesforce. Could they have been hoping to make their Pardot customers aware of this quietly. I guess it’s entirely possible Salesforce didn’t even know of this previously, but I don’t believe that.
Either way, this does not reflect well on Salesforce.com, remaining silent.
Salesforce is the “whale” in the CRM industry with tens of thousands of clients ;-( How many of those are on/using Pardot??
They responded after my story went up. I’ve included their comments as an update in the middle of the story.
How should we advise others to keep from falling for the ploy, or even myself for that matter? The email looks legit, so what’s the takeaway? Never click on a link in an email you didn’t ask for? Instead, always log in to your UR account to see what invoices are in fact due. Let’s not forget our pedagogical role. Thanks for your advise and help.
Ask everyone to set up 2FA [1].
Where possible, tell businesses that aren’t using/offering 2FA that you intend to take your business to another vendor which does (and then do so).
I think Brian’s approach is to browse the web w/ a VM or readonly computer (i.e. a computer w/ roughly no hard drive and just a read-only CD/DVD/USB). (He wrote about this a while ago.)
Basically, to the extent that you can air-gap your accounting/banking from your browsing/email activities, you want to.
What does this look like in practice?
Ideally:
2 disconnected networks
— one for social activities (email)
— one for expenses related activities (procurement, accounting, banking)
Computers on the two networks shouldn’t talk to each-other.
If you receive an email from someone, e.g. your boss instructing you to do something, don’t rely on the email. Don’t reply to the email. Don’t use the phone number listed in the email.
General preference is to call your boss at the number you know your boss has and confirm w/ them directly. Short of that, email your boss using the email address you have in your contacts (be careful not to rely on “collected address book(s)” which are easily poisoned) asking for confirmation, include the Date/Summary/Reference Number/Amount/Destination (don’t forward the email, assume that the email is booby-trapped). — There was a report recently where someone used a voice synthesizer to impersonate a CEO’s voice for a phone call to confirm a transaction order. — This is amongst the reasons you don’t want to rely on the phone number listed in an email — if the information in the email was controlled by a fraudster, it can be directed to them and you’re at their mercy.
Note: I’m using “boss” here, but that’s a stand-in for “person directing you to do something that involves money”.
If someone includes a link you didn’t ask for, yes, don’t click it, reach out the same way, as if clicking it might have financial consequences (because it might!).
Personally, I’d also encourage the use of either GSuite or O365 as I’m hopeful that their phishing detection will be better than most other providers given that they have a large corpus.
For the really paranoid, I’d encourage people to consider Google Fi [2] and Google Advanced Protection [3] for their mobile phone service — hopefully that pair should protect your phone number from being SIM-swapped. I don’t have Fi, but I use Google Voice [4] (which should be similarly immune to SIM-swapping) and am dipping my toes into Advanced Protection. — If you’re dealing w/ large dollar amounts (or a significant portion of your entities funds even if they aren’t lage dollar amounts), then you should seriously consider this even if it feels like a burden.
Getting Google Voice working isn’t particularly painful, you can either sign up for a new free US number, or pay a small fee ($5?) to port your existing number. And then you set up Hangouts* (Google is trying to replace Hangouts, although they haven’t explained how this will work for Google Voice users) on your phone(s) / device(s) to receive calls for the number (the calls are billed as Data — if you have an old plan you could use the Google Voice app instead which makes them into voice calls, but Google is really trying to discontinue that…).
[1] https://twofactorauth.org
[2] https://fi.google.com/about/
[3] https://landing.google.com/advancedprotection/
[4] https://voice.google.com/
I still have a grudge against the U.S. Dept of Defense and Dept of Commerce for their policy back around the 1990s of trying to forbid encryption by the general public. If emails from United Rentals had been encrypted, and decryptable with a trustworthy public key, this could all have been stopped.
Agreed, trustworthy key distribution isn’t something that just happens, but done right it gives us the basis for an internet that can be used for serious business.
You are too late or too early to be holding a grudge on encryption use by the general public for email and other messaging. There are no such restrictions now, but that could change.
Read:
https://en.wikipedia.org/wiki/Pretty_Good_Privacy
https://en.wikipedia.org/wiki/S/MIME
https://www.checktls.com/
Then WhatsApp, Signal, Telegram, KiK, Confide, and iMessage.
