
Image: Shutterstock.
Apple and the satellite-based broadband service Starlink each recently took steps to address new research into the potential security and privacy implications of how their services geo-locate devices. Researchers from the University of Maryland say they relied on publicly available data from Apple to track the location of billions of devices globally — including non-Apple devices like Starlink systems — and found they could use this data to monitor the destruction of Gaza, as well as the movements and in many cases identities of Russian and Ukrainian troops.
At issue is the way that Apple collects and publicly shares information about the precise location of all Wi-Fi access points seen by its devices. Apple collects this location data to give Apple devices a crowdsourced, low-power alternative to constantly requesting global positioning system (GPS) coordinates.
Both Apple and Google operate their own Wi-Fi-based Positioning Systems (WPS) that obtain certain hardware identifiers from all wireless access points that come within range of their mobile devices. Both record the Media Access Control (MAC) address that a Wi-FI access point uses, known as a Basic Service Set Identifier or BSSID.
Periodically, Apple and Google mobile devices will forward their locations — by querying GPS and/or by using cellular towers as landmarks — along with any nearby BSSIDs. This combination of data allows Apple and Google devices to figure out where they are within a few feet or meters, and it’s what allows your mobile phone to continue displaying your planned route even when the device can’t get a fix on GPS.
With Google’s WPS, a wireless device submits a list of nearby Wi-Fi access point BSSIDs and their signal strengths — via an application programming interface (API) request to Google — whose WPS responds with the device’s computed position. Google’s WPS requires at least two BSSIDs to calculate a device’s approximate position.
Apple’s WPS also accepts a list of nearby BSSIDs, but instead of computing the device’s location based off the set of observed access points and their received signal strengths and then reporting that result to the user, Apple’s API will return the geolocations of up to 400 more BSSIDs that are nearby the one requested. It then uses approximately eight of those BSSIDs to work out the user’s location based on known landmarks.
In essence, Google’s WPS computes the user’s location and shares it with the device. Apple’s WPS gives its devices a large enough amount of data about the location of known access points in the area that the devices can do that estimation on their own.
That’s according to two researchers at the University of Maryland, who theorized they could use the verbosity of Apple’s API to map the movement of individual devices into and out of virtually any defined area of the world. The UMD pair said they spent a month early in their research continuously querying the API, asking it for the location of more than a billion BSSIDs generated at random.
They learned that while only about three million of those randomly generated BSSIDs were known to Apple’s Wi-Fi geolocation API, Apple also returned an additional 488 million BSSID locations already stored in its WPS from other lookups.
UMD Associate Professor David Levin and Ph.D student Erik Rye found they could mostly avoid requesting unallocated BSSIDs by consulting the list of BSSID ranges assigned to specific device manufacturers. That list is maintained by the Institute of Electrical and Electronics Engineers (IEEE), which is also sponsoring the privacy and security conference where Rye is slated to present the UMD research later today.
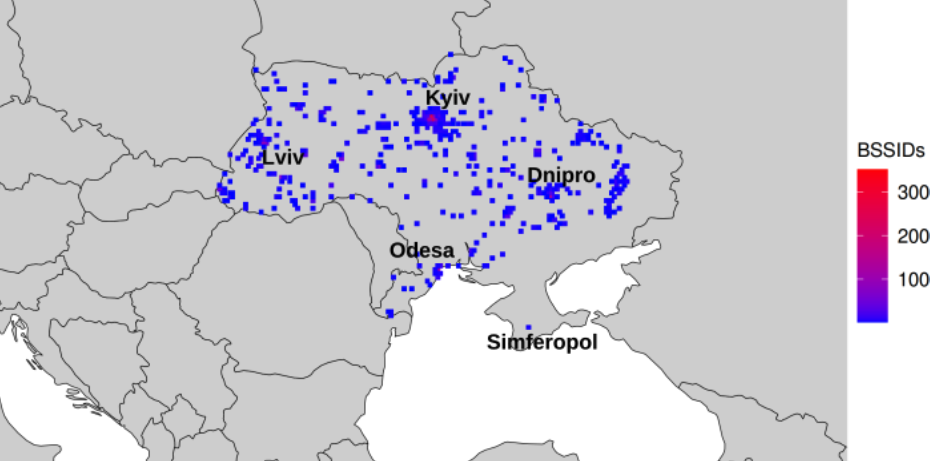
Plotting the locations returned by Apple’s WPS between November 2022 and November 2023, Levin and Rye saw they had a near global view of the locations tied to more than two billion Wi-Fi access points. The map showed geolocated access points in nearly every corner of the globe, apart from almost the entirety of China, vast stretches of desert wilderness in central Australia and Africa, and deep in the rainforests of South America.
