Apple, Google and Microsoft announced this week they will soon support an approach to authentication that avoids passwords altogether, and instead requires users to merely unlock their smartphones to sign in to websites or online services. Experts say the changes should help defeat many types of phishing attacks and ease the overall password burden on Internet users, but caution that a true passwordless future may still be years away for most websites.
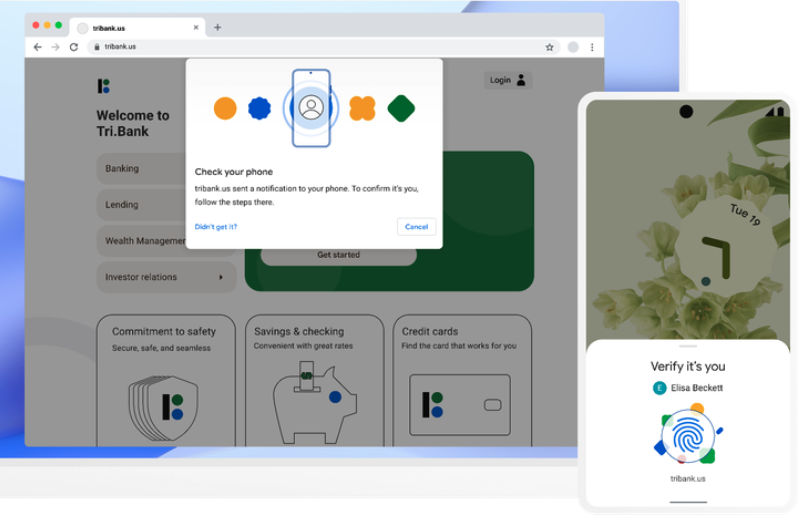
Image: Blog.google
The tech giants are part of an industry-led effort to replace passwords, which are easily forgotten, frequently stolen by malware and phishing schemes, or leaked and sold online in the wake of corporate data breaches.
Apple, Google and Microsoft are some of the more active contributors to a passwordless sign-in standard crafted by the FIDO (“Fast Identity Online”) Alliance and the World Wide Web Consortium (W3C), groups that have been working with hundreds of tech companies over the past decade to develop a new login standard that works the same way across multiple browsers and operating systems.
According to the FIDO Alliance, users will be able to sign in to websites through the same action that they take multiple times each day to unlock their devices — including a device PIN, or a biometric such as a fingerprint or face scan.
“This new approach protects against phishing and sign-in will be radically more secure when compared to passwords and legacy multi-factor technologies such as one-time passcodes sent over SMS,” the alliance wrote on May 5.
Sampath Srinivas, director of security authentication at Google and president of the FIDO Alliance, said that under the new system your phone will store a FIDO credential called a “passkey” which is used to unlock your online account.
“The passkey makes signing in far more secure, as it’s based on public key cryptography and is only shown to your online account when you unlock your phone,” Srinivas wrote. “To sign into a website on your computer, you’ll just need your phone nearby and you’ll simply be prompted to unlock it for access. Once you’ve done this, you won’t need your phone again and you can sign in by just unlocking your computer.”
As ZDNet notes, Apple, Google and Microsoft already support these passwordless standards (e.g. “Sign in with Google”), but users need to sign in at every website to use the passwordless functionality. Under this new system, users will be able to automatically access their passkey on many of their devices — without having to re-enroll every account — and use their mobile device to sign into an app or website on a nearby device.
Johannes Ullrich, dean of research for the SANS Technology Institute, called the announcement “by far the most promising effort to solve the authentication challenge.”
“The most important part of this standard is that it will not require users to buy a new device, but instead they may use devices they already own and know how to use as authenticators,” Ullrich said.
Steve Bellovin, a computer science professor at Columbia University and an early internet researcher and pioneer, called the passwordless effort a “huge advance” in authentication, but said it will take a very long time for many websites to catch up.
Bellovin and others say one potentially tricky scenario in this new passwordless authentication scheme is what happens when someone loses their mobile device, or their phone breaks and they can’t recall their iCloud password.