” trustworthy key distribution”
Keep in mind that the Salesforce et al. would want to keep their system easy to use. That will come down to simple access to the system to send customer emails. Remote control of those systems will then give the bad guys a way to send proper trusted and encrypted emails to the recipients.
Thanks Brian.
When I started reading the article and it said CRM, I already had guessed, and I was right.
SF is not a well thought out CRM platform. In many different ways. I cringe when I sit down in front of it daily.
I’ve used much better CRM products in the past, that work better, less clicks, and uses much less resources, in addition to the exorbitant licensing costs for the company.
Its so sad when IT depts don’t do their due diligence when selecting application platforms that affect an entire enterprise.
Another case in point. EPIC Systems EMR.
Stephanie sounds like she has a vested interest in SF.
“…attached invoice for United Rentals which is prompt payment with order”??
The importance of reading every word of an unsolicited email for fraud clues can’t be overstated.
The idea here is that unitedrentals set up their own malicious subdomain which tricks you into thinking you’re getting emails from a “www.” unitedrentals.com when in reality the subdomain is “wVw.”.
A legitimate email from your domain name is generally safe, and picked up by spam filters.
If it is a subdomain, verified as external but clearly stated as, say, pardot.unitedrentals.com, it wouldn’t be as readily clicked-on.
They just hide the fact these emails are external from their own users, and that’s why this whole situation happened. Disgraceful.
Or just have a simple policy to bounce messages from anyone outside an immediate workgroup that contains links or attachments, with an auto-response explaining why.
And limit every user’s ability to do harm, whether by accident or malfeasance.
There is really no reason why employees should be put in a position of having to be the email filter. We have tools to protect them and reduce the company’s exposure if they make a mistake.
Brian, as far as the malware getting run on the system, the story said only:
“…led to a malware download”
“…if clicked on, could deliver malware”
To me, it’s very important to know the mechanics of malware getting onto the system, and not just the psychological and business context. Did the person click on an infected .doc, .pdf, run a .exe, etc.? It sounds unlikely that a URL was exploiting a browser hole.
Do you have any info on that?
The malware was served off of a redirect from the ‘wvw’ UR site. The downloader dropped in the form of an .LNK which ran VBscript to retrieve the actual malware, in this instance titled “рВяАсмыцЛщреп.exe”, MD5: AD5296B280E8F522A8A897C96BAB0E1D.
This attack required a fair amount of user intervention, and especially should have been suspicious to native English speakers given the Cyrillic alphabet used in the filename.
Correction, the MD5 is: 6facb0eb24830d2db619f525e84bc97
The MD5 I initially supplied is for Explorer.exe…
I imagine the hash is not relevant though as I’m certain the malware changes.
Thanks TonyN.
Presumably the victim actually clicked-on/ran the .lnk shortcut, after saving it.
Happens everyday …..
Funny I was just writing up requirements for third party email senders last night and started worrying about those platforms being hack and what to do about it.
But before we worry about that, isn’t email authentication (SPF/DKIM/DMARC) the first line of defense in email phishing? The beauty of this phishing attack is an email response is not need and the link to the malware download is on the United Rental own website. So, if somebody had unauthorized access into the web site this email could have been a simple domain spoofing email and worked.
Is there evidence that this email was sent from the Pardot servers? Do you have access to the email headers?
A couple things to note. First, the email domain in the display field is ‘ur.com’ not ‘unitedrental.com’. Although both domains have Pardot in their SPFs. Second, neither domain has a DMARC record, so I am not sure how this email gets authenticated. Third, the from display field (“alaija” ) does not look like a well-formed email address, since the ‘Alberto Laija’ is between the . Although this could be an email client artifact it just does not look normal – which is what we teach are users.
If this was a simple domain spoofed email without a DMARC I am not sure how it would have been flagged. Even a DMARC p= none would have given several email receivers enough information to at least flagged it as suspicious.
Moral of the story – enable email authentication on ALL your domains with SPF/DKIM/DMARC records. Even domains that do not send emails should have SFP and DMARC records so they can not be used spoof you company.