The researchers said that by zeroing in on or “geofencing” other smaller regions indexed by Apple’s location API, they could monitor how Wi-Fi access points moved over time. Why might that be a big deal? They found that by geofencing active conflict zones in Ukraine, they were able to determine the location and movement of Starlink devices used by both Ukrainian and Russian forces.
The reason they were able to do that is that each Starlink terminal — the dish and associated hardware that allows a Starlink customer to receive Internet service from a constellation of orbiting Starlink satellites — includes its own Wi-Fi access point, whose location is going to be automatically indexed by any nearby Apple devices that have location services enabled.
The University of Maryland team geo-fenced various conflict zones in Ukraine, and identified at least 3,722 Starlink terminals geolocated in Ukraine.
“We find what appear to be personal devices being brought by military personnel into war zones, exposing pre-deployment sites and military positions,” the researchers wrote. “Our results also show individuals who have left Ukraine to a wide range of countries, validating public reports of where Ukrainian refugees have resettled.”
In an interview with KrebsOnSecurity, the UMD team said they found that in addition to exposing Russian troop pre-deployment sites, the location data made it easy to see where devices in contested regions originated from.
“This includes residential addresses throughout the world,” Levin said. “We even believe we can identify people who have joined the Ukraine Foreign Legion.”
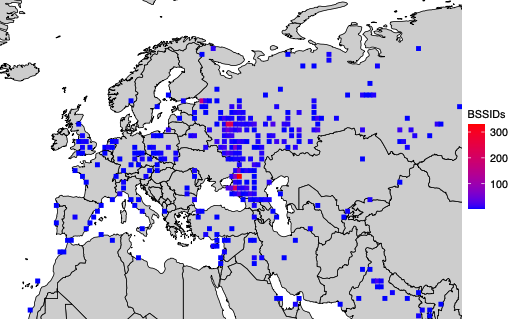
A simplified map of where BSSIDs that enter the Donbas and Crimea regions of Ukraine originate. Image: UMD.
Levin and Rye said they shared their findings with Starlink in March 2024, and that Starlink told them the company began shipping software updates in 2023 that force Starlink access points to randomize their BSSIDs.
Starlink’s parent SpaceX did not respond to requests for comment. But the researchers shared a graphic they said was created from their Starlink BSSID monitoring data, which shows that just in the past month there was a substantial drop in the number of Starlink devices that were geo-locatable using Apple’s API.
