Last week, KrebsOnSecurity reported to health insurance provider Blue Shield of California that its Web site was flagged by multiple security products as serving malicious content. Blue Shield quickly removed the unauthorized code. An investigation determined it was injected by a browser extension installed on the computer of a Blue Shield employee who’d edited the Web site in the past month.
The incident is a reminder that browser extensions — however useful or fun they may seem when you install them — typically have a great deal of power and can effectively read and/or write all data in your browsing sessions. And as we’ll see, it’s not uncommon for extension makers to sell or lease their user base to shady advertising firms, or in some cases abandon them to outright cybercriminals.

The health insurance site was compromised after an employee at the company edited content on the site while using a Web browser equipped with a once-benign but now-compromised extension which quietly injected code into the page.
The extension in question was Page Ruler, a Chrome addition with some 400,000 downloads. Page Ruler lets users measure the inch/pixel width of images and other objects on a Web page. But the extension was sold by the original developer a few years back, and for some reason it’s still available from the Google Chrome store despite multiple recent reports from people blaming it for spreading malicious code.
How did a browser extension lead to a malicious link being added to the health insurance company Web site? This compromised extension tries to determine if the person using it is typing content into specific Web forms, such as a blog post editing system like WordPress or Joomla.
In that case, the extension silently adds a request for a javascript link to the end of whatever the user types and saves on the page. When that altered HTML content is saved and published to the Web, the hidden javascript code causes a visitor’s browser to display ads under certain conditions.
Who exactly gets paid when those ads are shown or clicked is not clear, but there are a few clues about who’s facilitating this. The malicious link that set off antivirus alarm bells when people tried to visit Blue Shield California downloaded javascript content from a domain called linkojager[.]org.
The file it attempted to download — 212b3d4039ab5319ec.js — appears to be named after an affiliate identification number designating a specific account that should get credited for serving advertisements. A simple Internet search shows this same javascript code is present on hundreds of other Web sites, no doubt inadvertently published by site owners who happened to be editing their sites with this Page Ruler extension installed.
If we download a copy of that javascript file and view it in a text editor, we can see the following message toward the end of the file:
[NAME OF EXTENSION HERE]’s development is supported by advertisements that are added to some of the websites you visit. During the development of this extension, I’ve put in thousands of hours adding features, fixing bugs and making things better, not mentioning the support of all the users who ask for help.
Ads support most of the internet we all use and love; without them, the internet we have today would simply not exist. Similarly, without revenue, this extension (and the upcoming new ones) would not be possible.
You can disable these ads now or later in the settings page. You can also minimize the ads appearance by clicking on partial support button. Both of these options are available by clicking \’x\’ button in the corner of each ad. In both cases, your choice will remain in effect unless you reinstall or reset the extension.
This appears to be boilerplate text used by one or more affiliate programs that pay developers to add a few lines of code to their extensions. The opt-out feature referenced in the text above doesn’t actually work because it points to a domain that no longer resolves — thisadsfor[.]us. But that domain is still useful for getting a better idea of what we’re dealing with here.
Registration records maintained by DomainTools [an advertiser on this site] say it was originally registered to someone using the email address frankomedison1020@gmail.com. A reverse WHOIS search on that unusual name turns up several other interesting domains, including icontent[.]us.
icontent[.]us is currently not resolving either, but a cached version of it at Archive.org shows it once belonged to an advertising network called Metrext, which marketed itself as an analytics platform that let extension makers track users in real time.
“Three lines into your product and it’s in live,” iContent enthused. “High revenue per user.”
Another domain tied to Frank Medison is cdnpps[.]us, which currently redirects to the domain “monetizus[.]com.” Like its competitors, Monetizus’ site is full of grammar and spelling errors: “Use Monetizus Solutions to bring an extra value to your toolbars, addons and extensions, without loosing an audience,” the company says in a banner at the top of its site.
Contacted by KrebsOnSecurity, Page Ruler’s original developer Peter Newnham confirmed he sold his extension to MonetizUs in 2017.
