Many readers are understandably concerned about recent moves by the U.S. Congress that would roll back privacy rules barring broadband Internet service providers (ISPs) from sharing or selling customer browsing history, among other personal data. Some are concerned enough by this development that they’re looking at obfuscating all of their online browsing by paying for a subscription to a virtual private networking (VPN) service. This piece is intended to serve as a guidepost for those contemplating such a move.
 On Tuesday, the House approved a Senate resolution to roll back data privacy regulations enacted late last year at the Federal Communications Commission (FCC) that would block ISPs from selling to advertisers information about where you go and what you do online. President Trump has signaled his intent to sign the bill (S.J. Res. 34) into law soon.
On Tuesday, the House approved a Senate resolution to roll back data privacy regulations enacted late last year at the Federal Communications Commission (FCC) that would block ISPs from selling to advertisers information about where you go and what you do online. President Trump has signaled his intent to sign the bill (S.J. Res. 34) into law soon.
As shocking as this sounds, virtually nothing has changed about the privacy of the average American’s connection to the Internet as a result of this action by Congress, except perhaps a greater awareness that ISP customers don’t really have many privacy protections by default. The FCC rules hadn’t yet gone into effect, and traditional broadband providers successfully made the case to lawmakers that the new rules put them at a competitive disadvantage vis-a-vis purely Web-based rivals such as Facebook and Google.
Nevertheless, this hasn’t stopped news outlets from breathlessly urging concerned citizens to reclaim their privacy by turning to VPN providers. And VPN providers have certainly capitalized on the news. One quite large (and savvy) VPN provider even took out a full-page ad in the New York Times listing the names of the Republican senators who voted to repeal the still-dormant regulations.
I’m happy if this issue raises the general level of public awareness about privacy and the need for Internet users everywhere to take a more active role in preserving it. And VPNs can be a useful tool for protecting one’s privacy online. However, it’s important to understand the limitations of this technology, and to take the time to research providers before entrusting them with virtually all your browsing data — and possibly even compounding your privacy woes in the process.
In case any readers are unclear on the technology, in a nutshell VPNs rely on specialized software that you download and install on your computer. Some VPN providers will supply customers with their own custom brand of VPN software, while others may simply assign customers a set user credentials and allow users to connect to the service via open-source VPN software like OpenVPN.
Either way, the software creates an encrypted tunnel between your computer and the VPN provider, effectively blocking your ISP or anyone else on the network (aside from you and the VPN provider) from being able to tell which sites you are visiting or viewing the contents of your communications. A VPN service allows a customer in, say, New York City, to tunnel his traffic through one of several servers around the world, making it appear to any Web sites that his connection is coming from those servers, not from his ISP in New York.
If you just want a VPN provider that will keep your ISP from snooping on your everyday browsing, virtually any provider can do that for you. But if you care about choosing from among VPN providers with integrity and those that provide reliable, comprehensive, trustworthy and affordable offerings, you’re going to want to do your homework before making a selection. And there are plenty of factors to consider.
For better or worse, there are hundreds of VPN providers out there today. Simply searching the Web for “VPN” and “review” is hardly the best vetting approach, as a great many VPN companies offer “affiliate” programs that pay people a commission for each new customer they help sign up. I say this not to categorically discount VPN providers that offer affiliate programs, but more as a warning that such programs can skew search engine results in favor of larger providers.
That’s because affiliate programs often create a perverse incentive for unscrupulous marketers to do things like manufacture phony VPN reviews by the virtual truckload, reviews that are aimed at steering as many people as possible to signing up with the service and earning them commissions. In my admittedly limited experience, this seems to have the effect of funneling search results toward VPN providers which spend a lot of money marketing their offerings and paying for affiliate programs.
Also, good luck figuring out who owns and operates many of these companies. Again, from the admittedly few instances in which I’ve attempted to determine exactly who or what is at the helm of a specific VPN provider, I can say that this has not been a particularly fruitful endeavor.
My bar for choosing a VPN provider has more to do with selecting one that makes an effort to ensure its customers understand how to use the service securely and safely, and to manage their customers’ expectations about the limitations of using the service. Those include VPN companies that take the time to explain seemingly esoteric but important concepts, such as DNS and IPv6 leaks, and whether they keep any logs of customer activity. I also tend to put more stock in VPN providers that offer payment mechanisms which go beyond easily-traceable methods such as credit cards or PayPal, to offering more privacy-friendly payment options like Bitcoin (or even cash).
Many VPN providers claim they keep zero records of customer activity. However, this is almost always untrue if you take the time to read the fine print. Also, some VPN services can’t truthfully make this claim because they merely resell network services offered by third-parties. Providers that are honest and up-front about what information they collect and keep and for how long carry more weight in my book.
Most VPN providers will keep basic information about their customers, including any information supplied at the creation of the account, as well as the true Internet address of the customer and the times that customers connect and disconnect from the service. I’ve found that VPN providers which collect the minimum amount of information about their customers also tend to offer little or no customer support. This isn’t necessarily a bad thing, especially if you know what you’re doing and don’t need or want a lot of hand-holding. For my part, I would avoid any VPN provider which asks for personal information that isn’t required by the form of payment I choose.
Then there are more practical, day-to-day considerations that may have little to do with privacy and anonymity. For example, some VPN providers pay a great deal of attention to privacy and security, but may not offer a huge number of servers and locations to chose from. This can present issues for people who frequently watch streaming video services that are restricted for use in specific countries. Other VPN providers may offer an impressive range of countries and/or states to chose from, but do not provide fast enough speeds to reliably satisfy data-intensive applications, such as streaming video. Continue reading →