“I worry about people who can’t afford an extra device, or can’t easily replace a broken or stolen device,” Bellovin said. “I worry about forgotten password recovery for cloud accounts.”
Google says that even if you lose your phone, “your passkeys will securely sync to your new phone from cloud backup, allowing you to pick up right where your old device left off.”
Apple and Microsoft likewise have cloud backup solutions that customers using those platforms could use to recover from a lost mobile device. But Bellovin said much depends on how securely such cloud systems are administered.
“How easy is it to add another device’s public key to an account, without authorization?” Bellovin wondered. “I think their protocols make it impossible, but others disagree.”
Nicholas Weaver, a lecturer at the computer science department at University of California, Berkeley, said websites still have to have some recovery mechanism for the “you lost your phone and your password” scenario, which he described as “a really hard problem to do securely and already one of the biggest weaknesses in our current system.”
“If you forget the password and lose your phone and can recover it, now this is a huge target for attackers,” Weaver said in an email. “If you forget the password and lose your phone and CAN’T, well, now you’ve lost your authorization token that is used for logging in. It is going to have to be the latter. Apple has the infrastructure in place to support it (iCloud keychain), but it is unclear if Google does.”
Even so, he said, the overall FIDO approach has been a great tool for improving both security and usability.
“It is a really, really good step forward, and I’m delighted to see this,” Weaver said. “Taking advantage of the phone’s strong authentication of the phone owner (if you have a decent passcode) is quite nice. And at least for the iPhone you can make this robust even to phone compromise, as it is the secure enclave that would handle this and the secure enclave doesn’t trust the host operating system.”
The tech giants said the new passwordless capabilities will be enabled across Apple, Google and Microsoft platforms “over the course of the coming year.” But experts said it will likely take several more years for smaller web destinations to adopt the technology and ditch passwords altogether.
Recent research shows far too many people still reuse or recycle passwords (modifying the same password slightly), which presents an account takeover risk when those credentials eventually get exposed in a data breach. A report in March from cybersecurity firm SpyCloud found 64 percent of users reuse passwords for multiple accounts, and that 70 percent of credentials compromised in previous breaches are still in use.
A March 2022 white paper on the FIDO approach is available here (PDF). A FAQ on it is here.




And if you don’t have a phone?
There is a good market for dumb phones. These are phones that are just for phone calls and text messages. There is growing resistance to smartphones that are personal tracking devices that grab too much attention time.
That is why I still hang onto my Samsung flip phone. It is digital but not a ‘smart’ phone.
Just because a phone does not have all of those “smart” features…don’t expect that you cannot be tracked.
Cellular communications only works because the internal guts (the HLR systems) of the cellphone carrier networks HAVE TO TRACK where cell phones are located in order to: (1) ring that phone for an incoming call; (2) push a TXT message out to the phone (your phone does not query the network for “Any messages for me?”); (3) verify that your phone is permitted to operate on that carrier’s network. And there may be other features that require carriers to geo-locate your phone.
So when you wonder how it works…that’s how it works and why it has to work that way.
It also explains why in times of an emergency call that your cellular service provider can locate your phone within a certain distance of their towers; it’s a triangulation function.
And NO you cannot turn off your phone’s ability to respond to these network messages because if you did: (1) your phone would not ring, you could not receive an incoming call; (2) you could not receive a TXT message; (3) your carrier might not allow your phone to work on their network.
Just sayin….
I don’t own a cell phone and I do not want one. It’s an expense and a personal privacy invasion tool.
Yubikey or any number of FIDO security keys have the same functionality. This isn’t new.
Very good point, Elizabeth.
Millions of
hearing-impaired / deaf people
don’t even own a cellphone.
And many people
don’t even have one
….simply because they don’t need or want one.
Yet,
all of the above people,
DO have a Bank acct.
Amazing how some marketing people
are out of touch with reality.
Thanks f/ the article Brian!.
