The still-unfolding breach at network management software firm SolarWinds may have resulted in malicious code being pushed to nearly 18,000 customers, the company said in a legal filing on Monday. Meanwhile, Microsoft should soon have some idea which and how many SolarWinds customers were affected, as it recently took possession of a key domain name used by the intruders to control infected systems.

On Dec. 13, SolarWinds acknowledged that hackers had inserted malware into a service that provided software updates for its Orion platform, a suite of products broadly used across the U.S. federal government and Fortune 500 firms to monitor the health of their IT networks.
In a Dec. 14 filing with the U.S. Securities and Exchange Commission (SEC), SolarWinds said roughly 33,000 of its more than 300,000 customers were Orion customers, and that fewer than 18,000 customers may have had an installation of the Orion product that contained the malicious code. SolarWinds said the intrusion also compromised its Microsoft Office 365 accounts.
The initial breach disclosure from SolarWinds came five days after cybersecurity incident response firm FireEye announced it had suffered an intrusion that resulted in the theft of some 300 proprietary software tools the company provides to clients to help secure their IT operations.
On Dec. 13, FireEye published a detailed writeup on the malware infrastructure used in the SolarWinds compromise, presenting evidence that the Orion software was first compromised back in March 2020. FireEye didn’t explicitly say its own intrusion was the result of the SolarWinds hack, but the company confirmed as much to KrebsOnSecurity earlier today.
Also on Dec. 13, news broke that the SolarWinds hack resulted in attackers reading the email communications at the U.S. Treasury and Commerce departments.
On Dec. 14, Reuters reported the SolarWinds intrusion also had been used to infiltrate computer networks at the U.S. Department of Homeland Security (DHS). That disclosure came less than 24 hours after DHS’s Cybersecurity and Infrastructure Security Agency (CISA) took the unusual step of issuing an emergency directive ordering all federal agencies to immediately disconnect the affected Orion products from their networks.
ANALYSIS
Security experts have been speculating as to the extent of the damage from the SolarWinds hack, combing through details in the FireEye analysis and elsewhere for clues about how many other organizations may have been hit.
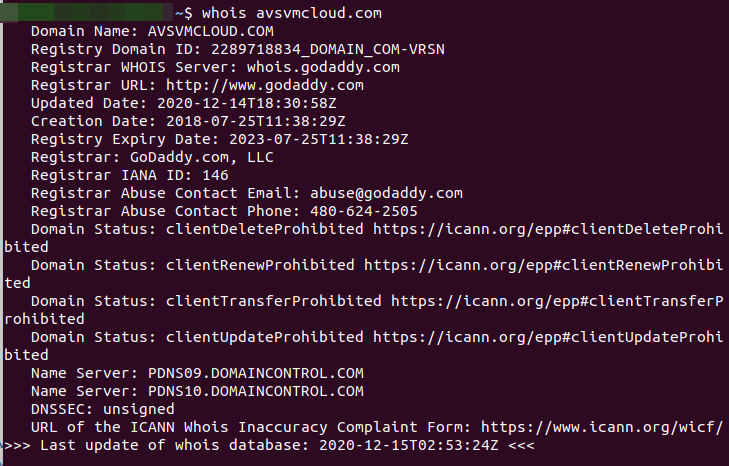
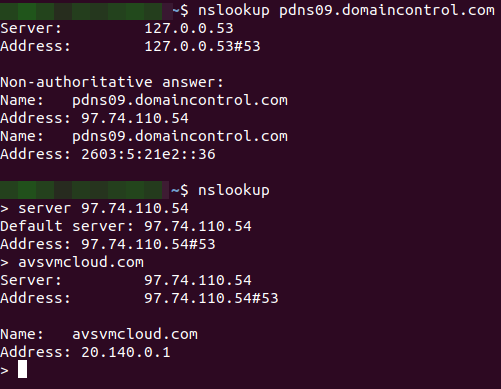
And it seems that Microsoft may now be in perhaps the best position to take stock of the carnage. That’s because sometime on Dec. 14, the software giant took control over a key domain name — avsvmcloud[.]com — that was used by the SolarWinds hackers to communicate with systems compromised by the backdoored Orion product updates.
- A WHOIS lookup on the malware control domain.
