
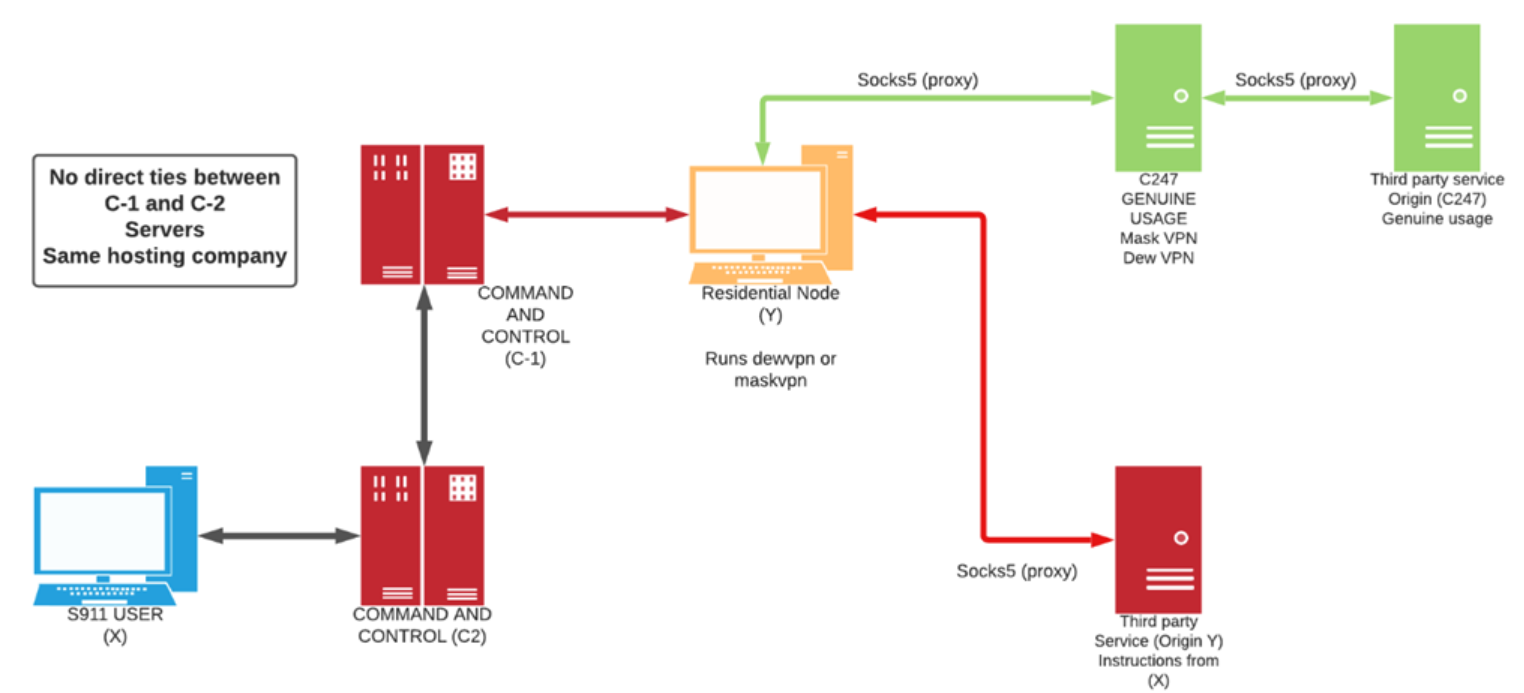
The 911 service as it exists today.
For the past seven years, an online service known as 911 has sold access to hundreds of thousands of Microsoft Windows computers daily, allowing customers to route their Internet traffic through PCs in virtually any country or city around the globe — but predominantly in the United States. 911 says its network is made up entirely of users who voluntarily install its “free VPN” software. But new research shows the proxy service has a long history of purchasing installations via shady “pay-per-install” affiliate marketing schemes, some of which 911 operated on its own.
