The password manager service LastPass is now forcing some of its users to pick longer master passwords. LastPass says the changes are needed to ensure all customers are protected by their latest security improvements. But critics say the move is little more than a public relations stunt that will do nothing to help countless early adopters whose password vaults were exposed in a 2022 breach at LastPass.
LastPass sent this notification to users earlier this week.
LastPass told customers this week they would be forced to update their master password if it was less than 12 characters. LastPass officially instituted this change back in 2018, but some undisclosed number of the company’s earlier customers were never required to increase the length of their master passwords.
This is significant because in November 2022, LastPass disclosed a breach in which hackers stole password vaults containing both encrypted and plaintext data for more than 25 million users.
Since then, a steady trickle of six-figure cryptocurrency heists targeting security-conscious people throughout the tech industry has led some security experts to conclude that crooks likely have succeeded at cracking open some of the stolen LastPass vaults.
KrebsOnSecurity last month interviewed a victim who recently saw more than three million dollars worth of cryptocurrency siphoned from his account. That user signed up with LastPass nearly a decade ago, stored their cryptocurrency seed phrase there, and yet never changed his master password — which was just eight characters. Nor was he ever forced to improve his master password.
That story cited research from Adblock Plus creator Wladimir Palant, who said LastPass failed to upgrade many older, original customers to more secure encryption protections that were offered to newer customers over the years.
For example, another important default setting in LastPass is the number of “iterations,” or how many times your master password is run through the company’s encryption routines. The more iterations, the longer it takes an offline attacker to crack your master password.
Palant said that for many older LastPass users, the initial default setting for iterations was anywhere from “1” to “500.” By 2013, new LastPass customers were given 5,000 iterations by default. In February 2018, LastPass changed the default to 100,100 iterations. And very recently, it upped that again to 600,000. Still, Palant and others impacted by the 2022 breach at LastPass say their account security settings were never forcibly upgraded.
Palant called this latest action by LastPass a PR stunt.
“They sent this message to everyone, whether they have a weak master password or not – this way they can again blame the users for not respecting their policies,” Palant said. “But I just logged in with my weak password, and I am not forced to change it. Sending emails is cheap, but they once again didn’t implement any technical measures to enforce this policy change.”
Either way, Palant said, the changes won’t help people affected by the 2022 breach.
“These people need to change all their passwords, something that LastPass still won’t recommend,” Palant said. “But it will somewhat help with the breaches to come.”
LastPass CEO Karim Toubba said changing master password length (or even the master password itself) is not designed to address already stolen vaults that are offline.
“This is meant to better protect customers’ online vaults and encourage them to bring their accounts up to the 2018 LastPass standard default setting of a 12-character minimum (but could opt out from),” Toubba said in an emailed statement. “We know that some customers may have chosen convenience over security and utilized less complex master passwords despite encouragement to use our (or others) password generator to do otherwise.”
A basic functionality of LastPass is that it will pick and remember lengthy, complex passwords for each of your websites or online services. To automatically populate the appropriate credentials at any website going forward, you simply authenticate to LastPass using your master password.
LastPass has always emphasized that if you lose this master password, that’s too bad because they don’t store it and their encryption is so strong that even they can’t help you recover it.
But experts say all bets are off when cybercrooks can get their hands on the encrypted vault data itself — as opposed to having to interact with LastPass via its website. These so-called “offline” attacks allow the bad guys to conduct unlimited and unfettered “brute force” password cracking attempts against the encrypted data using powerful computers that can each try millions of password guesses per second.
A chart on Palant’s blog post offers an idea of how increasing password iterations dramatically increases the costs and time needed by the attackers to crack someone’s master password. Palant said it would take a single high-powered graphics card about a year to crack a password of average complexity with 500 iterations, and about 10 years to crack the same password run through 5,000 iterations.
