Instagram users should soon have more secure options for protecting their accounts against Internet bad guys. On Tuesday, the Facebook-owned social network said it is in the process of rolling out support for third-party authentication apps. Unfortunately, this welcome new security offering does nothing to block Instagram account takeovers when thieves manage to hijack a target’s mobile phone number — an increasingly common crime.
New two-factor authentication options Instagram says it is rolling out to users over the next few weeks.
For years, security experts have warned that hackers are exploiting weak authentication at Instagram to commandeer accounts. Instagram has long offered users a security option to have a one-time code sent via text message to a mobile device, but these codes can be intercepted via several methods (more on that in a bit).
The new authentication offering requires users to download a third-party app like Authy, Duo or Google Authenticator, which generates a one-time code that needs to be entered after the user supplies a password.
In a blog post Tuesday, Instagram said support for third-party authenticator apps “has begun to roll out and will be available to the global community in the coming weeks.
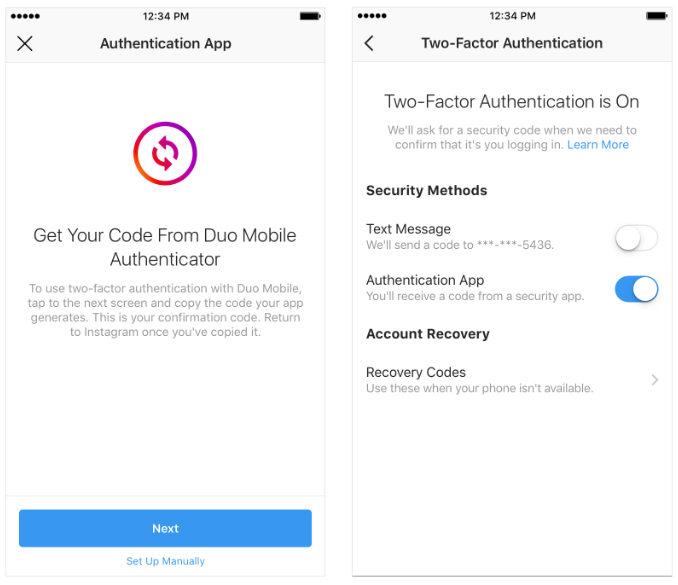
Instagram put me on a whitelist of accounts to get an early peek at the new security feature, so these options probably aren’t yet available to most users. But there’s a screenshot below that shows the multi-factor options available in the mobile app. When these options do become more widely available, Instagram says people can use a third-party app to receive a one-time code. To do this:
- Go to your Settings.
- Scroll down and tap Two-Factor Authentication.
- If you haven’t already turned two-factor authentication on, tap Get Started.
- Tap next to Authentication App, then follow the on-screen instructions.
- Enter the confirmation code from the third party authentication app to complete the process.
Note that if you have previously enabled SMS-based authentication, it is likely still enabled unless and until you disable it. The app also prompts users to save a series of recovery codes, which should be kept in a safe place in case one’s mobile device is ever lost.
WHAT IT DOESN’T FIX
Instagram has received quite a lot of bad press lately from publications reporting numerous people who had their accounts hijacked even though they had Instagram’s SMS authentication turned on. The thing is, many of those stories have been about people having their Instagram accounts hijacked because fraudsters were able to hijack their mobile phone number.
In these cases, the fraudsters were able to hijack the Instagram accounts because Instagram allows users to reset their account passwords with a single factor — using nothing more than a text message sent to a mobile number on file. And nothing in these new authentication offerings will change that for people who have shared their mobile number with Instagram.
Criminals can and do exploit SMS-based password reset requests to hijack Instagram accounts by executing unauthorized “SIM swaps,” i.e., tricking the target’s mobile provider into transferring the phone number to a device or account they control and intercepting the password reset link sent via SMS. Once they hijack the target’s mobile number, they can then reset the password for the associated Instagram account.
