Apple, Google and Microsoft announced this week they will soon support an approach to authentication that avoids passwords altogether, and instead requires users to merely unlock their smartphones to sign in to websites or online services. Experts say the changes should help defeat many types of phishing attacks and ease the overall password burden on Internet users, but caution that a true passwordless future may still be years away for most websites.
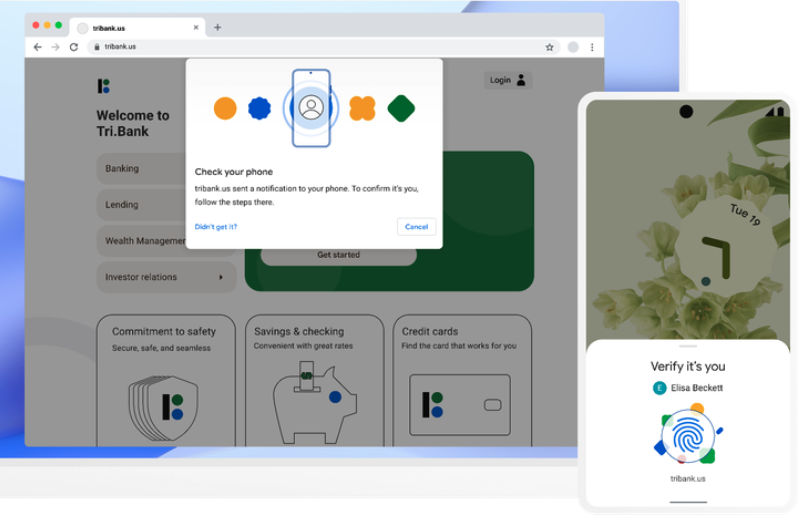
Image: Blog.google
The tech giants are part of an industry-led effort to replace passwords, which are easily forgotten, frequently stolen by malware and phishing schemes, or leaked and sold online in the wake of corporate data breaches.
Apple, Google and Microsoft are some of the more active contributors to a passwordless sign-in standard crafted by the FIDO (“Fast Identity Online”) Alliance and the World Wide Web Consortium (W3C), groups that have been working with hundreds of tech companies over the past decade to develop a new login standard that works the same way across multiple browsers and operating systems.
According to the FIDO Alliance, users will be able to sign in to websites through the same action that they take multiple times each day to unlock their devices — including a device PIN, or a biometric such as a fingerprint or face scan.
“This new approach protects against phishing and sign-in will be radically more secure when compared to passwords and legacy multi-factor technologies such as one-time passcodes sent over SMS,” the alliance wrote on May 5.
Sampath Srinivas, director of security authentication at Google and president of the FIDO Alliance, said that under the new system your phone will store a FIDO credential called a “passkey” which is used to unlock your online account.
“The passkey makes signing in far more secure, as it’s based on public key cryptography and is only shown to your online account when you unlock your phone,” Srinivas wrote. “To sign into a website on your computer, you’ll just need your phone nearby and you’ll simply be prompted to unlock it for access. Once you’ve done this, you won’t need your phone again and you can sign in by just unlocking your computer.”
As ZDNet notes, Apple, Google and Microsoft already support these passwordless standards (e.g. “Sign in with Google”), but users need to sign in at every website to use the passwordless functionality. Under this new system, users will be able to automatically access their passkey on many of their devices — without having to re-enroll every account — and use their mobile device to sign into an app or website on a nearby device.
Johannes Ullrich, dean of research for the SANS Technology Institute, called the announcement “by far the most promising effort to solve the authentication challenge.”
“The most important part of this standard is that it will not require users to buy a new device, but instead they may use devices they already own and know how to use as authenticators,” Ullrich said.
Steve Bellovin, a computer science professor at Columbia University and an early internet researcher and pioneer, called the passwordless effort a “huge advance” in authentication, but said it will take a very long time for many websites to catch up.
Bellovin and others say one potentially tricky scenario in this new passwordless authentication scheme is what happens when someone loses their mobile device, or their phone breaks and they can’t recall their iCloud password.
“I worry about people who can’t afford an extra device, or can’t easily replace a broken or stolen device,” Bellovin said. “I worry about forgotten password recovery for cloud accounts.”
Google says that even if you lose your phone, “your passkeys will securely sync to your new phone from cloud backup, allowing you to pick up right where your old device left off.”
Apple and Microsoft likewise have cloud backup solutions that customers using those platforms could use to recover from a lost mobile device. But Bellovin said much depends on how securely such cloud systems are administered.
“How easy is it to add another device’s public key to an account, without authorization?” Bellovin wondered. “I think their protocols make it impossible, but others disagree.”
Nicholas Weaver, a lecturer at the computer science department at University of California, Berkeley, said websites still have to have some recovery mechanism for the “you lost your phone and your password” scenario, which he described as “a really hard problem to do securely and already one of the biggest weaknesses in our current system.”
“If you forget the password and lose your phone and can recover it, now this is a huge target for attackers,” Weaver said in an email. “If you forget the password and lose your phone and CAN’T, well, now you’ve lost your authorization token that is used for logging in. It is going to have to be the latter. Apple has the infrastructure in place to support it (iCloud keychain), but it is unclear if Google does.”
Even so, he said, the overall FIDO approach has been a great tool for improving both security and usability.
“It is a really, really good step forward, and I’m delighted to see this,” Weaver said. “Taking advantage of the phone’s strong authentication of the phone owner (if you have a decent passcode) is quite nice. And at least for the iPhone you can make this robust even to phone compromise, as it is the secure enclave that would handle this and the secure enclave doesn’t trust the host operating system.”