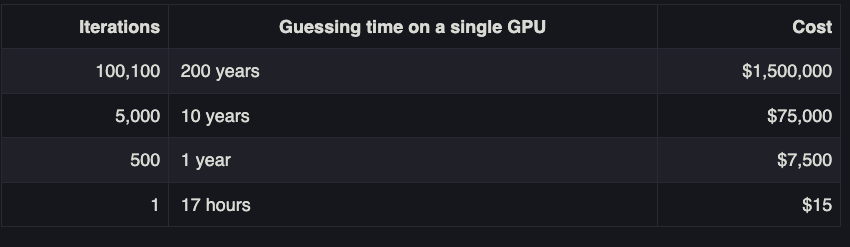
Image: palant.info
However, these numbers radically come down when a determined adversary also has other large-scale computational assets at their disposal, such as a bitcoin mining operation that can coordinate the password-cracking activity across multiple powerful systems simultaneously.
Meaning, LastPass users whose vaults were never upgraded to higher iterations and whose master passwords were weak (less than 12 characters) likely have been a primary target of distributed password-cracking attacks ever since the LastPass user vaults were stolen late last year.
Asked why some LastPass users were left behind on older security minimums, Toubba said a “small percentage” of customers had corrupted items in their password vaults that prevented those accounts from properly upgrading to the new requirements and settings.
“We have been able to determine that a small percentage of customers have items in their vaults that are corrupt and when we previously utilized automated scripts designed to re-encrypt vaults when the master password or iteration count is changed, they did not complete,” Toubba said. “These errors were not originally apparent as part of these efforts and, as we have discovered them, we have been working to be able to remedy this and finish the re-encryption.”
Nicholas Weaver, a researcher at University of California, Berkeley’s International Computer Science Institute (ICSI) and lecturer at UC Davis, said LastPass made a huge mistake years ago by not force-upgrading the iteration count for existing users.
“And now this is blaming the users — ‘you should have used a longer passphrase’ — not them for having weak defaults that were never upgraded for existing users,” Weaver said. “LastPass in my book is one step above snake-oil. I used to be, ‘Pick whichever password manager you want,’ but now I am very much, ‘Pick any password manager but LastPass.'”
Asked why LastPass isn’t recommending that users change all of the passwords secured by the encrypted master password that was stolen when the company got hacked last year, Toubba said it’s because “the data demonstrates that the majority of our customers follow our recommendations (or greater), and the probability of successfully brute forcing vault encryption is greatly reduced accordingly.”
“We’ve been telling customers since December of 2022 that they should be following recommended guidelines,” Toubba continued. “And if they haven’t followed the guidelines we recommended that they change their downstream passwords.”




For my interest only and as a matter of principle not being a Crypto user/owner
Was the loser able to seek, and successfully obtain, redress or refund, etc. please?
Rob
Which loser? The one Brian interviewed? I would think it’s too early for that yet.
Once crypto is moved to the thief’s crypto wallet, it is unlikely that you can recover anything. The only possibility is if the thief opened a centralized exchange account with real KYC information and they could freeze the funds there before it is cashed out. But then you need to deal with mostly international law enforcement and it doesn’t take long to move the funds to an anonymous wallet or have it washed
Probably a $3 million credit toward his LastPass subscription; non-transferable and non-refundable, of course. But that’s a lot of savings! Even Stevens
Almost certainly not. The only major recoveries of crypto that I’ve seen are through white hacking or by branching the chain from before the theft occurred. Crypto is money for highlanders, and God bless their hearts.
What I wonder is why anybody, given the last 20 years history of breaches, thinks that storing passwords online is a safe idea, even if encrypted.
My recommendation to everybody is use a locally encrypted spreadsheet instead. Excel for Windows users and LibreOffice for non-Windows users. These both use AES256 encryption in their latest incarnations. Then you can safely back up your critical passwords to the Cloud in a known encryption format that is robust.
If anybody has info otherwise on the latest versions of either LibreOffice or Excel, please edify us.
Apple disk images can use the same encryption level https://support.apple.com/guide/disk-utility/create-a-disk-image-dskutl11888/mac which makes for a very convenient format. I can store screen shots of password recovery questions etc as well as a text doc of credentials,
Stored in Dropbox it’s accessible from all my systems. I’ve used this for years. Too bad this is something Microsoft has not used their copiers to add to Windows.
