Facebook, Instagram, TikTok, and Twitter this week all took steps to crack down on users involved in trafficking hijacked user accounts across their platforms. The coordinated action seized hundreds of accounts the companies say have played a major role in facilitating the trade and often lucrative resale of compromised, highly sought-after usernames.
 At the center of the account ban wave are some of the most active members of OGUsers, a forum that caters to thousands of people selling access to hijacked social media and other online accounts.
At the center of the account ban wave are some of the most active members of OGUsers, a forum that caters to thousands of people selling access to hijacked social media and other online accounts.
Particularly prized by this community are short usernames, which can often be resold for thousands of dollars to those looking to claim a choice vanity name.
Facebook told KrebsOnSecurity it seized hundreds of accounts — mainly on Instagram — that have been stolen from legitimate users through a variety of intimidation and harassment tactics, including hacking, coercion, extortion, sextortion, SIM swapping, and swatting.
THE MIDDLEMEN
Facebook said it targeted a number of accounts tied to key sellers on OGUsers, as well as those who advertise the ability to broker stolen account sales.
Like most cybercrime forums, OGUsers is overrun with shady characters who are there mainly to rip off other members. As a result, some of the most popular denizens of the community are those who’ve earned a reputation as trusted “middlemen.”
These core members offer escrow services that – in exchange for a cut of the total transaction cost (usually five percent) — will hold the buyer’s funds until he is satisfied that the seller has delivered the credentials and any email account access needed to control the hijacked social media account.
For example, one of the most active accounts targeted in this week’s social network crackdown is the Instagram profile “Trusted,” self-described as “top-tier professional middleman/escrow since 2014.”
Trusted’s profile included several screenshots of his OGUsers persona, “Beam,” who warns members about an uptick in the number of new OGUsers profiles impersonating him and other middlemen on the forum. Beam currently has more reputation points or “vouches” than almost anyone on the forum, save for perhaps the current and former site administrators.
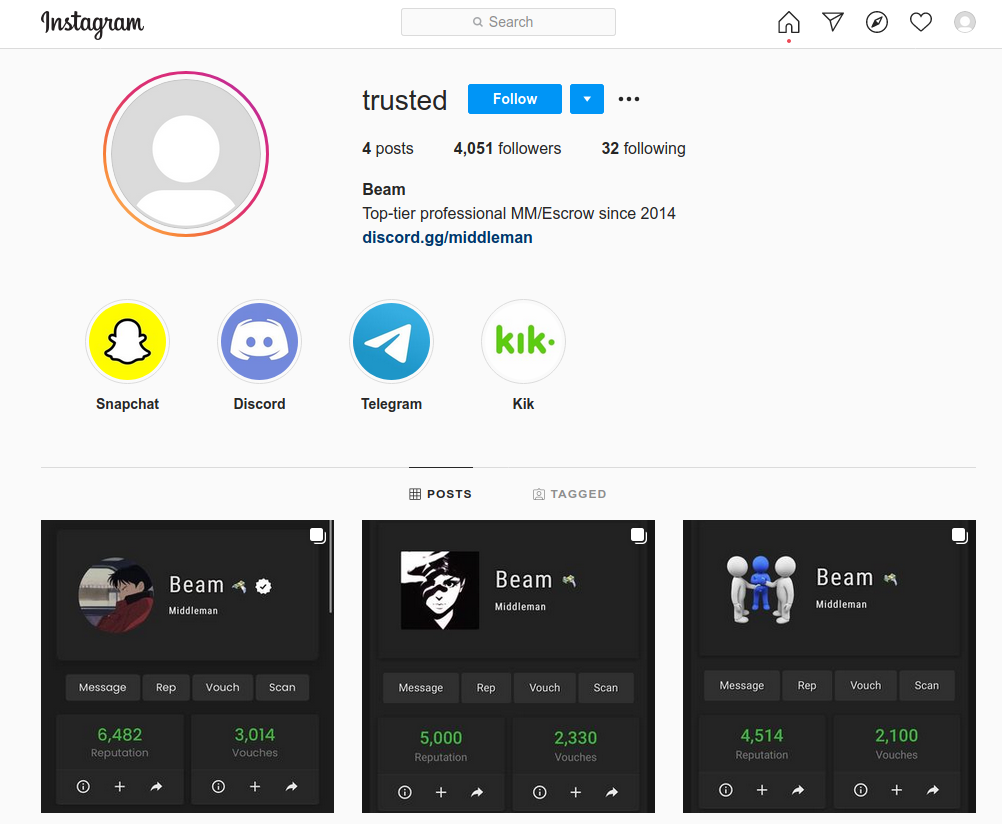
The now-banned Instagram account for the middleman @trusted/beam.