I asked Instagram if there was any way for people who have supplied the company with their phone number to turn off SMS-based password reset requests. I received this response from their PR folks:
“I can confirm that disabling SMS two factor will not disable the ability to reset a password via SMS,” a spokesperson said via email. “We recommend that the community use a third-party app for authentication, in place of SMS authentication. We’ll continue to iterate and improve on this product to keep people safe on our platform.”
Fraudulent SIM swaps illustrate the value of moving away from SMS-based authentication when more secure options are available. Doing so makes one less likely to be targeted by these phone number hijacks, which are generally perpetrated by determined, well-organized attackers.
The hard truth is that if an attacker wants control over your mobile number badly enough, he will get it. And if he does, he will likely gain access to far more than your Instagram account: Someone who hacks your phone number can then compromise any account that allows authentication or password resets via text message or automated phone call.
In May, KrebsOnSecurity documented the case of a Boston man who had his Instagram account hijacked after a crooked T-Mobile employee transferred his phone number to another device without authorization. Additionally, authorities in California and Florida have recently arrested several men accused of conducting similar attacks, and according to charging documents all of these individuals routinely worked with associates at mobile phone stores to carry out their heists.
In case you missed it, KrebsOnSecurity ran a story earlier this month about the sound security advice allegedly offered by one of the most accomplished SIM swappers of late, who recommended using Internet-based phone services like Google Voice in lieu of relying on mobile phone providers for multi-factor authentication.
Standard disclaimer: If SMS-based authentication is the strongest form of extra security a Web site offers, this is still far better than relying on just passwords for login security. If app-based options are available, take advantage of that. If the site in question offers hardware-based security keys, even better. 2fa.directory lists multi-factor authentication options for hundreds of sites, including probably many that you use on a daily basis. Take a moment this week to strengthen your login options.




Any website associated with Facebook is going to be a huge joke when it comes to security
Wouldn’t something like Signal with registration pin lock be a much simpler solution? My understanding is that the regular API can only send to registered accounts, and so even if the SIM was hijacked, the thief wouldn’t be able to receive a (Signal) SMS. It seems that this would be much simpler on implementation and rollout and more familiar in terms of usability.
Wouldn’t the thief be able to just install Signal on their phone using the new, duplicated SIM, importing the victim’s phone number?
Until we can get the mobile phone providers to be responsible and disallow SIM swaps with relative ease, then that possibility is the weak link in 2FA. FYI, I asked my provider (a large one) to set up my account so that my phone can only be swapped if I come in with a state issued photo ID. They declined and instead put a PIN lock on it. While that is better than nothing, it is NOWHERE near positive identification. If mobile phone providers were responsible for loss due to unauthorized SIM swaps, then I believe that weakness would be resolved in fairly short order…
If college students can easily buy fake IDs for booze, then I doubt organized criminals have a problem getting one.
Also in the article Brian mentions that SMS password recovery is only single factor (phone number), not 2FA as mentioned in your comment.
Of course, requiring ID does nothing to protect against a corrupt phone company employee who doesn’t need it to simply change your account details.
I asked my provider to set up my account so that my phone cannot be SIM-swapped at a mobile carrier’s store (only via call center). They acquiesced.
The reason I drag my feet adopting 2FA is I’d rather have my account taken over than my phone. I can handle that easier, and with less damage. I don’t even like giving my cell phone number to online businesses. I don’t even like giving my LANDLINE number to them either. Too many breaches in these servers now days.
Brian, you skipped several steps before step 1.
Step 0.1 Download authenticator app.
Step 0.2 Create authenticator app account.
Step 0.3 Configure authenticator app
Step 0.4 setup back password for authenticator app
Then after step 5
6 Download and create account on password vault app
7 configure master password on password vault
8 create entry for instagram account to save backup codes for authentication codes
Now you need three apps to use Instagram.
Authenticator apps using the TOTP (time-based one time password) protocol, for example Authy and Google Authenticator, don’t need accounts and only store the secrets on the mobile device. So there’s no need to create accounts to go with the apps.
And, many people already have one of these authenticator apps in use. Adding a new account is as simple as scanning a QR code with the device’s camera.