- Where does the malware control domain now point? 20.140.0.1
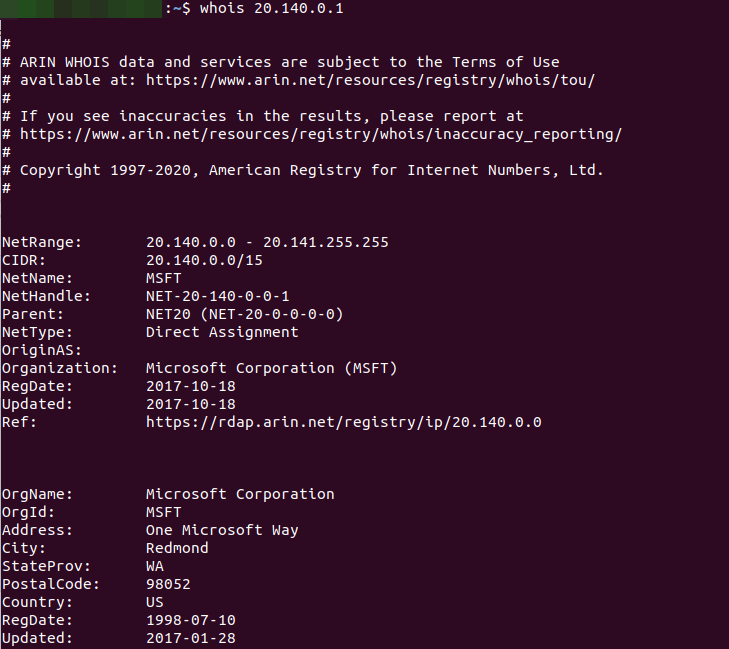
- A WHOIS lookup on the IP address (20.140.0.1).
Armed with that access, Microsoft should be able to tell which organizations have IT systems that are still trying to ping the malicious domain. However, because many Internet service providers and affected companies are already blocking systems from accessing that malicious control domain or have disconnected the vulnerable Orion services, Microsoft’s visibility may be somewhat limited.
Microsoft has a long history of working with federal investigators and the U.S. courts to seize control over domains involved in global malware menaces, particularly when those sites are being used primarily to attack Microsoft Windows customers.
Microsoft dodged direct questions about its visibility into the malware control domain, suggesting those queries would be better put to FireEye or GoDaddy (the current domain registrar for the malware control server). But in a response on Twitter, Microsoft spokesperson Jeff Jones seemed to confirm that control of the malicious domain had changed hands.
“We worked closely with FireEye, Microsoft and others to help keep the internet safe and secure,” GoDaddy said in a written statement. “Due to an ongoing investigation and our customer privacy policy, we can’t comment further at this time.”
FireEye declined to answer questions about exactly when it learned of its own intrusion via the Orion compromise, or approximately when attackers first started offloading sensitive tools from FireEye’s network. But the question is an interesting one because its answer may speak to the motivations and priorities of the hackers.
Based on the timeline known so far, the perpetrators of this elaborate hack would have had a fairly good idea back in March which of SolarWinds’ 18,000 Orion customers were worth targeting, and perhaps even in what order.
Alan Paller, director of research for the SANS Institute, a security education and training company based in Maryland, said the attackers likely chose to prioritize their targets based on some calculation of risk versus reward.
Paller said the bad guys probably sought to balance the perceived strategic value of compromising each target with the relative likelihood that exploiting them might result in the entire operation being found out and dismantled.
“The way this probably played out is the guy running the cybercrime team asked his people to build a spreadsheet where they ranked targets by the value of what they could get from each victim,” Paller said. “And then next to that they likely put a score for how good the malware hunters are at the targets, and said let’s first go after the highest priority ones that have a hunter score of less than a certain amount.”
The breach at SolarWinds could well turn into an existential event for the company, depending on how customers react and how SolarWinds is able to weather the lawsuits that will almost certainly ensue.
“The lawsuits are coming, and I hope they have a good general counsel,” said James Lewis, senior vice president at the Center for Strategic and International Studies. “Now that the government is telling people to turn off [the SolarWinds] software, the question is will anyone turn it back on?”
According to its SEC filing, total revenue from the Orion products across all customers — including those who may have had an installation of the Orion products that contained the malicious update — was approximately $343 million, or roughly 45 percent of the firm’s total revenue. SolarWinds’ stock price has fallen 25 percent since news of the breach first broke.