Helpfully, OGUsers has been hacked multiple times over the years, and its database of user details and private messages posted on competing crime forums. Those databases show Beam was just the 12th user account created on OGUsers back in 2014.
In his posts, Beam says he has brokered well north of 10,000 transactions. Indeed, the leaked OGUsers databases — which include private messages on the forum prior to June 2020 — offer a small window into the overall value of the hijacked social media account industry.
In each of Beam’s direct messages to other members who hired him as a middleman he would include the address of the bitcoin wallet to which the buyer was to send the funds. Just two of the bitcoin wallets Beam used for middlemanning over the past of couple of years recorded in excess of 6,700 transactions totaling more than 243 bitcoins — or roughly $8.5 million by today’s valuation (~$35,000 per coin). Beam would have earned roughly $425,000 in commissions on those sales.
Beam, a Canadian whose real name is Noah Hawkins, declined to be interviewed when contacted earlier this week. But his “Trusted” account on Instagram was taken down by Facebook today, as were “@Killer,” — a personal Instagram account he used under the nickname “noah/beam.” Beam’s Twitter account — @NH — has been deactivated by Twitter; it was hacked and stolen from its original owner back in 2014.
Reached for comment, Twitter confirmed that it worked in tandem with Facebook to seize accounts tied to top members of OGUsers, citing its platform manipulation and spam policy. Twitter said its investigation into the people behind these accounts is ongoing.
TikTok confirmed it also took action to target accounts tied to top OGUusers members, although it declined to say how many accounts were reclaimed.
“As part of our ongoing work to find and stop inauthentic behavior, we recently reclaimed a number of TikTok usernames that were being used for account squatting,” TikTok said in a written statement. “We will continue to focus on staying ahead of the ever-evolving tactics of bad actors, including cooperating with third parties and others in the industry.”
‘SOCIAL MEDIA SPECIALISTS’
Other key middlemen who’ve brokered thousands more social media account transactions via OGUsers that were part of this week’s ban wave included Farzad (OGUser #81), who used the Instagram accounts @middleman and @frzd; and @rl, a.k.a. “Amp,” a major middleman and account seller on OGUusers.
Naturally, the top middlemen in the OGUsers community get much of their business from sellers of compromised social media and online gaming accounts, and these two groups tend to cross-promote one another. Among the top seller accounts targeted in the ban wave was the Instagram account belonging to Ryan Zanelli (@zanelli), a 22-year-old self-described “social media marketing specialist” from Melbourne, Australia.
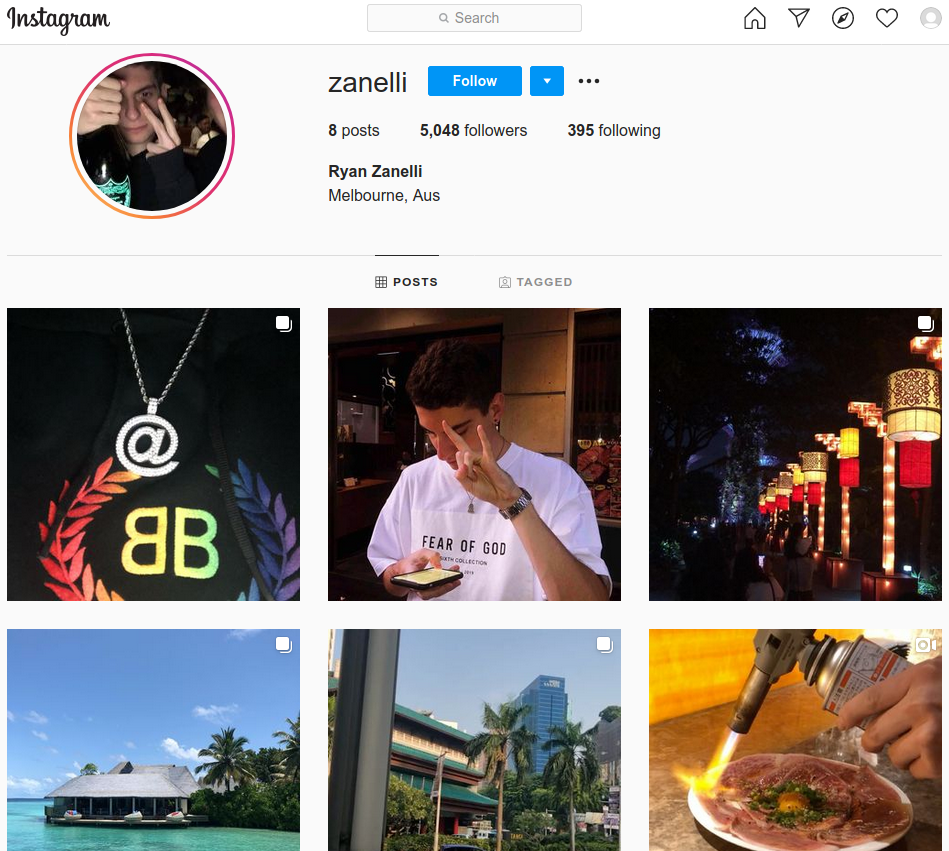
The leaked OGusers databases suggest Zanelli is better known to the OGusers community as “Verdict,” the fifth profile created on the forum and a longtime administrator of the site.
