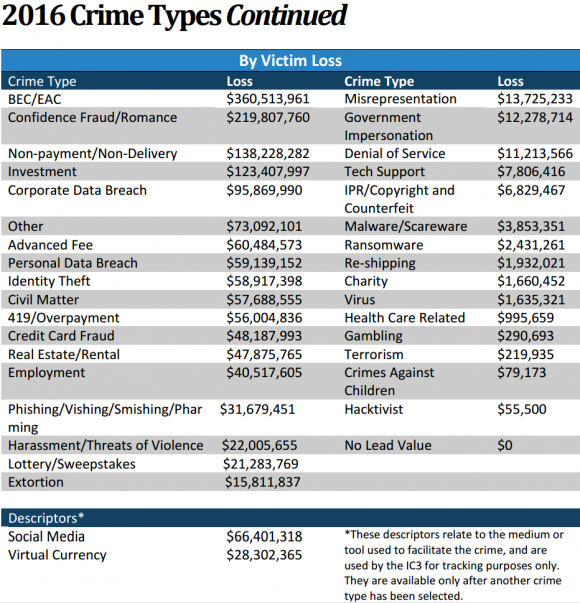
B&B Theatres, a company that owns and operates the 7th-largest theater chain in America, says it is investigating a breach of its credit card systems. The acknowledgment comes just days after KrebsOnSecurity reached out to the company for comment on reports from financial industry sources who said they suspected the cinema chain has been leaking customer credit card data to cyber thieves for the past two years.
 Headquartered in Gladstone, Missouri, B&B Theatres operates approximately 400 screens across 50 locations in seven states, including Arkansas, Arizona, Florida, Kansas, Missouri, Mississippi, Nebraska, Oklahoma and Texas.
Headquartered in Gladstone, Missouri, B&B Theatres operates approximately 400 screens across 50 locations in seven states, including Arkansas, Arizona, Florida, Kansas, Missouri, Mississippi, Nebraska, Oklahoma and Texas.
In a written statement forwarded by B&B spokesman Paul Farnsworth, the company said B&B Theatres was made aware of a potential breach by a local banking partner in one of its communities.
“Upon being notified we immediately engaged Trustwave, a third party security firm recommended to B&B by partners at major credit card brands, to work with our internal I.T. resources to contain the breach and mitigate any further potential penetration,” the statement reads. “While some malware was identified on B&B systems that dated back to 2015, the investigation completed by Trustwave did not conclude that customer data was at risk on all B&B systems for the entirety of the breach.”
The statement continued:
“Trustwave’s investigation has since shown the breach to be contained to the satisfaction of our processing partners as well as the major credit card brands. B&B Theatres values the security of our customer’s data and will continue to implement the latest available technologies to keep our networks & systems secure into the future.”
In June, sources at two separate U.S.-based financial institutions reached out to KrebsOnSecurity about alerts they’d received privately from the credit card associations regarding lists of card numbers that were thought to have been compromised in a recent breach.
The credit card companies generally do not tell financial institutions in these alerts which merchants got breached, leaving banks and credit unions to work backwards from those lists of compromised cards to a so-called “common point-of-purchase” (CPP).
In addition to lists of potentially compromised card numbers, the card associations usually include a “window of exposure” — their best estimate of how long the breach lasted. Two financial industry sources said initial reports from the credit card companies said the window of exposure at B&B Theatres was between Sept. 1, 2015 and April 7, 2017.
However, a more recent update to this advisory shared by my sources shows that the window of exposure is currently estimated between April 2015 and April 2017, meaning cyber thieves have likely been siphoning credit and debit card data from B&B Theatres customers for nearly two years undisturbed. Continue reading








 The reader — Cedric (he asked to keep his last name out of this story) had grown increasingly aggravated with the calls as well, until one day he opted to play along by telling a white lie to the automated voice response system that called him: Yes, he said, yes he definitely was interested in credit repair services.
The reader — Cedric (he asked to keep his last name out of this story) had grown increasingly aggravated with the calls as well, until one day he opted to play along by telling a white lie to the automated voice response system that called him: Yes, he said, yes he definitely was interested in credit repair services.