Or if you live in a remote area where the only way to get even a minimal signal is to go outside?
At my house, if you want to use a cell phone, you have to go outside and stand in the yard. Sometimes you can get a text message through, but it may take ten or twenty minutes for that.
This doesn’t require any signal on your phone.
Unlike SMS 2FA.
Great point Elizabeth. This seems to be yet another fraud site. The many comments pointing out serious flaws in the imaginary thinking of the technocrats have been erased. At least they left yours.
Thanks, Brian, for giving us some perspective on this. Progress toward a solution to something that’s vexed the connected world for years is exciting indeed!
I’ll be curious to see how well it deals with a suddenly-broken mobile device. Currently, if my phone breaks, I still have access to email, banking, and other time-critical sites via my computer, allowing me time to research and purchase a replacement device in an orderly manner. But if FIDO requires me to buy and re-sync a new device before I can connect to ANYTHING, we might feel rather immense pressure to do so in a matter of hours.
Wouldn’t it seem more prudent to have a “hot backup” mechanism such as, say, designating my spouse’s device as a proxy?
Thanks,
Dave
Just use a password manager and preferably one not using the cloud. A unique long computer generated password for each account. Do not use “Log in with Google”, Facebook, etc. Talk about a single point of failure!
If the system has a recovery scheme, it will be social engineered.
I would go Yubikey before this phone scheme. People who use the Yubikey buy two and keep one locked up for a backup.
I completely agree.
It’s better just to get a separate hardware token like yubikey, which is also FIDO.
This scheme is essentially using your phone’s internal security chip as a FIDO token, which has two benefits. Cost savings and being able to lock the key with a pin or biometric.
As for “do not use ‘Log in with Google’, ‘Log in with Facebook'”, one does not have a choice. If the Facebook security system is hacked (as it was a few years ago), your accounts on sites that accept Facebook logins are also broken. Even if you’ve never used Facebook, your accounts were at risk. Ridiculous “security” system.
Jon
This would enable the government to get total access to all your accounts, they wouldn’t even have to have it in their possession, they could use a Stingray as a middle-man (a device between your phone & a cell tower).
What? This doesn’t even use cell signals.
That’s great…and then you lose your phone. Or it gets stolen. Or something gets hacked server-side.
Oh yes, it’s all encrypted, uh huh.
Still way better than a single factor password. Passwords get lost or stolen, or even guessed. And it’s easier to recognize when your phone is lost or stolen, so you can revoke its credential.
Most passwords get compromised without the user ever knowing until their money is gone.
At least it’s from the usual suspects we know have earned our trust, right? Sheesh.
Good for you. There is a paid schill (above your comment)on here trying to mitigate critical comments.
I’m looking for extra work. Is google or apple hiring shills here?
I think this is a technology best suited for corporate environments, not home owners
It relies on a set of assumptions that the phone will always work, that there will always be a decent signal, that this will not encourage hackers to attack phones even more
This also removes personal autonomy from the individual, by obfuscating the means to secure your life and placing that power in the hands of corporate board rooms
I’m not sure what owning a home has to do with anything.
This authentication method is optional and does not assume you must always have a working phone. There will be other ways to authenticate if your phone is lost.
Although this article does not go into the details, the phone must be in Bluetooth proximity, and does not need a cellular or Wi-Fi signal.
“The FIDO caBLE protocol uses Bluetooth to verify physical proximity and does not depend on Bluetooth security properties for the actual security of the sign-in. Instead, it uses standard cryptographic primitives at the application layer to protect data.”
Any autonomy you think you have over securing your online accounts, is an illusion. This is local authentication and does not rely on another third party storing your credentials. You actually have more control.
Not true. Some sites have switched to exclusive phone access. No phome, no access. I want passwords, with my password manager program, and 40-character passwords
Which sites?
It would be listed here…
https://2fa.directory/
No site would have 0 recovery methods.