“The Cloud” and online are essentially the same thing. You start with the premise that even encrypted passwords should not be stored online but then end with suggesting storing passwords in the cloud using a general purpose tool which can also do encryption.
I am familiar with LibreOffice and Bitwarden (password manager). Btiwarden likewise uses AES256 specifically AES in CBC mode with 256-bit keysize which is proper detail in cryptography speak. Bitwarden also defines how it derives the encryption key from the master password and how it protects the master password. LibreOffice use of encryption and AES256 is not as easily verified, but can interface with OpenGPG for improved key handling rather than just a password, allowing for easier secure sharing of documents. Passwords are not generally shared so password managers generally do not support easy sharing of them.
LibreOffice/MS Office is an officesuite software package, designed for general purpose office document usage with the ability to secure some of those documents by use of secure encryption.
Bitwarden is a password manager software package, designed for the specific purpose of securely managing passwords. The encryption of a password manager is not and added feature, but inherent to its design. Any good password manager should focus first on secure storage of the passwords.
My assessment is the software package designed for the task is going to have a better chance at securing the passwords.
Personally, I choose to use a password manager. I chose one which can securely synchronize across my devices. I need access to them from different devices at different varying locations. I also have hundreds nearly a thousand passwords to store. The password manager allows me to use the longest strongest unique randomly generated password for any particular site without worry of forgetting it. My master password which I must remember is very long to resist brute force attack, but it is the only password I need to remember.
Just because *any* of these are dedicated for protection of passwords doesn’t mean they are safe. Lots of high-value assets have been successfully hacked. Cloud (and it’s many derivatives) are trading ease-of-use for safety. Especially dangerous are cases where you don’t know what the programmers did in writing the software.
This issue is that LastPass makes using strong, unique, passwords easy. The browser integration, allowing access from multiple devices are features that encourage good password polices. I use LastPass, have done for over a decade, on Linux, Windows, MacOS, iOS and it means I have unique passwords for well over 200 online sevices.
Using an offline password storage means I would be reusing password, using shorter passwords, writing them down, and having to carry a little black book of passwords around. All of this is inherently insecure.
LastPass, though, have been woeful in their management of information. They seem to have a head-in-the-sand approach. They could and should have FORCED everyone to change their master password to at least 12 characters. Mine was, but my wife’s was not. She was quite prepared to say that she didn’t fully understand the need for this., and thus was going to ignore it. So even their latest missive failed in its reception.
So, now, I have to go through 200+ sites and change passwords. Oh, what deep joy.
The “cloud” can be safe if you do it right, of which both Apple with iCloud Keychain and 1Password do.
The critical thing is to encrypt the data not only with the user’s password, not ONLY with using a strong iteration count for the password hash to turn the user’s password into the key, but to ALSO effectively entangle the key with a random secret that is kept on-device and which needs to be explicitly migrated to new devices.
This means if you lose all your devices your passwords MUST be unrecoverable, but its a tradeoff that provides security against “the cloud storage got hacked” threat model. I’m pretty high on the paranoid security front, and I’m a very happy 1Password user because
1: Password reuse is a huge problem, and this eliminates it
2: I have a multi-platform ecosystem (Windows, Mac, iOS) that this allows me to sync across.
3: This makes my life EASIER as I don’t have to type in a gazillion passwords while making it more secure by #1
4: The security architecture specifically assumes the “cloud” is hostile.
…at LEAST as safe as experian, tesla, microsoft, Apple, solarwinds, …
And the movie Studio that was caught a few years ago with embarrassing comments in Emails that were made public by foreign hackers.
That is no safer or less safe than any other online password storage manager with encryption. Conrrary to what people believe, Lastpass’ system did exactly what it was designed to do. Modern encryption algorithms are uncrackable and will remain so forever. The math has been done and even if every molecule the universe was dedicated to cracking the encryption, it would still take over a million years to break it, thus being useless to any living being.
Every single password vault in their system is entirely safe, unless for some reason some people chose absolutely abysmal passwords for their master, and got hacked that way. In that case they deserve whatever happens to them. I use Lastpass, have for years, and still don’t have any issues. No compromised passwords and no issues. My master password is over 30 characters long and will never be cracked. It’s the only password I actually need to no, and I never need to change it in my lifetime.