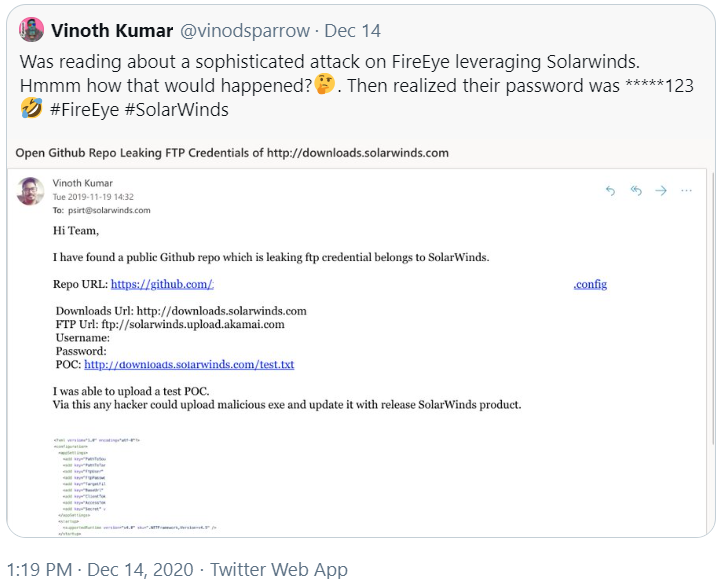
Some of the legal and regulatory fallout may hinge on what SolarWinds knew or should have known about the incident, when, and how it responded. For example, Vinoth Kumar, a cybersecurity “bug hunter” who has earned cash bounties and recognition from multiple companies for reporting security flaws in their products and services, posted on Twitter that he notified SolarWinds in November 2019 that the company’s software download website was protected by a simple password that was published in the clear on SolarWinds’ code repository at Github.
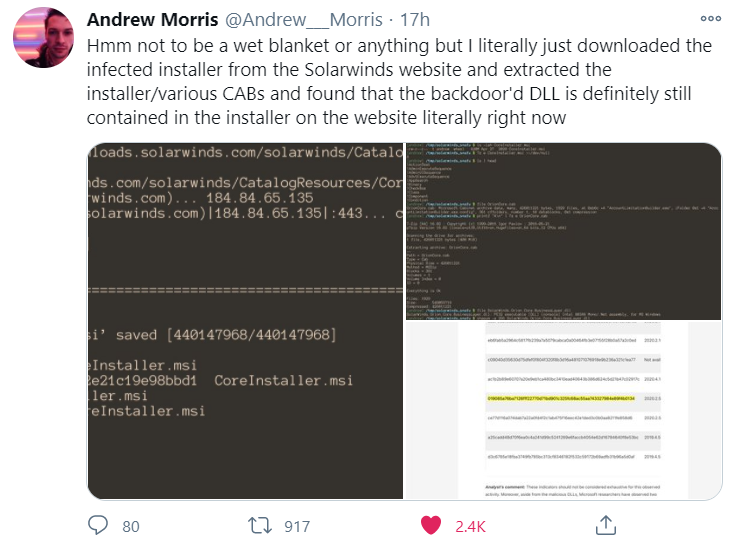
Andrew Morris, founder of the security firm GreyNoise Intelligence, on said that as of Tuesday evening SolarWinds still hadn’t removed the compromised Orion software updates from its distribution server.
Another open question is how or whether the incoming U.S. Congress and presidential administration will react to this apparently broad cybersecurity event. CSIS’s Lewis says he doubts lawmakers will be able to agree on any legislative response, but he said it’s likely the Biden administration will do something.
“It will be a good new focus for DHS, and the administration can issue an executive order that says federal agencies with regulatory authority need to manage these things better,” Lewis said. “But whoever did this couldn’t have picked a better time to cause a problem, because their timing almost guarantees a fumbled U.S. response.”




…bye bye solarwinds…
Lewis said. “But whoever did this couldn’t have picked a better time to cause a problem, because their timing almost guarantees a fumbled U.S. response.”
Yet another example of 2020 being the year of “never let a crisis go to waste.”
The adversary knows that too.
Nonsense. Elections don’t have any influence on cyber (at all).
…defensive cyber no change maybe, response (sanctions, kinetic, etc.) – big time difference…
Who said anything about elections? Lewis didn’t.
He was merely making the point that you have a change in administration and a change in Congress. Plus you have several leaders in the current administration leaving early.
It will take time for new decisions to be made. And that will impact a response, or continuity of a response started now, and/or what a longer-term response looks like.
This is absolutely the worst time of the worst year do this.
Not to mention that the director of the CISA was just recently canned for matters relating directly to election (He didn’t lie for the president about the election).
A statistical anomaly is one thing, a statistical impossibility is another. Several statistical impossibilities only happen purposely. Blue teaming is based on this concept.
To wave such anomalies away is either purposeful or caused by incredible ineptitude.
