On September 22, 2016, this site was forced offline for nearly four days after it was hit with “Mirai,” a malware strain that enslaves poorly secured Internet of Things (IoT) devices like wireless routers and security cameras into a botnet for use in large cyberattacks. Roughly a week after that assault, the individual(s) who launched that attack — using the name “Anna-Senpai” — released the source code for Mirai, spawning dozens of copycat attack armies online.
After months of digging, KrebsOnSecurity is now confident to have uncovered Anna-Senpai’s real-life identity, and the identity of at least one co-conspirator who helped to write and modify the malware.
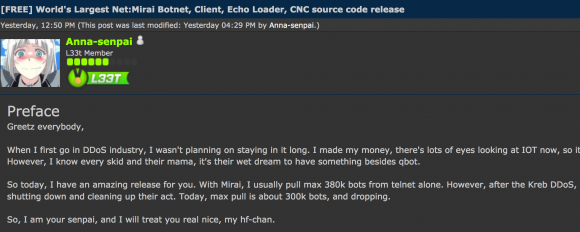
Mirai co-author Anna-Senpai leaked the source code for Mirai on Sept. 30, 2016.
Before we go further, a few disclosures are probably in order. First, this is easily the longest story I’ve ever written on this blog. It’s lengthy because I wanted to walk readers through my process of discovery, which has taken months to unravel. The details help in understanding the financial motivations behind Mirai and the botnet wars that preceded it. Also, I realize there are a great many names to keep track of as you read this post, so I’ve included a glossary.
The story you’re reading now is the result of hundreds of hours of research. At times, I was desperately seeking the missing link between seemingly unrelated people and events; sometimes I was inundated with huge amounts of information — much of it intentionally false or misleading — and left to search for kernels of truth hidden among the dross. If you’ve ever wondered why it seems that so few Internet criminals are brought to justice, I can tell you that the sheer amount of persistence and investigative resources required to piece together who’s done what to whom (and why) in the online era is tremendous.
As noted in previous KrebsOnSecurity articles, botnets like Mirai are used to knock individuals, businesses, governmental agencies, and non-profits offline on a daily basis. These so-called “distributed denial-of-service (DDoS) attacks are digital sieges in which an attacker causes thousands of hacked systems to hit a target with so much junk traffic that it falls over and remains unreachable by legitimate visitors. While DDoS attacks typically target a single Web site or Internet host, they often result in widespread collateral Internet disruption.
A great deal of DDoS activity on the Internet originates from so-called ‘booter/stresser’ services, which are essentially DDoS-for-hire services which allow even unsophisticated users to launch high-impact attacks. And as we will see, the incessant competition for profits in the blatantly illegal DDoS-for-hire industry can lead those involved down some very strange paths, indeed.
THE FIRST CLUES
The first clues to Anna-Senpai’s identity didn’t become clear until I understood that Mirai was just the latest incarnation of an IoT botnet family that has been in development and relatively broad use for nearly three years.
Earlier this summer, my site was hit with several huge attacks from a collection of hacked IoT systems compromised by a family of botnet code that served as a precursor to Mirai. The malware went by several names, including “Bashlite,” “Gafgyt,” “Qbot,” “Remaiten,” and “Torlus.”
All of these related IoT botnet varieties infect new systems in a fashion similar to other well-known Internet worms — propagating from one infected host to another. And like those earlier Internet worms, sometimes the Internet scanning these systems perform to identify other candidates for inclusion into the botnet is so aggressive that it constitutes an unintended DDoS on the very home routers, Web cameras and DVRs that the bot code is trying to subvert and recruit into the botnet. This kind of self-defeating behavior will be familiar to those who recall the original Morris Worm, NIMDA, CODE RED, Welchia, Blaster and SQL Slammer disruptions of yesteryear.
Infected IoT devices constantly scan the Web for other IoT things to compromise, wriggling into devices that are protected by little more than insecure factory-default settings and passwords. The infected devices are then forced to participate in DDoS attacks (ironically, many of the devices most commonly infected by Mirai and similar IoT worms are security cameras).
Mirai’s ancestors had so many names because each name corresponded to a variant that included new improvements over time. In 2014, a group of Internet hooligans operating under the banner “lelddos” very publicly used the code to launch large, sustained attacks that knocked many Web sites offline.
The most frequent target of the lelddos gang were Web servers used to host Minecraft, a wildly popular computer game sold by Microsoft that can be played from any device and on any Internet connection.
