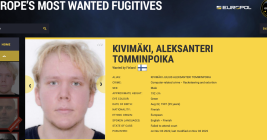
Arrests in $400M SIM-Swap Tied to Heist at FTX?
Three Americans were charged this week with stealing more than $400 million in a November 2022 SIM-swapping attack. The U.S. government did not name the victim organization, but there is every indication that the money was stolen from the now-defunct cryptocurrency exchange FTX, which had just filed for bankruptcy on that same day.