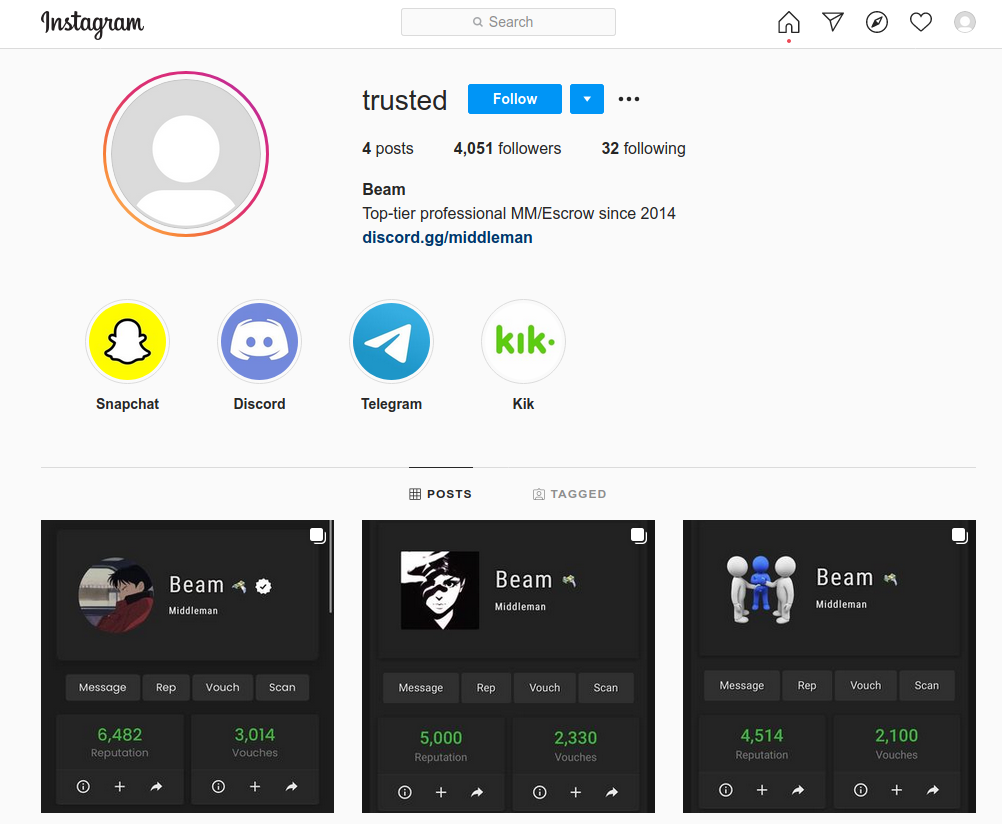
Facebook, Instagram, TikTok and Twitter Target Resellers of Hacked Accounts
Facebook, Instagram, TikTok, and Twitter this week all took steps to crack down on users involved in trafficking hijacked user accounts across their platforms. The coordinated action seized hundreds of accounts the companies say have played a major role in facilitating the trade and often lucrative resale of compromised, highly sought-after usernames.