My desktops do not have Bluetooth, so they will never be in Bluetooth proximity. The FIDO approach has not been thought out very well for anything but the mainstream cases. I hope it never replaces the other security approaches. Which of course implies that the current crop of vulnerabilities will never go away. By which I mean that the current FIDO effort will not solve the problem.
Jon
Doesn’t sound like you know what FIDO is. It seems new to a lot of people, but it’s been around a lot and well tested.
Using your phone as a FIDO token requires Bluetooth yes. But Yubikey and others use USB and/or NFC. Anyone can get a cheap USB Bluetooth dongle.
Password authentication is the flawed mechanism that needs solutions. This is just one of many.
What if the device you’re using doesn’t have Bluetooth? I build PCs from parts and almost never include bluetooth (or Wifi for that matter) because there’s no need – and it’s a security risk. I just don’t understand why everyone so frightened of cables and so intent on shoveling batteries into landfills? I mean I get the Apple folks, they have to be SO trendy at ALL times and ALWAYS have the NEWEST and BEST thing that APPLE tells them is GOOD, but surely there’s more people in this world than them.
That’s indeed better security.
I don’t know why everyone is thinking that this is some mandatory implementation. It’s not.
If you don’t have bluetooth, don’t want bluetooth. Don’t have a smartphone, don’t want a smartphone. Fine. You don’t have to use this particular optional feature.
This is a option that can save money for people who don’t want to buy new hardware because they probably already have laptops with Bluetooth and a smartphone.
If that’s not you, no problem, use something else.
Not no, but $OBSCENITY no.
A smartphone is a steaming pile of untrustable hardware and software. Using it as an authenticator is about as secure as using “1234” for your password everywhere.
A smartphone is as untrustworthy as your laptop.
Many individuals, especially the elderly and tech illiterates don’t have or want smartphones. What is their solution?
Yubikey
Those people most likely have weak passwords that will get cracked anyway. If you fall into this category, you should simply stay away from technology and continue life in the jungle. Get onboard or get out of the way. Those posting fear of cell phones but are posting to this thread, is nothing but ironic.
I really don’t want to make my phone my Achilles heel. What if I prefer to browse the Internet on my desktop or laptop computer. Or want to user a public computer in a library. Or, or, or….
For something like 95% of the websites, security is not really a big issue. I want good security for my bank, my credit card account, things like that. I don’t care if anyone gets into my CVS account, or my Target account, or my New York Times account, or any of the hundreds of other online accounts (just make sure not to “remember your credit card”). I want to use a hard to guess but simple to remember password for all the myriad of accounts that are not critical.
Personally, I still reject the 2-factor authentication. What if I lose my phone? I don’t even know my phone number by heart, let alone whatever I have set up for data backup and recovery. And who has audited Google’s backup infrastructure? What if Google itself gets hacked?
Really, putting all your eggs in one basket sounds like a horrible idea to me.
Not sure if you’ve misunderstood the technology and why security and privacy advocates are applauding it.
“I want to use a hard to guess but simple to remember password for all the myriad of accounts that are not critical.”
This is the big problem. Computers can guess anything that is easy for a human brain to remember.
Three guesses and you/the hacker are locked out
Unless its an offline attack. Or, like so many online sites, misconfigured to bypass rate limiting or lockouts.
Is nobody worried about the privacy aspects of this? I.e. Microsoft/Google/Apple would now know what websites your signing into and when? Especially if the api is always scanning to see if x site is in the list of compatible sites?
FIDO is offline. Maybe you’re thinking OAuth2 type Single Sign On.
Yeah, ok. That makes sense. I didn’t know that. I need to read up more on FIDO clearly Thanks
The privacy issue is that your cell phone number is now linked to your accounts, for accounts that have no need of it. It’s a step to de-anonomising internet access.
Phone number? No.
That’s not what’s happening.
FIDO tokens are not tied to phone numbers. SMS based 2FA is what requires each site to have your phone number. And this is meant to replace that.
If it’s on your phone it can get your IMEI. Stop being obtuse intentionally.
Yubikey doesn’t need a cheerleader or mascot. It’s fine without you.