Reached via Telegram, Zanelli acknowledged he was an administrator of OGUsers, but denied being involved in anything illegal.
“I’m an early adaptor to the forum yes just like other countless members, and no social media property I sell is hacked or has been obtained through illegitimate means,” he said. “If you want the truth, I don’t even own any of the stock, I just resell off of people who do.”
This is not the first time Instagram has come for his accounts: As documented in this story in The Atlantic, some of his accounts totaling more than 1 million followers were axed in late 2018 when the platform took down 500 usernames that were stolen, resold, and used for posting memes.
“This is my full-time income, so it’s very detrimental to my livelihood,” Zanelli told The Atlantic, which identified him only by his first name. “I was trying to eat dinner and socialize with my family, but knowing behind the scenes everything I’ve built, my entire net worth, was just gone before my eyes.”
Another top seller account targeted in the ban wave was the Instagram account @h4ck, whose Telegram sales channel also advertises various services to get certain accounts banned and unbanned from differed platforms, including Snapchat and Instagram.
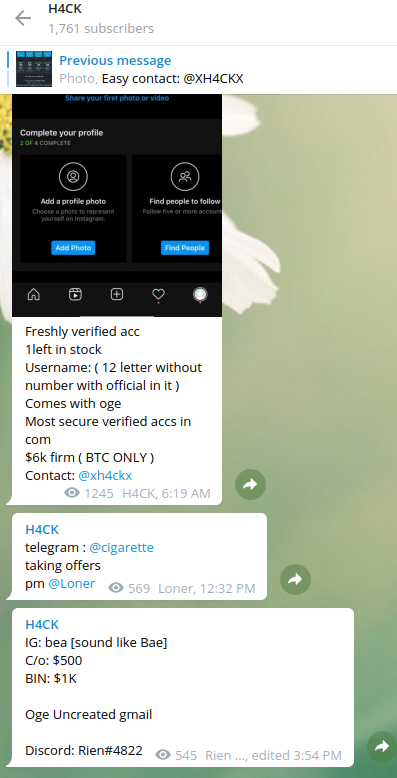
Snippets from the Telegram sales channel for @h4ck, one of the Instagram handles seized by Facebook today.
Facebook said while this is hardly the first time it has reclaimed accounts associated with hijackers, it is the first time it has done so publicly. The company says it has no illusions that this latest enforcement action is going to put a stop to the rampant problem of account hijacking for resale, but views the effort as part of an ongoing strategy to drive up costs for account traffickers, and to educate potential account buyers about the damage inflicted on people whose accounts are hijacked.
In recognition of the scale of the problem, Instagram today rolled out a new feature called “Recently Deleted,” which seeks to help victims undo the damage wrought by an account takeover.
“We know hackers sometimes delete content when they gain access to an account, and until now people had no way of easily getting their photos and videos back,” Instagram explained in a blog post. “Starting today, we will ask people to first verify that they are the rightful account holders when permanently deleting or restoring content from Recently Deleted.”
Facebook wasn’t exaggerating about the hijacking community’s use of extortion and other serious threats to gain control over highly prized usernames. I wish I could get back the many hours spent reading private messages from the OGUsers community, but it is certainly not uncommon for targets to be threatened with swatting attacks, or to have their deeply personal and/or financial information posted publicly online unless they relinquish control over a desired account.
WHAT YOU CAN DO
Any accounts that you value should be secured with a unique and strong password, as well the most robust form of multi-factor authentication available. Usually, this is a mobile app that generates a one-time code, but some sites like Twitter and Facebook now support even more robust options — such as physical security keys.