The object of Minecraft is to run around and build stuff, block by large pixelated block. That may sound simplistic and boring, but an impressive number of people positively adore this game – particularly pre-teen males. Microsoft has sold more than a 100 million copies of Minecraft, and at any given time there are over a million people playing it online. Players can build their own worlds, or visit a myriad other blocky realms by logging on to their favorite Minecraft server to play with friends.

Image: Minecraft.net
A large, successful Minecraft server with more than a thousand players logging on each day can easily earn the server’s owners upwards of $50,000 per month, mainly from players renting space on the server to build their Minecraft worlds, and purchasing in-game items and special abilities.
Perhaps unsurprisingly, the top-earning Minecraft servers eventually attracted the attention of ne’er-do-wells and extortionists like the lelddos gang. Lelddos would launch a huge DDoS attack against a Minecraft server, knowing that the targeted Minecraft server owner was likely losing thousands of dollars for each day his gaming channel remained offline.
Adding urgency to the ordeal, many of the targeted server’s loyal customers would soon find other Minecraft servers to patronize if they could not get their Minecraft fix at the usual online spot.
Robert Coelho is vice president of ProxyPipe, Inc., a San Francisco company that specializes in protecting Minecraft servers from attacks.
“The Minecraft industry is so competitive,” Coelho said. “If you’re a player, and your favorite Minecraft server gets knocked offline, you can switch to another server. But for the server operators, it’s all about maximizing the number of players and running a large, powerful server. The more players you can hold on the server, the more money you make. But if you go down, you start to lose Minecraft players very fast — maybe for good.”
In June 2014, ProxyPipe was hit with a 300 gigabit per second DDoS attack launched by lelddos, which had a penchant for publicly taunting its victims on Twitter just as it began launching DDoS assaults at the taunted.
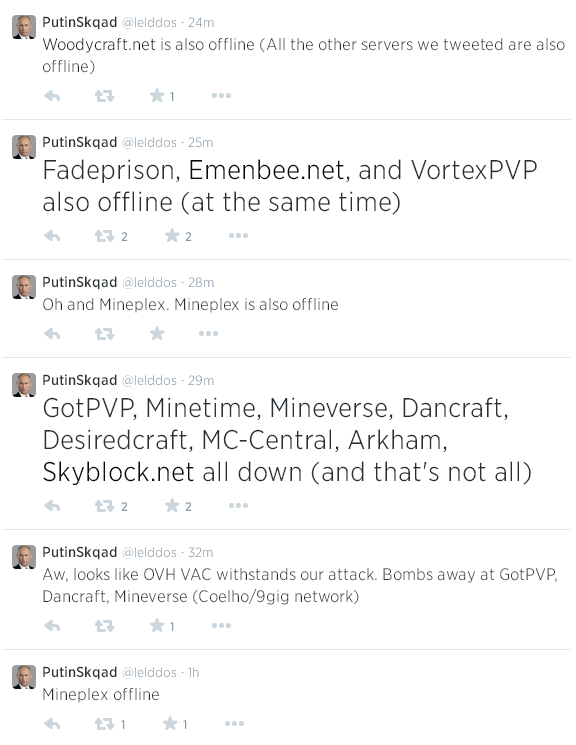
The hacker group “lelddos” tweeted at its victims before launching huge DDoS attacks against them.
At the time, ProxyPipe was buying DDoS protection from Reston, Va. -based security giant Verisign. In a quarterly report published in 2014, Verisign called the attack the largest it had ever seen, although it didn’t name ProxyPipe in the report – referring to it only as a customer in the media and entertainment business.
Verisign said the 2014 attack was launched by a botnet of more than 100,000 servers running on SuperMicro IPMI boards. Days before the huge attack on ProxyPipe, a security researcher published information about a vulnerability in the SuperMicro devices that could allow them to be remotely hacked and commandeered for these sorts of attacks.
THE CENTRALITY OF PROTRAF
Coelho recalled that in mid-2015 his company’s Minecraft customers began coming under attack from a botnet made up of IoT devices infected with Qbot. He said the attacks were directly preceded by a threat made by a then-17-year-old Christopher “CJ” Sculti, Jr., the owner and sole employee of a competing DDoS protection company called Datawagon.
Datawagon also courted Minecraft servers as customers, and its servers were hosted on Internet space claimed by yet another Minecraft-focused DDoS protection provider — ProTraf Solutions.

