In November 2022, the password manager service LastPass disclosed a breach in which hackers stole password vaults containing both encrypted and plaintext data for more than 25 million users. Since then, a steady trickle of six-figure cryptocurrency heists targeting security-conscious people throughout the tech industry has led some security experts to conclude that crooks likely have succeeded at cracking open some of the stolen LastPass vaults.
Taylor Monahan is lead product manager of MetaMask, a popular software cryptocurrency wallet used to interact with the Ethereum blockchain. Since late December 2022, Monahan and other researchers have identified a highly reliable set of clues that they say connect recent thefts targeting more than 150 people. Collectively, these individuals have been robbed of more than $35 million worth of crypto.
Monahan said virtually all of the victims she has assisted were longtime cryptocurrency investors, and security-minded individuals. Importantly, none appeared to have suffered the sorts of attacks that typically preface a high-dollar crypto heist, such as the compromise of one’s email and/or mobile phone accounts.
“The victim profile remains the most striking thing,” Monahan wrote. “They truly all are reasonably secure. They are also deeply integrated into this ecosystem, [including] employees of reputable crypto orgs, VCs [venture capitalists], people who built DeFi protocols, deploy contracts, run full nodes.”
Monahan has been documenting the crypto thefts via Twitter/X since March 2023, frequently expressing frustration in the search for a common cause among the victims. Then on Aug. 28, Monahan said she’d concluded that the common thread among nearly every victim was that they’d previously used LastPass to store their “seed phrase,” the private key needed to unlock access to their cryptocurrency investments.
MetaMask owner Taylor Monahan on Twitter. Image: twitter.com/tayvano_
Armed with your secret seed phrase, anyone can instantly access all of the cryptocurrency holdings tied to that cryptographic key, and move the funds to anywhere they like.
Which is why the best practice for many cybersecurity enthusiasts has long been to store their seed phrases either in some type of encrypted container — such as a password manager — or else inside an offline, special-purpose hardware encryption device, such as a Trezor or Ledger wallet.
“The seed phrase is literally the money,” said Nick Bax, director of analytics at Unciphered, a cryptocurrency wallet recovery company. “If you have my seed phrase, you can copy and paste that into your wallet, and then you can see all my accounts. And you can transfer my funds.”
Bax said he closely reviewed the massive trove of cryptocurrency theft data that Taylor Monahan and others have collected and linked together.
“It’s one of the broadest and most complex cryptocurrency investigations I’ve ever seen,” Bax said. “I ran my own analysis on top of their data and reached the same conclusion that Taylor reported. The threat actor moved stolen funds from multiple victims to the same blockchain addresses, making it possible to strongly link those victims.”
Bax, Monahan and others interviewed for this story say they’ve identified a unique signature that links the theft of more than $35 million in crypto from more than 150 confirmed victims, with roughly two to five high-dollar heists happening each month since December 2022.
KrebsOnSecurity has reviewed this signature but is not publishing it at the request of Monahan and other researchers, who say doing so could cause the attackers to alter their operations in ways that make their criminal activity more difficult to track.
But the researchers have published findings about the dramatic similarities in the ways that victim funds were stolen and laundered through specific cryptocurrency exchanges. They also learned the attackers frequently grouped together victims by sending their cryptocurrencies to the same destination crypto wallet.
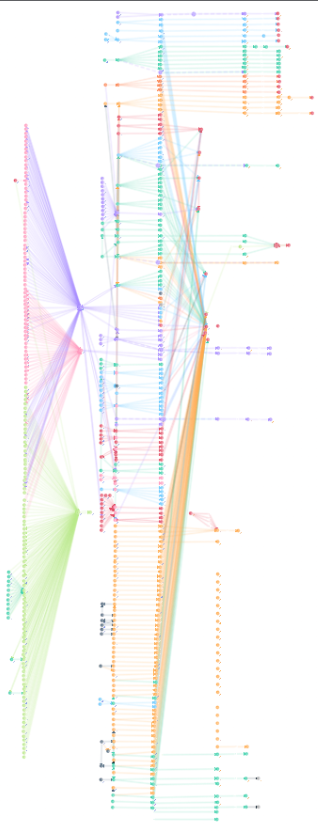
A graphic published by @tayvano_ on Twitter depicting the movement of stolen cryptocurrencies from victims who used LastPass to store their crypto seed phrases.
