Code-signing certificates are supposed to help authenticate the identity of software publishers, and provide cryptographic assurance that a signed piece of software has not been altered or tampered with. Both of these qualities make stolen or ill-gotten code-signing certificates attractive to cybercriminal groups, who prize their ability to add stealth and longevity to malicious software. This post is a deep dive on “Megatraffer,” a veteran Russian hacker who has practically cornered the underground market for malware focused code-signing certificates since 2015.
A review of Megatraffer’s posts on Russian crime forums shows this user began peddling individual stolen code-signing certs in 2015 on the Russian-language forum Exploit, and soon expanded to selling certificates for cryptographically signing applications and files designed to run in Microsoft Windows, Java, Adobe AIR, Mac and Microsoft Office.
Megatraffer explained that malware purveyors need a certificate because many antivirus products will be far more interested in unsigned software, and because signed files downloaded from the Internet don’t tend to get blocked by security features built into modern web browsers. Additionally, newer versions of Microsoft Windows will complain with a bright yellow or red alert message if users try to install a program that is not signed.
“Why do I need a certificate?” Megatraffer asked rhetorically in their Jan. 2016 sales thread on Exploit. “Antivirus software trusts signed programs more. For some types of software, a digital signature is mandatory.”
At the time, Megatraffer was selling unique code-signing certificates for $700 apiece, and charging more than twice that amount ($1,900) for an “extended validation” or EV code-signing cert, which is supposed to only come with additional identity vetting of the certificate holder. According to Megatraffer, EV certificates were a “must-have” if you wanted to sign malicious software or hardware drivers that would reliably work in newer Windows operating systems.
Part of Megatraffer’s ad. Image: Ke-la.com.
Megatraffer has continued to offer their code-signing services across more than a half-dozen other Russian-language cybercrime forums, mostly in the form of sporadically available EV and non-EV code-signing certificates from major vendors like Thawte and Comodo.
More recently, it appears Megatraffer has been working with ransomware groups to help improve the stealth of their malware. Shortly after Russia invaded Ukraine in February 2022, someone leaked several years of internal chat logs from the Conti ransomware gang, and those logs show Megatraffer was working with the group to help code-sign their malware between July and October 2020.
WHO IS MEGATRAFFER?
According to cyber intelligence firm Intel 471, Megatraffer has been active on more than a half-dozen crime forums from September 2009 to the present day. And on most of these identities, Megatraffer has used the email address 774748@gmail.com. That same email address also is tied to two forum accounts for a user with the handle “O.R.Z.”
Constella Intelligence, a company that tracks exposed databases, finds that 774748@gmail.com was used in connection with just a handful of passwords, but most frequently the password “featar24“. Pivoting off of that password reveals a handful of email addresses, including akafitis@gmail.com.
Intel 471 shows akafitis@gmail.com was used to register another O.R.Z. user account — this one on Verified[.]ru in 2008. Prior to that, akafitis@gmail.com was used as the email address for the account “Fitis,” which was active on Exploit between September 2006 and May 2007. Constella found the password “featar24” also was used in conjunction with the email address spampage@yandex.ru, which is tied to yet another O.R.Z. account on Carder[.]su from 2008.
The email address akafitis@gmail.com was used to create a Livejournal blog profile named Fitis that has a large bear as its avatar. In November 2009, Fitis wrote, “I am the perfect criminal. My fingerprints change beyond recognition every few days. At least my laptop is sure of it.”
Fitis’s Livejournal account. Image: Archive.org.
Fitis’s real-life identity was exposed in 2010 after two of the biggest sponsors of pharmaceutical spam went to war with each other, and large volumes of internal documents, emails and chat records seized from both spam empires were leaked to this author. That protracted and public conflict formed the backdrop of my 2014 book — “Spam Nation: The Inside Story of Organized Cybercrime, from Global Epidemic to Your Front Door.”
One of the leaked documents included a Microsoft Excel spreadsheet containing the real names, addresses, phone numbers, emails, street addresses and WebMoney addresses for dozens of top earners in Spamit — at the time the most successful pharmaceutical spam affiliate program in the Russian hacking scene and one that employed most of the top Russian botmasters.