“They didn’t say what they were going to do with it but I assumed they were going to try to monetize it somehow, probably with the scripts their website mentions,” Newnham said.
“I could have probably made a lot more running ad code myself but I didn’t want the hassle of managing all of that and Google seemed to be making noises at the time about cracking down on that kind of behaviour so the one off payment suited me fine,” Newnham said. “Especially as I hadn’t updated the extension for about 3 years and work and family life meant I was unlikely to do anything with it in the future as well.”
Monetizus did not respond to requests for comment.
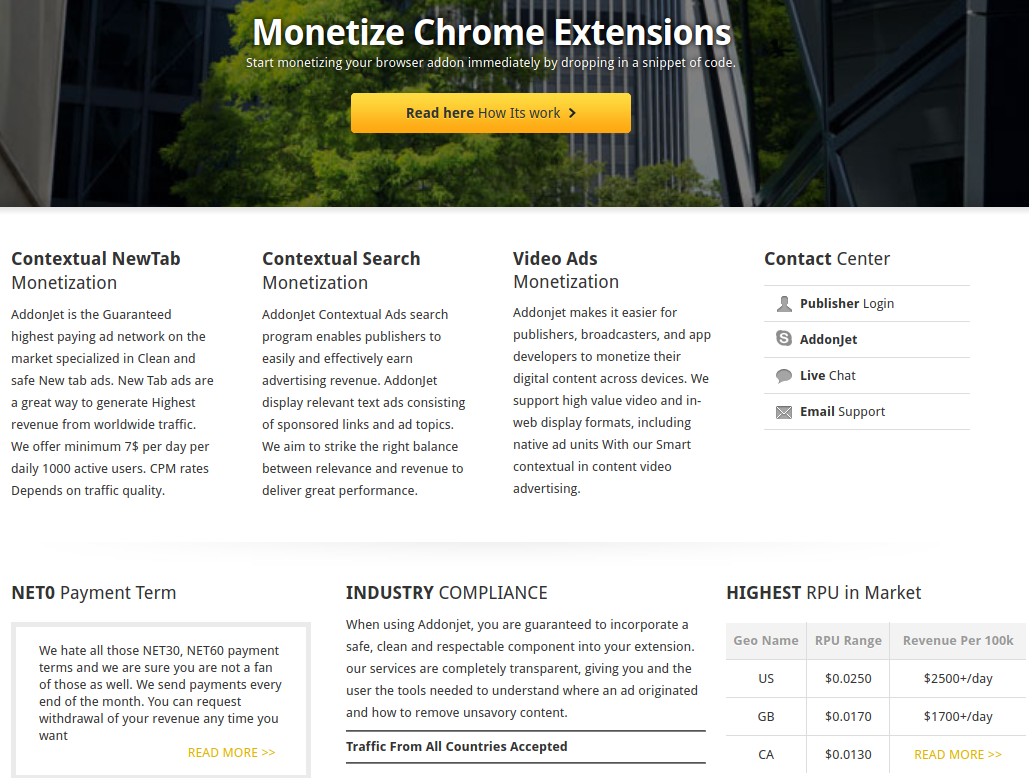
Newnham declined to say how much he was paid for surrendering his extension. But it’s not difficult to see why developers might sell or lease their creation to a marketing company: Many of these entities offer the promise of a hefty payday for extensions with decent followings. For example, one competing extension monetization platform called AddonJet claims it can offer revenues of up to $2,500 per day for every 100,000 user in the United States (see screenshot below).
I hope it’s obvious by this point, but readers should be extremely cautious about installing extensions — sticking mainly to those that are actively supported and respond to user concerns. Personally, I do not make much use of browser extensions. In almost every case I’ve considered installing one I’ve been sufficiently spooked by the permissions requested that I ultimately decided it wasn’t worth the risk.
If you’re the type of person who uses multiple extensions, it may be wise to adopt a risk-based approach going forward. Given the high stakes that typically come with installing an extension, consider carefully whether having the extension is truly worth it. This applies equally to plug-ins designed for Web site content management systems like WordPress and Joomla.
