I spent four days last week in Mexico, tracking the damage wrought by an organized crime ring that is bribing ATM technicians to place Bluetooth skimmers inside of cash machines in and around the tourist areas of Cancun. Today’s piece chronicles the work of this gang in coastal regions farther south, following a trail of hacked ATMs from Playa Del Camen down to the ancient Mayan ruins in Tulum.
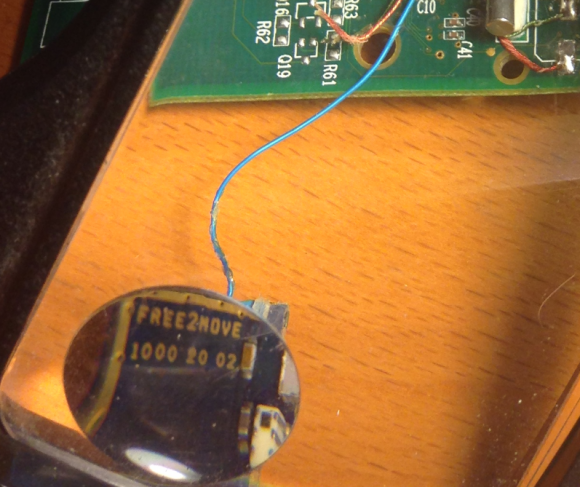
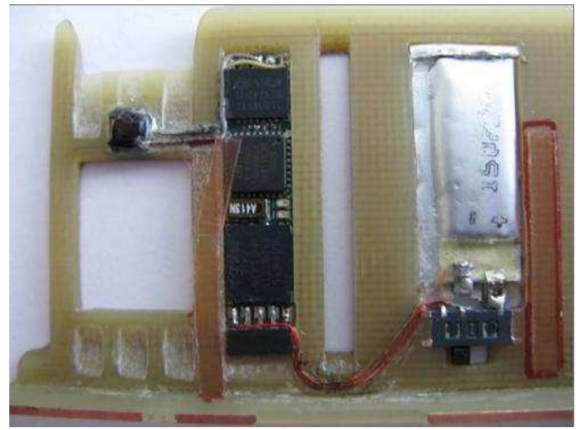
As I noted in yesterday’s story, the skimmers that this gang is placing in hacked ATMs consist of two Bluetooth components: One connected to the card reader inside each machine, and another attached to the PIN pad. Both components beacon out a Bluetooth signal called “Free2Move.” The thieves can retrieve the purloined card and PIN data just by strolling up to the hacked ATM with a smartphone, entering a secret passcode, and downloading all of the collected information.
Having found two hacked ATMs in Cancun — including one in the lobby of my hotel (the Marriott CasaMagna) — I decided to check out other tourist destinations in the region. On the way to Tulum, I dropped in at the Barcelo, a huge, all-inclusive resort. The security guards at the front gate at the resort initially prevented me from entering the complex because I didn’t have reservations.
After 10 minutes of Googling on my phone and a call to the front desk, the guards seemed satisfied that I was interested in buying a day pass to the hotel’s various facilities. The gate lifted and I was let in. Five minutes later, the very first ATM I stopped at was found to be emanating the telltale Free2Move Bluetooth signals indicating a compromise.
No sooner had I finished documenting that hacked ATM than a security guard rode up on a motorcycle and asked if I was having trouble finding the day-pass desk. I replied that I’d be headed that way shortly.
The Barcelo security guard followed me closely as I returned to my rented Jetta and drove to a different building in the complex. Multiple security guards were beginning to shadow me at a respectful distance. I decided it was best to at least demonstrate that I had an intention of buying a day pass.
The Barcelo reception desk said the price would be USD $80 per person. Feigning shock over the hefty price tag, I declared loudly that I had to hit the hotel’s ATM to withdraw more cash in order to pay such exorbitant prices. That ATM also was beaconing the Free2Move Bluetooth signal, but the ATM itself returned errors stating that it was temporarily offline and unable to dispense cash.
That outage turned out to be the perfect excuse to visit a third ATM in the complex, as I again loudly explained to the security guy following a few paces behind. By this point, a much more stern and beefy guard began following me around on foot, his walkie-talkie buzzing periodically as I crossed the hotel campus. The third and final ATM I checked also was compromised. While I was sure there were more ATMs I hadn’t checked in other areas of the resort, I decided not to press my luck, and hopped back in the Jetta and resumed my journey to Tulum.
TULUM
Halfway down the southbound four-lane highway from Cancun to the ancient ruins in Tulum, traffic inexplicably slowed to a halt. There was some sort of checkpoint ahead by the Mexican Federal Police. I began to wonder whether it was a good idea to have brought along the ATM skimmer I’d received from a source instead of leaving it in the hotel safe. If the cops searched my stuff, how could I explain having ultra-sophisticated Bluetooth ATM skimmer components in my backpack?
After several nervous minutes of creeping traffic, I was waved on through the checkpoint and immediately felt silly for having gotten so worked up about it. However, upon my arrival 20 minutes later in Tulum — a popular tourist destination due to its proximity to the Mayan ruins — I would have a much closer encounter with the police.
As I pulled into the area where tour buses normally drop off passengers by the hundreds each hour, a number of men stood waving pamphlets and offering “Cheap!” parking that was anything but (or at least I thought at the time). Each was trying to direct me to park the Volkswagen in one of several large, dusty lots.
“I’ll just be about five minutes,” I said, stupidly putting the vehicle in park on the main street right in front of the tourist lot. The attendants just shook their heads and began hailing other newcomers.
The Tulum visit yielded another three ATMs within a few hundred meters of each other that were all emanating the Free2Move signal. But unfortunately, that jaunt took more than five minutes: When I returned to the Volkswagen, I found a parking ticket on the windshield and the parking attendants smirking, gleefully shouting in Spanish that I should have listened to them and parked in their lot. Continue reading