Last week, KrebsOnSecurity detailed how BackConnect Inc. — a company that defends victims against large-scale distributed denial-of-service (DDoS) attacks — admitted to hijacking hundreds of Internet addresses from a European Internet service provider in order to glean information about attackers who were targeting BackConnect. According to an exhaustive analysis of historic Internet records, BackConnect appears to have a history of such “hacking back” activity.
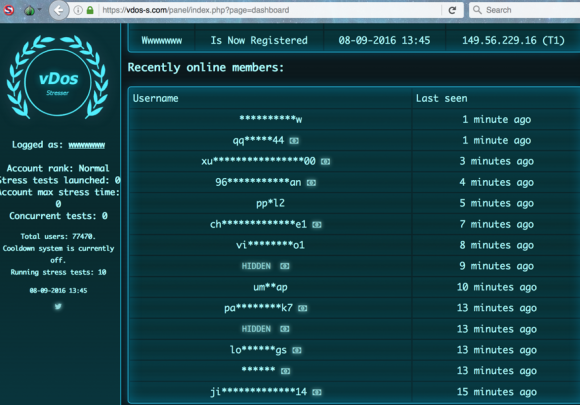
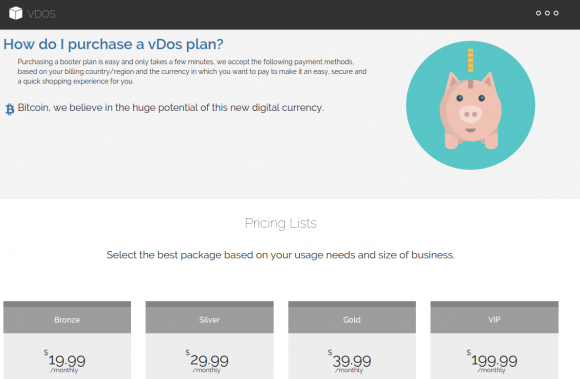
On Sept. 8, 2016, KrebsOnSecurity exposed the inner workings of vDOS, a DDoS-for-hire or “booter” service whose tens of thousands of paying customers used the service to launch attacks against hundreds of thousands of targets over the service’s four-year history in business.
Within hours of that story running, the two alleged owners — 18-year-old Israeli men identified in the original report — were arrested in Israel in connection with an FBI investigation into the shady business, which earned well north of $600,000 for the two men.
In my follow-up report on their arrests, I noted that vDOS itself had gone offline, and that automated Twitter feeds which report on large-scale changes to the global Internet routing tables observed that vDOS’s provider — a Bulgarian host named Verdina[dot]net — had been briefly relieved of control over 255 Internet addresses (including those assigned to vDOS) as the direct result of an unusual counterattack by BackConnect.
Asked about the reason for the counterattack, BackConnect CEO Bryant Townsend confirmed to this author that it had executed what’s known as a “BGP hijack.” In short, the company had fraudulently “announced” to the rest of the world’s Internet service providers (ISPs) that it was the rightful owner of the range of those 255 Internet addresses at Verdina occupied by vDOS.
In a post on NANOG Sept. 13, BackConnect’s Townsend said his company took the extreme measure after coming under a sustained DDoS attack thought to have been launched by a botnet controlled by vDOS. Townsend explained that the hijack allowed his firm to “collect intelligence on the actors behind the botnet as well as identify the attack servers used by the booter service.”
Short for Border Gateway Protocol, BGP is a mechanism by which ISPs of the world share information about which providers are responsible for routing Internet traffic to specific addresses. However, like most components built into the modern Internet, BGP was never designed with security in mind, which leaves it vulnerable to exploitation by rogue actors.
BackConnect’s BGP hijack of Verdina caused quite an uproar among many Internet technologists who discuss such matters at the mailing list of the North American Network Operators Group (NANOG).
BGP hijacks are hardly unprecedented, but when they are non-consensual they are either done accidentally or are the work of cyber criminals such as spammers looking to hijack address space for use in blasting out junk email. If BackConnect’s hijacking of Verdina was an example of a DDoS mitigation firm “hacking back,” what would discourage others from doing the same, they wondered?
“Once we let providers cross the line from legal to illegal actions, we’re no better than the crooks, and the Internet will descend into lawless chaos,” wrote Mel Beckman, owner of Beckman Software Engineering and a computer networking consultant in the Los Angeles area. “BackConnect’s illicit action undoubtedly injured innocent parties, so it’s not self defense, any more than shooting wildly into a crowd to stop an attacker would be self defense.”
A HISTORY OF HIJACKS
Townsend’s explanation seemed to produce more questions than answers among the NANOG crowd (read the entire “Defensive BGP Hijacking” thread here if you dare). I grew more curious to learn whether this was a pattern for BackConnect when I started looking deeper into the history of two young men who co-founded BackConnect (more on them in a bit).