Do not agree to update an extension if it suddenly requests more permissions than a previous version. This should be a giant red flag that something is not right. If this happens with an extension you trust, you’d be well advised to remove it entirely.
Also, never download and install an extension just because some Web site says you need it to view some type of content. Doing so is almost always a high-risk proposition. Here, Rule #1 from KrebsOnSecurity’s Three Rules of Online Safety comes into play: “If you didn’t go looking for it, don’t install it.” Finally, in the event you do wish to install something, make sure you’re getting it directly from the entity that produced the software.
Google Chrome users can see any extensions they have installed by clicking the three dots to the right of the address bar, selecting “More tools” in the resulting drop-down menu, then “Extensions.” In Firefox, click the three horizontal bars next to the address bar and select “Add-ons,” then click the “Extensions” link on the resulting page to view any installed extensions.




Kinda makes all software un-trustable if it can be repurposed like that by criminals.
The only add-on I use is an add blocker. I consider goog’s Chrome to be spyware and will never use it. One look up about how their spell checker works and you may not either.
Think your ad blocker blocks that too?
https://browserleaks.com/webrtc
https://github.com/gorhill/uBlock/wiki/Prevent-WebRTC-from-leaking-local-IP-address
I’m at a loss as to how that extension is even useful. Images on modern web pages are scaled on the fly or just use htlm5 features to adjust automatically. (Object-fit). In any event, installing an extension triggers a warning. I have never got past that stage.
Is there a 3rd party service to check the reputation and code for browser extensions?
As in, submit the extension id in a web form, and it returns a risk score.
We have lots of options for traditionally installed programs…. but browser add-ons still seem to be the wild west.
Even scarier, non admin users can install whatever, forcing enterprise admins to completely take over handling of extensions. There isn’t a good way to manage since there isn’t a trusted source to validate each one.
There’s got to be a better way.
I would consider a service like CRXCavator
but it doesn’t see much wrong with the extension that is the topic of this article…. emliamioobfffbgcfdchabfibonehkme/1.0.4
You can whitelist extensions via GPO, that way anything that is not on that list isn’t allowed, however, getting management buy off on it is the issue. https://support.google.com/chrome/a/answer/7532015?hl=en Also, bad guys have taken to altering already existing extensions. https://www.zdnet.com/article/google-chrome-under-attack-have-you-used-one-of-these-hijacked-extensions/
That’s what I mean…. if we had a trusted source of safe extensions, that re-validate when an app is updated, we could manage with GPO (that part is easy and known for years).
Anti-malware solutions look at signatures and behavior, and run on the endpoint… but nothing really equivalent to browser security/privacy that would catch these types of malicious add-0ns. It would have to exploit the browser itself before an anti-malware agent or HIPS would catch it. But in reality, these bad extensions don’t break out of the browser, so its code is never evaluated, and its behavior is trusted since the permissions were accepted by the user.
CRXcavator seems to be the best solution thus far… but not sure why this ‘page ruler’ app has not raised any significant flags.
I suppose this begs the question, with extensions such as uBlock Origin, NoScript, etc., are script blocking extensions a possible solution to this very problem?
Heh, you just gotta hope the blocking add-on isn’t itself malicious, right ? Could be running a crypto-miner in the background, for all we know !
uBlock Origin is open source so you can just check the code and build it yourself if you’re paranoid.
Additionally, on Firefox the add-on code must be unobfuscated anyway so you can check it manually for any extension regardless.
I use different browsers for different things.
Chrome Canary for online banking.
Brave for general browsing (with ad blocking on).
Chrome for test / development.
Firefox for any potentially risky stuff.
Clear apps, cookies, history frequently.
Concurring / endorsing this approach, and adding another browser to the menu: Vivaldi.
I distribute my usage amongst my installed browsers differently, but IMHO the underlying approach — different browsers for different activities — has merit.
I’d say a conditioned, “No”, and here’s why:
UBlock Origin does a great job protecting me on most sites. But, would likely failed on the BCBS site. Many sites like BCBS that “take security seriously”, also make them unusable when you also use great plugins designed to protect us. So, we must disable them, or the site just won’t work.