Whenever possible, avoid opting to receive the second factor via text message or automated phone calls, as these methods are prone to compromise via SIM swapping — a crime that is prevalent among people engaged in stealing social media accounts. SIM swapping involves convincing mobile phone company employees to transfer ownership of the target’s phone number to a device the attackers control.
These precautions are even more important for any email accounts you may have. Sign up with any service online, and it will almost certainly require you to supply an email address. In nearly all cases, the person who is in control of that address can reset the password of any associated services or accounts –merely by requesting a password reset email. Unfortunately, many email providers still let users reset their account passwords by having a link sent via text to the phone number on file for the account.
Most online services require users to supply a mobile phone number when setting up the account, but do not require the number to remain associated with the account after it is established. I advise readers to remove their phone numbers from accounts wherever possible, and to take advantage of a mobile app to generate any one-time codes for multifactor authentication.




Please explain how to use a mobile app to generate one-time codes for multifactor authentication. Generally,The holder of my account sent me a text message with a code that I need to enter. This is what you’re saying doesn’t work. How do I change it to where I generate the code?
Not saying getting your codes via text isn’t possible or doesn’t work, just that it’s not hard to bypass. And if they do sim-swap your number, you’re liable to have even bigger problems for any accounts (including your email) that may allow password resets via text.
Sites that support one-time passwords by mobile app will have one or more mobile apps they support, such as Authy or Google Authenticator. You just go into your settings on the account you wish to secure, look for something that says 2-step or multi-factor authentication, and select the option that’s for mobile app authentication. Usually, the site will have you open the authentication app and scan a QR code on the screen, and then enter the one-time code that shows up in your app. From then on, it may ask for a one-time code generated by your app when you log in, or when it detects you’re logging in from a different computer or device.
I heard a user by the alias “milk” takes part in these heinous crimes, I would like you to crack down on him.
I can’t believe I didn’t make the cut as one of the most reputable people onsite. Your sources must be faulty. https://ogusers.com/Dropset
Hello my name is Emily Miller! I go by @Czmo on Instagram and I’m the biggest scamming female and I didn’t get banned! Too bad bozos.
Goodbye original usernames dot com
https://ogusers.com/Thread-Krebs-on-the-case
this is oh so sinister of these lil jits. as a part time gang member part time stay at home mom I’d like to teach these brats a valued lesson!
who tryna sell me a minecon
For over a week now, when I need to sign in on a Google account, my multifactor ID has been malfunctioning. That occurs while using the latest Firefox browser in Android from Verizon Wireless. I get either the page containing their single #, yet I cannot pull down or otherwise access the page that gives me a choice of numbers to verify. Any phone # you know of to contact Google to get this worked out ? Tnx. Bruce
idk what this is but rip ogusers dot com
Another informative article !
What is that sim swpping is new business in carders world?
Regarding the SIM swapping risk, it should be noted that:
1) you’re really only truly at risk for this as much as you are a specific target, whether you’re moderately famous, or have upset someone, or have a desirable username – some people seem to think they could be part of a broad spraying attack and get hit in this way
2) you should also call out that not every site allows you to do something more secure than traditional SMS/Call, and many carriers allow additional PINs/protection to be set on a line, and everyone should do this – yes there’s still room for your weakest link to be an underpaid and tired support person at the phone company, but it helps
There is no middleman that would implicate big FANG in compliance.
For MFA, are land lines more secure than cell phones, or is there a way to “SIM swap” them, too?
Landline attacks are MUCH harder for an attacker to pull off.
Social engineering is an easy attack against cellular providers, because of how often they have to legitimately port over numbers to new devices. Everyone from the lowest level employee, with maybe a day of training, might have a real need to help real customers port over numbers to a new phone. This presents a huge attack surface ranging from social engineering, bribery of insiders, and the systems used to carry out the actual porting operation.
For landlines, there are the well known attacks of phone wire tapping. And Mitnick made famous by old school attacks against Telecom systems and processes.
But landlines are semi permanent. So procedures for changing numbers, adding new access for internal systems, and the process for legit wire tapping… is MUCH MORE ROBUST.
For enterprise environments, VOIP is largely managed internally. So an attacker could potentially call up the service desk and move a phone line to another VOIP phone by either Ethernet jack port number or MAC address, to something the attacker controls. This would be the equivalent to SIM swapping.
But not many MFA implementations use VOIP landlines for authentication. It is slower for users to listen for a code, but some do allow the user to just press a button on the phone to authenticate.
My Instagram was hacked into and stolen. The hacker is now trying to sell my account. Please tell me who i contact to report the hackers account