The claims of statistical impossibilities were also made up.
Everyone paying attention knew months before the election that red mirages and blue shifts would occur due to covid-19 and the obvious difference between mail and in person voters.
It’s basic math anyone here could follow, if they paid attention beforehand.
You’re right, the “blue wave” was forecast months in advance. But what transpired was an order of magnitude larger than anything forecast. Other simple numbers issues pop up as well. For example, the general consensus is that Biden supporters made up a higher percentage of mail-in voters and this therefore explains the early morning “dumps” of 70-80% Biden ballot counts. But when you look at the actual numbers you’ll find that in Wisconsin, for instance, Republicans requested more absentee ballots. Republicans also votes 95% for Trump on election day. Either Republicans turned left in MASSIVE numbers in only the precincts that reported latest or something does not add up.
The “requested” ballots by party affiliation are indeed a poor indicator. Moderates and independents tend to still be registered to political parties they no longer really are a part of. Same is true in the deep south. Older dixie conservatives still registered as Democrats.
They vote Republican for decades, because they don’t care about primaries or the hassle of officially changing party affiliation.
Then there are plenty of real Republicans that hate Trump.
It also explains down ballot races across the country. Trump has very loud supporters, but they have always been a minority.
Wisconsin is one of only 14 states with open primaries. That means they have a lot of people with party affiliations that don’t vote for that party’s candidate.
Not just a blue wave, but a red mirage too.
What transpired was actually not as big as predictions. Predictions had a much larger Biden victory if you recall. Polling errors of course.
It is funny that when it suits your argument, you claim there was a bigger swing than predicted, but Trump makes the opposite argument that the swing wasn’t as big as the polls said…. as if him doing better than predictions shows he should not have still lost.
Do not equate the “Republicans” who requested ballots, and the “Republicans” who answered pollsters about who they would vote for. That’s bad math at best and really just ignorance of politics.
First, lets look at your math. 70%-80% of mail in votes went for Biden, true. But your other number, 95% is a polling number similar to the 96% of democrats voting for Biden. It doesn’t indicate anything about mail-in or in-person voting.
A higher percentage of in-person votes may have went to Trump. But there were fewer of them.
Out of the 1,924,838 votes in Wisconsin, only 649,819 were in-person and 1,275,019 were mail ballots. That 2/3rds of voters were mail in, and if 70% of mail in were for Biden… that would have been a HUGE Trump loss. In reality, so many Wisconsinites mailed in early… Biden only needed maybe 54% of mail in votes to win as he did.
The requested ballots by party affiliation are a poor indicator of vote, period. Especially in places like Wisconsin.
Why? Because they are 1 of the 14 states that have OPEN PRIMARIES. This means there is little to no incentive to register with the party you would vote for in an election.
Moderates and independents tend to still be registered to political parties they no longer really are a part of. Same is true in the deep south. Older dixie conservatives still registered as Democrats.
They vote Republican for decades, because they don’t care about primaries or the hassle of officially changing party affiliation.
Then there are also plenty of real Republicans that hate Trump.
It also explains down ballot races across the country. Trump has very loud supporters, but they have always been a minority.
OK, explain this…Trump has 88.6 million followers on Twitter…Biden has 20 million followers. The guy who didnt come out of his basement, who never did anything for America in 48 years…We all went to bed with Trump in a landslide lead, we wake up after 6 states stop counting(unprecedented) and bring in ballots in the back door and nobody got to observe. The dominion voting system was compromised, they has bullies kicking people out of polling stations. People being threatened, their children are being threatened. Criminals act this way…not leaders. Only a willfully blind idiot cannot see what’s happened to our country.
Followers on Twitter aren’t counted during an election. Only votes are counted. The other arguments you make are the same ones that the ‘Strike Force One’ legal team made and lost in the courts more than 50 times over. If all avenues of investigation confirm that your assumptions are incorrect, maybe, it’s possible that your assumptions are incorrect.
Followers on twitter, do not equate to votes. The tide was changing long ago. As a person who is neither Democrat or Republican, I decided I was going to vote by mail for Biden a while back, while my Republican friends decided to vote in person. This is what happened with the election. Trump himself submitted an absentee vote and most people did not want to deal with lines and COVID, so it made it easier to vote. Then there were those who were calling and emailing telling people to vote. This didn’t happen out of nowhere. It’s easy to blame a conspiracy, but the true conspiracy is that there isn’t one. The way the administration handled the crisis was appalling. The calling it a hoax and the sheer ineptitude showed that Trump does not have the leadership to help navigate us through such difficult times. He’s too unstable. Additionally, it was because of his administrations lack of taking these things seriously that we are where we are as a nation. Lest we forget he thought it was wise to nix a whole pandemic team that could have noticed COVID. And now this breach. It happened in March and is now being seen. He nixed that team as well right? See the pattern. He’s consistent.
