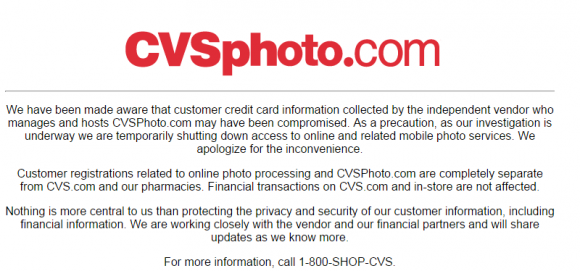
By now, many of you loyal KrebsOnSecurity readers have seen stories in the mainstream press about the coordinated global law enforcement takedown of Darkode[dot]me, an English-language cybercrime forum that served as a breeding ground for botnets, malware and just about every other form of virtual badness. This post is an attempt to distill several years’ worth of lurking on this forum into a narrative that hopefully sheds light on the individuals apprehended in this sting and the cybercrime forum scene in general.
To tell this tale completely would take a book the size of The Bible, but it’s useful to note that the history of Darkode — formerly darkode[dot]com — traces several distinct epochs that somewhat neatly track the rise and fall of the forum’s various leaders. What follows is a brief series of dossiers on those leaders, as well as a look at who these people are in real life.
ISERDO
Darkode began almost eight years ago as a pet project of Matjaz Skorjanc, a now-36-year-old Slovenian hacker best known under the hacker alisas “Iserdo.” Skorjanc was one of several individuals named in the complaints published today by the U.S. Justice Department.
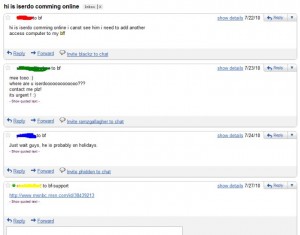
Butterfly Bot customers wonder why Iserdo isn’t responding to support requests. He was arrested hours before.
Iserdo was best known as the author of the ButterFly Bot, a plug-and-play malware strain that allowed even the most novice of would-be cybercriminals to set up a global cybercrime operation capable of harvesting data from thousands of infected PCs, and using the enslaved systems for crippling attacks on Web sites. Iserdo was arrested by Slovenian authorities in 2010. According to investigators, his ButterFly Bot kit sold for prices ranging from $500 to $2,000.
In May 2010, I wrote a story titled Accused Mariposa Botnet Operators Sought Jobs at Spanish Security Firm, which detailed how several of Skorjanc’s alleged associates actually applied for jobs at Panda Security, an antivirus and security firm based in Spain. At the time, Skorjanc and his buddies were already under the watchful eye of the Spanish police.
MAFI
Following Iserdo’s arrest, control of the forum fell to a hacker known variously as “Mafi,” “Crim” and “Synthet!c,” who according to the U.S. Justice Department is a 27-year-old Swedish man named Johan Anders Gudmunds. Mafi is accused of serving as the administrator of Darkode, and creating and selling malware that allowed hackers to build botnets. The Justice Department also alleges that Gudmunds operated his own botnet, “which at times consisted of more than 50,000 computers, and used his botnet to steal data from the users of those computers on approximately 200,000,000 occasions.”
Mafi was best known for creating the Crimepack exploit kit, a prepackaged bundle of commercial crimeware that attackers can use to booby-trap hacked Web sites with malicious software. Mafi’s stewardship over the forum coincided with the admittance of several high-profile Russian cybercriminals, including “Paunch,” an individual arrested in Russia in 2013 for selling a competing and far more popular exploit kit called Blackhole.
Paunch worked with another Darkode member named “J.P. Morgan,” who at one point maintained an $800,000 budget for buying so-called “zero-day vulnerabilities,” critical flaws in widely-used commercial software like Flash and Java that could be used to deploy malicious software.
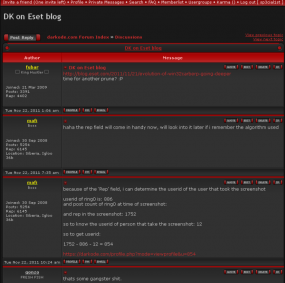
Darkode admin “Mafi” explains his watermarking system.
Perhaps unsurprisingly, Mafi’s reign as administrator of Darkode coincided with the massive infiltration of the forum by a number of undercover law enforcement investigators, as well as several freelance security researchers (including this author).
As a result, Mafi spent much of his time devising new ways to discover which user accounts on Darkode were those used by informants, feds and researchers, and which were “legitimate” cybercriminals looking to ply their wares.
For example, in mid-2013 Mafi and his associates cooked up a scheme to create a fake sales thread for a zero-day vulnerability — all in a bid to uncover which forum participants were researchers or feds who might be lurking on the forum.
That plan, which relied on a clever watermarking scheme designed to “out” any forum members who posted screen shots of the forum online, worked well but also gave investigators key clues about the forum’s hierarchy and reporting structure.

Mafi worked closely with another prominent Darkode member nicknamed “Fubar,” and together the two of them advertised sales of a botnet crimeware package called Ngrbot (according to Mafi’s private messages on the forum, this was short for “Niggerbot.” The password databases from several of Mafi’s accounts on hacked cybercrime forums included variations on the word “nigger” in some form). Mafi also advertised the sale of botnets based on “Grum” a spam botnet whose source code was leaked in 2013. Continue reading →
 The lawsuit comes just days after a judge in New Hampshire handed down a 13-year jail sentence against Hieu Minh Ngo, a 25-year-old Vietnamese man who ran an ID theft service variously named Superget.info and findget.me.
The lawsuit comes just days after a judge in New Hampshire handed down a 13-year jail sentence against Hieu Minh Ngo, a 25-year-old Vietnamese man who ran an ID theft service variously named Superget.info and findget.me.