911[.]re is one of the original “residential proxy” networks, which allow someone to rent a residential IP address to use as a relay for his/her Internet communications, providing anonymity and the advantage of being perceived as a residential user surfing the web.
From a website’s perspective, the IP traffic of a residential proxy network user appears to originate from the rented residential IP address, not from the proxy service customer. These services can be used in a legitimate manner for several business purposes — such as price comparisons or sales intelligence — but they are massively abused for hiding cybercrime activity because they can make it difficult to trace malicious traffic to its original source.
Residential proxy services are often marketed to people seeking the ability to evade country-specific blocking by the major movie and media streaming providers. But some of them — like 911 — build their networks in part by offering “free VPN” or “free proxy” services that are powered by software which turns the user’s PC into a traffic relay for other users. In this scenario, users indeed get to use a free VPN service, but they are often unaware that doing so will turn their computer into a proxy that lets others use their Internet address to transact online.
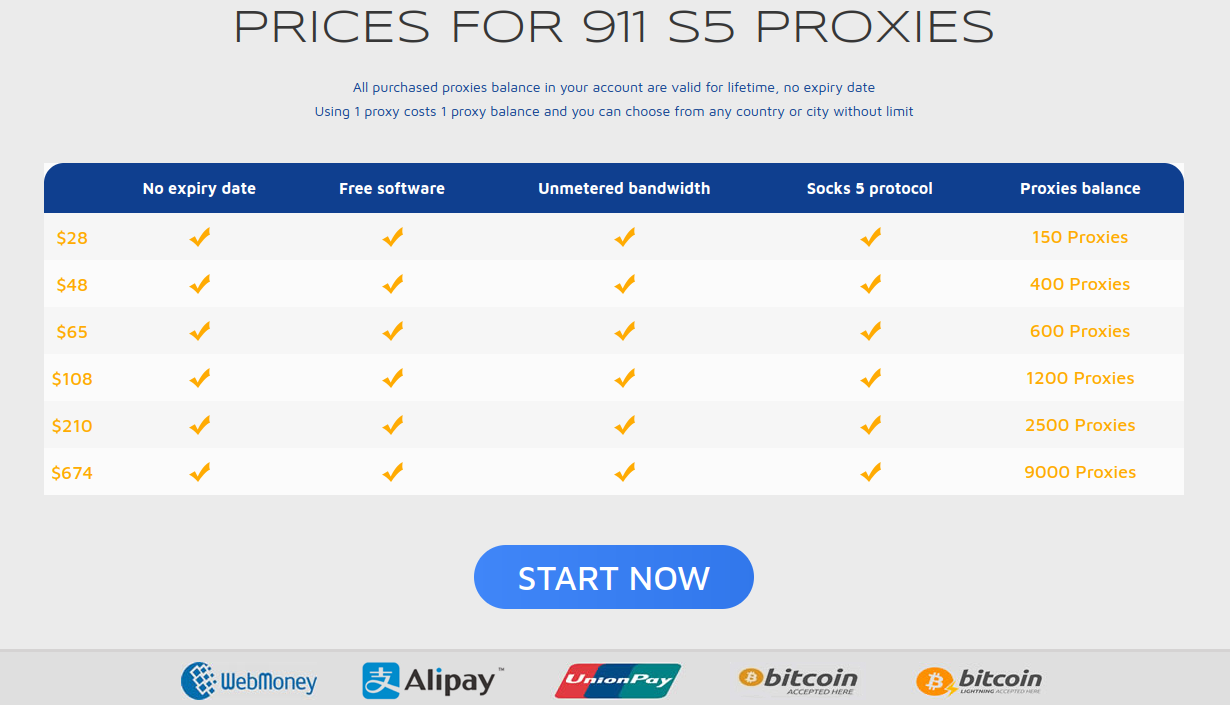
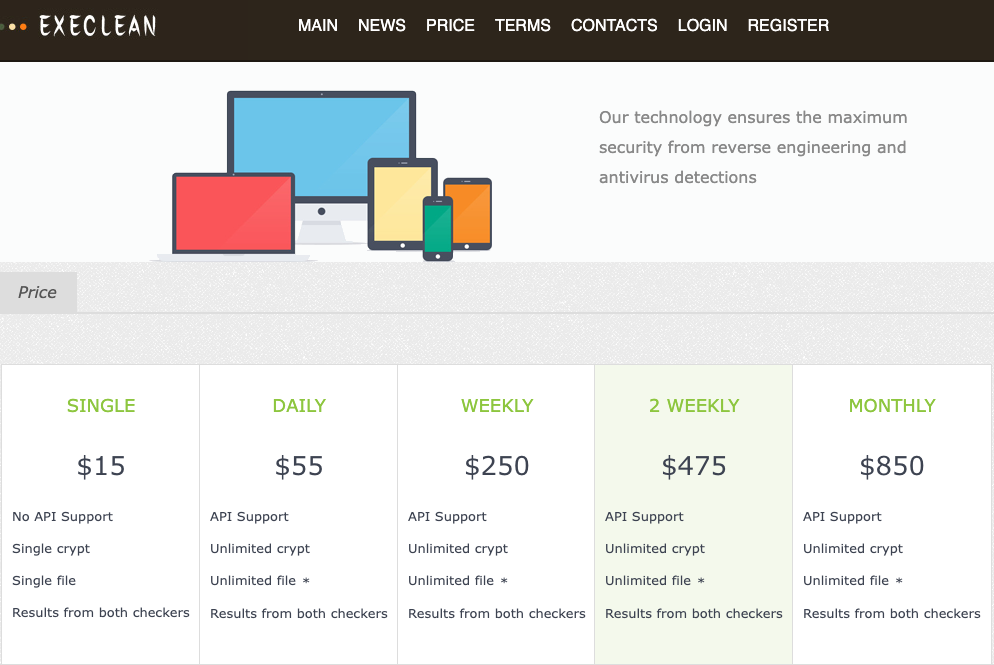
The current prices for 911’s proxies.
Researchers at the University of Sherbrooke in Canada recently published an analysis of 911, and found there were roughly 120,000 PCs for rent via the service, with the largest number of them located in the United States.
“The 911[.]re network uses at least two free VPN services to lure its users to install a malware-like software that achieves persistence on the user’s computer,” the researchers wrote. “During the research we identified two free VPN services that [use] a subterfuge to lure users to install software that looks legitimate but makes them part of the network. These two software are currently unknown to most if not all antivirus companies.”
The researchers concluded that 911 is supported by a “mid scale botnet-like infrastructure that operates in several networks, such as corporate, government and critical infrastructure.” The Canadian team said they found many of the 911 nodes available for rent were situated within several major US-based universities and colleges, critical infrastructures such as clean water, defense contractors, law enforcement and government networks.
Highlighting the risk that 911 nodes could pose to internal corporate networks, they observed that “the infection of a node enables the 911.re user to access shared resources on the network such as local intranet portals or other services.”
“It also enables the end user to probe the LAN network of the infected node,” the paper continues. “Using the internal router, it would be possible to poison the DNS cache of the LAN router of the infected node, enabling further attacks.”