The tech giants said the new passwordless capabilities will be enabled across Apple, Google and Microsoft platforms “over the course of the coming year.” But experts said it will likely take several more years for smaller web destinations to adopt the technology and ditch passwords altogether.
Recent research shows far too many people still reuse or recycle passwords (modifying the same password slightly), which presents an account takeover risk when those credentials eventually get exposed in a data breach. A report in March from cybersecurity firm SpyCloud found 64 percent of users reuse passwords for multiple accounts, and that 70 percent of credentials compromised in previous breaches are still in use.
A March 2022 white paper on the FIDO approach is available here (PDF). A FAQ on it is here.




Device dependent authentication is subject to failure and as a consequence the necessary reinstatement procedures can be exploited. Device independent authentication that is not subject to device failure is required to secure networks. Password reuse can be defeated by using proprietary tables this also assists with preventing spoofed websites and website links to prevent phishing attacks. Remotely encrypted tables that bypass device tables prevents password stealing malware even if users are induced to click. Using proprietary tables enables the use of simple passwords for ease of access without the loss of underlying complexity for encryption. Incorporating proprietary picture and voice keys can improve accessibility to networks for all types of users without the need to setup complex software and devices as outlined in the system described in this article that lock users into a centralised system that allows users to be tracked that is supported by vendors that are promulgating those devices.
Tracking is the feature according to them.
Can you translate that into English please?
I thought security people were saying for years that passwords alone are the cause of so many account takeovers, and that Multifactor Authentication using secure devices was absolutely needed to secure critical systems. You’re saying the opposite?
Read harder please. It was far more nuanced than your proposed summary.
It’s not that MFA doesn’t do the job, but traditional MFA (push, and especially SMS) have their shortcomings. Password managers are a band-aide for the problem which is utilizing a shared secret as one of the factors. Not to mention the user experience is horrible and costly.
The future is PKI that is user friendly and most importantly user initiated (versus OTP/push). Check out HYPR who is doing this already for google, apple, and Microsoft.
FIDO tokens as MFA is an improvement over those traditional forms of MFA that you mention. Both in security and ease of use. And yes, PKI is the future. FIDO2 uses PKI as well, and it’s seamless so the user is unaware.
Thanks for mentioning HYPR.
They do passwordless authentication using, that’s right, FIDO.
HYPR just uses their own proprietary software on the desktop, on the smartphone, and running in the cloud attached to the webserver.
Basically, it works just like the FIDO implementation described in this article.
But what is the news that this article brings? The adoption of FIDO natively on smartphones using the built in hardware and supported natively by the smartphone manufacturers.
What this means is, as nice as HYPR is…. it is going to be obsolete. Won’t be the first time a startup company with lots of funding and a great product that provides a solution to a problem, goes under because the function became natively supported.
Security solutions that are dependent on solving a problem that exists because of a temporary gap in hardware capabilities, are fleeting because the hardware manufacturers will eventually provide the solution themselves.
So HYPR is good as a software solution, only until the hardware does it natively, which is happening now.
You prognosticate way too frequently.
Excuse me guy, why are you interjecting? Jammin and I were conversing on something and you’re not involved. Go away.
So the future is single factor authentication? Sounds like a step backwards.
Not only that, but a single biometric (e.g. your fingerprint) will be used across all log-in sites!?!
Replace it with an infallible system that only trusted authorities can modify without us knowing.
Trusted. Authorities. Look for the wacky flailing arm inflatable tube guy doing you the big favor.
Phones are multifactor. They require Something You Have (physical possession of the phone itself) and Something You Know (the unlock code) or Something You Are (biometrics)
Brian, may I ask if this article was syndicated elsewhere on some Infowars-type blog?
Because your writing on this article is without flaw, but the comments seem to be flooded by people who are intent on misunderstanding and ignorance, with many going down conspiratorial rabbit holes.
Myths:
1. Smartphones will need persistent Internet access for this to work. Loss of signal would mean inability to authenticate.
FALSE. FIDO using smartphones use Bluetooth LE (caBLE), and are completely functional without Internet.
2. “Big Tech” can now know what you are logging into.
FALSE. Although this uses hardware from Google, Apple and Microsoft… it doesn’t use any additional cloud servers (beyond syncing to other devices if the user wants to). As always, the website provider will know when you log in, as well as all the 3rd parties to whom they sell that data. That’s always been the case though.
3. Losing a smartphone will permanently lock you out.
MOSTLY FALSE. Every website will have a recovery method. The security of that method is the subject of the current debate as many sites have very weak methods that will continue to be abused by attackers. So the entire POINT of secure authentication using a physical device, is losing the devices SHOULD make it much more difficult, precisely because an attacker is going to pretend to be a user who has lost their phone.
4. The government or big tech are going to force you to use this.
FALSE. FIDO has been around for a while. And in every implementation, its been an option to use. Even in secure environments like banking sites, you have to beg and plead the admins to adopt good MFA options to use. This is just another option.
I think its insane so many people here are clinging to single factor, after it has failed us so badly for so many decades. We’ve been fighting for good, usable multifactor for so long.
Maybe the headline spooked them into thinking something nefarious. “your phone may soon replace many of your passwords” could be taken as some ominous threatening scenario that “big tech” is doing something against their will. That people’s “freedom of choice” is being taken away. Even when it’s only optional, people think it won’t be for long. And even when its a good thing, people will think its secretly part of an evil plot.
Vaccines, patches and good security, all get suspicion and accusations.
This is why we can’t have nice things.
“And even when its a good thing, people will think its secretly part of an evil plot.”