He did some good, which every president does, but his inability to be a good leader sacked him. A president is not a president just for Republicans, a president is a president for the country. He didn’t embody that, so he was removed.
It’s almost as if there’s a pandemic on and people voted by mail. Except Republicans, who the president told not to do that.
For your statement to pan out, the FBI lied, the courts lied, the CIA lied, the attorney general lied, the entire state Republican parties of Georgia, Arizona, Michigan, PA lied… everyone lied…
or..
Trump lost.
Perhaps the reason Trump can’t comprehend losing is he did everything he could to disenfranchise voters, crippled the postal system and he still lost. Also, look up “Republicans for Biden”. So many Republicans hated that guy, so they voted Biden. But for Senate etc they kept the Repub ticket. Hence the split.
Occams razor, dipstick.
“Pandemic,” what a joke. Business as usual in most of the world.
“most of the world”? This is about US elections. And the pandemic wave hit hardest as people went out to vote, and hit hard in swing states.
Business as Usual in the rest of the world?4 You perhaps need to do some research – maybe start here: https://ourworldindata.org/coronavirus
and make sure you select the checkbox for per 1M population so that you get a fair comparison.
Literally nothing you said has even an ounce of truth.
Literally everything he said is 100% true. Take your damn blinders off. The proof of fraud is LITERALLY EVERYWHERE.
You need to put your blinders back on….
“The proof of fraud is LITERALLY EVERYWHERE”
And THIS is the real root cause. That ignorance is prevalent among the masses.
This is what separates the real lawyers, forensic investigators, judges and experts in the field… from the sheep. The gullible Trump followers don’t know what the word “proof” means. They have no objective concept of “evidence” beyond their own fiction.
When people lower the bar to the point when anything passes for “proof”, they can be taken advantage of. And that is what has happened here.
I looked in my bathroom, found no evidence.
They would then just say you flushed it.
This is the collective mental illness of conspiracy theories. There is no falsifiability and an ignorance of logic. There will always be another and another. Facts be damned, the imagination is unlimited.
It’s funny to me that the people who proclaim so loudly that the rest of us are blind are somehow staking this belief on a TV show host with a decades long history of fraud and bankruptcy.
I didn’t realize you had to enter your twitter user name on your voter registration form.
Oops.
Only a willfully blind idiot would still be hanging onto the fact that dEaR leAdEr lost. I heard a lot of “don’t like it, leave” comments post 2016….maybe some of y’all should take your own advice?
And Russia hacked the election in 2016 and made trump president…… Also, why did we only have 2 alzeimers patients as a choice? thats the bigger question here. Also, I guess all you security lovers conveniently forgot the entire defcon hacking village which proved that these voting machines are the laughing stock of the world. The biden votes don’t obey benford’s law which mathematically detects fraud.
Benfords Law claim has already been debunked by mathematicians.
https://www.reuters.com/article/uk-factcheck-benford/fact-check-deviation-from-benfords-law-does-not-prove-election-fraud-idUSKBN27Q3AI
The Constitution of the United States states plainly that States get to set elections whichever way they choose. That is what the foundation is, and we respectfully fart in the general direction of anyone who thinks otherwise, including the esteemed mathematicians. Voters decide elections in America, not lawyers, and States get to decide how those votes are taken and counted.
Remember, Comrade, it’s not who votes that matters, it’s who counts the votes that matters, and in this instance both parties did so…
Hey, can you guys go back to Parler?
Best one thus far..awesome..discuss securty not freaking Trumpsh* lies
I saw this incredibly dumb thing about twitter followers and I thought it was a joke. But apparently there really are idiots who think this way? Amazing.
Let’s ignore that it is completely possible to buy twitter followers.
Trump amassed twitter follower by being president of the united states for four years. Which calls attention from a lot of international people to his tweets. His twitter feed is also a guaranteed source of train wrecks, so lots of people follow him just for that. Meanwhile, Joe Biden is a milquetoast democrat whose tweets no one really wants to read. This doesn’t mean people won’t vote for him over the absolute trash fire of a president trump turned out to be
Drumpf has more twitter bot followers than biden. What’s your point?