PW managers – Want to log in securely on a high value site like banking? Good luck, because often they are disabled from working, lest other bots can log in for you. So we must either use very weak passwords so they can be accurately typed before three mistakes, and you are locked out. Or, copy and paste from a plain text file somewhere, (provided the page didn’t disable paste).
I would suggest you copy and paste from your secure encrypted password manager instead of a plaintext file.
That has been my experience as well. However with the MalwareBytes Anti-malware extension, I haven’t had any problems since. I do have to allow ads on KOS and other sites I like though, but it still is supposed to continue blocking malware even after that allowance. I don’t know if you can install it without owning a license for MBAM Premium or not.
I prefer to copy/paste from a password manager that automatically encrypts its data when the app is closed. (For those websites that disable pasting there is the “StopTheMadness” extension for most browsers and it’s available in the Apple and Chrome app stores. The Mac-only extension restores a variety of commonly-disabled functions while adding some unique anti-tracking features.)
Instead of using a weak password you can memorize a randomly generated 3 or 4-word pass phrase that is stronger than passwords using special characters.
I’ve had bad , past experiences with Firefox extensions.
I wouldn’t install a huge amount of extensions. on your browser(s) at one time. Very bad idea !
Noscript. Only add-on you need
Tautology. No need for further effort, all is known.
When mozilla broke NoScript, I was very close to being an ex-firefox user. I have swapped emails with the developer and essentially went dark while he re-jiggered things. NoScript is one of the best features of firefox.
On the Firefox Add-Ins page mentioned in the post, I see a little yellow trophy badge next to some of the extensions I am using. Mousing over it displays a tooltip which reads “Firefox only recommends extensions that meet our standards for security and performance.”
So those extensions are safe…. right? RIGHT??
Another problem are scam extensions, pretending to be popular extensions. I just tried the new Edge browser on Windows 10. First thing I did was to look for uBlock Origin. Searching in Microsoft’s extension store turned up an extension with that name, but it was NOT the real thing.
Sadly enough, being that the new Edge browser is Chromium-based, you would have to go to the Chrome Web Store to add uBlock Origin itself rather than through Microsoft’s app store.
Why the hell would someone do that?
1. use W-X!
2. surf with it!!
3. use Edge for surfing!!!
Three faults at once.
If you go to the GitHub page for uBlock Origin, you will find the most official Edge-specific build: https://github.com/gorhill/uBlock#microsoft-edge
This build is actually maintained in a fork by a different developer, nikrolls, and is available here: https://microsoftedge.microsoft.com/addons/detail/odfafepnkmbhccpbejgmiehpchacaeak
For what it’s worth, I use a fork of uBO called Nano Adblocker, and its Edge-specific build is here: https://microsoftedge.microsoft.com/addons/detail/epbkapkgcmdmfpogenoebpdeibmfinpf
I prefer to use the Edge-specific builds because they’re the only ones that a GPO can force-install in Chromium-based Edge; also, the only result for uBlock Origin that I got when searching the Edge Add-Ons site *is* the real one, but you might have been concerned because the developer is not listed as gorhill (Raymond Hill).
I was an original user of Page Ruler, but uninstalled it when it was flagged for malware a couple years back. I believe one of my antimalware programs flagged it, which perhaps begs the additional question, is this developer not running antimalware on his system?
FWIW, after the original extension went rogue, another developer created a replacement with all the same features, minus the malware. I use it occasionally for quickly checking the size of various web objects for development analysis: https://chrome.google.com/webstore/detail/page-ruler-redux/giejhjebcalaheckengmchjekofhhmal
All anti-malware software very frequently pop false positives. Anything they deem as “hacking tools” or tools used by hackers will frequently get flagged or removed by these malware softwares. It is highly doubtful that extension actually contains malware.
What’s being described above – secretly injecting malicious javascript on pages – certainly sounds like “malware” to me. But beyond the semantics, I removed it because it was flagged – either by my antimalware or Google or somewhere for containing malicious code. It was a few years ago, so I really don’t remember what flagged it.