Unless completely binary you understand this basic dichotomy of ‘an idea’ vs an
implementation by an untrustworthy source in an adversarial relation to end users.
That which can be described as ‘good’ can often be harnessed for other purposes.
Billed improvements in one area have undermined other concerns historically.
Not all vaccines are equal, not all patches work, not all security ensures privacy.
Not all implementations of all “good” ideas by all actors are equally egalitarian.
It’s one thing to debunk a particular conspiracy theory, another to pretend that
no conspiracies have been sold as “good” ideas by hand-wave pontification before.
Nowhere do I suggest any particualr SMS 2FA implementaion is a “good” solution,
but any suggesting that all implementations of “N” are “good” = crackpots ^(N+y)
That’s a very good point. Ideas versus implementations.
Why is it that so many people commenting here seem to think this is only some new idea?
This is a standard for implementation that’s existed for me, many years now.
Companies are not implementing this basic idea on some whim or using their own implementation standards.
Whole point of the FIDO ALLIANCE is that the security implementation, which is good, is a standard that must be followed.
^ again the declared infallibility of all possible implementations on the flawed basis that the original idea cannot be subverted by any means, in defense of an alternatively motivated actor from a known fallible source, recursively. Next they’ll claim the HTTPS standard infallible also and apple/google/etc “security” companies deserving of blind trust with no caveats possible.
That would be a straw man argument, as no person has suggested infallibility of any kind.
Just “more” secure than existing popular methods of authentication.
FIDO is significantly better since it makes traditional phishing impractical and requires an attacker to perform a much more difficult attack such as Man-in-the-Browser rather than just spoofing a webpage.
You can’t read what you spam here apparently somehow.
You missed the entire point.
Surface analysis.
“Every website will have a recovery method…” – THIS is the scary part. I have had numerous times where CITIBANK thinks i had a fraudulent transaction, or a logon did not work . it takes me FIFTEEN to THIRTY minutes to get the account fixed. I DO NOT HAVE THAT time, inclination, or stamina. There needs to be a Desktop-computer way, to log in, SECURELY, if the phone gets lost. these web sites screw up even the PASSWORD logons, and we are going to rely on them to have an easy recovery method? NOTE, if the phone is LOST or DESTROYED, going through recovery is NOT BECAUSE somebody tried to hack the account and they need to do special verification of you; it is just that YOU do not have what was set up as the ONLY method of login
currently, I use keepass. I generate complex 30 to 60 character passwords. I can use this from my phone, OR from my desktop computer. Heck, have the sites devise a three or four password entry sequence if they want. I could live with that, because i could generate those in my password program, and have them STORED, so i don’thave to remember them; all i do is copy/paste them. whether i paste ONE or FOUR, in sequence, is not a problem.
but GOING THROUGH some robotic or human recovery process is what is scary, and to me unworkable
Your guess is as good as mine, Jammin. I’m a bit in awe of some of the comments here. It’s almost as if they read a different story.
My coworkers have been taking bets on when you’ll disable comments.
Your website is valuable but I’ve never seen anything good in the comments and I’m not sure why I read them.
JamminJ = 75% of all postings gets old quick.
The majority of comments are from the same people, just with different usernames. JamminJ is the only one being consistent and thus being singled out.
It wouldn’t be necessary if some conspiracy loonies didn’t flood the comments here all repeating the same myths.
The more Q-anon conspiracy theorists show up here, the more it becomes apparent that only JamminJ and a few others actually understand the subject here.
Thank you Brian for the great work, and thank you JamminJ for busting the myths from these troglodytes.
(I’ll just point out JJ has made such comments about himself in 3rd person before, obviously.)
My point is that Google does have an authentication process by using your phone. I have been able to log in my account using my phone and yes you need the internet. Microsoft have been using Windows Hello in place of password and I have been able to log in without my password by using the device authentication process. Both works seamlessly.
The current auth process of using your phone that requires the phone to be on the Internet is very different. Phishing is still a big problem, and Google is essentially a “broker” for the authentication. Sounds like OAuth.
This Phone as your FIDO token is completely different, and does not require your phone be connected to the internet. Windows Hello actually uses the laptop’s TPM chip as FIDO to work without Internet. And Windows Hello will also be able to use your phone as the FIDO device if you want it.
You know nothing about this except bullet points you repeat.
Repeated misinformation deserves repeated correction.
All these schemes ignore those at the edge – those who don’t own a smart phone (income issue, disability, age/preference), those who cannot own a smart phone and those who want to use the web but don’t want to participate in the apple or google systems. For many, the portability and shareability of a password is what enables trusted others to manage the online experience of those in their care. Parents with children, caretakers for aged or disabled can set up devices for their charges to use password protected sites, such as youtube, Spotify, facebook or other popular sites. Point is, there will be some number of people needing and wanting access to sites who do not own smart phones.
Readers like yourself ignore the fact that these schemes are optional. Edge cases are not going to be forced.
Pontificating again.
sorry, they ARE forced. Go to the IRS web site. if you aint got a dedicated smart phone, you can’t set up the account to log in.
ONE PERSON, ONE PHONE. and if that phone is gone, it takes you TEN DAYS to get a paper letter with recovery PIN number on it.
I set up an account on IRS.gov, and didn’t need a smartphone.
Don’t know what you’re talking about.
Good for you. There is a paid schill (above your comment)on here trying to mitigate critical comments.
Some paid troll such as JamminJ will try to marginalize any criticism of the garbage they are trying to sell.
Seems if your criticism is too explicit JamminJ will have your comment blocked.