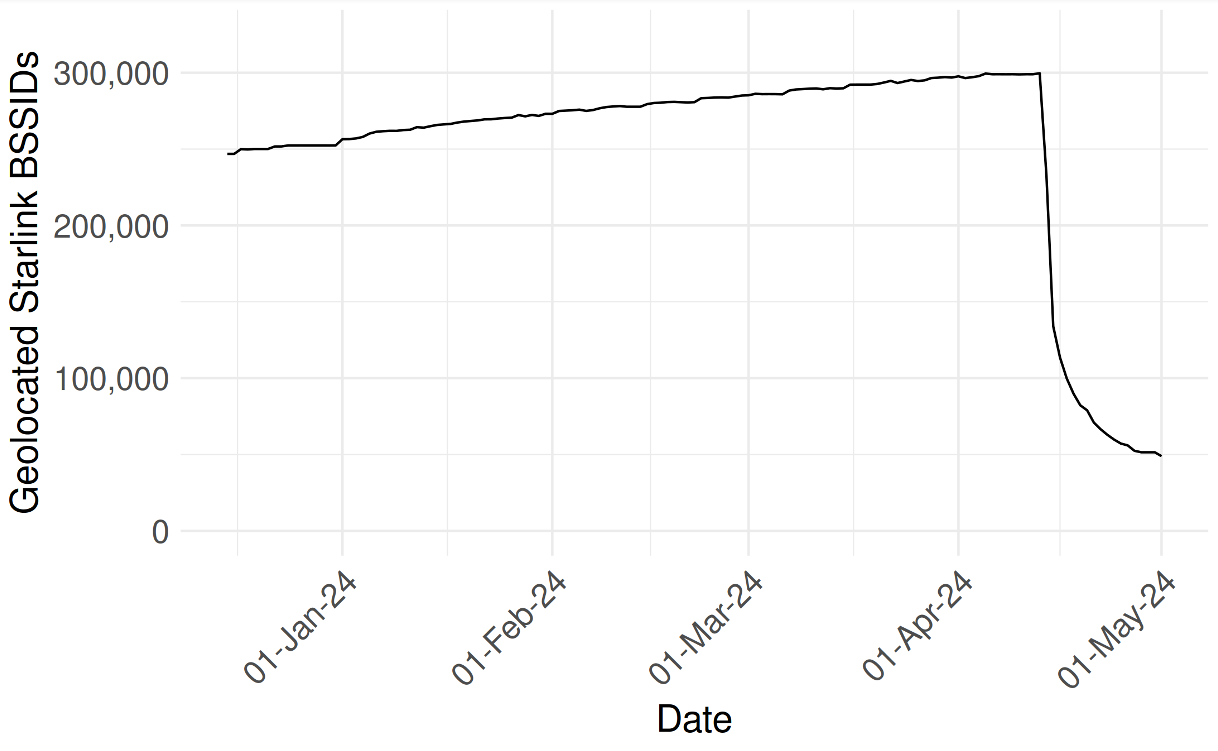
UMD researchers shared this graphic, which shows their ability to monitor the location and movement of Starlink devices by BSSID dropped precipitously in the past month.
They also shared a written statement they received from Starlink, which acknowledged that Starlink User Terminal routers originally used a static BSSID/MAC:
“In early 2023 a software update was released that randomized the main router BSSID. Subsequent software releases have included randomization of the BSSID of WiFi repeaters associated with the main router. Software updates that include the repeater randomization functionality are currently being deployed fleet-wide on a region-by-region basis. We believe the data outlined in your paper is based on Starlink main routers and or repeaters that were queried prior to receiving these randomization updates.”
The researchers also focused their geofencing on the Israel-Hamas war in Gaza, and were able to track the migration and disappearance of devices throughout the Gaza Strip as Israeli forces cut power to the country and bombing campaigns knocked out key infrastructure.
“As time progressed, the number of Gazan BSSIDs that are geolocatable continued to decline,” they wrote. “By the end of the month, only 28% of the original BSSIDs were still found in the Apple WPS.”
In late March 2024, Apple quietly updated its website to note that anyone can opt out of having the location of their wireless access points collected and shared by Apple — by appending “_nomap” to the end of the Wi-Fi access point’s name (SSID). Adding “_nomap” to your Wi-Fi network name also blocks Google from indexing its location.
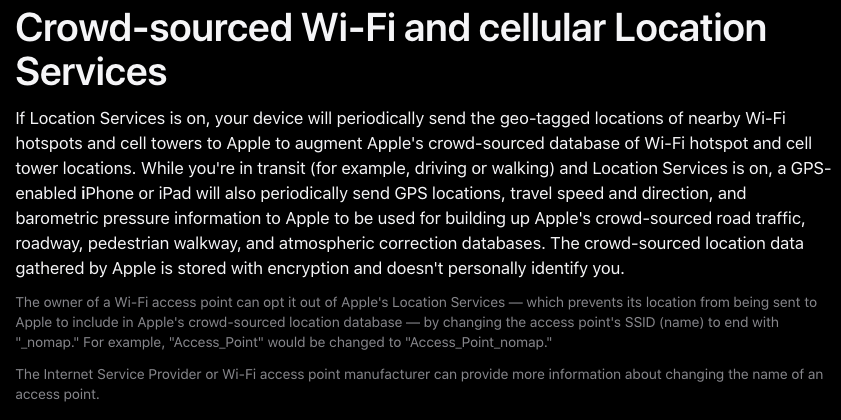
Apple updated its privacy and location services policy in March 2024 to allow people to opt out of having their Wi-Fi access point indexed by its service, by appending “_nomap” to the network’s name.