By identifying points of overlap in these destination addresses, the researchers were then able to track down and interview new victims. For example, the researchers said their methodology identified a recent multi-million dollar crypto heist victim as an employee at Chainalysis, a blockchain analysis firm that works closely with law enforcement agencies to help track down cybercriminals and money launderers.
Chainalysis confirmed that the employee had suffered a high-dollar cryptocurrency heist late last month, but otherwise declined to comment for this story.
Bax said the only obvious commonality between the victims who agreed to be interviewed was that they had stored the seed phrases for their cryptocurrency wallets in LastPass.
“On top of the overlapping indicators of compromise, there are more circumstantial behavioral patterns and tradecraft which are also consistent between different thefts and support the conclusion,” Bax told KrebsOnSecuirty. “I’m confident enough that this is a real problem that I’ve been urging my friends and family who use LastPass to change all of their passwords and migrate any crypto that may have been exposed, despite knowing full well how tedious that is.”
LastPass declined to answer questions about the research highlighted in this story, citing an ongoing law enforcement investigation and pending litigation against the company in response to its 2022 data breach.
“Last year’s incident remains the subject of an ongoing investigation by law enforcement and is also the subject of pending litigation,” LastPass said in a written statement provided to KrebsOnSecurity. “Since last year’s attack on LastPass, we have remained in contact with law enforcement and continue to do so.”
Their statement continues:
“We have shared various technical information, Indicators of Compromise (IOCs), and threat actor tactics, techniques, and procedures (TTPs) with our law enforcement contacts as well as our internal and external threat intelligence and forensic partners in an effort to try and help identify the parties responsible. In the meantime, we encourage any security researchers to share any useful information they believe they may have with our Threat Intelligence team by contacting securitydisclosure@lastpass.com.”
THE LASTPASS BREACH(ES)
On August 25, 2022, LastPass CEO Karim Toubba wrote to users that the company had detected unusual activity in its software development environment, and that the intruders stole some source code and proprietary LastPass technical information. On Sept. 15, 2022, LastPass said an investigation into the August breach determined the attacker did not access any customer data or password vaults.
But on Nov. 30, 2022, LastPass notified customers about another, far more serious security incident that the company said leveraged data stolen in the August breach. LastPass disclosed that criminal hackers had compromised encrypted copies of some password vaults, as well as other personal information.
In February 2023, LastPass disclosed that the intrusion involved a highly complex, targeted attack against a DevOps engineer who was one of only four LastPass employees with access to the corporate vault.
“This was accomplished by targeting the DevOps engineer’s home computer and exploiting a vulnerable third-party media software package, which enabled remote code execution capability and allowed the threat actor to implant keylogger malware,” LastPass officials wrote. “The threat actor was able to capture the employee’s master password as it was entered, after the employee authenticated with MFA, and gain access to the DevOps engineer’s LastPass corporate vault.”
Dan Goodin at Ars Technica reported and then confirmed that the attackers exploited a known vulnerability in a Plex media server that the employee was running on his home network, and succeeded in installing malicious software that stole passwords and other authentication credentials. The vulnerability exploited by the intruders was patched back in 2020, but the employee never updated his Plex software.
As it happens, Plex announced its own data breach one day before LastPass disclosed its initial August intrusion. On August 24, 2022, Plex’s security team urged users to reset their passwords, saying an intruder had accessed customer emails, usernames and encrypted passwords.
OFFLINE ATTACKS
A basic functionality of LastPass is that it will pick and remember lengthy, complex passwords for each of your websites or online services. To automatically populate the appropriate credentials at any website going forward, you simply authenticate to LastPass using your master password.
LastPass has always emphasized that if you lose this master password, that’s too bad because they don’t store it and their encryption is so strong that even they can’t help you recover it.
But experts say all bets are off when cybercrooks can get their hands on the encrypted vault data itself — as opposed to having to interact with LastPass via its website. These so-called “offline” attacks allow the bad guys to conduct unlimited and unfettered “brute force” password cracking attempts against the encrypted data using powerful computers that can each try millions of password guesses per second.