Brian is well aware by now of JJ’s impersonation and trolling of people who see things differently than himself, so don’t automatically confuse the delay in comments being approved on a weekend with being censored for that reason. It is unfortunate that we have to put up with arrogant tinnitus constantly but what do you want for free and anonymous in 2022? Some things aren’t easily fixed without breaking others unfortunately.
So Brian is colluding with JamminJ to censor the truth. He’s no better then. This is a scam site where the technocrats suppress all free speech and only allow deep state sponsored content.
Nobody is censoring you, Jesse. Or should I call you Bodi? Or Nick? Keep having conversations with yourself. The only people I censor are those who accuse me of censorship (which I don’t have time for).
This is Brian’s website, so he’s free to agree with JamminJ’s (mostly basic) points all day.
It’s not collusion nor is it censoring if your comment doesn’t appear for whatever reason.
Brian’s goal is blogging and engagement, not mitigating a particular troll’s egotism issue,
and it’s not really worth his time to investigate JamminJ’s impersonation acting out.
Don’t confuse that with a legitimate first amendment issue, it’s entirely typical stuff.
This seems to be yet another fraud site. The many comments pointing out serious flaws in the imaginary thinking of the technocrats have been erased.
I’ve read through the comments, and it seems only JamminJ’s comments actually contribute anything to the subject. I don’t see that as impersonation or trolling, but as real civil discourse. I do not see you or the other Q-anon comment actually contributing anything but accusations.
” I don’t see that as impersonation ”
-Because that’s not what’s being referred to, most likely your reading is missing a step or twelve.
Can someone help me understand? This is the exact same thing as using a secure password manager on your phone and it solves the exact same problems while creating the exact same problems. So exactly as (in)effective.
I don’t get the point of it.
Phishing attacks work on even strong passwords. They won’t work on this.
My son’s face unlocks my phone and my wife’s phone. What about identical twins? Won’t these cases cause major problems for the stated methodology?
The authentication your phone uses is irrelevant. You could turn off FaceID on your phone and revert to a pass code if you are concerned about specific scenario.
Frankly, you shouldn’t use Biometrics as an authentication method. It exists, but as you’ve discovered, it’s incredibly insecure.
Most likely if you’ve enabled facial recognition your face can be used to unlock your phone if you’re drugged.
A password is something you know and can choose to disclose or choose not to disclose. And to date (although not necessarily going forward given the current Supreme Court) you can’t be legally compelled (by govs in the US) to reveal a password. You can be compelled to give DNA, fingerprints, and a face — not to mention that you’re constantly shedding all three.
Unlocking a phone w/ a password/passcode (and maybe swipe — although there are questions about it) is going to be about as secure as you’re going to get. The phone is something you have, the passcode is something you know (and willingly choose to disclose). Using that object to then unlock other sites (and not relying on internet access for the phone) is pretty good.
Yes, a phone can be compromised (but, again, you could be drugged), and if that happens, you’re probably in trouble — note that the major phone vendors have a financial interest in preventing this, so they’ll fight hard to protect against this (both in court and in software/hardware). The App Stores will scan for problems, the phones will scan for problems. Their lawyers will fight against intrusions too.
Two obvious questions. Does adoption depend on OS version and what about Linux?
I will not give up the authority over my logins to some company. What if I decide to have a phone without Android or IOS? What if I decide not to have a phone at all? Phones break, I have been there. Phones get stolen, I have been there. Yes, people are stupid and ignorant about their passwords, but taking the responsibility away from them does not solve this problem. It makes them even more ignorant and dependent on some big corporations.
Yep
This is all part of the globalist one world,one government,one religion plan. You can find all the details at the World Economic Forum,the World Government summit 2022. The United Nations :U.N.agenda 21 and agenda 2030. They openly talk about this stuff all the time. Take your heads out of the sand,cause if you think this is a good idea you will one day realize its not
How do you get from using a mobile device (via public key cryptography) to authenticate log ins to a globalist one world, one government, one religion plan?
QUESTION, where are all the comments? (including mine) – were they deleted – it states “83 thoughts on this….” b ut i only see about 12 comments/thoughts/etc?
QUESTION, where are all the comments? (including mine) – were they deleted – it states “83 thoughts on this….” b ut i only see about 12 comments/thoughts/etc?
Great point Nick. This seems to be yet another fraud site. The many comments pointing out serious flaws in the imaginary thinking of the technocrats have been erased. At least they left yours.
Learn to use this site: find the link to “Older comments” and all the rest of the comments will magically appear.
I know many people who use short, easy to guess passwords because they were forced to provide a user name and password to access a blog or newsletter that had no legitimate reason to positively identify them. There is not nearly enough discussion about how to ensure companies do not have enough information to link your internet use on their one site with everything else you do.
I use a local password manager and 2FA where allowed without giving up my personal phone number. I don’t want to give it out before we have effective laws that would prevent providers from using it for advertising or spilling it in their inevitable breaches without accepting liability.
I really don’t want companies using my phone number or other device ID to link everything together in one massive dossier. I guess we can give that job to Equifax, eh?
My Win laptop has a perfectly good fingerprint reader. Why force me to use my phone to authenticate??
Nobody is forcing this. You have to opt in.
At this point. Of course google would never force anything on users, no sir!
If your laptop has a compliant TPM you can use that reader with any FIDO compliant website.
this stuff interoperates pretty well.
when will you all wake up sheeple? This is like the 5G plan and microchipping our children all over again.
There are still some people not “leashed” to their phones. I have four PCs and a iPod Touch. It is NOT convenient to have the phone near them at all times. I hope alternate arrangements are available.
This is the alternate. You have to opt in, it won’t be default or mandatory. It’s all in the article, pls read.
If the solution is properly FIDO compliant you can use a USB device like the open source Solo key or the more popular yubikeys.