Asked about the changes, Apple said they have respected the “_nomap” flag on SSIDs for some time, but that this was only called out in a support article earlier this year.
Rye said Apple’s response addressed the most depressing aspect of their research: That there was previously no way for anyone to opt out of this data collection.
“You may not have Apple products, but if you have an access point and someone near you owns an Apple device, your BSSID will be in [Apple’s] database,” he said. “What’s important to note here is that every access point is being tracked, without opting in, whether they run an Apple device or not. Only after we disclosed this to Apple have they added the ability for people to opt out.”
The researchers said they hope Apple will consider additional safeguards, such as proactive ways to limit abuses of its location API.
“It’s a good first step,” Levin said of Apple’s privacy update in March. “But this data represents a really serious privacy vulnerability. I would hope Apple would put further restrictions on the use of its API, like rate-limiting these queries to keep people from accumulating massive amounts of data like we did.”
The UMD researchers said they omitted certain details from their study to protect the users they were able to track, noting that the methods they used could present risks for those fleeing abusive relationships or stalkers.
“We observe routers move between cities and countries, potentially representing their owner’s relocation or a business transaction between an old and new owner,” they wrote. “While there is not necessarily a 1-to-1 relationship between Wi-Fi routers and users, home routers typically only have several. If these users are vulnerable populations, such as those fleeing intimate partner violence or a stalker, their router simply being online can disclose their new location.”
The researchers said Wi-Fi access points that can be created using a mobile device’s built-in cellular modem do not create a location privacy risk for their users because mobile phone hotspots will choose a random BSSID when activated.
“Modern Android and iOS devices will choose a random BSSID when you go into hotspot mode,” he said. “Hotspots are already implementing the strongest recommendations for privacy protections. It’s other types of devices that don’t do that.”
For example, they discovered that certain commonly used travel routers compound the potential privacy risks.
“Because travel routers are frequently used on campers or boats, we see a significant number of them move between campgrounds, RV parks, and marinas,” the UMD duo wrote. “They are used by vacationers who move between residential dwellings and hotels. We have evidence of their use by military members as they deploy from their homes and bases to war zones.”
A copy of the UMD research is available here (PDF).
Update, May 22, 4:54 p.m. ET: Added response from Apple.




This is interesting. I assume my remote CCTV running through my router (apple TV hub) would be unaffected by deploying “_nomap”. Many other iOS features come to mind. “Find My” is one. Operates so well thanks to all those archived locations. Or am I being foolish?
” Apple’s API will return return the geolocations of up to 400 hundred more BSSIDs that are nearby the one requested. It then uses approximately eight of those BSSIDs to work out the user’s location based on known landmarks.”
You may have too many returns in that sentence Brian
Thanks.
“400 hundred”
Thanks for bringing this to light. It’s highly frustrating that Apple is putting the onus for improving the security on people that might not even be in their ecosystem. Add on to that most AP owners probably wouldn’t know how to rename their AP outside of the initial setup program or that most normal people don’t keep up to date on security news and I’d guess it’s a very small percentage of users that will actually implement the remedy.
OK, so to improve the privacy of my home WiFi router (which includes an access point) I log on as admin, change the SSID (a.k.a. the network name so that it ends in _nomap, then update all devices that connect to it.
Same with café owners who provide free public WiFi!
Does this also protect against privacy issues with Google’s WPS?
> Same with café owners who provide free public WiFi!
Why would the owner of a café, whose location is presumably public knowledgs, need to be worried about their BSSID being stored?
> Does this also protect against privacy issues with Google’s WPS?