“Conrrary to what people believe, Lastpass’ system did exactly what it was designed to do.”
Oh? It was designed to allow users to use insecure root password / iteration combos?
I guess if you consider that management decision to be “by design” maybe so, sure.
It’s also a massive fail and another swollen black eye for the thrice-hacked company.
(You can stop posting the “every molecule” claptrap every time, it’s still inapplicable nonsense.)
LastPass was not meant to teach you about best practices on what password to choose. So, yeah, it did do exactly what it was supposed to do.
This entire page is dedicated to the harsh reality that everything can and will be hacked eventually and that many times this happens via exploiting the weakest link in all systems: people. LP was no different.
“LastPass was not meant to teach you about best practices on what password to choose.”
No, it was meant to keep ALL your userland passwords secure, and because of a patently stupid decision by the management it failed to enforce what they even acknowledged were the most basic standards for doing that. It stored for example banking passwords where competent security-minded management ENFORCED a strong password regime, only to be undermined because LP had zero such qualms about allowing users to be eventually hacked.
LP had several opportunities to close this gap over years and still fails today.
*Another apologist grabs some pine.
It’s a fricking password manager, the holy grail, ostensibly for GREATER security than the individual password regimes that it is being tasked with storing. It’s supposed to be MORE secure by default but made nearly no attempt to at all ensure that. Their excuse of running into some corruption in individual vaults as the reason they “couldn’t” be upgraded to secure minimums is absolutely possible, but what did they effectively do to mitigate the problem? Identify the corruption sources and tell users they needed to blow out that entry and re-enter it? No, they did FWIW nothing, they let it go for years like that. Ongoing in fact if this reporting is correct. There’s no excuse. There’s no hand-waving that makes the fail go away. It failed to enforce minimum standards for pw security and punted for years after realizing it. FTFY.
Thanks for the reminder, I chose bitwarden, maybe slightly better? Time for me to increase iterarions again and update my master password. The battle never ends
Brian, thanks for that “dummy proof” explanation of “iterations”. My iterations in my new P.W.M.(I left L.P.) are set at 2 million.
So previously requirement was less than 12 characters? Horrible…
Thanks, Brian, for giving us a chuckle with the very apt title you chose for your article!
Agree! For me it’s “Dead Horse & Battery, Bent Staple”.
Every vault that was accessed at LastPass was encrypted. LastPass does not store passwords, so passwords were not stolen. LastPass has been properly audited and their implementation of the strongest mathematically proven encryption algorithms available has been shown to be safe and sound. I wonder how many of LastPass’s competitors with their “proprietary encryption algorithms” can truly make that claim. There are only three ways to open those stolen vaults, know the password, guess the password or brute-force the password [with massive computer resources]. The encryption itself cannot be broken. As usual, the weakest link is the user that uses short passwords, or passwords that contain mostly dictionary words or numbers. Yes, LastPass should have been more pro-active in enforcing strong master passwords, but at the end of the day, if a LastPass user’s password has been guessed or brute-forced, that responsibility lies firmly with the user.
Your analysis of the “guessing time for a single GPU” is skewed, because you are using decade old iterations figures on current generation high-end discrete GPUs. 10 years ago, discrete GPUs were [possibly] as many three orders of magnitude slower than they are today and the embedded Intel GPUs were simply pathetic in comparison to those GPUs. Back then, the number of iterations used by LastPass was in line with being safe [with the computing power available then]. You forget that these iterations are computed in the web browser. Try running 600,000 iterations of AES256 encryption on a Windows XP Core 2 CPU [with embedded GPU] computer, with a 200GB hard drive, 1 GB of RAM, using Windows Explorer… yeah, good luck with that.
Needless to say, I remain a LastPass user [and my Master Password runs off the end of the input frame with all character types in use].
“LastPass does not store passwords, so passwords were not stolen.”
And after this facepalm statement you give them a “pass” for not forcing
users to upgrade to a secure length/iteration combination for many YEARS.