Also, there’s a good chance that your iPod touch will work since the ‘your phone’ mentioned in the article can be anything with a bluetooth radio and FIDO chip in it.
Brian, I am not grasping the details of this plan. Will this entail installing some sort of token generator app on the phone that will then generate a code that must agree to the website’s code? This is what my bank uses and it is very bulletproof — only if someone physically had my phone AND forced me to enter my PIN for the app could they access the one-time code, which expires in 30 seconds.
Or is it some other technology? Can you elaborate on this? Thanks.
https://fidoalliance.org/faqs/#multi-device-fido-credentials
The simple answer is that SMS OTP better than no 2FA, but poor. OTP using an authenticator app is good. And FIDO2 keys are best.
The security from an unknown attacker trying to guess or spoof your identity is about the same.
However, the real benefit of FIDO over an OTP app, is the anti phishing feature.
Phishing OTP codes are becoming very popular. Many fake login sites now dynamically prompt for OTP codes. And people are falling for it just like those single factor phishing sites.
With FIDO, there’s kind of a mutual authentication going on, well specifically credentials are “scoped”. Only the real site can get the right key from the FIDO token. Spoofing doesn’t work anymore.
https://community.ibm.com/community/user/security/blogs/shane-weeden1/2021/12/08/what-makes-fido-and-webauthn-phishing-resistent
… and what happens when your biometric information is leaked or stolen?
Can’t generate new finger prints and a face within any reasonable cost.
Additionally, biometric information is still 1s and 0s that are going through human input devices, which means that it can be copied, used multiple times, stored, 3D printed, you name it.
You can pay for someone’s data from the middle of no where and keep feeding that into a tampered device.
Indeed. I’ve been victim to the OPM breach, so I know. I don’t use biometrics for anything too important.
All the big companies follow NIST standards for biometrics. Which means they don’t export the biometric data to be used on other devices. Which is why you must enroll on each and every device you use. Not exporting it, is good for security.
From what I understand, the data stored from biometrics is uniquely bound to that single device, such that stealing the data alone won’t work on other devices. Which is why hackers need an actual image of the original fingerprint/face.
I don’t know of any dark web marketplace for biometrics. Perhaps Brian would report if that were a thing.
“So I know” no, you don’t.
In short, phishing is still a big problem even with OTP based 2FA, but it’s essentially solved using FIDO…
“FIDO authentication is considered phishing resistant because the decision about whether a particular scoped credential may be used and the results shared with a server endpoint is delegated to security mechanisms within a trusted computer program such as the browser rather than the human having to visually recognise a phishing attempt themselves”
^ conflates x-resistant with x-proof quite blatantly and deliberately as if phishing is solved now, smh.
Nobody said 100% proof. It’s always good to hedge by saying resistant.
But as of 2022, nobody has successfully phished FIDO using traditional means of phishing. Feel free to show an example to prove that wrong.
Closest thing I’ve seen in breaking FIDO has been man in the browser attacks, which is very different and significantly harder to pull off.
“but it’s essentially solved” and I’ll just omit the aspects that aren’t while I repeatedly cheerlead for something I’m not actually analyzing the implications of in any actual way.
Security analysis doesn’t require propagandists. Take five, take a walk.
Yes, phishing is essentially solved.
Do you have any example of a FIDO authentication being phished?
And I don’t omit the aspects that remain a vulnerability, such as the man in the browser attack. Should be understood that it’s a much more difficult attack to pull off compared to fishing with a spoofed website login page.
One of the big problems in security is that there are not enough people explaining it. Brian Krebs does a great job but it does not help when people don’t read the actual article and just overreact to the headline.
You do a disservice to security when you pile onto Mass Hysteria. People are now thinking that secure authentication is somehow bad for you and wanting to stick with passwords. It’s insane.
FIDO is clearly strong and increases the complexity of the attack required to be executed by the attacker.
This is definitely a benefit to the industry and many. It should reduce the amount of successful phishing attacks by 90% (where the organisations use static password and or sms otp currently)
Ultimately you are signing the session so as long as the user meant to take the action of starting a session with their FI then they’re good. It reduces the possibility of malware present on a users device from harvesting an OTP (sent by SMS or generated in an APP) from being relayed to an attackers device. Or a user providing this to someone socially engineering them over the phone.
However
If the user does not mean to:
– Establish a session on their machine (numerous videos covering this with Jim Browning) where they are behind team viewer or they change the content of what a user sees on their account
– Is coerced into thinking (via social engineering) that they should allow access by mobile or YubiKey
– Is coerced into thinking they should make a payment (via social engineering) by mobile or YubiKey.
Then the attacker is in control.
The issue is context.
– What did the user want to do?
– What does the user expect to happen next?
– What are they actually signing?
– Do they understand they cannot undo what they are doing?
None of this is solved with FIDO, hence the need for dynamic linking to show to the user what they are actually doing and that the signature is generated on the action that they want to take. I.e. you want to take this action, on this device, with this implications. Are you sure?
Even this is fallible to invoice fraud, fake services, advanced vishing. Hence it is an area of research requiring more study.
Ultimately, we need to allow users to understand that they need to have context, pause, reflect and give them the capability to immediately revoke access. The problem with the approach taken by many FI’s is that it is all or nothing.
i.e.
– You approve a login, then realize you shouldn’t have. Tough they’re in.
– You approved a beneficiary creation, then realize you shouldn’t have. Tough it’s trusted and a payment will happen
– You approved an instant transfer, then realize you shouldn’t. Tough the money left your account.
FI’s have the capability to recognize unusual beneficiaries, countries, amounts, currencies etc.. Why do they still execute an instant transfer?