Lie? Ha Ha Ha…..proof is in the pudding man! Its all out there. He didnt have to lie. We all know Dominion has ties to Solarwinds so there ya go…..
cyber has nothing to do with changing admins, either.
This attack started happening in March 2020.
The current administration gutted the cybersecurity, fired the guy in charge of it, and put a barely qualified person in charge of their big “CMMC” initiative to prevent this sort of thing, so no, the election had nothing to do with it – the lack of any response to cyber threats due to the desire to downplay Russian interference in the 2016 election DID … our cybersecurity is without a qualified pilot, so …
How would you envision CMMC preventing this?
Do you actually work in information security? there hasn’t been a downgrading of cyber capabilities under trump, there has been MORE communication. In fact, the NSA is actually releasing vuln data and notifying people before vulnerabilities get exploited/stolen.
How, exactly, could CMMA have been defined, to prevent the SolarWinds hack? It sounds like the kind of thing uninformed managers and bean counters like, but which actually is useless.
… and we trust *Microsoft* — whose founder is
*LITERALLY BEHIND “THE GREAT RESET”*
to ‘get to the bottom’ of things?
Could people get any more completely *STUPlD*?
I see a reckoning coming for all of Big Tech. Lawsuits would be the *best possible outcome* for all of them.
“Could people get any more completely *STUPlD*?”
Apparently you are…..
Makes me wonder how many SolarWinds installs were on ITAR or HIPAA level security computers systems.
Krebs, has Dominion issued a statement regarding use of SolarWinds products?
…tongue firmly planted in cheek – “we take your security very seriously”…
Why would they (Dominion “issue a statement”)?
No one (i.e. in the press) is going to investigate or ask the question, and Dominion isn’t going to volunteer.
Even if they don’t use Orion at all, and assumingly could issue a “we’re not affected” statement, I really doubt they’d welcome any more scrutiny by saying anything.
Voting machines are not online in any state.
I’ve only read mention of compromised Windows hosts. Any word on Linux targets. Solarwinds Orion supports Linux too.
Agents are supported on the following Linux/Unix operating systems.
Amazon AMI, 64-bit
CentOS 6.x, 32-bit
CentOS 6.x, 7.x, 8.x, 64-bit
IBM AIX 7.x
Oracle Linux 6.x, 7.x, 8.x, 64-bit
Raspbian Jessie 8.0
Red Hat Enterprise Linux 5.11, 6.x, 86-bit
Red Hat Enterprise Linux 5.11, 6.x, 7.x, 8.x, 64-bit
SUSE Linux Enterprise Server 11.x – 15.x, 64-bit
SUSE Linux Enterprise Server 11.x, 86-bit
Ubuntu 14.x – 16.x, 86-bit
Ubuntu 14.x – 18.x, 64-bit
https://documentation.solarwinds.com/en/Success_Center/orionplatform/Content/Core-Deploy-a-Linux-agent-manually.htm
Supposedly, agents are not affected.
” …said that as of Tuesday evening… ”
The time stamp in that screenshot is monday, not tuesday.
Yesterday there seemed to be concern about whether the stated timelines made sense (August vs March?) – I admit to not following that closely, but can anyone say whether the timeline now makes sense?
These breaches are like flowers budding. Many interesting layers to peal before the entire picture is revealed.
if ever revealed…
Really a shame as they make some good products. Wish the management of the products had been up to level needed to ensure proper security. I’ll keep my SEM for now.
As a backbone of our economy perhaps we should admit the internet and things connected to it are far from secure and its only a question of time when someone throws a really big wrench into it. Our go to communication used to be word of mouth, then the printed word, telegraphy and then radio and telephone. Now the internet ties us all together in everyday life from birth to death, school and university, our work and play. In short we rely on the a system that is at risk and being attacked continuously.
Hate to admit this, but I am old enough to recall the Morris Worm in 1988 (https://en.wikipedia.org/wiki/Morris_worm). The Internet was not built for security, it was built for survivability — to survive a nuclear attack.
Had it been built for security, you’d likely have an Internet access license authenticated and tracked by the government. See the emerging PRC surveillance state for an example.
Access control rigor imposes friction that impedes operation and convenience.
Great analysis. Don’t feel bad. I had been in the industry almost a decade in 1988…
18K in press-release math really means 500,000.
These articles are interesting to me, in a general way, but I’m not savvy on the inner workings of computers/hacking. How would this type of hack ‘trickle down’ to an average user like me? Is it anything I should PERSONALLY be concerned about?