Yes. Google has supported _nomap for about a decade already.
Updating all the devices is the big one. Just adding “_nomap” to the end of the SSID will result in the average household having to change the network settings on quite a few devices to connect to the new SSID. Laziness + ignorance will win. Hopefully Apple are looking at swapping to a solution similar to Google’s to rectify this huge privacy issue.
Meanwhile when I get home, I’ll be closely checking both the router and Wi-FI extender for a randomise BSSID / MAC option. Saves me changing several devices (and explaining to the family why I want to change the SSID).
Yep, the minute you change the main Wi-Fi network SSID, all the things in your house that use the Wi-Fi have to be reauthenticated. It can be a serious PITA, depending on how many technological beings you have (or that have you!)
For most consumer-grade devices, I don’t think that the BSSID / MAC address of the Access Point (or of the Extender) cannot be ‘randomized’ … without the client STAtions having to manually find and log in to the network _each_ time they’re accessed. Geekspeak: I have yet to see devices which maintain an ESSID and yet randomly change their own BSSID.
It seems that the only avenue is to rely on the “good graces” of Apple and of Google to act according to their published policy, by, after a one-time change of MAC address (IF POSSIBLE), naming your SSID “MySSID_optout_nomap” .
(I sure wish the two behemoths could have settled on the same SafeWord… always adding the 13 character compound string “_optout_nomap” limits the flexibility in choosing a 32 character limit SSID name.)
Note that _filling_ the vendors’ location databases can be disabled within most browsers. How society ever let’em get away with having a browser scan SSIDs is incredible.
I am too lazy to read the paper, and wonder how many APs there are in North Korea. The map shown above does correlate well with the size of a countries economy
Google maps provides a way to opt out. I’m not sure if it opts you out of other services though.
To opt out, change the SSID (name) of your Wi-Fi access point (your wireless network name) so that it ends with “_nomap.” For example, if your SSID is “12345,” you would change it to “12345_nomap.”
So somebody did not read the full article before commenting, then?
It Crazy! Apple is suppose to have some of the Best Security? Think they need some work on that one lol. Thanks for the share. I have an IPhone, and IPad, n I also have a Router. Wow, maybe I should throw all of My Information out there and save Hackers the trouble lol
Thanks
Mystic
Do I understand this correctly, my SSID on a non Apple device should be modified to prevent them from mapping it? Plus, the notice for this was given in an Apple privacy notice that I never received because I do not own an Apple device?
“Do I understand this correctly, my SSID on a non Apple device should be modified to prevent them from mapping it?”
You misunderstood. It doesnt /prevent/ anything.
All it does is to pretty-please *ask* them not to include you in their list. Do you want to bet on it that they will actually honor your request ?
My thoughts exactly. What’s the point of making these changes to your SSID(s). Its a lot of work and besides the tech giants always get what they want anyway.
Google had been called out on this a long time ago. They chose the opt out approach by appending _nomap to an SSID. At least Apple chose the same string. But this should be an opt-in. How does this jive with EU GDPR which usually goes for opt-in for things?
Should to SSID changed to end with “_nomap” or “_nomap.”
Even this article beems to be confused which is the correct one.
Interesting for sure. But why the BLEEP should I actually need to change my SSID (and until I read this article I didn’t know about it, so I doubt the average home user will know or understand it) to stop the stickybeaks at Apple and Google doing their nonsense.
Opt-in or f-off out should be the default. Naive I know.
Apple did not respond to requests for comment. But in late March 2024, Apple quietly tweaked its privacy policy, allowing people to opt out of having the location of their wireless access points collected and shared by Apple — by appending “_nomap” to the end of the Wi-Fi access point’s name (SSID). Adding “_nomap” to your Wi-Fi network name also blocks Google from indexing its location.
It should be noted that the Google/Apple opt out (_nomap) needs to be at the end of SSID name. Whereas the Microsoft opt out (_optout) can be anywhere in the SSID name.
Therefore, to opt out of both, it would be in this order:
SSIDName_optout_nomap
The problem is, this is a really poor solution and should be unlawful. Many routers (D-Link for example) do not allow using underscores in the SSID name, therefore it’s not possible to opt out even if you want to. That is not consent.