Mealy, I suppose it *could grab or use the IMEI number. If they designed it that way. But they did not.
Sounds like your paranoia is just reaching for an excuse. Or, as I suspect, you don’t actually disagree with this technology, rather just jumping on the bandwagon of conspiracy theorists who have flooded this article.
I use USB YubiKeys but this is different. The smart phone doesn’t have to be physically attached to your computer. I haven’t tried wireless YubiKeys yet but even those communicate with your computer in order to authenticate.
I think the new FIDO authenticates through the internet to the website, not through your computer. But I’m not sure. It seems like Google’s authentication through its phone apps, which I don’t like because their apps are notorious for vacuuming user data, which they sell.
One logical countermeasure to defeat this new FIDO is to physically steal the smartphone and force the victim to open it. I don’t carry my USB YubiKey with me but do carry my phone around.
There have already been cases of thieves stealing phones at gun point and demanding the user unlock the phone and enter passwords for various things, I think for Apple ID so the iphone’s FindMy (kill switch) can be disabled. I’ve only very rarely seen such stories in the news but I think they’ll increase if this FIDO takes off.
Also, if government law enforcement in any country can bypass (defeat) a phone’s passcode, they’d be able to log into the user’s accounts. Though after bypassing a passcode they can already do that by resetting passwords at sites and receiving the reset email on the compromised phone.
I suspect sites that offer this FIDO will also offer traditional passwords for a long time. By the time they stop offering that, earth’s habit will have degraded to the point of global extinction and it won’t matter — circa 2027-2030. We’ll see soon enough.
“The FIDO caBLE protocol uses Bluetooth to verify physical proximity and does not depend on Bluetooth security properties for the actual security of the sign-in. Instead, it uses standard cryptographic primitives at the application layer to protect data.”
Before too long it will be your phone and it must have location services turned on. Then any access to places on the internet will require you to disclose where you’re at. Just part of a global tracking effort, and keeps you from using a dumb phone, or borrowing someone else’s (phone, computer, library system, etc) to do something online.
What if you die and your family can’t access important accounts? Is there escrow or something similar?
There’s always backup methods. Print out the recovery codes, put them into a safe or bank deposit box.
Very good point, Elizabeth.
Millions of
hearing-impaired / deaf people
don’t even own a cellphone.
And many people
don’t even have one
….simply because they don’t need or want one.
Yet,
all of the above people,
DO have a Bank acct.
Amazing how some marketing people
are out of touch with reality.
Thanks f/ the article Brian!.
Millions of
hearing-impaired / deaf people
don’t even own a cellphone.
And many people
don’t even have one
….simply because they don’t need or want one.
Yet,
all of the above people,
DO have a Bank acct.
Amazing how some marketing people
are out of touch with reality.
Thanks f/ the article Brian!.
Thanks to everyone who recommended Yubikey—whatever that is. I will look it up.
I have refused to use two-factor log in because if I lose my phone or break it. I will be locked out of everything. I wouldn’t be able to simply log in on my laptop as I can now. A friend of mine lost her phone a month or two ago. It was a total nightmare. She was unable to even lock her phone because of two-factor log ins.
And if it’s stolen? I won’t be able to change the passwords on all my accounts because I wouldn’t have access to my phone.
Or if you live in a remote area where the only way to get even a minimal signal is to go outside?
At my house, if you want to use a cell phone, you have to go outside and stand in the yard. Sometimes you can get a text message through, but it may take ten or twenty minutes for that.
Or if you live in a remote area where the only way to get even a minimal signal is to go outside?
At my house, if you want to use a cell phone, you have to go outside and stand in the yard. Sometimes you can get a text message through, but it may take ten or twenty minutes for that.
I still haven’t seen a description of how this would work for the consumer step by step. So I’m standing at the card reader in the 7-11. First, I get out my phone, right? After that?
How did you find this article?
This is about website authentication, not your credit card purchases.