FWIW, good antimalware programs throw up very few false positives. I use Bitdefender, do a fair amount of “development stuff”, and I almost never see one. And the new page ruler extension – which is identical to the original clean one – doesn’t get flagged by Bitdefender, either.
Brian, how is that “Page Ruler” extension still available in Google Store?
No clue. I wondered the same thing.
i guess there needs to be a human involved, something google really hates 😉
This issue is present for code repositories, mobile app stores, and browser plugins.
Code gets created, becomes popular then gets abandoned. This becomes a prime target for attackers who offer to take over maintenance or buy it from the original dev.
Ideally repos/apps/extensions are hashed, then when hash changes have static code application testing performed on them and business logic assessment. This will cost money (at minimum compute time for scans and analysis) so not sure the model for “free” app/plugin. There should also be some onus on the repository to take down known bad.
I only run uBlock Origin (GorHill) and Privacy Badger (EFF). I donate to EFF and would donate to uBlock if it was easy/knew how, especially if it went towards security testing/validation.
For a lot of my browsing I use Virtualbox, disable copy/paste and filesharing and load Lubuntu or Xubuntu run uBlock and Privacy Badger in Firefox, get it configured the way I like, snapshot and revert between uses or boot from a non-persistent USB.
Browser performance and capability have made it so I don’t need the army of extensions I use to use for all three of the main browsers. But now I only use five for Chrome and Firefox, and they are security aids by nature, and well known. One of them only claims to improve privacy, but I’ve put it on Chrome, and it actually speeds up the browser performance, and the only way I can see that happening, is it keeps Chrome from phoning home on every little move you make on the web – so I’m convinced it works. Probably every one here has heard of DuckDuckGo – I’ve had less script problems since using it too.
I haven’t needed NoScript for years – but Avast’s script blocker was a better extension than it was. Now I don’t even use Avast, since it and MBAM don’t get along, I decided to keep MBAM and finally after many years I got rid of Avast. I can’t say that was a mistake either, because MBAM is running things better than Avast lately; but Avast made the same mistake a lot of successful AVs do, and kept trying to make it a suite does it all, product that got bloated and performed less and less. Just like most of them do, with the exception of ESET’s NOD32.
Avast and AVG have been hot garbage since their inception. Windows defender, in it’s infancy, was miles ahead of it. Both were and are basically malware from inception. If you can’t afford MBAM, Webroot, or ESET then just the existing Windows anti-malware. It is literally better than everything else out there with the exception of of the three previously mentioned.
Free Avast/AVG recently got in trouble for tracking users. See https://www.foxbusiness.com/technology/avast-antivirus-user-browsing-data-sold on the web.
I only use 2 browser extensions, and they are both security related–an ad blocker (uBlock Origin) and a malicious web page blocker (Emsisoft Browser Security), which hashes web pages locally so the developer can’t tell where you search. I only search the web with DuckDuckGo or Startpage.com.
Regards,
Mozilla extension .XPI’s are just compressed folders.
Not difficult to poke around in them and get a sense of what they’re doing.
grep URL’s, etc. find out who’s calling who.
Change the version check to let a newer extension install and run on an older browser release.
Wait: you contacted a huge company about a security issue and they *took action* rather than blow you off or call the FBI?
This almost never happens – how did you do it?
He’s Brian Krebs, of course!
my choice for avoid spy collect date extensions is onion browser.
There are a few extensions that I consider in a separate class from the others: HTTPS Everywhere, Privacy Badger, and NoScript. The first two are products of the EFF (very unlikely to be sold off). NoScript has such a large user base that a sale is unlikely to go unnoticed, and in my opinion, the benefits of it’s use outweigh the risks.
“PoperBlocker” is another goodware turned malware. Until a couple of years ago it was a benign pop-up blocker. Then, same as Page Ruler, it was bought by some scumbag for harvesting user creds.
That’s when I realized the risks of extensions and became much more careful. In Chrome (actually the Vivaldi variant) I now use only ScriptSafe and Ublock Origin.
Such a shame that people abuse this wonderful technology to fleece others.