Given their ONLY product is meant to secure all the keys to user’s kingdom,
not requiring users to use the service securely is inherently a massive fail.
Fact. One that has now bit THEM along with all the users who were burned.
Allowing people to use it insecurely was a purely stupid decision.
Purely stupid decisions don’t need apologists winding on about encryption
being “unbreakable” as if that has any actual bearing on this conversation.
Deliberately hobby-horsing over it is pointless and deliberately missing the point,
as it appears you just don’t accept/understand the basic tenet that it’s SOP for
ANY security-minding app/feature/service to ENFORCE security minimums for
pw length/complexity specifically because they ARE INTENDED TO BE SECURE,
even when users who aren’t trained in security use the service. Think a tiny bit.
Anybody have any ideas how many runs Apple makes with iCloud Keychain?
We never trusted these 3rd party or browser extension password managers, instead using a modular password scheme and an excel table. But when iCloud Keychain for iOS came ca. 2014 we converted over. We figured Apple had the resources to do PWM right and if they breached we would quickly know.
But because so much of what Apple does runs underneath the hood, and through simplified and minimally customizable user interfaces, we never see things like selectable encryption runs.
In maybe 2011 or 12 I wrote to Mr Cook asking for an Apple p/w manager and was pleased in 2014; it launched with a 15 character password generator. A few years after that, I wrote again bc asking for more than 15 characters. Security replied tha at that time was 15 adequate, but a couple years ago bumped it to 20-characters.
So Apple does make visible security, UI and feature upgrades but I’m wondering what they’ve done to prevent vulnerability to offline cracking should they ever be breached.
Can anybody give insight here?
Apple provides a very comprehensive security guide:
https://help.apple.com/pdf/security/en_US/apple-platform-security-guide.pdf
This is documented in the “Password and password management” section.
Bitwarden increased the iteration requirement February 2023. Likewise, they did not require existing accounts to increase their iterations for the key. They also did not do a good job of notifying existing accounts of the change.
I have increased the iterations on my key beyond the minimum recommended. I have only a few devices which will be slower accessing, but I am trying not to be the easy target.
I am off to complain of the lack of good notification and maybe re-evaluate options.
I changed half my passwords after the hack. When I went back to finish the job, guess what? NO WAY to see what PW’s you have already changed or not. LP removed the PW AGE field and refuses to put it back. LP gave standard PR BS and said I would have to change ALL 400-500 passwords AGAIN!
PW age is a useful metric! Why would they get rid of it besides incompetence?
My password manager is entirely offline and since it is solely for me, it sits on my computer desk. It cost $8 and is a box of index cards. It can be hacked only by someone breaking into the house.
It is not as easy to use as these password managers, but ease of use has been demonstrated repeatedly to be overrated.
My password manager is also entirely off line in a notebook in my home. I like your idea of index cards and will consider switching to that. I don’t trust password managers. Anything can be hacked.
This method makes any sort of backup into a challenge. A house fire or similar event is bad enough but losing all passwords adds stress to the loss.
agree. I used a notebook, then a little database, then Excel before LastPass. Little paper books are totally inadequate if you have to go anywhere, use multiple computers, and of course frequently need to add/modify accounts and passwords.
Most people I attempt to convince to using strong passwords are resistant. Convenience vs security. Human nature is the weak link and LastPass may try to insist on enforcing strong master passwords but it is not realistic for them or any other company to force people gainsta their will.
As a LastPass user I very much appreciate this reporting. I am fortunate in that a longer master password and increased iterations have been in effect for some time. Nevertheless I took steps to reduce my vulnerability as a result of these detailed reports. My remaining concern is that the internal security culture within LastPass may not be up to the job. To me it is most worrisome that the vault was reportedly exfiltrated from an employee’s residence. If accurate this event seems most damaging to the company’s reputation. It would be helpful to see more reporting along those lines. Thank you to Krebs.
That is incorrect. A security flaw in a top security exec’s home server, due to Plex, allowed them access to his server. This then allowed access to the off-site system (he was working from home) through his credentials after they had unfettered access to his home network.This is no different than any other work from home situation. This is, among many other reasons, why working from home shouldn’t be allowed, in ANY industry.