I’ve wanted to enable multi factor auth on joint banks accounts. The challenge is doing so effectively locks my wife out of the account. I’m looking for a fool proof way to use multi factor and other security methods that don’t leave my spouse unable to acces important accounts should I be incapacitated or die.
@Khürt
Perhaps the following is a solution to our concern?
LastPass has the capability to set up emergency access to your passwords after a set time period, e.g. 15 to 30 days, as explained on their website.
https://support.logmeininc.com/lastpass/help/set-up-and-manage-emergency-access-lp030013
If you are using something like Google Authenticator for the second factor, you should be able to have multiple copies of the app display the correct code. You have to set them up concurrently, but it does work. I have setup my phone and my tablet with Google Authenticator, so i can get the code with either device.
Check out Authy.
Unfortunately, when you share Authy (same time code entry or backup/restore), when a phone is stolen, if the attacker has access to authy, when they delete codes, the other phones sync the deletion and poof, all your 2FA account accesses are locked out.
The same for LastPass and shared folders or identities.
Stolen phones aren’t just a way to compromise your accounts, they are also a way to inflict a very likely non-recoverable lockout for everything stored in both Authenticator and Password vault apps.
“In these cases, the fraudsters were able to hijack the Instagram accounts because Instagram allows users to reset their account passwords with a single factor — using nothing more than a text message sent to a mobile number on file. And nothing in these new authentication offerings will change that for people who have shared their mobile number with Instagram.”
So glad you brought this up! This is exactly how I lost my account. A strong password and 2FA does NOT help against this. (side note: Also, does not help against social engineering.)
I have a short username which seems to be very popular. I get a few SMS with password reset links from Instagram/Facebook every week which drives me crazy, can’t believe how insecure that is and that they keep sending them! And yes, I receive multiple password reset emails as well, but luckily you can disable email reset for 60 days if Instagram notices that you receive a lot of them.
Call me paranoid, but I don’t have any trust in google 2fa. I have no doubt that google can and will access anything they want, or are asked to by the ABC departments. You know, for marketing purposes.
While I do think that’s a little paranoid, there are plenty of alternate authenticator apps out there, including TOTP features or plugins in various popular password managers. Some of these alternatives are even open source.
Just FYI Lastpass has used data blobs and encryption methodology that is rather good. I am sure there are others out there that also use this data blob storage. Long story short the data blob is unusable without a encryption key, password, and a 2FA token of some sort(if you choose this option). Without all of these things gaining access to the data is really really difficult, including but not limited to even Lastpass themselves not being able to assist in gaining access to the data if you lose the master pw.
they really are a TNO shop and I am sure there are others out there as well.
@Paranoid
You can use other apps that emulate Google authenticator, such as Microsoft authenticator and/or LastPass authenticator. They are functionally equivalent wrt the algorithm and therefore the time-based passwords are identical no matter which of these compatible apps you use. LastPass and perhaps MS authenticator allow you to backup your accounts to the cloud. In that way you don’t have to be concerned if your smartphone is lost or stolen, or when migrating to another phone.
Anyone of these 3 apps and any other Google authenticator compatible app can be used interchangeably.
So unless all of these companies are in league with each other, you shouldn’t worry. If they are, we don’t have a chance in any case. If they can’t be trusted, then they would already know your passwords.
My mobile phone company (in Canada) has moved away from PIN to voice recognition as a security measure when authenticating customers so that it’s employees do not have access to any secrets.
A fair number of financial institutions have introduced voice recognition security.
However, in this area as well, there is evidence that these security systems can be defeated – in this case, by voice impersonators. See the study done by the University of Eastern Finland.
https://www.uef.fi/-/voice-impersonators-can-fool-speaker-recognition-systems
Many of the businesses I use, phone company, health insurance, banking, now state they are recording my voice for ID purposes. I think this is a good idea. I can “modify” my voice but for a bad guy to pretend he is me, he needs to know what my voice sounds like, correct?
Companies could also have us say a phrase or entire sentence to be captured and used for future ID. How unique we make that phrase sound would be impossible for bad guys to know unless they access that database (which I’m sure they will figure out a way to do).