My TDS router won’t allow the underscore symbol either, unfortunately. (Only letters and numbers are allowed.)
This thing is going to go the way of the DNT header flag. For a hot minute, some big companies were touting DNT as a way to opt out (Do Not Track) web browsing. But then they quietly stopped and now, nobody really honors it.
1. If one “hides” the name of their SSIDs through their router settings, will their BSSIDs still be indexed (if hiding works, is it necessary to append “_nomap”)?
2. Once a BSSID is indexed, how if at all can one get their information removed from the database (does Apple revise its database to reflect “_nomap”’s added after the fact)?
3. Will another Apple device user be able to negate “hiding” and see one’s BSSID/SSID information via the database (my own rudimentary tests are not definitive)?
The problem with hiding your SSID is that it stops your AP from broadcasting its presence, but then all of your devices have to broadcast that they’re looking for your WiFi network. So, when you’re in a coffee shop, your phone will be shouting “Is Johns_Wifi here?”.
That’s only if you have ‘automatically connect when in range’ enabled. If you exclusively connect to wifi manually it doesn’t broadcast looking for wifi until you check that box.
_nomap may no longer show you on a publicly accessible map. But I doubt very much an AP with _nomap will disappear from the dataset. And if a dataset exists, somebody has access to it…
My concern is that map with one country absent from it. How is this possible? Are they that good that they can just shut it down? I bring this up because when I peruse my server logs, attackers are not coming from Russian, Islamic, or .gov addresses. Attackers not coming from VPNs/TOR are coming from, i.e., Baidu and Tencent cloud IP addresses, sometimes geolocated to the continental USA… The map showing one absent country should be one hell of a wake up call to those who care about security and safety.
Today we are going to study a new word in class, kids! That word is “infiltrated”…
The Great Firewall is used for a Great many different things, including preventing a lot of ‘phone home’ type tasks on devices.
If the curious outline of missing data should tell us anything, it’s that someone long ago figured out how important this kind of data was, and we are just now reading about it being researched.
I’d rather hide my SSID if it works. Easier than changing my 30+ devices to a new SSID.
Did Lucius Fox forget to destroy the dark knights 1984 billionare toy? was that not a real movie?
Wait what? gotta stop eatin so much chinese and switch back to marios pizza.
Live long and prosper.. with space force and wafu pillows sleepers… ahhh clarrise stop
being so gosh darn jealous.
As a joke, maybe wear a full AU, suit and not carry any cell phone but not really an option. Someone probably has AI Side Channel Survallence that can figure out all the info they need without a target carrying any device. They probably can figure out now with all the cams deployed a general guess where, why, how, and possiblly what you might be up to. Sound familiar or have you seen this before? Minority report – precog pre crime. Trust your instincts.
You bring up a good point. AI augmented video surveillance and ubiquitous video cameras. Things like Arlo, Blink, Nest, and Ring literally everywhere. So if Apple and Google are trapping geolocation data/metadata off of personal devices, storing it and presenting that on an API, what makes anybody think that other vendors aren’t doing the same and more?
We’ve been getting surveilled for a long, long time. But it took the Internet to make the possibility of Orwellian surveillance a reality. Better yet for those that surveil, humans, being the sheeple we are, gleefully and joyfully took the best tool for the job, a personal connected device, to heart. We even go so far as to camp out, in lines a block long, to purchase the latest tool. Adding live video would probably be a minor technical matter at this point…
I dont expect an answer or anything, but I unfortunately get asked this a lot and likely wont reply back.
Even with all of these deterrents we cannot thwart the very things that they attempt to stop? Where do we draw the line between safety and oppression? How do we differentiate between observation and spying? We can philosophize this subject ad-nauseum.
I am seeing increased security emboldens them to do it MORE as they get free publicity for their acts (Think social media; TikTok, Youtube Shorts, etc). That “There’s something very important in there and I want it” mentality. We’ve done it in computer games. That rush from the now, more difficult challenge. Even if the crime doesnt yield anything useful.