Apple, Google, Microsoft, Facebook and all the rest of you big shots Great Idea just please don’t
force me into this , I’m perfectly happy with my thirty caracter passwords and if they start
cracking those I can still increase it 65 and by the way none of them will be on your cloud.
Just what I need. Another gubmint back door into my personal life. No thanks!
Wow, the NSA and Mossad want to make the internet even less secure? Why, that sounds like a grand idea!
While this could be a big step forward in terms of security, the fact that it requires compliance from the end user in order to be used. How many people are willing to even use 2FA? Or to actually use secure e2e messaging? If you want someone like my wife to use ANY kind of crypto-voodoo-black magic security methinks Microsmurf,Affel, and Giggle are going to be in for a surprise.
At the beginning, there has to be an initial physical authentication. Assuming the scenario of an iPhone and iCloud, at some point you have to physically authenticate on a device that it belongs to user x to be able to sync relying on that initial physical authentication to iCloud. The method of that initial authentication is immaterial, however it has to be reproducible across a galaxy of devices. Keyboard input is reproducible regardless of brand or manufacturer. Will biometrics be reproducible in the same way across a galaxy of devices? Or imaging? Or whatever they wind up using. It’s hard to visualize a system where the lowest level fallback for authentication isn’t keyboard input, i.e. a password.
I’ve been down the path of a lost 2FA entry in a phone authentication app, and it was such a pain in the butt that I now have two phones, different brands, to help mitigate phone loss in the future. I got off cheap. It was only an eighty dollar lesson…
this is INSANITY. to lock in authentication to the phone? I do NOT WANT to use my phone. I want to use my desktop, log in with my screwy passwords, examples
a!minuet!Sponsors3!a2!Drifter0
a2!Helm0!Averted!an!axle9
An9!airport2!draws8!Its!mind
A!phantom4!Hustles4!a3!turret
i can make them 60 characters long; but some sites LIMIT length !!! NUTS
i use KeePass. I don’t REMEMBER ANY passwords, other than the main logon. it works on my phone, or desktop.
i am not limited to just the phone as login.
TWO-FACTOR authentication as is, is crippled. it ShOULD have multiple available methods, because if a SINGLE REQUIRED method gets locked up (your phone), you are SCREWED. multiple security articles discuss this. and now they are considering RESTRICTING this to phone?
try the IRS site – no phone , can’t get code, wait over 10 days for PIN number by mail – you are screwed.
WHERE to write to contest this ludicrous idea? it am NOT AGAINST using the phone, it does work well, WHEN I HAVE it. BUT, i want an acceptable easy to use alternative, to log in, if i LOST the phone, or it got stolen. I do NOT WANT to ahve to call someone, wait 10 hours on the phone, and do verification.
go ahead and make the alternative, a 5-different-password logon sequence. I can store them in keepass. but i need a way to log on, from desktop, in emergencies, or non-phone-available circumstances, so i can get to my software IN A NORMAL FASHION.
WHRE in the heck to people get these ideas???
I ALREADY WENT through the debacle of ID.ME, and its nefarious rollout by the IRS. DUE to this, i still cannot set up access for my 95 year old mother, to get irs link. and I NEED that link, to check on some problems with tax return, etc, because the IRS is FORCING you to go to that site, for more and more info.
I’m not sure you understand the technology here.
Nobody is forcing this. It is an option and always will be. Just like existing websites using FIDO using a security key (like Yubikey).
https://2fa.directory/
Also, FIDO as a standard, doesn’t know or care if it is a phone or USB key. There is no difference that the server can see.
You can even use the TPM chip in your laptop or desktop as a FIDO token.
Yes, that does mean that if you lose your device, then you will have to go through a recovery process. The IRS process is notoriously bad, but they are the exception, not the rule.
Oh you have an adblocker to prevent tracking ? Try blocking this login prompt telling us exactly who is logging in to which website.
Thankfully there are many astute observers out there. Many concerns are identified and addressed. However, one concern that I see no one has addressed is the absolute control you will give the big “Tech” companies. Most already know and understand the absolute ID theft being conducted by technocrats.