Brian, did you see the corresponding code in page ruler to add a request for a javascript link to the end of whatever the user types and saves on the page?
I found the javascript injection in analytics.js is for the Mixpanel library installation.
the verion of page ruler is 1.0.4
Nice breakdown!! Google recently removed several hundred extensions which were found to contain malware. Tons of extensions have been caught saving & selling users’ browsing history, notably the ironically titled popular “Web of Trust”.
I am the co-founder of the team behind the Epic Privacy Browser which has since inception blocked almost all extensions citing those vulnerabilities and in order to reliably provide private internet access. That policy has kept our users private and secure, while Chrome, Brave, and other users were vulnerable.
Just wanted to add that the other extensions were similar to this one — they installed malicious ads. This also is not uncommon — malware operators buying extensions and then using it to inject ads to spread their malware.
Extensions are so hard to monetize, hence they tend to be sold off to shady companies. I have an extension with couple million users and have received many offers. Fortunately none have been worth my time, or worth selling my soul for. Point is, as these shady firms continuing buying off popular extensions, we are seeing a systematic corruption of the browser extension ecosystem.
The pay per click system of revenue generation has been an unmitigated disaster.
This may really show my ignorance as regards computer stuff. I don”t understand how someone could make a system so vulnerable to so many forms of corruption and continue to hawk it to so many people the world over.
The computer security game is a battle of who is better. Any man-made system can be un-made by someone intelligent enough. No system will EVER be fully secure. There will always be flaws, always be glitches, always be vulnerabilities. It’s a game of who finds it first. Also, the bigger and more popular a software gets, the more of a Target it becomes. This is why Windows has a ton of possible malware and viruses when compared to MacOS and Linux.
I switched to the Brave browser when Apple broke Safari’s ability to use thrid-party extensions that I have relied upon for years. While I was using Safari I also did a lot of testing with Firefox but ultimately gave up because it is more trouble than it is worth. . .
Brave’s built-in privacy settings are pretty darn good but I also use Disconnect, Privacy Badger, HTTPS Everywhere, uBlock Origin and StopThe Madness (which has some unique anti-tracking options). Combined with IVPN I enjoy an ad-free Internet with minimal tracking.
I’m done with commercial anti-malware. These days I rely on a number of excellent utilities from Objective-See, specifically LuLu, BlockBlock and KnockKnock. They are “freeware” but are so darn dependable I made a one-time donation to the developer via Patreon.
I only use Privacy Badger, uBlock Origin, HTTPS Everywhere and NoScript. These are all legit and cover most bases pretty well.
ALWAYS KNOW YOUR SOURCE!
I wonder if holding the original author in some way accountable for what happens to his product once he sells it would change the equation somewhat for authors who essentially build up a following on a solid product, only to screw those followers over for their personal financial benefit.
Don’t want to develop it anymore? Just shut it down. And make it open source. People can’t re-publish it under the original name, so followers would have to find the new extension on their own and each make a judgement call. It’s a lot harder to start at 0 and scam people, they catch on quick enough.
Because the original authors know exactly what they’re doing when selling it to scumbags. This is the inevitable consequence of that decision. Anyone who claims otherwise is lying. They should bear some responsibility for having made it. I’m not saying lock them in prison for 99 years, maybe pay some compensation to the victims. Make the decision to sell to criminals unprofitable and people won’t so be quick to sell to criminals.
How would the original guy know that he’s selling to a “scumbag”?
“In that case, the extension silently adds a request for a javascript link to the end of whatever the user types and saves on the page. ”
So the question begs, if you have multiple websites you are working on the content for, how do yo go back now to see if additional js script found its way into your work?
Do you have to check all your text blocks in the text editor rather than the Visual editor to see the added code?
Brian, I want to add a “me too” to Brendan Ryan’s comment. I’ve just set up in the business of building websites on WordPress and I had Page Ruler installed — until today. How can I check my built site to see if the malware has been injected?
Maybe you could add a coda to your article, covering this?
I figured once plugins went away the bad guys would move on to creating ways to exploit extensions. I don’t use a single one myself, only because there are so many questions about how well these extensions are vetted.