Voice ID is another hurdle for the bad guys and one I think most of them will fail at, study or no study. If they want to make this more secure, have us say a specific phrase (password equivalent) for their records. That could be a question from the business that we know the answer to and they record our response. True, some dimwit will forget the answer he gave, so it’s not entirely foolproof.
That’s kinda stupid. Your voice fingerprint is like real fingerprints, you leave it everywhere. Have they not seen the movie Sneakers?
Very good and easy to understand article. after I read about Instagram, and found instagram mod that can store images on a cellphone. is that safe? https://downloadiosapps.com/download-oginsta-for-iphone-and-ipad/
Instagram says “disabling SMS two factor will not disable the ability to reset a password via SMS”.
I must be missing something, because this seems idiotic. Surely a company as large and capable as Instagram wouldn’t be as brainless as this appears to imply…
Who not? Are is that sarcasm?
Not who? Is are sarcasm?
Perhaps this would work to protect against a password reset by SMS after the authenticator app is set up.
1) Get a Google voice number and change the mobile number for the SMS password reset to that.
2) Change the phone number for the SMS password reset to a land line number if you have one, or to something like (000) 000-000, which should then not go anywhere.
You know, after doing some thinking.. is it possible Brian created leakedsource and who knows what else? Who else could know all of the incredibly technical details that he seems to know.. and not have acquired it from years of blackhat web activity…
[CASE CLOSED]
No, he is so gangster, he invented the Internet 30 years ago with Gore. It’s part of their evil plan to collect the largest quantity of cat videos on the planet.
Not everyone has a voice to use up voice recognition with. Why should we be excluded from *our* accounts because some of don’t have a literal voice?
Are you f-ing kidding me? God you are one narcissistic POS. “Not everyone has a voice….” Have you ever seen Star Trek? “The needs of the many outweigh the needs of the few”. How about we secure the 99.99999999% of people that DO have a voice first? Then we can worry about you and the other 10 people on the planet that don’t.
He wasn’t advocating *not* having voice recognition. He was advocating that security engineers designing these systems must also think carefully about the failure scenarios.
Who’s the narcissistic jerk now?
Do you also eschew those who ask for recovery codes because “we secure the 99.99999999% of people that DO have” their phones with them at all times? Wow.
Don’t worry, voice based systems are a stupid idea. They’re at best theater (theatre). Plenty of movies have shown how stupid an idea it is.
Movies? Try lyrebird.ai
Movies? Try lyrebird
To give Instagram the benefit of the doubt, the PR krewe said, “We’ll continue to iterate and improve on this …” .
It’s necessary for security programmers to iterate and improve. Any security team who says, “ok we fixed our security and it’s all set,” is demonstrating their incompetence.
It sounds like Instagram knows it’s dealing with smart, motivated, and malicious cybercreeps.
The TOTP (time-based one time password) protocol is time tested, and the Google Authenticator is open source. So security researchers have taken a close look.
“The app also prompts users to save a series of recovery codes, which should be kept in a safe place in case one’s mobile device is ever lost.”
This should be MANDATORY. Not “prompts users”.
Because it isn’t “in case one’s mobile device is ever lost”, it is “*WHEN* one’s mobile device or tablet gets *STOLEN*”.
Phones are not authentication. They’re like a wallet. They are physical *bearer tokens*, at best.
After trying a number of authenticator apps, I now use Authy because it can be installed on more than one device, which is very handy if you lose your phone, or it dies (as happened to me recently). The data is backed up to the cloud (encrypted with a password you choose) and access to the app is controlled by fingerprint or PIN.
Strangely enough, I can only choose SMS OTP as 2FA method on Instagram, no Authenticator option here?
Good for Instagram for choosing to add authentication options that actually work. Unfortunately, even now in 2018, there are large Internet companies that either still don’t have a clue or truly just don’t care about providing secure token-based authentication options to users to help protect their accounts… (or, to use their ridiculous industry buzz-phrase, “to enhance their user experience”).
Yeah, I’m looking at you Yahoo!