That document shows Fitis was one of Spamit’s most prolific recruiters, bringing more than 75 affiliates to the Spamit program over several years prior to its implosion in 2010 (and earning commissions on any future sales from all 75 affiliates).
The document also says Fitis got paid using a WebMoney account that was created when its owner presented a valid Russian passport for a Konstantin Evgenievich Fetisov, born Nov. 16, 1982 and residing in Moscow. Russian motor vehicle records show two different vehicles are registered to this person at the same Moscow address.
The most interesting domain name registered to the email address spampage@yahoo.com, fittingly enough, is fitis[.]ru, which DomainTools.com says was registered in 2005 to a Konstantin E. Fetisov from Moscow.
The Wayback Machine at archive.org has a handful of mostly blank pages indexed for fitis[.]ru in its early years, but for a brief period in 2007 it appears this website was inadvertently exposing all of its file directories to the Internet.
One of the exposed files — Glavmed.html — is a general invitation to the infamous Glavmed pharmacy affiliate program, a now-defunct scheme that paid tens of millions of dollars to affiliates who advertised online pill shops mainly by hacking websites and manipulating search engine results. Glavmed was operated by the same Russian cybercriminals who ran the Spamit program.

A Google translated ad circa 2007 recruiting for the pharmacy affiliate program Glavmed, which told interested applicants to contact the ICQ number used by Fitis, a.k.a. MegaTraffer. Image: Archive.org.
Archive.org shows the fitis[.]ru webpage with the Glavmed invitation was continuously updated with new invite codes. In their message to would-be Glavmed affiliates, the program administrator asked applicants to contact them at the ICQ number 165540027, which Intel 471 found was an instant messenger address previously used by Fitis on Exploit.
The exposed files in the archived version of fitis[.]ru include source code for malicious software, lists of compromised websites used for pharmacy spam, and a handful of what are apparently personal files and photos. Among the photos is a 2007 image labeled merely “fitis.jpg,” which shows a bespectacled, bearded young man with a ponytail standing next to what appears to be a newly-married couple at a wedding ceremony.
Mr. Fetisov did not respond to requests for comment.
As a veteran organizer of affiliate programs, Fitis did not waste much time building a new moneymaking collective after Spamit closed up shop. New York City-based cyber intelligence firm Flashpoint found that Megatraffer’s ICQ was the contact number for Himba[.]ru, a cost-per-acquisition (CPA) program launched in 2012 that paid handsomely for completed application forms tied to a variety of financial instruments, including consumer credit cards, insurance policies, and loans.
“Megatraffer’s entrenched presence on cybercrime forums strongly suggests that malicious means are used to source at least a portion of traffic delivered to HIMBA’s advertisers,” Flashpoint observed in a threat report on the actor.
Intel 471 finds that Himba was an active affiliate program until around May 2019, when it stopping paying its associates.

Fitis’s Himba affiliate program, circa February 2014. Image: Archive.org.
Flashpoint notes that in September 2015, Megatraffer posted a job ad on Exploit seeking experienced coders to work on browser plugins, installers and “loaders” — basically remote access trojans (RATs) that establish communication between the attacker and a compromised system.
“The actor specified that he is looking for full-time, onsite help either in his Moscow or Kiev locations,” Flashpoint wrote.




So even experienced cybercriminals use lousy passwords!
What’s the mechanism for stealing EV certs? I thought those had to be on tokens.
My guess is that he’s filling out forms and using fake companies to legitimately get EV certs. Unless there is a way to flash/clone them?
Important work with compelling & engaging storytelling. Bravo
“I am the perfect criminal. I can only be caught by the waybackmachine (of all things) archiving my unambiguously scam-named directories published on my website, weak password reuse, etc.”
All those millions but still can’t get a pair of decent shoes for his sister’s wedding.
So if you can’t trust code-signed certs and they fool our malware scanners, where does that leave us? Totally screwed?
The U.S. needs to follow Russia’s lead and essentially legalize cybercrime against Russian citizens.
That’s the only way this BS stops.
Of course, the average Russian barely has 2 nickels to rub together, not much for American cybercriminals to steal, but it’s the principle of the thing.