Depends, but a really low-fi result may be a ransomware attack against the company where you work or purchase goods from. Moving up would be private (HR or Consumer) data theft. Followed by selling/revealing trade secrets. At worst if you work for the company that’s compromised then this could end you, at best it would create an IT nightmare where you are scrambling to rebuild your work environment. Either way it can cause disruption.
Personally I don’t think this particular attack vector will be used again on anyone else. It was a highly-targeted one-off job. The perpetrator(s) obviously had an extremely specific target (the US gov.) and they probably got all the information they were looking for. So I doubt they’ll risk exposing themselves further by attempting hacks on random businesses or private users, they simply have bigger fish to fry.
Something this big & high-up, could possibly have been behind Gmail going dark?
SolarWinds should go bankrupt and not a single Golden Parachute should be paid to the incredible mismanagement team that even after being warned, allowed Russian espionage against the United States Government.
Isn’t there any kind of criminal charges that can be brought against the incompetent CEO of SolarWinds?
If he met in a dark alley with a Russian agent multiple times and handed over confidential and maybe even secret government data, he’d be charged with espionage and sentenced to 20 years in a Federal prison.
Instead, he likely leaves with millions and goes on to another CEO position. This was pure negligence and SolarWinds needs to be sued into oblivion.
Freedom isn’t free and neither is information security. It appears to me that Solar Winds became complacent in their ability to effectively monitor their own product(s). From my professional and personal experiences, “assuming” all business processes, and business systems are secure because a person “believes” the key security vendors are lockdown secure, will sooner or later make “an ass out of you and me. “ Sure wouldn’t want to be anywhere close to the Solar Wind’s executive team!
Who’s to say he didn’t meet with someone in a dark alley?
But I realize many have been led to believe such things are only in spy novels, not realizing that spy novels are derived from actual spying and espionage.
Such types were probably surprised to read this week about the leaked info on CCP members who have infiltrated Western governments and corporations.
“actual spying and espionage” is more often than not exaggerated. HUMINT isn’t as sexy as the headlines and movies make them out to be.
Yes, conspiracies sometimes do occur. But they are exceedingly rare. The grander (more involved) the conspiracy, the faster it unravels,… so real conspiracies that are big don’t last too long.
The vast majority of conspiracy theories are NOT true.
Occam’s razor, Hanlon’s razor, apophenia and a bunch of other axioms are at play here. The boring reality it’s all psychological. The grim reality, is that some people have no scruples about exploiting this psychological weakness in the masses.
With the password SolarWinds123, my three-year-old great-granddaughter could hack into their website.
Any chance this bug was used to plant other bugs in systems that have not yet been detected? FireEye blog mentions Teardrop and Beacon, but is it possible that others which have not yet been detected may be live or dormant in impacted systems?
You and Steve C# ask a good question.
I am curious how far the hackers were able to get and what they might’ve done that we have yet to discover / will never discover? The one-time stealing of information assets is one thing but would it be so far-fetched that hackers got into Governmental / DoD systems / DoD contractors and injected backdoors/code into programs that allow for continued stealing of information assets or controlling things that impact national security?
Can’t believe the IT guys made a password that simple for important access that ended up compromising multiple systems and on top of it they still haven’t removed or changed the affected files and programs.
This with the *****123 pass is ridiculous I think this happend from the inside to open a backdoor and why not to make fun of them.
I’m wondering whether or not we should continue using Dameware MiniRemote control. They say the code has been audited and that it wasn’t compromised, but who knows.
If you have it restricted to internal network only, and monitor your edge, these tools shouldn’t even have an option to be a problem.
We pulled logs looking for traffic to the CC server/domain going back one year, glad we didn’t find any.
Hello how is everyone I hope well today..well I Kno. Alot of you will think I’m crazy but one of these men has been talking to me..that’s all I’m going to say on here ..
Interesting. Good write-up, good job. Just as in business, security is only as good as your least caring employee.
Somebody pooched, I wonder if this goes well with the ongoing vpn, and remote work hacks. And the separation of internet and workstations on common net. But…
It always amazes me when I read about big corporations and the government allowing outbound pings to command and control servers or software to communicate outbound for license checks or software “updates” with outside suppliers. Then they wonder about how data exfiltration occurred.
It’s especially surprising when you see how many Joe Average home users are posting about how they try to limit Windows Updates to the time of their choosing and block connections to ad servers and data analytics companies.
If only company executives had the same level of paranoia…
There is difference between home users and corporate enterprises. Commercial use licenses are not trivial and cannot simply be blocked without the legal department getting involved because of a purchase contract violation or something.