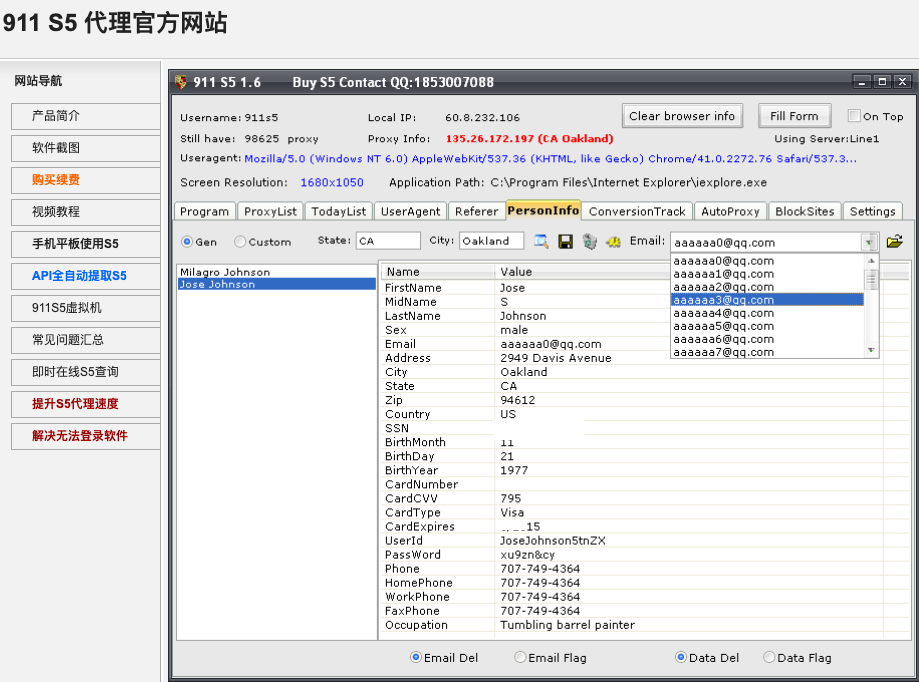
The 911 user interface, as it existed when the service first launched in 2016.
THE INTERNET NEVER FORGETS
A review of the clues left behind by 911’s early days on the Internet paint a more complete picture of this long-running proxy network. The domain names used by 911 over the years have a few common elements in their original WHOIS registration records, including the address ustraffic@qq.com and a Yunhe Wang from Beijing.
That ustraffic email is tied to a small number of interesting domains, including browsingguard[.]com, cleantraffic[.]net, execlean[.]net, proxygate[.]net, and flashupdate[.]net.
A cached copy of flashupdate[.]net available at the Wayback Machine shows that in 2016 this domain was used for the “ExE Bucks” affiliate program, a pay-per-install business which catered to people already running large collections of hacked computers or compromised websites. Affiliates were paid a set amount for each installation of the software, with higher commissions for installs in more desirable nations, particularly Europe, Canada and the United States.
“We load only one software — it’s a Socks5 proxy program,” read the message to ExE Bucks affiliates. The website said affiliates were free to spread the proxy software by any means available (i.e. “all promotion methods allowed”). The website’s copyright suggests the ExE Bucks affiliate program dates back to 2012.
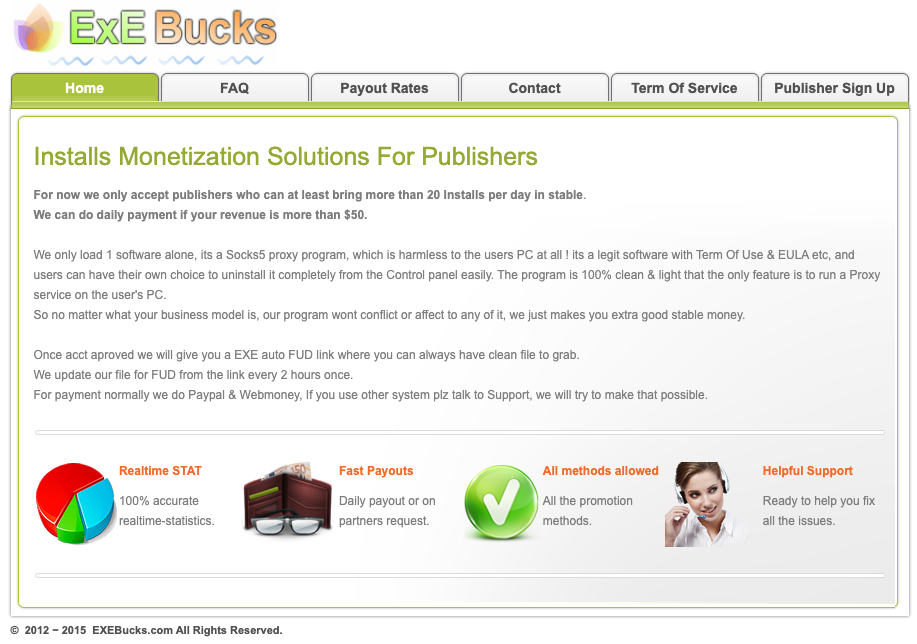
A cached copy of flashupdate[.]net circa 2016, which shows it was the home of a pay-per-install affiliate program that incentivized the silent installation of its software. “FUD” in the ad above refers to software and download links that are “Fully UnDetectable” as suspicious or malicious by all antivirus software.