I think they’ve got a point. If someone is serious about preventing detections of their malware then code signing certificates would be appealing. I think defenders should ensure that their protection software considers if an executable is commonly downloaded or not. This way a signed executable doesn’t have any added benefits and is still treated as a potential threat. I think manually selecting which certs to allow is beneficial as well. Then an attacker would need a cert stolen from a certain organization, reducing what’s possible.
That said it’s a tricky equation, you don’t want new but legitimate files causing alerts but you also can’t completely trust signatures. If you only rely on how common a file is I presume that’s not fullproof either, if an executable reaches commonly downloaded status before being marked as malicious it could slip by. What do you think is the right approach?
debugger
I would reason to argue that large/major tech are the only ones seeing a major benefit from the current application of online file safety. Well, that and nation state sponsored campaigns (is there a difference?)
Why does no one speak on how this effectively keeps a foot on the neck of developers just trying to get theirs in the door? The real story should be about the lack (see: non existence) of post production validation control mechanisms from cert issuers!
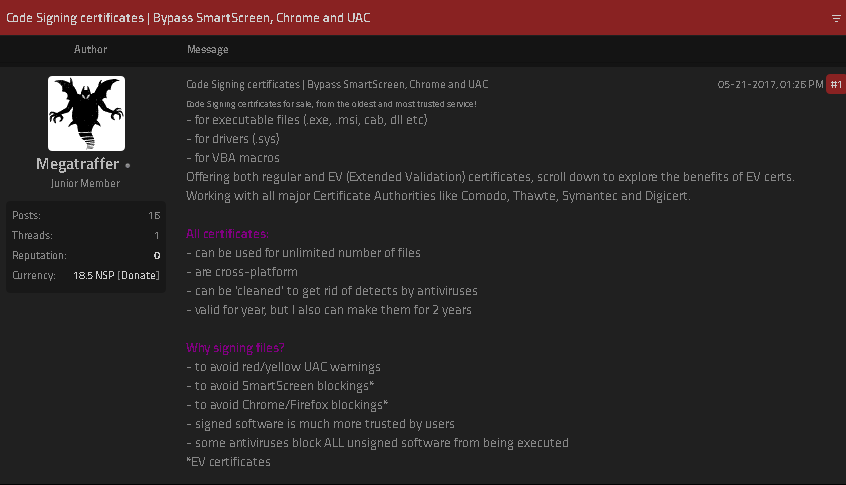
A few years back my lab studied the black market for code-signing certificates. We found four major vendors, including Megatraffer (who, at the time, was operating an e-shop called Codesigning Guru).
The e-shop sold about 12 certs per month, most of them issued recently. The certs were issued directly rather than stolen, and the vendors appeared quite confident in their supply of freshly issued certs. Many of the certs used to sign malware in those days were issued to Russian or Chinese publishers, but Megatraffer claimed on a forum that all certificates sold on Codesigning Guru were issued to British publishers. The publisher names tended to correspond to young companies, some incorporated around a month before their cert was issued. These could be shell companies incorporated by a malicious adversary who uses them to request code signing certificates, or legitimate companies that the adversary is able to impersonate, perhaps by using data mined from the public register.
We released our dataset of certs used to sign malware here: https://users.umiacs.umd.edu/~tdumitra/signedmalware/weis18/weis18.html. It’s 5 years old, but perhaps some folks will still find it useful.
The code-signing PKI includes some defenses against this kind of abuse. Microsoft’s SmartScreen assigns reputation
scores to executables and Authenticode certificates, and it displays a warning if it encounters an EXE signed with an unknown certificate. It’s like a whitelist, but more sophisticated because it can be updated automatically. The need to bypass SmartScreen, to ensure that the malware stays stealthy, was driving the demand for anonymous code-signing certificates in 2018. The vendors would give buyers advice for growing the SmartScreen reputation of their certificates, and, for a higher fee, they also sold certificates with built reputation.
We have more results and analyses in our paper: https://users.umiacs.umd.edu/~tdumitra/papers/WEIS-2018.pdf
Many things have probably changed since we did our research, but it’s interesting to see that Megatraffer is still in business. Thanks Brian for this cool piece of investigative journalism!
Wow! Thanks, Tudor for your comment and for sharing your research. Indeed, the fact that Megatraffer is still offering his services after all these years is the reason I started looking at him in the first place!
very informative blog, thanks for sharing this useful investigation with us.