Credit card industry giant Visa on Friday issued a security alert warning companies using point-of-sale devices made by Oracle‘s MICROS retail unit to double-check the machines for malicious software or unusual network activity, and to change passwords on the devices. Visa also published a list of Internet addresses that may have been involved in the Oracle breach and are thought to be closely tied to an Eastern European organized cybercrime gang.

The Visa alert is the first substantive document that tries to help explain what malware and which malefactors might have hit Oracle — and by extension many of Oracle’s customers — since KrebsOnSecurity broke news of the breach on Aug. 8. That story cited sources close to the investigation saying hackers had broken into hundreds of servers at Oracle’s retail division, and had completely compromised Oracle’s main online support portal for MICROS customers.
MICROS is among the top three point-of-sale vendors globally. Oracle’s MICROS division sells point-of-sale systems used at more than 330,000 cash registers worldwide. When Oracle bought MICROS in 2014, the company said MICROS’s systems were deployed at some 200,000+ food and beverage outlets, 100,000+ retail sites, and more than 30,000 hotels.
In short, tens of millions of credit cards are swiped at MICROS terminals monthly, and a breach involving the theft of credentials that might have granted remote access to even just a small percentage of those systems is potentially a big and costly problem for all involved.
So far, however, most MICROS customers are left scratching their heads for answers. A frequently asked questions bulletin (PDF) Oracle also released last Monday held little useful information. Oracle issued the same cryptic response to everyone who asked for particulars about how far the breach extended. “Oracle has detected and addressed malicious code in certain legacy MICROS systems.”
Oracle also urged MICROS customers to change their passwords, and said “we also recommend that you change the password for any account that was used by a MICROS representative to access your on-premises systems.”
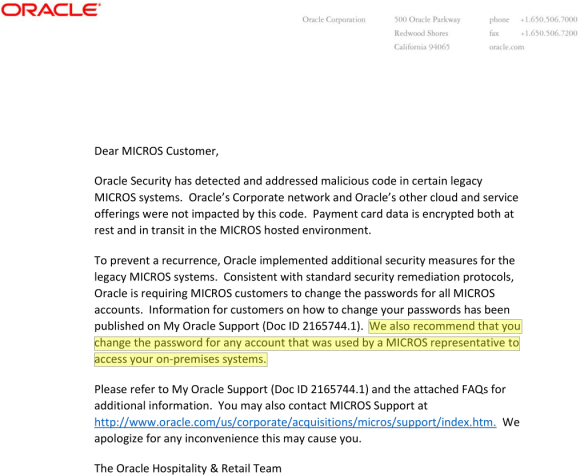
One of two documents Oracle sent to MICROS customers and the sum total of information the company has released so far about the breach.
Some technology and fraud experts, including Gartner Analyst Avivah Litan, read that statement highlighted in yellow above as an acknowledgement by Oracle that hackers may have abused credentials gained in the MICROS portal breach to plant malicious code on the point-of-sale devices run by an unknown number of MICROS customers.
“This [incident] could explain a lot about the source of some of these retail and merchant point-of-sale hacks that nobody has been able to definitively tie to any one point-of-sale services provider,” Litan told me last week. “I’d say there’s a big chance that the hackers in this case found a way to get remote access” to MICROS customers’ on-premises point-of-sale devices.”
Clearly, Visa is concerned about this possibility as well.
INDICATORS OF COMPROMISE
In my original story about the breach, I wasn’t able to reveal all the data I’d gathered about the apparent source of the attacks and attackers. A key source in that story asked that I temporarily delay publishing certain details of the investigation, specifically those known as indicators of compromise (IOCs). Basically, IOCs are list of suspect Internet addresses, domain names, filenames and other curious digital clues that are thought to connect the victim with its attacker.
I’ve been inundated all week with calls and emails from security experts asking for that very data, but sharing it wasn’t my call. That is, until yesterday (8/12/16), when Visa published a “merchant communication alert” to some customers. In that alert (PDF), Visa published IOCs that may be connected with the intrusion. These IOCs could be extremely useful to MICROS customers because the presence of Internet traffic to and from these online destinations would strongly suggest the organization’s point-of-sale systems may be similarly compromised.
Some of the addresses on this list from Visa are known to be associated with the Carbanak Gang, a group of Eastern European hackers that Russian security firm Kaspersky Lab estimates has stolen more than $1 billion from banks and retailers. Here’s the IOCs list from the alert Visa pushed out Friday:
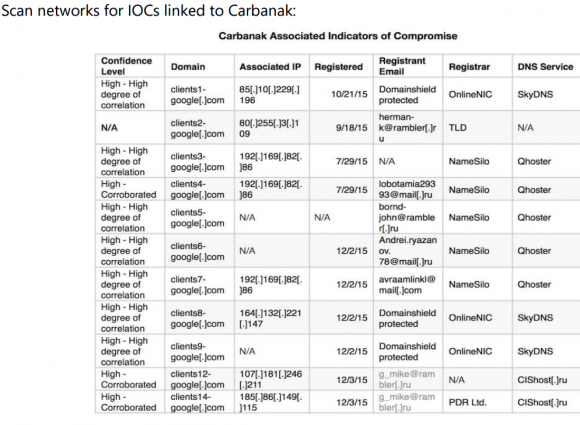
Visa warned merchants to check their systems for any communications to and from these Internet addresses and domain names associated with a Russian organized cybercrime gang called “Carbanak.”
