Trial Ends in Guilty Verdict for DDoS-for-Hire Boss
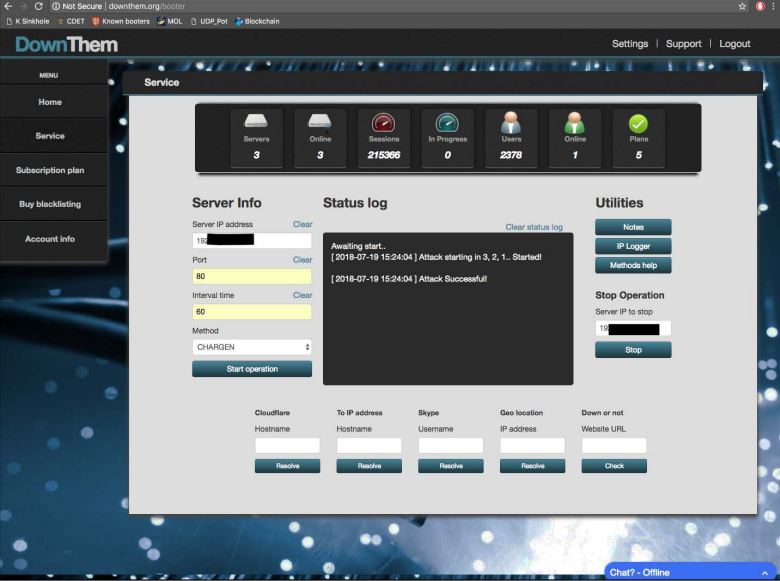
A jury in California today reached a guilty verdict in the trial of Matthew Gatrel, a St. Charles, Ill. man charged in 2018 with operating two online services that allowed paying customers to launch powerful distributed denial-of-service (DDoS) attacks against Internet users and websites. Gatrel’s conviction comes roughly two weeks after his co-conspirator pleaded guilty to criminal charges related to running the services.