“It does leave things vulnerable to brute force when the vaults are stolen en masse, especially if info about the vault HOLDER is available,” said Nicholas Weaver, a researcher at University of California, Berkeley’s International Computer Science Institute (ICSI) and lecturer at UC Davis. “So you just crunch and crunch and crunch with GPUs, with a priority list of vaults you target.”
How hard would it be for well-resourced criminals to crack the master passwords securing LastPass user vaults? Perhaps the best answer to this question comes from Wladimir Palant, a security researcher and the original developer behind the Adblock Plus browser plugin.
In a December 2022 blog post, Palant explained that the crackability of a LastPass master password depends largely on two things: The complexity of the master password, and the default settings for LastPass users, which appear to have varied quite a bit based on when those users began patronizing the service.
LastPass says that since 2018 it has required a twelve-character minimum for master passwords, which the company said “greatly minimizes the ability for successful brute force password guessing.”
But Palant said while LastPass indeed improved its master password defaults in 2018, it did not force all existing customers who had master passwords of lesser lengths to pick new credentials that would satisfy the 12-character minimum.
“If you are a LastPass customer, chances are that you are completely unaware of this requirement,” Palant wrote. “That’s because LastPass didn’t ask existing customers to change their master password. I had my test account since 2018, and even today I can log in with my eight-character password without any warnings or prompts to change it.”
Palant believes LastPass also failed to upgrade many older, original customers to more secure encryption protections that were offered to newer customers over the years. One important setting in LastPass is the number of “iterations,” or how many times your master password is run through the company’s encryption routines. The more iterations, the longer it takes an offline attacker to crack your master password.
Palant noted last year that for many older LastPass users, the initial default setting for iterations was anywhere from “1” to “500.” By 2013, new LastPass customers were given 5,000 iterations by default. In February 2018, LastPass changed the default to 100,100 iterations. And very recently, it upped that again to 600,000.
Palant said the 2018 change was in response to a security bug report he filed about some users having dangerously low iterations in their LastPass settings.
“Worse yet, for reasons that are beyond me, LastPass didn’t complete this migration,” Palant wrote. “My test account is still at 5,000 iterations, as are the accounts of many other users who checked their LastPass settings. LastPass would know how many users are affected, but they aren’t telling that. In fact, it’s painfully obvious that LastPass never bothered updating users’ security settings. Not when they changed the default from 1 to 500 iterations. Not when they changed it from 500 to 5,000. Only my persistence made them consider it for their latest change. And they still failed implementing it consistently.”
A chart on Palant’s blog post offers an idea of how increasing password iterations dramatically increases the costs and time needed by the attackers to crack someone’s master password. Palant said it would take a single GPU about a year to crack a password of average complexity with 500 iterations, and about 10 years to crack the same password run through 5,000 iterations.
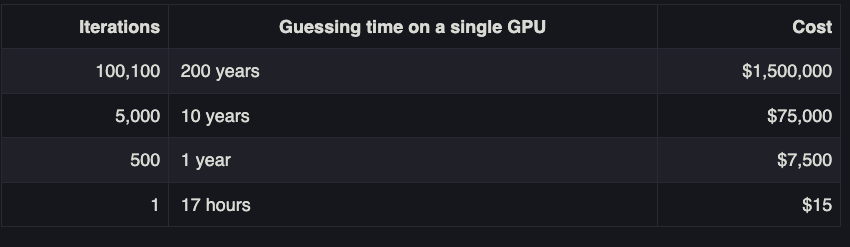
Image: palant.info
However, these numbers radically come down when a determined adversary also has other large-scale computational assets at their disposal, such as a bitcoin mining operation that can coordinate the password-cracking activity across multiple powerful systems simultaneously.
Weaver said a password or passphrase with average complexity — such as “Correct Horse Battery Staple” is only secure against online attacks, and that its roughly 40 bits of randomness or “entropy” means a graphics card can blow through it in no time.