Thankfully, since at least one of the addresses listed above (192.169.82.86) matched what’s on my source’s list, the source agreed to let me publish the entire thing. Here it is. I checked my source’s list and found at least five Internet addresses that were seen in both the Oracle attack and in a Sept. 2015 writeup about Carbanak by ESET Security, a Slovakian antivirus and security company. [NB: If you are unskilled at safely visiting malicious Web sites and/or handling malware, it’s probably best not to visit the addresses in the above-linked list.]
Visa also mentioned a specific POS-malware threat in its alert called “MalumPOS.” According to researchers at Trend Micro, MalumPOS is malware designed to target point-of-sale systems in hotels and related industries. In fact, Trend found that MalumPOS is set up to collect data specifically from point-of-sale systems running on Oracle’s MICROS platform.
It should come as no surprise then that many of Oracle’s biggest customers in the hospitality industry are starting to make noise, accusing Oracle of holding back key information that could help MICROS-based companies stop and clean up breaches involving malware and stolen customer credit card data.
“Oracle’s silence has been deafening,” said Michael Blake, chief executive officer at HTNG, a trade association for hotels and technology. “They are still grappling and trying to answer questions on the extent of the breach. Oracle has been invited to the last three [industry] calls this week and they are still going about trying to reach each customer individually and in the process of doing so they have done nothing but given the lame advice of changing passwords.”
The hospitality industry has been particularly hard hit by point-of-sale compromises over the past two years. Last month, KrebsOnSecurity broke the news of a breach at Kimpton Hotels (Kimpton appears to run MICROS products, but the company declined to answer questions for this story).
Kimpton joins a long list of hotel brands that have acknowledged card breaches over the last year, including Trump Hotels (twice), Hilton, Mandarin Oriental, and White Lodging (twice), Starwood Hotels and Hyatt. In many of those incidents, thieves had planted malicious software on the point-of-sale devices at restaurants and bars inside of the hotel chains. And, no doubt, many of those cash registers were run on MICROS systems.
If Oracle doesn’t exactly know which — if any — of its MICROS customers had malware on their point-of-sale systems as a result of the breach, it may be because the network intruders didn’t have any reason to interact with Oracle’s customers via the MICROS portal after stealing usernames and passwords that would allow them to remotely access customer on-premises systems. In theory, at that point the fraudsters could have bypassed Oracle altogether from then on. Continue reading →
 According to a notice added to the Kimpton Web site, the incident involved cards used at certain restaurants and hotel front desks from February 16, 2016 to July 7, 2016. Kimpton has posted a list of more than 60 restaurants and hotels where the company found and removed card-stealing malicious software from payment terminals.
According to a notice added to the Kimpton Web site, the incident involved cards used at certain restaurants and hotel front desks from February 16, 2016 to July 7, 2016. Kimpton has posted a list of more than 60 restaurants and hotels where the company found and removed card-stealing malicious software from payment terminals.




 On Feb. 20, 2016, James William Schwartz, 84, was going about his daily routine, which mainly consisted of caring for his wife, MaryLou. Mrs. Schwartz was suffering from the end stages of endometrial cancer and wasn’t physically mobile without assistance. When Mr. Schwartz began having a heart attack that day, MaryLou went to use her phone to call for help and discovered it was completely shut off.
On Feb. 20, 2016, James William Schwartz, 84, was going about his daily routine, which mainly consisted of caring for his wife, MaryLou. Mrs. Schwartz was suffering from the end stages of endometrial cancer and wasn’t physically mobile without assistance. When Mr. Schwartz began having a heart attack that day, MaryLou went to use her phone to call for help and discovered it was completely shut off. On July 5, 2016, KrebsOnSecurity reached out to Bellevue, Wash., based Eddie Bauer after hearing from several sources who work in fighting fraud at U.S. financial institutions. All of those sources said they’d identified a pattern of fraud on customer cards that had just one thing in common: They were all recently used at some of Eddie Bauer’s
On July 5, 2016, KrebsOnSecurity reached out to Bellevue, Wash., based Eddie Bauer after hearing from several sources who work in fighting fraud at U.S. financial institutions. All of those sources said they’d identified a pattern of fraud on customer cards that had just one thing in common: They were all recently used at some of Eddie Bauer’s