Do I understand correctly that Apple’s WPS API is publicly accessible? That also seems like a big security no-no.
The WPS system literally only exists to be publicly accessible. The only difference in this scenario is the scale at which it was accessed.
Remember, the WPS uses cell phone location information as well as public WiFi hot spots. Think walking past a Panera bread or a Comcast store or the dentist or … you get the idea. _nomap works for that ONE wifi. If your neighbors don’t opt out, so what?! Your location will be aggregated via their hotspots (And nearby cell towers). The only real solution, which is no solution, is to turn off location data on your phone/device. Only enabling location services when you need it etc..
An interesting article insomuch as how big the released Genie grew vs how small the bottle really is…
The point of the article is in its title: geolocating your router. Changing the SSID will help prevent the hotspot from being mapped, but no one said anything about “nomap” preventing your location being tracked by your phone. So you seem to be confused about what “nomap” is supposed to do.
I don’t think he’s confused at all and he makes an excellent point. People reading this and concerned about the confidentiality of their location may not realize that collection of their own router data is the smaller concern. The nomap flag being on or off in one’s own router does nothing if, for example, I’m using a VPN to conceal my location yet my location is still known because my device Wi-Fi sees other neighbors Wi-if BSSIDs and Google knows where THEY are. Sure, one can disable location services in a browser or phone IF one is aware of this AND knows how to do so. But what about other computer programs that may query what neighbors routers my wifi sees, queries Apple or Google database for location info that I have zero control over and then sends my location to a bad actor?
I noticed that in some instances a period is at the end of the opt out text and in some no period was added. So is it “_nomap” or “_nomap.”
It is _optout_nomap without a trailing period
> without a trailing period
Both Apple and Google have the instructions WITH a trailing period. Even in quotes.
I’d bet money, that they only ‘honor’ it if present with trailing dot. Most people will likely use the intuitive _nomap, only to have evil Google go “HA HA…you didn’t use the dot…HA HA!!”
What a PITA these companies are.
To me, this is theft of services by anybody using this technique to locate WiFI routers. I think a class action suit awarding every router in their database $1 is apropos. After that, it should be an opt-in option.
This article seems very confused about the difference between an SSID, a BSSID, and a MAC address.
Gosh. I guess someone could find out where I live. If the don’t think of looking in the phone book.
If I add “_nomap,” will guests still be able to log in to my WiFi?
As long as they choose to connect to “YourSSID__nomap” [or better still, you renamed to “YourSSID_optout_nomap” ] . It will take explicit reconnection effort on their part… the saved network named just “YourSSID” will no longer work.
Regulation, now! The policy should always be Privacy First, then we can add “_map” to our SSIDs it we want to participate, or let the router manufacturers add a flag to their firmware for opting in (or something like that). Looking at you, Ron Wyden [Sen.-D-OR].
*if we want to participate
It wouldn’t stop the nefarious types from mapping SSIDs anyway, but at least our corporate overlords would have to comply.
Regulation, now! The policy should always be Privacy First, then we can add “_map” to our SSIDs if we want to participate or the router manufacturers add a flag to their firmware for opting in (or something like that). It wouldn’t stop the nefarious types from mapping SSIDs anyway, but at least our corporate overlords would have to comply. Looking at you, Ron Wyden [Sen.-D-OR].
A recent east coast tour with an active wardriving device identified 238,664 unique Access Point SSIDs on the path of the journey.
Of those, 11 have “_nomap” in the SSID, and 9 have “_optout” in the SSID.
Adoption of these don’t-track-me mechanisms are pretty dismal.
I’d be curious to know how access to Apple’s API works. I assume the researchers were given temporary access for their paper. There is probably an interesting story around who inside apple can use this api and how much. (Not to be paranoid but I bet a couple 3rd party vendors with boring names and 3 letter agencies as their only customer might be in that list)
Totally ridiculous. Why the f**k do we have to opt out to stop others from mapping OUR own hardware?
My thoughts exactly. What’s the point of making these changes to your SSID(s). Its a lot of work and besides the tech giants always get what they want anyway.