“Our technology ensures the maximum security from reverse engineering and antivirus detections,” ExEClean promised.
Yet another domain connected to the ustraffic email is p2pshare[.]net, which advertised “free unlimited internet file-sharing platform” for those who agreed to install their software.
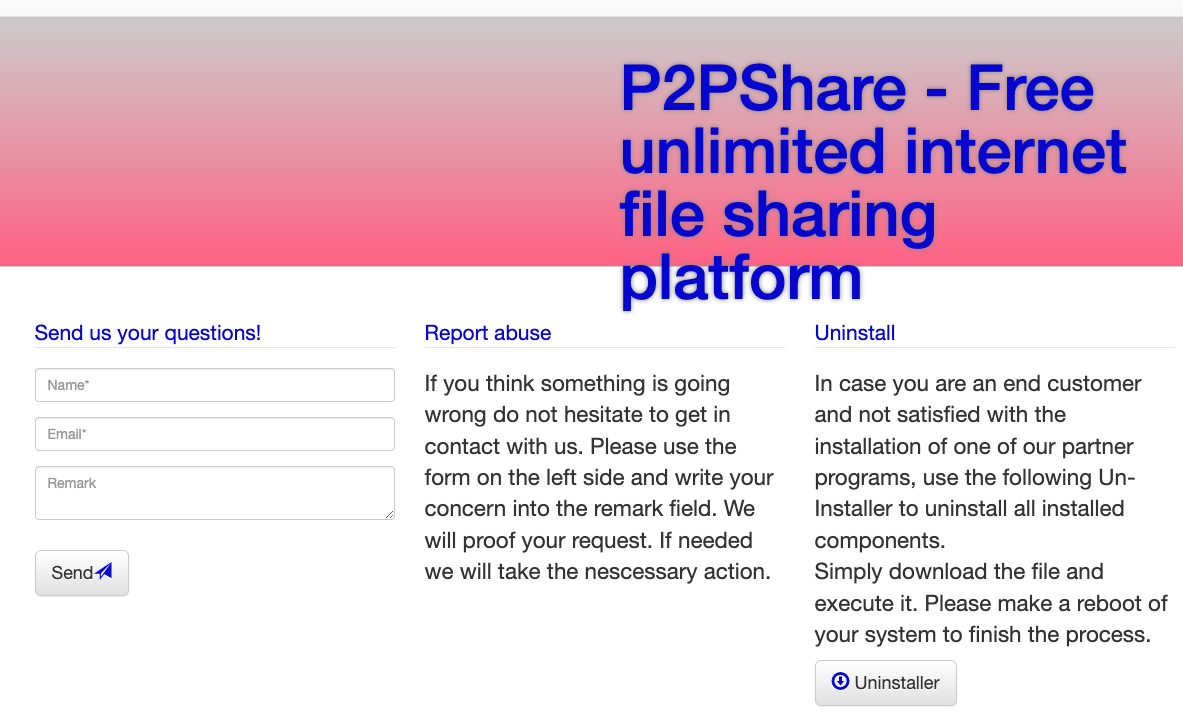
p2pshare.net, which bundled 911 proxy with an application that promised access to free unlimited internet file-sharing.
Still more domains associated with ustraffic@qq.com suggest 911’s proxy has been disguised as security updates for video player plugins, including flashplayerupdate[.]xyz, mediaplayerupdate[.]xyz, and videoplayerupdate[.]xyz.
