New research suggests that an elaborate cybercrime ring is responsible for stealing between $3 million and $5 million worth of revenue from online publishers and video advertising networks each day. Experts say the scam relies on a vast network of cloaked Internet addresses, rented data centers, phony Web sites and fake users made to look like real people watching short ad segments online.
Online advertising fraud is a $7 billion a year problem, according to AdWeek. Much of this fraud comes from hacked computers and servers that are infected with malicious software which forces the computers to participate in ad fraud. Malware-based ad fraud networks are cheap to acquire and to run, but they’re also notoriously unstable and unreliable because they are constantly being discovered and cleaned up by anti-malware companies.
Now researchers say they’ve uncovered a new class of ad robot or “bot” fraud that was designed from the ground up to keep its nose clean — running not on infected hosts but instead distributed across a vast, rented network of dedicated Web servers and computers.
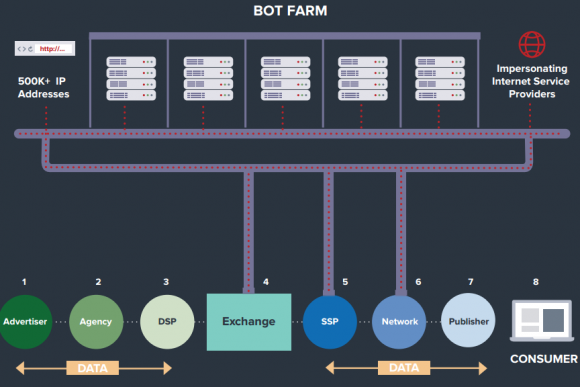
The Methbot ad fraud infrastructure. Image: White Ops.
According to White Ops, a digital advertising security company based in New York City, those rented computers are connected to a network of more than 570,000 Internet addresses apparently leased or hijacked from various sources.
White Ops dubbed the video ad fraud network “Methbot,” and says the individuals at the helm of this network are spending upwards of $200,000 a month just maintaining a fully automated fraud network that imitates real Web site publishers showing real viewers video-based advertisements.
Ryan Castellucci, principal security researcher at White Ops, said Methbot’s coders built many of the fraud network’s tools from scratch — including the Web browser that each rented computer in the network uses to mimic Web sites displaying video ads. Spoofing actual news Web sites and other popular video-rich destinations, Methbot requests video ads from ad networks, and serves the ads to a vast array of bots that “watch” the videos.
To make each Web browsing session appear more like one generated by a human, Methbot simulates cursor clicks and mouse movements, and even forges social network login information so that it appears the user who viewed the ad was logged in to a social network at the time.
“They’ve written their own browser from scratch in Javascript, and this allows them to arbitrarily control the information that gets fed back to the ad networks and to companies like us who try to detect this stuff,” Castellucci said. “This has allowed Methbot to scale to beyond anything the industry has seen before, putting it in a new class of ad fraud.”
Interestingly, the registration records for virtually all of those Internet addresses have been forged so they appear to be controlled by some of the world’s largest Internet service providers (ISPs).
For instance, one of the many Internet addresses White Ops says was used by Methbot — 196.62.126*117 — is registered in October 2015 to AT&T Services Inc., but the contact address is “adw0rd.yandex.ru@gmail.com” (the letter “o” is a zero). Adw0rd is no doubt a play on Google Adwords, an online advertising service where advertisers pay to display brief advertising copy to Web users.
Another address tied to Methbot — 196.62.3*117 — is registered to the same adw0rd.yandex.ru@gmail.com account but also to “Comcast Cable Communications, Inc.” Records for another Methbot IP — 161.8.252.* — says the address is owned by “Verizon Trademark Services LLC.”
Whoever dreamed up Methbot clearly spent a great deal of time and money building the fraud machine. For example, White Ops says the address space alone used by this ad fraud operation has a current market value of approximately $4 million. A full list of the 570,000+ Internet addresses used by Methbot is published in the White Ops report page.
“Methbot operators invested significant time, research, development, and resources to build infrastructure designed to remove these limitations and provide them with unlimited scale,” White Ops said in its report. “They created dedicated data centers to support proxy networks in order to hide the single origin source of their operation. This is the first time we’ve seen data centers impersonating residential internet connections. This makes the scale of this operation virtually unlimited, with none of the typical durability issues of maintaining a constant base of infected user machines.”
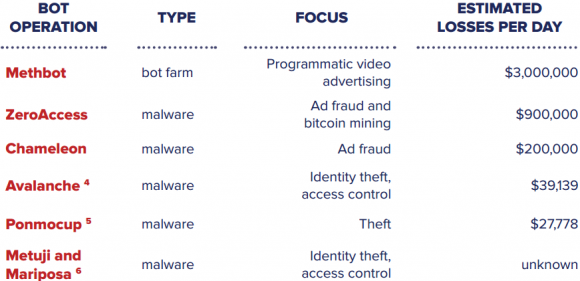
Methbot is thought to have helped steal quite a bit more ad revenue than malware-based ad bots that came before it. Source: White Ops.
White Ops said it estimated the earning potential of Methbot by looking at the number of phony video ad impressions it could serve up and the average cost to advertisers for displaying those ads. Assuming an average CPM (cost per mille, or per thousand number of impressions) of $13, the company estimates Methbot has the ability to serve between more than 300 million impressions each day, with a daily revenue ranging from $2.6 million to $5.2 million. Continue reading →






 Villain: You MUST pay the ransom!
Villain: You MUST pay the ransom!