DLP is a big business and many organizations deploy monitors that would catch this. It’s also easy to detect anomalies in outbound heartbeats if they turn into C2.
A LOT of crap comes from Godaddy servers! Methinks we are just seeing the tip of the iceberg. BTW, when random dots start connecting into a line or curve, you learn those dots are not random. From an sys admin perspective, the timing of this is just too worrisome…
Who’s your GoDaddy?
I think the federal government has a set of Cybersecurity recommendations ready to go form in the Solarium Commission. Do you think that could pushed through quickly?
Seems to be a big giveaway to the Defense Department/DHS, so I don’t know why anyone in Congress would be against it. Further, putting CEO’s and CFO’s on the hook will force the private sector to invest and not questions the value for at least 5 years or so.
I also think this would be a boom for the audit companies. SOX sure generated a lot of revenue.
…don’t hold your breath…
https://www.youtube.com/watch?v=VXUPyod6vqw
Mubix – Kicking Orion’s Assets.
Good watch.
Well…….there is only so much to spread, but in the end, FireEye can point the finger at everyone else, but their tools got out of the hen-house, so much for their joke of what they call security.
Solarwinds? I wouldn’t use one piece of their software right now, there is no way of knowing how deeply they were compromised?
Microsoft? Not ever sure I am ever glad to see them playing cop and seizing property (did they have a warrant for that?)
The Feds? Well…..what can be said. Every time something like this goes down, blame the Russians, again, again and again. It’s so easy too……how dare this government ever accuse the PRC of doing this……they might call out our debt to them……
Be funny to find out a 17 year old in this country did all of this…….
Wonder what Edward Snowden thinks……
China got blamed for the last big supply chain hack way back in 2018.
“The Big Hack: How China Used a Tiny Chip to Infiltrate U.S. Companies”
Of course it was reported by business news as fact, and not by cybersecurity or tech blogs as such.
It was a huge accusation, that all the victims (Super Micro, Apple and many others) denied. What happened? Nothing. Just the trade war with China, that made Bloomberg sound the alarm for a hypothetical attack that never happened. It was a political stunt that garnered continued support for a Trade War.
Secret chips were never found.
This supply chain hack is different, with lots of real evidence and the cybersecurity (not the business magazine world) sounding the alarm and investigating. It’s too soon to know for certain, but attribution is possible down to the APT level. And it’s looking Russian.
Rule of Thumb, if its attacking finance, business or intellectual property… China is indeed the first suspect. If it is military, infrastructure or energy… we looking at you, Russia.
China got blamed for the last big supply chain hack way back in 2018.
“The Big Hack: How China Used a Tiny Chip to Infiltrate U.S. Companies”
Of course it was reported by business news as fact, and not by cybersecurity or tech blogs as such.
It was a huge accusation, that all the victims (Super Micro, Apple and many others) denied. What happened? Nothing. Just the trade war with China, that made Bloomberg sound the alarm for a hypothetical attack that never happened. It was a political stunt that garnered continued support for a Trade War.
Secret chips were never found.
This supply chain hack is different, with lots of real evidence and the cybersecurity (not the business magazine world) sounding the alarm and investigating. It’s too soon to know for certain, but attribution is possible down to the APT level. And it’s looking Russian.
Rule of Thumb, if its attacking finance, business or intellectual property… China is indeed the first suspect. If it is military, infrastructure or energy… we’re looking at you, Russia.
Meanwhile, the CEO of 11 years announced resigning sells a tranch of stocks mid Nov ($11 million) and another Dec 7th for $46 million.
Exec VP sells off for a couple million in mid Nov also. No exfiltration of data found so far. Footprints of hackers monitoring network from IPs mimicking locations of company locations…since March. The new CEO is ex CEO of PulseSecure major hack fame…
You aren’t gonna extort cash form the feds, but you will eventually get exposed and investigated.
So much low hanging fruit, why Treasury, Commerce, DHS? What were they monitoring and actually looking for?
Timing is everything…but nothing to see here.
It seems like FireEye is doing much more than SolarWinds to investigate how this works and provide as much information as possible.
Solarwinds does network tools and monitoring… FireEye does these kinds of full scale intrusion investigations for a living.
It’s not surprising.
So, Mr Vinoth Kumar looked through his telescope a year ago, saw this comet heading straight for us and nobody took any notice.
Shouldn’t there a big prize for finding this kind of thing?
Nothing to see here? Short SWI stock with extreme prejudice.