“An Nvidia 3090 can do roughly 4 million [password guesses] per second with 1000 iterations, but that would go down to 8 thousand per second with 500,000 iterations, which is why iteration count matters so much,” Weaver said. “So a combination of ‘not THAT strong of a password’ and ‘old vault’ and ‘low iteration count’ would make it theoretically crackable but real work, but the work is worth it given the targets.”
Reached by KrebsOnSecurity, Palant said he never received a response from LastPass about why the company apparently failed to migrate some number of customers to more secure account settings.
“I know exactly as much as everyone else,” Palant wrote in reply. “LastPass published some additional information in March. This finally answered the questions about the timeline of their breach – meaning which users are affected. It also made obvious that business customers are very much at risk here, Federated Login Services being highly compromised in this breach (LastPass downplaying as usual of course).”
Palant said upon logging into his LastPass account a few days ago, he found his master password was still set at 5,000 iterations.
INTERVIEW WITH A VICTIM
KrebsOnSecurity interviewed one of the victims tracked down by Monahan, a software engineer and startup founder who recently was robbed of approximately $3.4 million worth of different cryptocurrencies. The victim agreed to tell his story in exchange for anonymity because he is still trying to claw back his losses. We’ll refer to him here as “Connor” (not his real name).
Connor said he began using LastPass roughly a decade ago, and that he also stored the seed phrase for his primary cryptocurrency wallet inside of LastPass. Connor chose to protect his LastPass password vault with an eight character master password that included numbers and symbols (~50 bits of entropy).
“I thought at the time that the bigger risk was losing a piece of paper with my seed phrase on it,” Connor said. “I had it in a bank security deposit box before that, but then I started thinking, ‘Hey, the bank might close or burn down and I could lose my seed phrase.'”
Those seed phrases sat in his LastPass vault for years. Then, early on the morning of Sunday, Aug. 27, 2023, Connor was awoken by a service he’d set up to monitor his cryptocurrency addresses for any unusual activity: Someone was draining funds from his accounts, and fast.
Like other victims interviewed for this story, Connor didn’t suffer the usual indignities that typically presage a cryptocurrency robbery, such as account takeovers of his email inbox or mobile phone number.
Connor said he doesn’t know the number of iterations his master password was given originally, or what it was set at when the LastPass user vault data was stolen last year. But he said he recently logged into his LastPass account and the system forced him to upgrade to the new 600,000 iterations setting.
“Because I set up my LastPass account so early, I’m pretty sure I had whatever weak settings or iterations it originally had,” he said.
Connor said he’s kicking himself because he recently started the process of migrating his cryptocurrency to a new wallet protected by a new seed phrase. But he never finished that migration process. And then he got hacked.
“I’d set up a brand new wallet with new keys,” he said. “I had that ready to go two months ago, but have been procrastinating moving things to the new wallet.”
Connor has been exceedingly lucky in regaining access to some of his stolen millions in cryptocurrency. The Internet is swimming with con artists masquerading as legitimate cryptocurrency recovery experts. To make matters worse, because time is so critical in these crypto heists, many victims turn to the first quasi-believable expert who offers help.
Instead, several friends steered Connor to Flashbots.net, a cryptocurrency recovery firm that employs several custom techniques to help clients claw back stolen funds — particularly those on the Ethereum blockchain.
According to Connor, Flashbots helped rescue approximately $1.5 million worth of the $3.4 million in cryptocurrency value that was suddenly swept out of his account roughly a week ago. Lucky for him, Connor had some of his assets tied up in a type of digital loan that allowed him to borrow against his various cryptocurrency assets.
Without giving away too many details about how they clawed back the funds, here’s a high level summary: When the crooks who stole Connor’s seed phrase sought to extract value from these loans, they were borrowing the maximum amount of credit that he hadn’t already used. But Connor said that left open an avenue for some of that value to be recaptured, basically by repaying the loan in many small, rapid chunks.
WHAT SHOULD LASTPASS USERS DO?
According to MetaMask’s Monahan, users who stored any important passwords with LastPass — particularly those related to cryptocurrency accounts — should change those credentials immediately, and migrate any crypto holdings to new offline hardware wallets.
“Really the ONLY thing you need to read is this,” Monahan pleaded to her 70,000 followers on Twitter/X: “PLEASE DON’T KEEP ALL YOUR ASSETS IN A SINGLE KEY OR SECRET PHRASE FOR YEARS. THE END. Split up your assets. Get a hw [hardware] wallet. Migrate. Now.”