The earliest version of the 911 website available from the Wayback Machine is from 2016. A sister service called proxygate[.]net launched roughly a year prior to 911 as a “free” public test of the budding new residential proxy service. “Basically using clients to route for everyone,” was how Proxygate described itself in 2016.
For more than a year after its founding, the 911 website was written entirely in Simplified Chinese. The service has only ever accepted payment via virtual currencies such as Bitcoin and Monero, as well as Alipay and China UnionPay, both payment platforms based in China.
911’s End-User Licensing Agreement (EULA) says the software belongs to International Media Ltd. in the British Virgin Islands. That is the same information currently displayed on the 911 website.
The EULA attached to 911 software downloaded from browsingguard[.]com (tied to the ustraffic@qq email that registered 911) references a company called Gold Click Limited. According to the UK Companies House, Gold Click Limited was registered in 2016 to a 34-year-old Yunhe Wang from Beijing City. Many of the WHOIS records for the above mentioned domains also include the name Yunhe Wang, or some variation thereof.
In a response to questions from KrebsOnSecurity, 911 said the researchers were wrong, and that 911 has nothing to do with any of the other domains mentioned above.
“We have 911 SDK link and how it works described clearly in the “Terms of use” of affiliated partners products, and we have details of how the community powered network works on our webpages,” read an email response.
“Besides that, for protecting the end users, we banned many domains’ access and blocked the vulnerable ports, e.g. spamming emails, and torrent is not possible from the 911 network,” the reply continued. “Same as scanning and many others…Accessing to the Lan network and router is also blocked. We are monitoring 911 user’s account closely, once any abnormal behavior detected, we suspend the user’s account right away.”
FORUM ACTIVITY?
911 has remained one of the most popular services among denizens of the cybercrime underground for years, becoming almost shorthand for connecting to that “last mile” of cybercrime. Namely, the ability to route one’s malicious traffic through a computer that is geographically close to the consumer whose credit card they’re about to charge at some website, or whose bank account they’re about to empty.
Given the frequency with which 911 has been praised by cybercrooks on the top forums, it was odd to find the proprietors of 911 do not appear to have created any official support account for the service on any of several dozen forums reviewed by this author going back a decade. However there are two cybercriminal identities on the forums that have responded to individual 911 help requests, and who promoted the sale of 911 accounts via their handles.
Both of these identities were active on the crime forum fl.l33t[.]su between 2016 and 2019. The user “Transfer” advertised and sold access to 911 from 2016 to 2018, amid many sales threads where they advertised expensive electronics and other consumer goods that were bought online with stolen credit cards.
In a 2017 discussion on fl.l33t[.]su, the user who picked the handle “527865713” could be seen answering private messages in response to help inquiries seeking someone at 911. That identity is tied to an individual who for years advertised the ability to receive and relay large wire transfers from China.
One ad from this user in 2016 offered a “China wire service” focusing on Western Union payments, where “all transfers are accepted in China.” The service charged 20 percent of all “scam wires,” unauthorized wire transfers resulting from bank account takeovers or scams like CEO impersonation schemes.
911 TODAY
In August 2021, 911’s biggest competitor — a 15-year-old proxy network built on malware-compromised PCs called VIP72 — abruptly closed up shop. Almost overnight, an overwhelming number of former VIP72 customers began shifting their proxy activities to 911.

The login page for VIP72, until recently 911’s largest competitor.
That’s according to Riley Kilmer, co-founder of Spur.us — a security company that monitors anonymity services. Kilmer said 911 also gained an influx of new customers after the Jan. 2022 closure of LuxSocks, another malware-based proxy network.
“911’s user base skyrocketed after VIP72 and then LuxSocks went away,” Kilmer said. “And it’s not hard to see why. 911 and VIP72 are both Windows-based apps that operate in a similar way, where you buy private access to IPs.”
Kilmer said 911 is interesting because it appears to be based in China, while nearly all of the other major proxy networks are Russian-backed or Russian-based.
