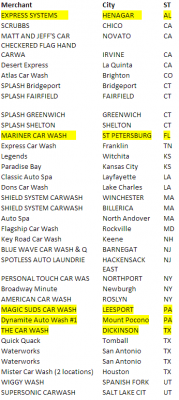
A Ukrainian man who claimed responsibility for organizing a campaign to send heroin to my home last summer has been arrested in Italy on suspicion of trafficking in stolen credit card accounts, among other things, KrebsOnSecurity.com has learned.
Last summer, appropos of nothing, an infamous cybercrook known as “Fly,” “Flycracker” and “Muxacc” began sending me profane and taunting tweets. On top of this, he posted my credit report on his blog and changed his Twitter profile picture to an image of an action figure holding up my severed head.
The only thing I knew about Fly then was that he was the founder and administrator of a closely-guarded Russian-language crime forum called thecc.bz (the “cc” part referring to credit cards). Fly also was a trusted moderator on Mazafaka, one of the most exclusive and venerable Russian carding forums online today.
Shortly after Fly began sending those nasty tweets, I secretly gained access to his forum, where I learned that he had hatched a plot to buy heroin on the Silk Road, have it shipped to my home, and then spoof a call from one of my neighbors to the local police when the drugs arrived (see Mail from the Velvet Cybercrime Underground).
Thankfully, I was able to warn the cops in advance, even track the package along with the rest of the forum members thanks to a USPS tracking link that Fly had posted into a discussion thread on his forum.
Angry that I’d foiled his plan to have me arrested for drug possession, Fly had a local florist send a gaudy floral arrangement in the shape of a giant cross to my home, complete with a menacing message that addressed my wife and was signed, “Velvet Crabs.”
After this incident, I became intensely curious about the identity of this Fly individual, so I began looking through databases of hacked carding and cybercrime forums. My first real break came when Russian computer forensics firm Group-IB provided a key piece of the puzzle (they also were quite helpful on the heroin sleuthing as well). Group-IB found that on the now-defunct vulnes[dot]com, Fly maintained an account under the nickname Flycracker, and signed up with the email address mazafaka@libero.it (.it is the country code for Italy).
According to a trusted source in the security community, that email account was somehow compromised last year. The source said the account was full of emailed reports from a keylogging device that was tied to another email address — 777flyck777@gmail.com (according to Google, mazafaka@libero.it is the recovery email address for 777flyck777@gmail.com).
Those keylog reports contained some valuable information, and indicated that Fly had planted a keylogger on his wife Irina’s computer. On several occasions, those emails show Fly’s wife typed in her Gmail address, which included her real first and last name — Irina Gumenyuk.
Later, Gumenyuk would change the surname on her various social networking profiles online to Vovnenko. She even mentioned her husband by name several times in emails to friends, identifying him as 28-year-old “Sergei Vovnenko”. Payment information contained in those emails — including shipping and other account information — put the happy couple and their young son in Naples, Italy. Continue reading