I wonder if a different disputable transfer system where this is the case that allows a user to call and revoke what they did. i.e. rather than instant transfer, under certain conditions a holding agreement (by both FI’s) that allows a reversal.
I would argue a transfer is not actually agreed until the user, beneficiary, sender bank and recipient bank all agree on the transfer. AND anyone can remove approval at any point. Clearly this is not the current approach and should change. We can do better.
Yes, thank you. Finally someone in the biz who knows this stuff is chiming in.
FIDO, for all its benefits, IS NOT A PANACEA. Yes. That point needs to be understood.
The problem I see here, is that people who don’t understand it want to take things to the extreme. On one end, this is some conspiracy to steal their private data and this is no better than their single factor passwords. On the other end, they craft a straw man by saying that advocates for better security are making claims that the technology is “infallible”.
The reality is the nuanced and moderate. That this technology is better than the existing, but won’t solve everything.
I’m also a fan of Browning, and just finished the latest series with Mark Rober. That really does highlight the “higher bar” that hackers must reach when they are deprived of simple phishing. If phishing for authentication no longer works, they have to raise their game and raise the stakes of being caught significantly. Phishing works on all kinds of victims, while the advanced social engineering needed to have victims install Teamviewer (and get around country anti-fraud protections) really reduces the population of likely victims.
With FIDO2, authentication becomes a much bigger hurdle. So as you point out, the next step is to attack the session (victim already logged in). This is where the Man-in-the-Browser attack becomes relevant as well other implanted malware and the Remote Access social engineering campaign.
Regarding the “approve to login”, which is phishable, that is a feature of Push MFA apps like Duo, RSA, and others. But FIDO doesn’t work that way. An attacker cannot send a “approve to login” to a FIDO phone. They would have to be “on the local device already” using malware such as Man-in-the-Browser, or Remote Teamviewer. This is because FIDO using a smartphone uses Bluetooth LE. And the user also does have “context” to know where the prompt is coming from.
Regarding FI’s wanting a “all or nothing approach”, I agree. There is a never ending fight between IAM/security and the business units wanting to simplify to the point it opens up vulnerabilities. That’s a fight I’m in daily.
And you make a great point about having “step-up” authentication where FIDO or other approval steps are prompted based on the risk level of the transactions, not just the initial login. That’s a bit advanced for some FI’s, but many are working on just that approach.
We certainly CAN DO BETTER.
Exactly @JamminJ Agreed!
“Regarding the “approve to login”, which is phishable, that is a feature of Push MFA apps like Duo, RSA, and others. But FIDO doesn’t work that way. An attacker cannot send a “approve to login” to a FIDO phone. They would have to be “on the local device already” using malware such as Man-in-the-Browser, or Remote Teamviewer. This is because FIDO using a smartphone uses Bluetooth LE. And the user also does have “context” to know where the prompt is coming from.”
Yes studies done have found that users simply know they have to follow an authentication process, which at times can be stressful to them. It can be quite confusing / using technology / processes they don’t understand. So they just approve it and they are somewhat disconnected from what that authentication is actually doing.
A great example of that was the SSO spamming on an msft contractor / okta by Lapsus$. Generally due to noise from applications generating random SSO’s, people become so used to getting popups that they simply authenticate. No context, this is crucial on push notifications. These attacks are successful with tech savvy people.
FIDO is still vulnerable to social engineering.
If the user is under stress / coerced they will likely do what they can to reduce the stress / help someone. If that means they authenticate on their local device, connect a hardware authenticator etc.. they will do it. That stress is easily generated by attacking Maslow’s hierarchy of needs, typically the feeling of safety being targeted.
Also, as you mentioned on the Browning videos, many times the bank is on the phone with the victim but the attacker is more convincing.
There are accounts of numerous fraud teams saying their customer hangs up the phone and executes the payment.
Some fraud teams have the capability to put the session into “read only mode” if they catch it in time and can monitor the real time session. This way the user doesn’t actually execute the payment but they think they have, as does the attacker. Then they are able to help the victim to recover their account.
My view here is there is a need for a secure communication channel between the FI’s and their users. i.e. We know that sms, social media, phone, email etc.. can and will be spoofed.
Is there a way to setup a secure communication channel between the FI and user. Similar to the known trusted prior approach. i.e. go to the branch and speak with an agent. It could be helpful, however I am mindful that may make people more susceptible to vishing. Hence more research needed.
I think FI’s need to do better. The sender bank knows the amount is unusual, the beneficiary is unusual, the destination country is unusual etc.. Given the sender bank can identify some form of risk with the payment they should be able to inject a message meaning that it is known as risky and held in the beneficiary bank. They could also flag in bold and red to the user everything that is unusual and ask them to pause and reflect on what they are doing.
The beneficiary bank should be looking for common signs of whether the account it is being transferred to is a mule account. I.e. warm up account (dormant to activity), transfer value in > than stated profile, age of person (student mule), time with bank, device fingerprints, ip’s, cookies etc… from interactions.
Because the authentication, user, sender bank, beneficiary bank risks are treated in isolation and decoupled it leaves the victim as the person responsible for understanding and signing the payment, and expected to have an experts knowledge on financial cybercrime / be invulnerable to social engineering.
Hence no silver bullet, but, FIDO is a great step forwards to increase the complexity of attacks and secure the vast majority of users.
Also 75bn data points breached in 3 years. If you use: user, static credential, email accounts, KBA etc.. to onboard, login or recover a user you must know a population of users are vulnerable to account takeover.