“They have two basic methods to get new IPs,” Kilmer said. “The free VPN apps, and the other is trojanized torrents. They’ll re-upload Photoshop and stuff like that so that it’s backdoored with the 911 proxy. They claim the proxy is bundled with legitimate software and that users all agree to their Terms of Service, meanwhile they can hide behind the claim that it was some affiliate who installed the software, not them.”
Kilmer said at last count, 911 had nearly 200,000 proxy nodes for sale, spanning more than 200 countries: The largest geographic concentration is the United States, where more than 42,000 proxies are currently for rent by the service.
PARTING THOUGHTS
Beware of “free” or super low-cost VPN services. Proper VPN services are not cheap to operate, so the revenue for the service has to come from somewhere. And there are countless “free” VPN services that are anything but, as we’ve seen with 911.
In general, the rule of thumb for transacting online is that if you’re not the paying customer, then you and/or your devices are probably the product that’s being sold to others. Many free VPN services will enlist users as VPN nodes for others to use, and some even offset costs by collecting and reselling data from their users.
All VPN providers claim to prioritize the privacy of their users, but many then go on to collect and store all manner of personal and financial data from those customers. Others are fairly opaque about their data collection and retention policies.
I’ve largely avoided wading into the fray about which VPN services are best, but there are so many shady and just plain bad ones out there that I’d be remiss if I didn’t mention one VPN provider whose business practices and transparency of operation consistently distinguish them from the rest. If maintaining your privacy and anonymity are primary concerns for you as a VPN user, check out Mullvad.net.
Let me make clear that KrebsOnSecurity does not have any financial or business ties to this company (for the avoidance of doubt, this post doesn’t even link to them). I mention it only because I’ve long been impressed with their candor and openness, and because Mullvad goes out of its way to discourage customers from sharing personal or financial data.
To that end, Mullvad will even accept mailed payments of cash to fund accounts, quite a rarity these days. More importantly, the service doesn’t ask users to share phone numbers, email addresses or any other personal information. Nor does it require customers to create passwords: Each subscription can be activated just by entering a Mullvad account number (woe to those who lose their account number).
I wish more companies would observe this remarkably economical security practice, which boils down to the mantra, “You don’t have to protect what you don’t collect.”
Update, July 24, 11:15 a.m. ET: 911’s homepage now includes a banner saying the service has halted new registrations and payments. “We are reviewing our network and adding a series of security measures to prevent misuse of our services,” the message reads. “Proxy balance top-up and new user registration are closed. We are reviewing every existing user, to ensure their usage is legit and [in] compliance with our Terms of Service.”
Update, July 30, 10:07 a.m. ET: 911 announced on July 28 that it is permanently closing down, following a series of data breaches this month that 911 says resulted in the deletion of customer data.




It’s a little surprising proxy trojans are operating this long without detection by the big AV shops. Do you attribute that to individual package/version crypting regime opsec being successful, or did they just fly below the radar of (all? major?) malware scanners without even a stub profile somehow? Is it secretly evasive or what is the reason major AV doesn’t already have it well-pegged? I can’t imagine a crypted dropper is the only reason, is it? (*& How many more such trojanized PPI proxies are out there doing the same if this one could sneak by?)
There is definitely a history of antivirus detection on some of the exploits, URLs etc. used by the pay-per-install affiliate programs, but the 911 proxy itself seems to have always been treated in a kind of “potentially unwanted program” classification, which is a step removed from malware (partly because these companies often sue when called malware) that refers to something which *might* have been installed with some type of disclaimer or notification.
Popular freeware scanner Malwarebytes for example by default will quarantine PUPs even for benign offer/bundleware marketed packages that are long known to be perfectly clean otherwise. If it’s got persistence after userland uninstall or any kind of PPI activity or C2 or is doing something significantly beyond what it says along any of those lines it seems to me that’s a plausible defense for designating it malware (or call it whatever, riskware, grayware) and flagging by default for quarantine unless the user whitelists. I do of course understand the legalistic inertia and due hesitation – yet AV has just one job. If it’s giving a pass to this via lack of a hard enough look, or via fear of lawsuits or business outcomes whatever, either way that’s not living up to the job. It begs the question how much else is flying right through and propagating over mainstream channels due to misclassifcation, and who ultimately steps up to deal with it generally in the absence of a lawsuit forcing that.