What happens when ‘someone’ wants to shut your key off? I see absolutely no reason to surrender my password functions to big tech under the guise of some FALSE sense of security or extorted “protection.” Aside from the technological failures that are often and rampant, but under reported, many have already noted the dysfunctional aspects of this new scheme by big tech to control more of you. I know many will mindlessly consent to this garbage for convenience. Just remember….. How much is convenience worth to you? To answer this question look at all of the weasel words and legalese all service agreements have.
They literally could switch off a selected group of people from all online passworded activity. They can do that now but they would have to actually commit additional fraud and theft to accomplish it. If you consent to this scam look at the part in the se3rvice agreement where they can do whatever they want, whenever they want, and are held harmless because you signed up for it. 100 bucks says this guy has an article soon where your EV can be monitored and controlled via your pw or made your password device. CA already has legislation where you will have to submit an application to charge your car and to drive your car only after approved route and time are issued to you by the state and you pay the fee for their permission. DO not believe me. Look into it yourself.
Sounds like nut job conspiracy theories.
There are too many actually security professionals here to believe this nonsense. You’re twisted by the media you consume, to automatically hate whatever cabal they seem is evil.
So when technology actually becomes more secure, you are just suspicious. When a lifesaving vaccine is finally available, you are just suspicious. Both come from ignorance.
Learn about the technology, and why security professionals are praising it, before you spew your conspiracies.
You are such a “security professional?” Go ahead. Believe your bs. Anyone so ignorant as to profess technocratic obedience has a demonstrable ignorance of fact and sincerely bereft knowledge of security.
Do as you choose. How you segue into vaccine fantasy is beyond me but seems like you are a gates tard and have a very limited scientific knowledge. You wouldn’t know science and technology if it smacked you in the face so peddle your nonsense elsewhere. Better yet go call Fauci liar and get another vaxx. Get two while you are at it.
Sounds like you have a limited intellect. Good for you the moderators are censoring truth like all of your technocrat scum. Your ignorance is glaringly obvious.
Some paid troll such as JamminJ will try to marginalize any criticism of the garbage they are trying to sell.
when will these sheeple all wake up? This is like the 5G plan and microchipping our children all over again.
I wonder if there is a clear set of assumptions upon which this new technology is based. For example, it seems that desktop users must have a phone. Do those users need to use cloud accounts? I have been avoiding cloud accounts (Google Drive, MS One Drive) for years, assuming that they are one more way to store data that will eventually be compromised. Until the set of assumptions behind this new approachare stated clearly, it is hard to know how to feel about this new technology (which appears to be forced upon us without our consultation or agreement). It may well solve the problem for 90% of users. I fear for the remaining users who are outside the list of assumptions.
Jon
Your fears are unfounded. This is all optional. FIDO has been around a while now. This is just finally using the secure chips on new smartphones as a FIDO device. Yubikeys were the defacto standard for years. This is just allowing people to use hardware that they already have instead of buying a Yubikey.
And no, you don’t need a cloud account. That’s just for seamless syncing across multiple devices. But you’re free to not do that and just manually set up multiple.
JamminJ is a schill. Censoring comments.
“If you forget the password and lose your phone and can’t recover it”
Mum had her phone stolen. Thanks to old age, she didn’t remember password. Deep troubles.
Techies should remember there are people who are not.
That’s a double failure that can easily be avoided.
All the older people i know keep a paper copy of passwords.
This sounds like a weaker version of Steve Gibson’s SQRL (https://www.grc.com/sqrl/sqrl.htm) in which, I think, Gibson and friends have designed answers to some of the issues raised in the article.
I had a look at the FAQ. It looks like if I want to move to a new phone, I would have to update authorizations on every website where I have an account. That’s … quite a hassle. Whereas at the moment if I change phones I don’t have to do anything like that since my passwords are still in my password safe. I hope I’ve misunderstood this aspect?
Yes, that is misunderstood. The keys are synced to other devices.