If you also had passwords tied to banking or retirement accounts, or even just important email accounts — now would be a good time to change those credentials as well.
I’ve never been comfortable recommending password managers, because I’ve never seriously used them myself. Something about putting all your eggs in one basket. Heck, I’m so old-fashioned that most of my important passwords are written down and tucked away in safe places.
But I recognize this antiquated approach to password management is not for everyone. Connor says he now uses 1Password, a competing password manager that recently earned the best overall marks from Wired and The New York Times.
1Password says that three things are needed to decrypt your information: The encrypted data itself, your account password, and your Secret Key. Only you know your account password, and your Secret Key is generated locally during setup.
“The two are combined on-device to encrypt your vault data and are never sent to 1Password,” explains a 1Password blog post ‘What If 1Password Gets Hacked?‘ “Only the encrypted vault data lives on our servers, so neither 1Password nor an attacker who somehow manages to guess or steal your account password would be able to access your vaults – or what’s inside them.
Weaver said that Secret Key adds an extra level of randomness to all user master passwords that LastPass didn’t have.
“With LastPass, the idea is the user’s password vault is encrypted with a cryptographic hash (H) of the user’s passphrase,” Weaver said. “The problem is a hash of the user’s passphrase is remarkably weak on older LastPass vaults with master passwords that do not have many iterations. 1Password uses H(random-key||password) to generate the password, and it is why you have the QR code business when adding a new device.”
Weaver said LastPass deserves blame for not having upgraded iteration counts for all users a long time ago, and called the latest forced upgrades “a stunning indictment of the negligence on the part of LastPass.”
“That they never even notified all those with iteration counts of less than 100,000 — who are really vulnerable to brute force even with 8-character random passwords or ‘correct horse battery staple’ type passphrases — is outright negligence,” Weaver said. “I would personally advocate that nobody ever uses LastPass again: Not because they were hacked. Not because they had an architecture (unlike 1Password) that makes such hacking a problem. But because of their consistent refusal to address how they screwed up and take proactive efforts to protect their customers.”
Bax and Monahan both acknowledged that their research alone can probably never conclusively tie dozens of high-dollar crypto heists over the past year to the LastPass breach. But Bax says at this point he doesn’t see any other possible explanation.
“Some might say it’s dangerous to assert a strong connection here, but I’d say it’s dangerous to assert there isn’t one,” he said. “I was arguing with my fiance about this last night. She’s waiting for LastPass to tell her to change everything. Meanwhile, I’m telling her to do it now.”




I had been a long time user of LastPass, but after the second breach I had to bail out. My master password was complex and longer than 12 characters, so I hope I’ll be OK. I switched to 1Password and spent 10 days changing over 1,000 passwords I had accumulated over the years. Shame on LastPass for 1) Not having better security from the start, and 2) Doing a terrible job keeping its customers informed.
LastPass had stated that there are unencrypted data elements that were associated with stolen vaults. If this is indeed associated with the LastPass breach(es), I wonder if the unencrypted data elements enabled a prioritization of the vaults to brute force. Knowing the vaults with the most valuable assets would certainly help speed up who to target.
My bet is yes: In the clear you could apparently see the iteration count and the user, which should be enough to specifically prioritize who you go after, so you don’t just brute force everyone with a 5000-count iteration, but specifically prioritize those who seem more likely.
I believe everything *about* a password *except* the password itself was (and is) stored in plaintext at LastPass. URL, username, created date, etc. So, another way to prioritize would obviously be to find vaults with crypto.com or whatever website info.
I believe the usernames were encrypted, but FOR CERTAIN the urls were not (I confirmed this with LP in January). So, bad actors are likely prioritizing those with Schwab and Fidelity accounts right after they clear out the cryptocoin wallets.
“Not because they were hacked. Not because they had an architecture (unlike 1Password) that makes such hacking a problem. But because of their consistent refusal to address how they screwed up and take proactive efforts to protect their customers.”
As a PASSWORD MANAGING SERVICE! Oh we’ll hold those crown jewels you for you, don’t ask how though.
