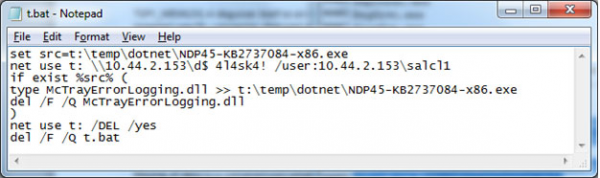
Sources in the financial industry say they’re seeing signs that Dairy Queen may be the latest retail chain to be victimized by cybercrooks bent on stealing credit and debit card data. Dairy Queen says it has no indication of a card breach at any of its thousands of locations, but the company also acknowledges that nearly all stores are franchises and that there is no established company process or requirement that franchisees communicate security issues or card breaches to Dairy Queen headquarters.
Update, Aug. 28, 12:08 p.m. ET: A spokesman for Dairy Queen has confirmed that the company recently heard from the U.S. Secret Service about “suspicious activity” related to a strain of card-stealing malware found in hundreds of other retail intrusions. Dairy Queen says it is still investigating and working with authorities, and does not yet know how many stores may be impacted.
Original story:
 I first began hearing reports of a possible card breach at Dairy Queen at least two weeks ago, but could find no corroborating signs of it — either by lurking in shadowy online “card shops” or from talking with sources in the banking industry. Over the past few days, however, I’ve heard from multiple financial institutions that say they’re dealing with a pattern of fraud on cards that were all recently used at various Dairy Queen locations in several states. There are also indications that these same cards are being sold in the cybercrime underground.
I first began hearing reports of a possible card breach at Dairy Queen at least two weeks ago, but could find no corroborating signs of it — either by lurking in shadowy online “card shops” or from talking with sources in the banking industry. Over the past few days, however, I’ve heard from multiple financial institutions that say they’re dealing with a pattern of fraud on cards that were all recently used at various Dairy Queen locations in several states. There are also indications that these same cards are being sold in the cybercrime underground.
The latest report in the trenches came from a credit union in the Midwestern United States. The person in charge of fraud prevention at this credit union reached out wanting to know if I’d heard of a breach at Dairy Queen, stating that the financial institution had detected fraud on cards that had all been recently used at a half-dozen Dairy Queen locations in and around its home state.
According to the credit union, more than 50 customers had been victimized by a blizzard of card fraud just in the past few days alone after using their credit and debit cards at Dairy Queen locations — some as far away as Florida — and the pattern of fraud suggests the DQ stores were compromised at least as far back as early June 2014.
“We’re getting slammed today,” the fraud manager said Tuesday morning of fraud activity tracing back to member cards used at various Dairy Queen locations in the past three weeks. “We’re just getting all kinds of fraud cases coming in from members having counterfeit copies of their cards being used at dollar stores and grocery stores.”
Other financial institutions contacted by this reporter have seen recent fraud on cards that were all used at Dairy Queen locations in Florida and several other states, including Alabama, Indiana, Illinois, Kentucky, Ohio, Tennessee, and Texas.
On Friday, Aug. 22, KrebsOnSecurity spoke with Dean Peters, director of communications for the Minneapolis-based fast food chain. Peters said the company had heard no reports of card fraud at individual DQ locations, but he stressed that nearly all of Dairy Queen stores were independently owned and operated. When asked whether DQ had any sort of requirement that its franchisees notify the company in the event of a security breach or problem with their card processing systems, Peters said no.
“At this time, there is no such policy,” Peters said. “We would assist them if [any franchisees] reached out to us about a breach, but so far we have not heard from any of our franchisees that they have had any kind of breach.”
Julie Conroy, research director at the advisory firm Aite Group, said nationwide companies like Dairy Queen should absolutely have breach notification policies in place for franchisees, if for no other reason than to protect the integrity of the company’s brand and public image.
“Without question this is a brand protection issue,” Conroy said. “This goes back to the eternal challenge with all small merchants. Even with companies like Dairy Queen, where the mother ship is huge, each of the individual establishments are essentially mom-and-pop stores, and a lot of these stores still don’t think they’re a target for this type of fraud. By extension, the mother ship is focused on herding a bunch of cats in the form of thousands of franchisees, and they’re not thinking that all of these stores are targets for cybercriminals and that they should have some sort of company-wide policy about it. In fact, franchised brands that have that sort of policy in place are far more the exception than the rule.”
DEJA VU ALL OVER AGAIN?
The situation apparently developing with Dairy Queen is reminiscent of similar reports last month from multiple banks about card fraud traced back to dozens of locations of Jimmy John’s, a nationwide sandwich shop chain that also is almost entirely franchisee-owned. Jimmy John’s has said it is investigating the breach claims, but so far it has not confirmed reports of card breaches at any of its 1,900+ stores nationwide.

The DHS/Secret Service advisory.
Rumblings of a card breach involving at least some fraction of Dairy Queen’s 4,500 domestic, independently-run stores come amid increasingly vocal warnings from the U.S. Department of Homeland Security and the Secret Service, which last week said that more than 1,000 American businesses had been hit by malicious software designed to steal credit card data from cash register systems.
In that alert, the agencies warned that hackers have been scanning networks for point-of-sale systems with remote access capabilities (think LogMeIn and pcAnywhere), and then installing malware on POS devices protected by weak and easily guessed passwords. The alert noted that at least seven point-of-sale vendors/providers confirmed they have had multiple clients affected.
Around the time that the Secret Service alert went out, UPS Stores, a subsidiary of the United Parcel Service, said that it scanned its systems for signs of the malware described in the alert and found security breaches that may have led to the theft of customer credit and debit data at 51 UPS franchises across the United States (about 1 percent of its 4,470 franchised center locations throughout the United States). Incidentally, the way UPS handled that breach disclosure — clearly calling out the individual stores affected — should stand as a model for other companies struggling with similar breaches. Continue reading →
 On July 21, 2014, this site broke the news that multiple banks were reporting indications that Goodwill Industries had suffered an apparent breach that led to the theft of customer credit and debit card data. Goodwill later confirmed that the breach impacted a portion of its stores, but blamed the incident on an unnamed “third-party vendor.”
On July 21, 2014, this site broke the news that multiple banks were reporting indications that Goodwill Industries had suffered an apparent breach that led to the theft of customer credit and debit card data. Goodwill later confirmed that the breach impacted a portion of its stores, but blamed the incident on an unnamed “third-party vendor.”




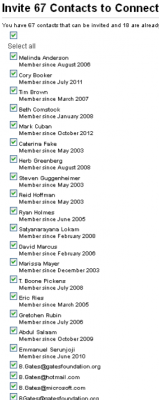


![The cybercrime shop Rescator[dot]cc pushed out nine new batches of cards from the same "American Sanctions" base of cards that banks traced back to Home Depot.](https://krebsonsecurity.com/wp-content/uploads/2014/09/AS6-12-600x558.png)