To get a better picture of BackConnect’s history, I turned to BGP hijacking expert Doug Madory, director of Internet analysis at Dyn, a cloud-based Internet performance management company. Madory pulled historic BGP records for BackConnect, and sure enough a strange pattern began to emerge.
Madory was careful to caution up front that not all BGP hijacks are malicious. Indeed, my DDoS protection provider — a company called Prolexic Communications (now owned by Akamai Technologies) — practically invented the use of BGP hijacks as a DDoS mitigation method, he said.
In such a scenario, an organization under heavy DDoS attack might approach Prolexic and ask for assistance. With the customer’s permission, Prolexic would use BGP to announce to the rest of the world’s ISPs that it was now the rightful owner of the Internet addresses under attack. This would allow Prolexic to “scrub” the customer’s incoming Web traffic to drop data packets designed to knock the customer offline — and forward the legitimate traffic on to the customer’s site.
Given that BackConnect is also a DDoS mitigation company, I asked Madory how one could reasonably tell the difference between a BGP hijack that BackConnect had launched to protect a client versus one that might have been launched for other purposes — such as surreptitiously collecting intelligence on DDoS-based botnets and their owners?
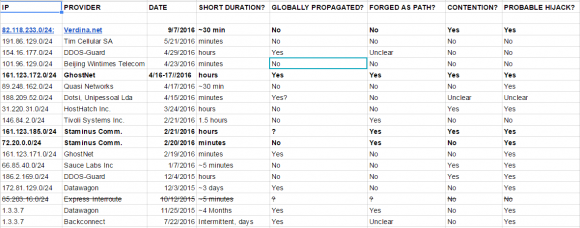
Madory explained that in evaluating whether a BGP hijack is malicious or consensual, he looks at four qualities: The duration of the hijack; whether it was announced globally or just to the target ISP’s local peers; whether the hijacker took steps to obfuscate which ISP was doing the hijacking; and whether the hijacker and hijacked agreed upon the action.
For starters, malicious BGP attacks designed to gather information about an attacking host are likely to be very brief — often lasting just a few minutes. The brevity of such hijacks makes them somewhat ineffective at mitigating large-scale DDoS attacks, which often last for hours at a time. For example, the BGP hijack that BackConnect launched against Verdina lasted a fraction of an hour, and according to the company’s CEO was launched only after the DDoS attack subsided.
Second, if the party conducting the hijack is doing so for information gathering purposes, that party may attempt to limit the number ISPs that receive the new routing instructions. This might help an uninvited BGP hijacker achieve the end result of intercepting traffic to and from the target network without informing all of the world’s ISPs simultaneously.
“If a sizable portion of the Internet’s routers do not carry a route to a DDoS mitigation provider, then they won’t be sending DDoS traffic destined for the corresponding address space to the provider’s traffic scrubbing centers, thus limiting the efficacy of any mitigation,” Madory wrote in his own blog post about our joint investigation.
Thirdly, a BGP hijacker who is trying not to draw attention to himself can “forge” the BGP records so that it appears that the hijack was performed by another party. Madory said this forgery process often fools less experienced investigators, but that ultimately it is impossible to hide the true origin of forged BGP records.
Finally, in BGP hijacks that are consensual for DDoS mitigation purposes, the host under attack stops “announcing” to the world’s ISPs that it is the rightful owner of an address block under siege at about the same time the DDoS mitigation provider begins claiming it. When we see BGP hijacks in which both parties are claiming in the BGP records to be authoritative for a given swath of Internet addresses, Madory said, it’s less likely that the BGP hijack is consensual.
Madory and KrebsOnSecurity spent several days reviewing historic records of BGP hijacks attributed to BackConnect over the past year, and at least three besides the admitted hijack against Verdina strongly suggest that the company has engaged in this type of intel-gathering activity previously. The strongest indicator of a malicious and non-consensual BGP hijack, Madory said, were the ones that included forged BGP records. Continue reading





 Half of the updates Microsoft released Tuesday earned the company’s most dire “critical” rating, meaning they could be exploited by malware or miscreants to install malicious software with no help from the user, save for maybe just visiting a hacked or booby-trapped Web site. Security firms
Half of the updates Microsoft released Tuesday earned the company’s most dire “critical” rating, meaning they could be exploited by malware or miscreants to install malicious software with no help from the user, save for maybe just visiting a hacked or booby-trapped Web site. Security firms 

 Mark Cobb, a computer technician in Reno, Nev., said had his daughter fallen for the ruse, her Gmail account would indeed have been completely compromised, and she really would have been locked out of her account because the crooks would have changed her password straight away.
Mark Cobb, a computer technician in Reno, Nev., said had his daughter fallen for the ruse, her Gmail account would indeed have been completely compromised, and she really would have been locked out of her account because the crooks would have changed her password straight away.