You wouldn’t like the answer. Trust us, our security goes to 5,000.
Hilarious. Noone could deserve it more than the scum who work for Chainanus..
”Security minded people”, and them not changing important passwords after the LastPass breach, makes me smirk. Let’s add ”Not very” to the beginning?
“security-minded individuals”
“previously used LastPass to store their “seed phrase,””
Is anyone else seeing the controversy here?
I get it. I probably should have mentioned that while you can change your passwords pretty easily, you can’t really change your crypto seed phrase. If you had your seed in LastPass, it’s still exposed unless you’ve moved your assets into brand new wallets, and that take effort, involves some amount of risk, and it’s not free: There are non-trivial costs for moving huge sums of crypto at all.
I used LastPass for quite a while. I got a little nervous when they were acquired by LogMeIn. But I was out the door when LogMeIn got taken over by some private equity companies. I thought that bad news written all over it. I wish I’d been wrong.
I too used L.P. for a number of years. When Joe Siegrist sold the company and then eventually left, I had a bad feeling about it. I didn’t know that LogMeIn sold the company as well.
You should use password managers for maximum privacy.
Sounds great!
You should give your private password manager to us.
Wait, what?
What’s the worst that could happen?
This is why I never use a password manager.
Changing the password of an account you had in LastPass is not enough. You also should change the user name of each such financial account, or risk that the financial institution might yield to a password reset request from a miscreant. Suspenders: move the assets to a different financial institution.
I did change user name and password on all my important accounts. I viewed it as sort of the other half of the equation–using the same username repeatedly is just as bad as using the same password repeatedly.
I’ve also started to notice more the system used by financial institutions. One I like does the 2FA thing after the entry of the user name, and before the password. I sort of like that because you’ll be alerted as soon as someone tries to enter your username, and not after they determine both username and password. And also, while it can be a PITA, some reset earlier than others after too many failed logins.
More here:
https://www.reddit.com/r/Lastpass/comments/164m04m/25_million_in_crypto_stolen_from_lastpass_secure/
Many takeaways here. One of them is that if you’re going to let your employees work from home, discourage them from using their home computers. Have them use company-provided computers whose software the company monitors. LastPass couldn’t control what that DevOps engineer installed on his home computer. They paid the price.
Yes, it’s a pain for employees, but it’s part of how we maintain secure infrastructure. Or at least, how we increase the difficulty of breaking a secure infrastructure.
It’s a good point considering they limited the “vault” access to only 4 people.
Begs the question, among any 4 “trusted, educated, security-minded” people…
how many are running some type of known-vuln’ed sw-app on the LAN?
It’s a small number to audit in this case. Remote work is “an” excuse, but…
Oh, it gets better. “LastPass Employee Could’ve Prevented Hack With a Software Update”
“The hacker exploited a vulnerability in the Plex Media Server software that was patched in May 2020.
‘The version that addressed this exploit was roughly 75 versions ago,’ Plex says.”
¯\_(ツ)_/¯ You can’t teach an old, unhygienic dog new tricks, but you MIGHT give him a bath once in 3 years…
From what I understand, the compromised Plex app was on an entirely different machine than the DevOps’ work machine. It just happened to be on the same home network which allowed the lateral movement of the hackers. A take away from that could be to segregate work and personal devices into separate networks to prevent that type of movement.
Unless you have a solid reason for 2 router ports to share a LAN, make separate VLANs for each port.
If the router doesn’t support VLANs it’s time to upgrade.
If you have more than 1 port, you don’t need VLANs…
Eh? If you have 1+n ports on the same VLAN, or “no VLAN options at all” which is essentially the same thing, those ports can talk to each other and enable lateral moves from 1 box to the rest. If they’re on separate VLANs there’s no direct-pipe possibility of that unless they also compromise the router. Not sure what you’re saying.
“A take away from that could be to segregate work and personal devices into separate networks to prevent that type of movement.”
And here in lies the problem. For years, DevOps have screamed “We need more access” and SecOps have replied “We need to restrict access” and C Suite always side with bottom-line productivity/cash-flow. Then we end up with this very scenario.
