The U.S. Internal Revenue Service (IRS) today sharply revised previous estimates on the number of citizens that had their tax data stolen since 2014 thanks to a security weakness in the IRS’s own Web site. According to the IRS, at least 724,000 citizens had their personal and tax data stolen after crooks figured out how to abuse a (now defunct) IRS Web site feature called “Get Transcript” to steal victim’s prior tax data.
 The number is more than double the figures the IRS released in August 2015, when it said some 334,000 taxpayers had their data stolen via authentication weaknesses in the agency’s Get Transcript feature.
The number is more than double the figures the IRS released in August 2015, when it said some 334,000 taxpayers had their data stolen via authentication weaknesses in the agency’s Get Transcript feature.
Turns out, those August 2015 estimates were more than tripled from May 2015, when the IRS shut down its Get Transcript feature and announced it thought crooks had abused the Get Transcript feature to pull previous year’s tax data on just 110,000 citizens.
In a statement released today, the IRS said a more comprehensive, nine-month review of the Get Transcript feature since its inception in January 2014 identified the “potential access of approximately 390,000 additional taxpayer accounts during the period from January 2014 through May 2015.”
The IRS said an additional 295,000 taxpayer transcripts were targeted but access was not successful, and that mailings notifying these taxpayers will start February 29. The agency said it also is offering free credit monitoring through Equifax for affected consumers, and placing extra scrutiny on tax returns from citizens with affected SSNs.
The criminal Get Transcript requests fuel refund fraud, which involves crooks claiming a large refund in the name of someone else and intercepting the payment. Victims usually first learn of the crime after having their returns rejected because scammers beat them to it. Even those who are not required to file a return can be victims of refund fraud, as can those who are not actually due a refund from the IRS.
As I warned in March 2015, the flawed Get Transcript function at issue required taxpayers who wished to obtain a copy of their most recent tax transcript had to provide the IRS’s site with the following information: The applicant’s name, date of birth, Social Security number and filing status. After that data was successfully supplied, the IRS used a service from credit bureau Equifax that asks four so-called “knowledge-based authentication” (KBA) questions. Anyone who succeeds in supplying the correct answers could see the applicant’s full tax transcript, including prior W2s, current W2s and more or less everything one would need to fraudulently file for a tax refund.
These KBA questions — which involve multiple choice, “out of wallet” questions such as previous address, loan amounts and dates — can be successfully enumerated with random guessing. But in practice it is far easier, as we can see from the fact that thieves were successfully able to navigate the multiple questions more than half of the times they tried. The IRS said it identified some 1.3 million attempts to abuse the Get Transcript service since its inception in January 2014; in 724,000 of those cases the thieves succeeded in answering the KBA questions correctly.
The IRS’s answer to tax refund victims — the Identity Protection (IP) PIN — is just as flawed as the now defunct Get Transcript system. These IP PINS, which the IRS has already mailed to some 2.7 million tax ID theft victims, must be supplied on the following year’s tax application before the IRS will accept the return.
The only problem with this approach is that the IRS allows IP PIN recipients to retrieve their PIN via the agency’s Web site, after supplying the answers to the same type of KBA questions from Equifax that opened the Get Transcript feature to exploitation by fraudsters. These KBA questions focus on things such as previous address, loan amounts and dates and can be successfully enumerated with random guessing. In many cases, the answers can be found by consulting free online services, such as Zillow and Facebook.
ID thieves understand this all to well, and even a relatively unsophisticated gang engaged in this activity can make millions via tax refund fraud. Last week, a federal grand jury in Oregon unsealed indictments against three men accused of using the IRS’s Get Transcript feature to obtain 1,200 taxpayers transcripts. In total, the authorities allege the men filed over 2,900 false federal tax returns seeking over $25 million in fraudulent refunds. The IRS says it rejected most of those claims, but that the gang managed to successfully obtain $4.7 million in illegal refunds.




 Stu Sjouwerman, chief executive at security awareness training company KnowBe4, told KrebsOnSecurity that earlier this week his firm’s controller received an email designed to look like it was sent by Sjouwerman requesting a copy of all employee W-2 forms for this year (full disclosure: KnowBe4 is an advertiser on this site). The email read:
Stu Sjouwerman, chief executive at security awareness training company KnowBe4, told KrebsOnSecurity that earlier this week his firm’s controller received an email designed to look like it was sent by Sjouwerman requesting a copy of all employee W-2 forms for this year (full disclosure: KnowBe4 is an advertiser on this site). The email read: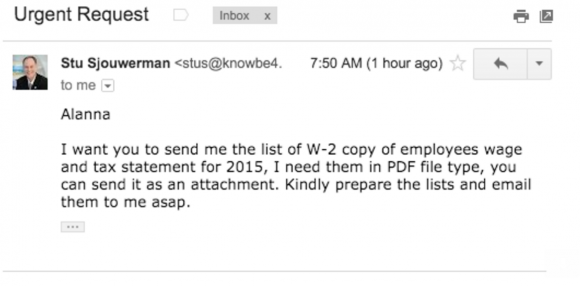



 Visa CEO Charles W. Scharf
Visa CEO Charles W. Scharf  KrebsOnSecurity reader Suzanne Perry, a self-professed “shopaholic” from Gilbert, Penn., said she recently received an email from Kohls.com stating that the email address on her account had been changed. Recognizing this as a common indicator of a compromised account, Perry said she immediately went to Kohls.com — which confirmed her fears that her password had been changed.
KrebsOnSecurity reader Suzanne Perry, a self-professed “shopaholic” from Gilbert, Penn., said she recently received an email from Kohls.com stating that the email address on her account had been changed. Recognizing this as a common indicator of a compromised account, Perry said she immediately went to Kohls.com — which confirmed her fears that her password had been changed. One
One 