However, no company on planet Earth is immune to infiltration by bad actors and there will never be a circumstance or situation where they ever will be. It isn’t because of bad practices or lazy employees. It is because I order for a system to function, it needs to be accessible to users. This very fact alone makes all systems vulnerable, and hackable. Every company has been hacked, either with or without their knowledge. Lastpass’ just had the guts to admit it.
“This is no different than any other work from home situation.”
In a word, wrong. They had limited the vault access to “4” people.
One of the 4 super-trusted engineers was completely insecure,
and obviously so. They did not have security in depth sufficient
to stop stolen credentials from being allowed to download LP’s
ENTIRE VAULT. They assumed their 4 were untouchable pros,
and it’s entirely obvious they DID NOT AUDIT SUFFICIENTLY.
Meanwhile, they did not force users to use the service securely,
and failed to enforce their own known BASIC best practices.
Their excuse now is that “our users read and follow directions,
so we didn’t need to make sure people used LP securely.”
That single arrogant failure sums up their other woes nicely.
“Every company has been hacked, either with or without their knowledge. Lastpass’ just had the guts to admit it.”
-Red herring horsecrap straight from the oxcart.
” It is because I order for a system to function, it needs to be accessible to users. ”
Who needs security in depth when you’re making these wonderful excuses?
Attackers either exfiltrated the ENTIRE vault through that user’s compromised LAN,
(which a rudimentary audit would have concluded was completely insecure for task)
OR they were able to download it using a different IP altogether w/ the stolen creds
without being flagged AT ALL by LP’s internal sentries. All eggs, 1 basket, no checks.
Keep the excuses coming faster, talk about all the molecules in the universe again.
How is ‘top security exec’’s corp workstation was compromised via home Plex server’ not an example of bad practices and/or lazy employees? As someone in a massive org with almost 100% hybrid workforce serving billions of internet-facing app users with shockingly effective security controls around all of it, remote work is far from the issue here.
What could be done is to ask people to change their master password and change the passwords of the account inside the password vault, especially anything with elevatored or sensitive privileges. That is the point of a password manager is to make changing passwords easy.
Then if your password vault is decrypted and exposed it does zero damage to the victim.
The hack was actually more serious than most people realise and there were also issues that nobody else had thought of, which I mention here.
https://michaels.me.uk/lastpass-hacked-how-serious-is-it-things-you-may-not-know/
If your vault is encrypted and you follow modern password recommendations, your vault isn’t even remotely at risk. Modern encryption is uncrackable, even with future quantum computing technology. Modern encryption will never be crackable, ever.
Your pontificating about future-proof encryption is laughable.
Face it, you’re repeatedly a deliberate apologist for Lastpass.
Give it a rest.
I’ve gotta strongly disagree. Security is not as black and white as you make it out to be. For starters, quantum safe cryptography isn’t common, not even in 2023. I’m not a big fan of you jinxing it, now I’m afraid experts may find holes in the most advanced cryptography lol. Secondly, a good master password is something you should memorize, we can only remember so much. Often people use that master password in more than one place. If one service doesn’t protect it, your master password is now known and it’s complexity doesn’t matter. Criminals add it to their brute forcing script and you’re done. There’s also the possibility for malware to intercept it, etc… There’s absolutely no. such. thing. as perfect security. Security evolves and always has to keep improving.
“now I’m afraid experts may find holes in the most advanced cryptography lol.”
Yes, lol. As long as you can manage it, as long as it makes sense to do so.
bleepingcomputer.com/news/security/new-marvin-attack-revives-25-year-old-decryption-flaw-in-rsa/
After the breach I checked and I was only at 500 iterations as a long time last pass user. I checked my wife and she had 5000 as a newer user. They never updated or even sent out a notice to check before the breach.
I still use Last Pass and have always had a very long password and yubikey to access the vault. One thing that has not been clear is if having a yubikey further increases the difficulty of decrypting a stolen vault, or if it only is used to access a vault online by the user, so villains still only have to solve for the password to access the contents of the vault.