At the very least, an internal risk assessment/audit and applicable security measures should have been implemented before somebody decided to hand “the keys to the kingdom”, to be used externally, to someone so lacking in the very fundamentals of SecOps. I’d put money on the fact that an audit was completed and the result; “it’s too hard/costly to implement” was the reply, and the Security team is left to clean up the mess once again.
I’d be very interested to know WHO was responsible for making THAT decision, particularly for shareholders. For a company in the Security Industry providing products aimed at high tech corporations, small business and families alike, this is a major fail and someone should be held accountable. The long term fallout to individuals could be huge … Watch this space.
The article didn’t mention anything about the victims’ use of 2fa to protect their crypto accounts. Are we to assume from the information provided that it is likely none used 2fa to protect multi-million accounts? Are there limitations to using 2fa for protecting crypto wallets that I’m not aware of? 2fa wouldn’t make be impossible to get around (as we know from SIM swapping), but would certainly make things much more difficult and (potentially) more traceable.
2FA protects your vault from being accessed while it’s online. If it is being hacked offline, 2FA provides no protection at all.
The LastPass vault was cracked offline, but not the crypto vaults. My guess is they were not using 2FA, or if they were their 2FA secret was also stored in LastPass.
2FA only protects logins. You don’t need to login to a victim’s account to steal their crypto.
> Are there limitations to using 2fa for protecting crypto wallets that I’m not aware of?
Yes. 2FA protects accounts, not wallets. It’s in the name; 2 factor *authentication*. You don’t authenticate to a wallet, it’s not a service. You cryptographically sign things with it, which is just maths. You don’t get to put a password or authentication around the ability to do maths.
Surprise! Today an email from LastPass arrived (though I’m no longer a customer), that included this update:
Master Password Enhancements
Next month, we’re implementing even stronger master password requirements to keep up with the ever-evolving cybersecurity landscape. If your master password is under the 12-character minimum, it’s time to update
I’m surprised supposedly security-conscious folks had not assumed the worst and taken action when the breach first got reported. I had deleted my LastPass account two years prior to their breach, and I still changed everything in my replacement password manager down to PINs, encryption keys, security questions, and so on. It took me about 3 months to do everything, but I felt it was warranted.
I thought LastPass was lying about the severity and likely wasn’t even sure how far back their exposure went. The only safe assumption for me was that my old account was somewhere in a test/dev environment that was pilfered.
Thanks for this breakdown and for the information about LastPass’s bad governance and lack of transparency. We’d been dragging our feet getting our family off of LP but this lit a fire under us! I also see that 1Password has instructions on migrating passwords from LastPass automatically so hopefully it’s less painful than we feared!
Is there a reason why a Yubikey or some other physical key wouldn’t provide better security than a password or seed phrase? Especially with the amount of money involved here…..
We knew that the decyption keys for LastPass secure notes were compromised in the original breach. Advice given by security personnel (including myself) was it is not urgent to rotate passwords stored in LastPass Vaults, but any sensitive information in Lastpass “secure notes” should be rotated immediately. Eventually, a migration to 1Password or another more cryptographically well-constructed password manager was also advised.
It appears hackers aren’t actually gaining access to lastpass vault contents per se but merely decrypting secure notes, using the compromised decryption key, for wallet seed information. We knew this was the first possibility from the outset, hopefully this encourages people to actively rotate credentials.
I’m using Schneier’s PasswordSafe and find it very good. That coupled with PWGen to generate strong passwords for accounts makes me sleep better at night.
I have 2 folder in my last pass passwords. One is called important. One is called not important. I change the important ones once every year or two. The not important don’t care. When breached happened changed master password and all important passwords. Took a few hours. It’s good security practice to change them on occasion anyways. Every service has the potential of getting hacked.
I remember helping my parents get last pass setup, luckily we created a very complex and random password to make the encryption hard to break. That said though, I’m going to have them switch to local password vaults.
Brian, you say, “I’ve never been comfortable recommending password managers, because I’ve never seriously used them myself. Something about putting all your eggs in one basket. Heck, I’m so old-fashioned that most of my important passwords are written down and tucked away in safe places.”
I’m really glad to know you don’t use them and don’t recommend them. However, I’ve never seen you mention this before.