An FI’s user security is like the security of a castle. They are only as strong as their weakest point. Many times that weakest point is the onboarding / recovery process if we ignore the user.
Typically the recovery / onboarding process is in the hands of an email provider or telco, where MFA isn’t applied and the FI has no control.
The FI should look to take back control and own that onboarding / recovery process. eIDAS or equivalent may help there.
A pleasure talking with you btw.
Oh, another thing I wanted to say because you got me thinking of the scam busting that Jim Browning does.
No matter how good the authentication method, how robust the session tracking, how diligent the fraud detection a bank may have… if a victim submits fully to a scammer, doing everything they say… it’s game over, they are pwned.
Once the victim is pwned like this, not even the fraud team can stop the scam. Jim Browning shows this time and again with the refund scam. The scammers bypass the fraud team’s analysis, because they don’t get the victim to wire money, instead they just spoof a transaction in the local browser, to make it look like an overpayment, and then tell their victim to go withdraw cash and send via the mail.
It works because it bypasses all technical controls like authentication and pwns the victim directly.
Exactly!
Many times the victim also realizes within 10 minutes too, but by then it is too late.
Hence why I think we need to setup legal dispute / different flags / processes for transactions of risk. Not all transfers are created equally, yet we treat them the same.
But it’s not a flaw in FIDO, to be bypassed this way. And should not reflect badly or cause suspicion or hesitation on using this stronger authentication method just because it can’t fix everything 100% (especially the human element). Don’t let the perfect be the enemy of the good.
100% agree
Of course user tracking is the point of FIDO2. Without knowing anything from the protocol details, that much should be obvious simply from looking at who’s pushing it. It appears to me that the game is for the smartphone OS giants (e.g., Google, Apple) to collude with website operators (e.g., Google, Microsoft), to correlate smartphones to website accounts by reconciling pairs of “smartphone model, access time” data points that are available to both the website and the smartphone OS, and then snarf all the secondary correlations thus implied. That the spec requires the smartphone’s model be conveyed to the website strikes me as a dead giveaway here. The tracking implications are obvious, and I cannot think of a legitimate reason for the spec to include this. (Note that the authenticator app itself may be completely honest, because the smartphone OS can see when you used the app without peeking inside it.)
JamminJ’s claim to the contrary is deeply disingenuous. While it’s true that the smartphone doesn’t contact an additional cloud server, the implication that tracking requires an additional server contact is utterly false. Likewise, while it’s true that website operators selling your data isn’t new, it totally elides the fact that the ability to correlate your smartphone to your website account using that data is new.
“Without knowing anything from the protocol details”
That’s the most important thing you said so far.
You don’t know anything about the protocol, and sounds like you refuse to learn about it.
The phone model and os is only conveyed to the website seeking authentication, and that communication happens over Bluetooth LE. It does not send the name of the website to Google cloud services, so there’s no correlating those two bits of information.
Why would the authenticating website need to know the make and model of your smartphone? Because it needs to be able to enforce a policy of minimum security.
The website administrators trying to secure their website, probably don’t want a 12-year-old Android, with no phone locking capability to be considered a Fido token.
This Mass hysteria is driven by the ignorance you begin to admit. It’s not rocket science, it’s actually possible for you to learn more about it and that will alleviate your fears and conspiracies.
Meh, if you’ve ever used your mobile phone web browser or an app for the website/service…. they already have that information. Nobody cares about keeping that secret, otherwise they would never even use a smartphone.
i disagree with giving corporations access to all authethentication. 100 per cent, is a bad idea. Imagine abuse and control of that access. No thanks and no way! Imagine the databreaches of the future! Violates every security principle!
That’s not what’s happening here. Please read the article.
This is not giving corporations more access to your authentication. Even though Google made the authenticator app, it’s not connected to their systems and they have no control or knowledge of the OTP codes you put in there. This is the same. Although they make the hardware for the chip in the phone, they have no access nor knowledge of the pass keys inside.
Those of us who work in areas that prohibit personal electronic devices are not wild about smartphone-based authentication. Let us hope Apple, Google, Microsoft, etc. remember that devices like the Yubikey also support FIDO.
Yes, you notice that many of them have RSA OTP hardware tokens dangling from their badge lanyard.
It’s basically a trade-off between expense and convenience.
Those tokens are generally $50 or more. But often worth it in order to ensure there’s no operating system that could be corrupted.
I keep reading about the war in Ukraine. My understanding that Russian invaders as they are looking for partisans in the captured territory setup checkpoints and demand at gunpoint to unlock phones so they can inspect digital content. If this technology is implemented, you just gave anyone who can coerce a user to unlock a phone a lot more access to all digital assets. This will only benefit dictators, invaders, and abusive law enforcement.
This certainly sounds like a step backwards. On the face of it, how many people even have a pin to lock their phone much less gone through the trouble of setting up biometrics? But assuming they have, and setup a fairly complex pin, even if it is single factor… Then at minimum, the question of remotely obtaining or guessing someones password vaporizes. To access their accounts you’d have to physically steal their phone AND crack its pin before the end user can replace it. Or alternately, compromise the account via recovery options. The latter I don’t see there being much of a way around. But the former, that does sound like a step up. We’ve already heard of various ways account access can be compromised even with MFA. Its harder, but the attacker doesn’t have to get close to the target. These proposals would mitigate that considerably, at least until someone figures out a way to obtain the token data via some kind of malware.
I’d much rather get a Yubikey or RSA device. If I got mugged, they’d take my wallet and phone but probably not bother with a dedicated 2FA device. And when they take my phone now they’re in all my accounts. No thanks.
I do the same thing too.
Even better, there’s very little need to carry a USB security key in any situation where mugging is a significant risk.