 On Tuesday, the House approved a Senate resolution to roll back data privacy regulations enacted late last year at the Federal Communications Commission (FCC) that would block ISPs from selling to advertisers information about where you go and what you do online. President Trump has signaled his intent to sign the bill (
On Tuesday, the House approved a Senate resolution to roll back data privacy regulations enacted late last year at the Federal Communications Commission (FCC) that would block ISPs from selling to advertisers information about where you go and what you do online. President Trump has signaled his intent to sign the bill (

 Bowling Green State University in Ohio has more than 20,000 students and faculty, and like virtually any other mid-sized state school its Internet users are constantly under attack from scammers trying to phish login credentials for email and online services.
Bowling Green State University in Ohio has more than 20,000 students and faculty, and like virtually any other mid-sized state school its Internet users are constantly under attack from scammers trying to phish login credentials for email and online services.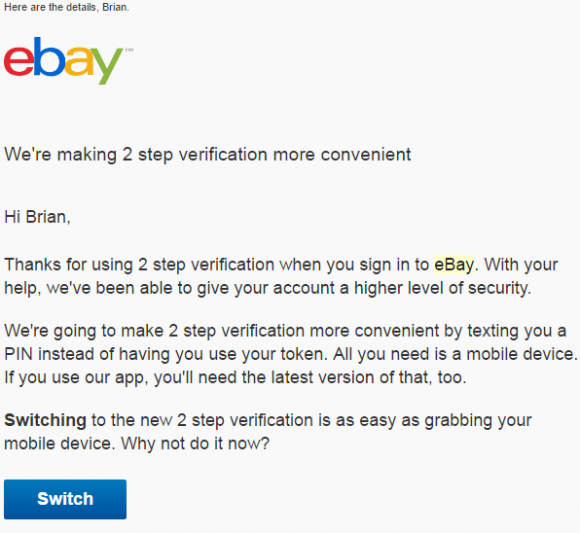 In early 2007, PayPal (then part of the same company as eBay) began offering its hardware token for a one-time $5 fee, and at the time the company was among very few that were pushing this second-factor (something you have) in addition to passwords for user authentication. In fact, I
In early 2007, PayPal (then part of the same company as eBay) began offering its hardware token for a one-time $5 fee, and at the time the company was among very few that were pushing this second-factor (something you have) in addition to passwords for user authentication. In fact, I 
 On Thursday, March 16, the CEO of Defense Point Security, LLC — a Virginia company that bills itself as “the choice provider of cyber security services to the federal government” — told all employees that their W-2 tax data was handed directly to fraudsters after someone inside the company got caught in a phisher’s net.
On Thursday, March 16, the CEO of Defense Point Security, LLC — a Virginia company that bills itself as “the choice provider of cyber security services to the federal government” — told all employees that their W-2 tax data was handed directly to fraudsters after someone inside the company got caught in a phisher’s net.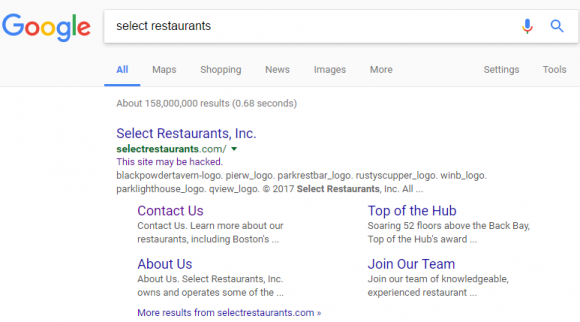

 Microsoft’s
Microsoft’s 