Christopher “CJ” Sculti, Jr.
According to Coelho, ProTraf was trying to woo many of his biggest Minecraft server customers away from ProxyPipe. Coelho said in mid-2015, Sculti reached out to him on Skype and said he was getting ready to disable Coelho’s Skype account. At the time, an exploit for a software weakness in Skype was being traded online, and this exploit could be used to remotely and instantaneously disable any Skype account.
Sure enough, Coelho recalled, his Skype account and two others used by co-workers were shut off just minutes after that threat, effectively severing a main artery of support for ProxyPipe’s customers – many of whom were accustomed to communicating with ProxyPipe via Skype.
“CJ messaged me about five minutes before the DDoS started, saying he was going to disable my skype,” Coelho said. “The scary thing about when this happens is you don’t know if your Skype account has been hacked and under control of someone else or if it just got disabled.”
Once ProxyPipe’s Skype accounts were disabled, the company’s servers were hit with a massive, constantly changing DDoS attack that disrupted ProxyPipe’s service to its Minecraft server customers. Coelho said within a few days of the attack, many of ProxyPipe’s most lucrative Minecraft servers had moved over to servers protected by ProTraf Solutions.
“In 2015, the ProTraf guys hit us offline tons, so a lot of our customers moved over to them,” Coelho said. “We told our customers that we knew [ProTraf] were the ones doing it, but some of the customers didn’t care and moved over to ProTraf anyway because they were losing money from being down.”
I found Coelho’s story fascinating because it eerily echoed the events leading up to my Sept. 2016 record 620 Gbps attack. I, too, was contacted via Skype by Sculti — on two occasions. The first was on July 7, 2015, when Sculti reached out apropos of nothing to brag about scanning the Internet for IoT devices running default usernames and passwords, saying he had uploaded some kind of program to more than a quarter-million systems that his scans found.
Here’s a snippet of that conversation:
July 7, 2015:
21:37 CJ: http://krebsonsecurity.com/2015/06/crooks-use-hacked-routers-to-aid-cyberheists/
21:37 CJ: vulnerable routers are a HUGE issue
21:37 CJ: a few months ago
21:37 CJ: I scanned the internet with a few sets of defualt logins
21:37 CJ: for telnet
21:37 CJ: and I was able to upload and execute a binary
21:38 CJ: on 250k devices
21:38 CJ: most of which were routers
21:38 Brian Krebs: o_0
The second time I heard from Sculti on Skype was Sept. 20, 2016 — the day of my 620 Gbps attack. Sculti was angry over a story I’d just published that mentioned his name, and he began rather saltily maligning the reputation of a source and friend who had helped me with that story.
Indignant on behalf of my source and annoyed at Sculti’s rant, I simply blocked his Skype account from communicating with mine and went on with my day. Just minutes after that conversation, however, my Skype account was flooded with thousands of contact requests from compromised or junk Skype accounts, making it virtually impossible to use the software for making phone calls or instant messaging.
Six hours after that Sept. 20 conversation with Sculti, the huge 620 Gbps DDoS attack commenced on this site. Continue reading →








 Microsoft’s batch includes updates for Windows, Office and Microsoft Edge (Redmond’s replacement for Internet Explorer). Also interesting is that January 2017 is the last month Microsoft plans to publish individual bulletins for each patch. From now on, some of the data points currently in the individual updates will be lumped into a “
Microsoft’s batch includes updates for Windows, Office and Microsoft Edge (Redmond’s replacement for Internet Explorer). Also interesting is that January 2017 is the last month Microsoft plans to publish individual bulletins for each patch. From now on, some of the data points currently in the individual updates will be lumped into a “
 “There are some fairly simple, immutable truths that each of us should keep in mind, truths that apply equally to political parties, organizations and corporations alike:
“There are some fairly simple, immutable truths that each of us should keep in mind, truths that apply equally to political parties, organizations and corporations alike:



 But there is another reason for my reticence: Both of these stories are so politically fraught that to write about them means signing up for gobs of vitriolic hate mail from readers who assume I have some political axe to grind no matter what I publish on the matter.
But there is another reason for my reticence: Both of these stories are so politically fraught that to write about them means signing up for gobs of vitriolic hate mail from readers who assume I have some political axe to grind no matter what I publish on the matter.