Most accounts that people have, stay logged in with cookies stored on their device. Should be considered low security logins. For important ones like banking, should be locked with two-factor, with one factor being the security key and the other being a knowledge Factor like a password.
In practice, a bank should not use passwordless authentication using just a phone. So adopting this Fido on a phone technology, would be in a two-factor implementation.
In essence it’s very strong and losing the phone to a mugger is only one factor. And very likely they will still need a PIN or biometric to unlock the key on the phone.
Set up correctly, this could be three factors of authentication.
Type in a long password into the website, prompts you for phone unlock, which is the second factor of having a physical device, then you unlock the phone with a biometric.
Sounds like this solution encourages violent crime. When you’re mugged, they will take your phone and your finger. I’ll stick with passwords.
Haha…. that’s the most creative defense of poor security practices I’ve seen yet. Thank you.
You could also use face recognition.
Or maybe Castor Troy will mug you and take your…. face…. off
You sound ridiculous.
It is going to be absolutely hilarious when one of these three suffer a massive data breach or it becomes ubiquitous enough for smaller parties to implement it with leaks and people need to, “reset their identities.”
Industry will drive towards the most profitable authentication method, the most trackable tech, because they are driven by profit.
Government will drive toward the most control, as it has lost its way from protecting people, to protecting cooperate interest.
This future is now.
I kind of agree with you here.
Just normal capitalism that work though.
And that explains why companies won’t really push this. The big tech companies are offering this because they do have good security engineers working,… So we’ll get a few articles trying to explain it to the people.
But you’ll never see a huge corporate investment and marketing campaign driving people toward it because it’s not profitable.
FIDO it’s good security and among the best we have. It’s been around for many many years, and people still don’t understand it because it’s not being marketed.
OAuth2.0 is the most profitable and least private form of authentication. “login with Facebook” for example.
It’s single sign on and uses the big tech companies as the broker. But it disproves your implication that companies would force its use. They have indeed encouraged its use, but its never been forced, in all its years.
So here is the BIG question. I don’t own a cell phone, how is this going to help me? Asking me to purchase one will not happen either as I don’t need a phone in my ear or my eyes 24/5/365. You need to call I have LL that I use all the time.
It is indeed a big question that nobody seems to want an answer to.
Anyone looking for the answer to this question can simply read the article and learn more.
The answer is it’s not going to help you, you don’t need to, it’s all optional.
You can still use the same secure authentication technology by buying a $40 USB hardware key.
This is a very practical question. As the responsible son taking care of an elderly parent, it is virtually impossible to help him manage his affairs in a world that requires a mobile device for everything and expects a pretty decent level of tech savvy just to get logged in. I DREAD the continue march toward this while I am helping out my parent, but being in InfoSec and being aware of what’s going on in the world, I know it really is needed. But still, these companies don’t do near enough to help their ‘edge case’ users participate without a lot of pain.
Side note, RE the whole topic of being able to recover, I had to reset my iPhone then just replaced it and in neither scenario did Microsoft Authenticator’s recovery process work. Google Authenticator was a cinch. I’m not enthused about my ability to recover when needed when it comes to MS.
I also help out my elderly parents with this stuff.
I actually think multifactor works better when I can be the daughter that can prevent scams and phishing.
Now, they need me to be an extra set of eyes to make sure they aren’t being scammed. I can be their approving authority.
Edge cases like ours do need to be addressed. Often that is done by just allowing single factor passwords. That is fine for 99% of the websites. But for the 1%, like online banking, I am glad they continue to march towards security. I can help where I can, even to recover, but without multifactor they are much more likely to be scammed.
We’ve selected Authy.
It’s possible to have the same Authy account tied to multiple devices, so you could add it to their device and pair it to your device, or you could install a copy of authy on your computer and pair their device to your computer, while using a different Authy account on your phone for your own purposes.
The security of Authy is arguably weaker than Google Authenticator’s as it allows this. And it allows one to regain access to an account using a backup password (which you should store in a bank vault).
We specifically found Microsoft Authenticator’s confusing Work vs Personal accounts a real pain point in addition to everything else. (The small benefit of fancier logins to MS sites really wasn’t worth anything.)
But, the ability to have multiple devices that share 2FA codes is valuable and a risk I’m willing to take.
I have to trust that if someone actively tries to brute force my recovery password that Authy will do something.
https://support.authy.com/hc/en-us/articles/360036077534-What-is-a-Backup-Password-Can-it-be-recovered-
1. What about those of us who have flip phones and landlines? Those of us who would rather *not* be tracked and geolocated (or who spend far too much of every day in front of a computer, and don’t need a hand-held to spend more time on it?)
2. How soon will we see faked SMS messages for you to click on a link… that’s there to steal your login?
3. What about people with dreadful or non-existent signal?
4. And M$ – what about if you’re offline, how do you log on (oh, I know, they want everything to be rented as SaaS, so this is not a consideration of you logging onto your own system).
1. Don’t need to opt into this option. Or you can use a USB security key.
2. This doesn’t use SMS, so a hacker cannot login by sending a spoofed SMS message.
3. No cellular signal is needed. The phone does not need to connect to the Internet for this to work. It’s offline.
4. If you’re talking about Windows Hello, it already works offline.
Biometrics is far from perfect. Face scans utterly failed here in AZ, and also for the SSA. Smartphones are *far* from safe for just about anything… What about requiring/permitting (perhaps redundant) YUBI tokens instead?
Any website that can use Phone as FIDO, can also use Yubikeys as FIDO too. It is all optional. If you don’t lock your phone with biometrics, it’ll still work if you use a PIN/Password.