YubiKery is a form of MFA (multi-factor authentication) and decrypting the vault doesn’t need MFA. Logging into the vault, yes it’s needed, but decrypting doesn’t. 🙁
I’ve been using LastPass with a password that is over 30 characters and a Yubikey from the onset, several years before the breach.
The only thing I am unsure of is if the Yubikey applies only to logging in to the LastPass online vault, or if it still is needed to decrypt a stolen vault.
The Yubikey will only be a second factor for 2FA. Therefore, it doesn’t help with preventing decryption of the vault. The 30 character password however does go a long way.
Everyone should have random password strings of at least 16 characters or as many as the host will support, 24 is much better to protect against brute force attacks using rainbow tables.
I put blame on both users and lastpass, moreso on the latter. Security conscious users should know better than to use poor passwords, and anyone using a password manager has at least some rudimentary concept of the importance of security. Lastpass obviously failed in enforcing minimum standards across user base. Lastpass should be held to higher standards than users as they are the ones selling a security product. Given lastpass’s history, it’s a wonder people continue to use it when competent alternatives exist.
– what “competent alternatives?”
are you referring to?
Alternatives I would consider are 1Password, Keepass and Bitwarden.
Another mentioned BW was not forcing upgraded security on existing, I have no idea whether that’s true, because I don’t trust online password management beyond what I set up.
bleepingcomputer.com/news/security/fake-bitwarden-sites-push-new-zenrat-password-stealing-malware/
https://youtu.be/Nma8NkLQl1Q?si=HEZ8EkGooDKlS-ci
What is Watson X and how does it differ from other AI security programs?
Remember the IBM AI that went on Jeopardy? Flash forward to 2023,
the “x” means whatever you want it to mean, in a marketing sense.
WatsonX’s marketing itself as a very useful savant. Not a sentient,
not a jazz artist, not a CEO, just a machine learning specific things.
They’re right, AI needs to be deeply and strictly curated to be useful.
Limiting scope to the subject matter is probably a good default start,
how exactly it differs from other curated AI regimes is all NDA details…
and I have no specific idea other than that details are very important.
It’s like the evolution of intelligence itself vs the final product.
You can make a machine that wins at tic tac toe every time, win.
Don’t give it the launch codes and just assume it knows what to do.
I second a couple of comments above, that LastPass is really further failing users by NOT having a report available to users to show “All passwords in my vault which have not been changed since ” (with the obvious default date being “the date when users’ encrypted vaults were stolen in the 2022 breach of LastPass).
This makes it too difficult to know which passwords inside users’ vaults the users should change, now, against the possibility that their stolen vault copies would eventually be brute forced. (I have over 1000 passwords in my LastPass vault, so manually checking one at a time to see the password history is impractical).
Brian, please publicly further shame LastPass about this particular point, to try to get them to implement this rather obvious function. Thanks.
1 year, 500 iterations, $7500, but then they (intruders) could be lucky and hit it in first brute force candidate. 1 year is only theoretical and even that is a ballpark number depending on attacker’s resources.
The right thing to do is to inform users of their risk. Even if you used a strong master password, you should change your passwords and move crypto to different wallets. Your strong master password could be exposed in other breaches or it may not be as strong as you think it is. Mitigate the risks even if you feel safe.
By notifying everyone that the minimum length of the master password is 12 characters, hasn’t that made it easier for crackers to crack the master password? Now they no longer have to try passwords of less than 12 characters, they can just start with 12 characters and work their way up until they crack the master password. Still quite a task, but easier now.
That’s to misunderstand how numbers work.
Remember. Online password managers have multifactor “authentication” which doesn’t apply to breached or leaked data. Hackers don’t need MFA in this case. It leads to a false sense of security and many users choose weak master passwords because they think they’re protected by MFA. So they wind up being decrypted early.
For me, offline password managers with multifactor encryption (all factors needed to decrypt) are superior. Users like me can handle backups and syncing ourselves.
One of the reasons I created my password website that is a little old fashioned and most people have either ignored me or ridiculed it for its simplicity (not an app on a smartphone etc.). It’s free to use and if the site gets hacked no personal data is stored. If you want to check out for yourself – justapassword.com