Everything that was likely, or even possibly, installed in a “bundled” software package should be noted by a quality anti/malware program. EVERYTHING! Affiliate programs incentivise sleazy distributors to force garbage software on the unsuspecting public. Identifying the possibly offensive item is often the first time an end user becomes aware of the software’s existence.
I regularly clean computers (PCs and Macs) with garbage software the user had no intention, or memory, of installing. Dump it all, I say. A user who know what the software is, and wants to keep it, can certainly chose to keep it and whitelist it. And I’ll tell you, that’s a LOT more straightforward than any agreement to install this rubbish software.
When “legit” companies like McAfee for instance, include a pre-selected download and install on another “legit” company’s update sight (I’m looking at you, Adobe), both should be publicly shamed and probably sued. It’s worthless marketing crap that does NOTHING to protect one’s computer. And I haven’t met a single person who installed it knowingly.
Hallelujah, brother! I have a similar business and EVERY time I ask my clients if they were aware that McAfee was installed, its a resounding “NO I had no idea!” Sneaky bastards! Their product is like taking sand to the beach!
All those clients needed to do was to pay attention. They’re victims of their own obliviousness.
Is it really just a loose consensus of individual technologies (and their ownership) that calls balls and strikes on what is considered malware outside of what a jury might decide, or not?
I noticed in the description text of the “EXE Bucks” screenshot you provide it says that the term “FUD” refers to “Fully UnDetectable” file, which I had not heard before. Now, in this context that may very well be true, however I have always understood that acronym to mean “File UpDate” (and of course the Microsoft invention – perhaps their only true one – “Fear, Uncertainty, and Doubt”).
Both are correct. In scope of __cyber__, though, the latter is more prevalent with DNM community users, while the former is more common in hacking and malware development circles
Ah, but FUD in that context goes back to the days of IBM salespeople trying to dissuade customers from buying Amdahl’s cheaper, and at least as capable, hardware. So not invented in Redmond!
“Feature Under Development” was the other sales FUD. Used whenever a client or prospect desired capabilities not present in the product the salesperson was repping.
911 closed their registration. Do you think it ever will be up again?
Brian kys
Your trolling is fail. Jump off your 5 story building in St. Petersburg or be thrown.
If your reading this if you have 911.proxy they recently signed a deal with FBI to see how exactly their proxies are used by different users you & or your proxies are not safe iv tried to find more details to support what im saying i found out today lets save as many as we can.
where are you sourcing this information?
By clicking “I agree”, accessing, or using the Platform you agree to be bound by this Agreement and the Privacy Policy. We may amend our Terms of Use or the Privacy Policy and may not notify you when we do so.
Your continued use of the Platform following any revision of the Platform or this Agreement constitutes your complete and irrevocable acceptance of any and all such changes. PLEASE BE AWARE THAT THERE ARE ARBITRATION AND CLASS ACTION PROVISIONS THAT MAY AFFECT YOUR RIGHTS. And this is updated dont be the next huspuppi
what is happened to 911 proxy i cant get access into it , is there any problem >???
They shut down too, according to the message in the homepage
911.re exit scammed.
lost over 5k proxies across 3 accounts. no refunds given
should have known not to trust the chinese
911 proxy suddenly stops working. I lost over 7k proxies. Can anyone recommend a nice proxy VPN? I’m really in need of it right now
We regret to inform you that we permanently shut down 911 and all its services on July 28th.
now HaCkErS got the information please delete the program from your computer !!
WHAT AN ABRUPT CLOSE A DAY AFTER I POSTED THE COMMENT !
What about HOLA ? and brightdata / luminatti ?))
im in need of a new proxy like 911.re anyone know of one?
Me too i also need a new proxy like 911 anyone?
Is Yilu proxy like 911.re?