You previously quoted people who recommended using password managers, without qualifying it (as you did here), by mentioning that you personally are not comfortable recommending PW managers and don’t use them yourself. Here’s two examples from previous articles of yours:
1) https://krebsonsecurity.com/2021/05/the-wages-of-password-re-use-your-money-or-your-life/
Password managers are ideal for people who can’t break the habit of re-using passwords, because you only have to remember one (strong) master password to access all of your stored credentials.
2) https://krebsonsecurity.com/2019/08/the-risk-of-weak-online-banking-passwords/
Knight said. “For now, all the standard precautions we’ve been giving consumers for years still stand: Pick strong passwords, avoid re-using passwords, and get a password manager.”
Some of the most popular password managers include 1Password, Dashlane, LastPass and Keepass. Wired.com recently published a worthwhile writeup which breaks down each of these based on price, features and usability.
A few years back, after looking at PW managers, I chose Sticky Password, because it allowed you to store everything locally, although you couldn’t sync multiple devices if you did this. It also offered a USB version. But after using it for a while, I migrated to a hardware wallet.
I learn a lot from what you write, and follow a great deal of the recommendations and tips and strategies that you write about, so I am very grateful for your articles. Thank you.
Yeah, I probably should have said that publicly sooner. But still, my stories tend to be more about admiring and measuring the problem, as opposed to fixing it.
But as it relates to security matters, I would never ask or expect anyone to do something I wasn’t prepared to do myself. And password managers definitely fall into that category. And I doubt I will change my mind on that, personally.
They definitely have been cracking them. I recently started getting notifications in my email about login attempts to several of my online accounts. Fortunately ,I’ve already changed all of my important passwords and set up 2FA/MFA where possible
Yes, one whose vault likely was taken, but thankfully it was after I had gone to a much larger passphrase, but with the same low iteration count of the original, though over 5. But aside from the 2 lacking in info emails, and a link to the also less than explanatory blog posts, I did update the iteration count and passphrase, and am slowly working through the account list to update the less important passwords, though the compromised ones are hard to change, government entities who do not understand why you would want to change a password, and why wanting more that 5 characters is also an idea.
AC for obvious reasons as well
Any one putting their seed phrases on ANY online platform is just plain ignorant. Not putting your seed phrases ANYWHERE on line is the very FIRST RULE of crypto security. They can get hacked anywhere else, not just Lastpass. Crypto is not for the newby or for the uneducated crypro folk. This report is biased.
One word: PassKeys. Enough of this password sh** already.
One word: PassKeys. Enough already.
Passkeys wouldn’t have done anything to prevent this. They are a means to authenticate, not to encrypt.
Former LP user and advocate (regrettably). After witnessing their horrendous handling of the beaches, learning about the lack of complete DB encryption, and discovering their poor internal security practices and governance, I migrated to another PW manager and recommended everyone I know do the same. I figured the stolen vaults would be accessed eventually. The saving grace is I never used/recommended any cloud-based pw manager for sensitive accounts or data. I’ll echo prior comments. I wouldn’t call those using a pw manager to store a seed phrase (especially a cloud-based product) “security-minded”.
I would still make the argument that PW managers are a useful tool. When used correctly, the benefits for the average user outweigh the risks (especially those you find storing a PW list in spreadsheets or as notes of a “random” contact, in their phone, yes I’ve seen both). The key is education. People need to be made aware of the risks and how the tool should be properly used (just like anything else). For sensitive data, the only secure solution is a hw wallet or hidden (secure) paper, plus a backup. At the end of the day we’re always weighing security vs convenience. We need to take into account that the average person won’t do it if it’s too hard. On average, using a PW manager to store non-sensitive data does make people safer online because people use them and they encourage unique password and rotation. It’s a shame that LP tarnished that.
I stopped recommending LastPass after the last breach, which is a real shame. This just reinforces that decision.
Any thoughts on BitDefender, the open source password manager? I switched to the free version after the LP debacle. Thanks.
Oops. Make that Bitwarden.
Did you mean bitwarden? If so, I like it. I believe if you don’t want to pay you can host it yourself. I pair it with yubico security key authentication.