An examination of the malware used in the Target breach suggests that the attackers may have had help from a poorly secured feature built into a widely-used IT management software product that was running on the retailer’s internal network.
As I noted in Jan. 15’s story — A First Look at the Target Intrusion, Malware — the attackers were able to infect Target’s point-of-sale registers with a malware strain that stole credit and debit card data. The intruders also set up a control server within Target’s internal network that served as a central repository for data hoovered up from all of the infected registers.
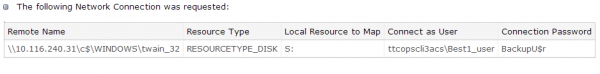
“ttcopscli3acs” is the name of the Windows share used by the POS malware planted at Target stores; the username that malware used to upload stolen card data was “Best1_user”; the password was “BackupU$r”
That analysis looked at a malware component used in Target breach that was uploaded to Symantec’s ThreatExpert scanning service on Dec. 18 but which was later deleted (a local PDF copy of it is here). The ThreatExpert writeup suggests that the malware was responsible for moving stolen data from the compromised cash registers to that shared central repository, which had the internal address of 10.116.240.31. The “ttcopscli3acs” bit is the Windows domain name used on Target’s network. The user account “Best1_user” and password “BackupU$r” were used to log in to the shared drive (indicated by the “S:” under the “Resource Type” heading in the image above.
That “Best1_user” account name seems an odd one for the attackers to have picked at random, but there is a better explanation: That username is the same one that gets installed with an IT management software suite called Performance Assurance for Microsoft Servers. This product, according to its maker — Houston, Texas base BMC Software — includes administrator-level user account called “Best1_user.”
This knowledge base article (PDF) published by BMC explains the Best1_user account is installed by the software to do routine tasks. That article states that while the Best1_user account is essentially a “system” or “administrator” level account on the host machine, customers shouldn’t concern themselves with this account because “it is not a member of any group (not even the ‘users’ group) and therefore can’t be used to login to the system.”
“The only privilege that the account is granted is the ability to run as a batch job,” the document states, indicating that it could be used to run programs if invoked from a command prompt. Here’s my favorite part:
“Perform Technical Support does not have the password to this account and this password has not be released by Perform Development. Knowing the password to the account should not be important as you cannot log into the machine using this account. The password is known internally and used internally by the Perform agent to assume the identity of the “Best1_user” account.”
I pinged BMC to find out if perhaps the password supplied in the Target malware (BackupU$r) is in fact the secret password for the Best1_user account. The company has so far remained silent on this question.
This was the hunch put forward by the Counter Threat Unit (CTU) of Dell SecureWorks in an analysis that was privately released to some of the company’s clients this week.
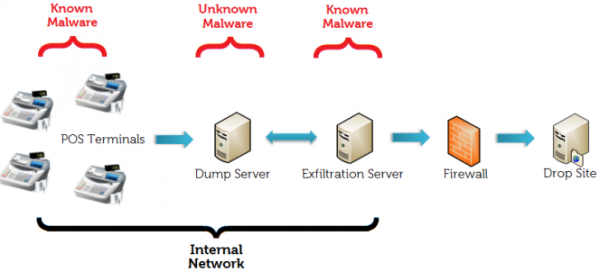
Relationships between compromised and attacker-controlled assets. Source: Dell Secureworks.
“Attackers exfiltrate data by creating a mount point for a remote file share and copying the data stored by the memory-scraping component to that share,” the SecureWorks paper notes. “In the previous listing showing the data’s move to an internal server, 10.116.240.31 is the intermediate server selected by attackers, and CTU researchers believe the “ttcopscli3acs” string is the Windows domain name used on Target’s network. The Best1_user account appears to be associated with the Performance Assurance component of BMC Software’s Patrol product. According to BMC’s documentation, this account is normally restricted, but the attackers may have usurped control to facilitate lateral movement within the network.”
According to SecureWorks, one component of the malware installed itself as a service called “BladeLogic,” a service name no doubt designed to mimic another BMC product called BMC BladeLogic Automation Suite. BMC spokeswoman Ann Duhon said that the attackers were simply invoking BMC’s trademark to make the malicious program appear legitimate to the casual observer, but it seems likely that at least some BMC software was running inside of Target’s network, and that the attackers were well aware of it.
Update Jan. 30, 5:48 p.m.: BMC just issued the following statement:
There have been several articles in the press speculating about the Target breach. BMC Software has received no information from Target or the investigators regarding the breach. In some of those articles, BMC products were mentioned in two different ways.
The first was a mention of a “bladelogic.exe” reference in the attack. The executable name “bladelogic.exe” does not exist in any piece of legitimate BMC software. McAfee has issued a security advisory stating that: “The reference to “bladelogic” is a method of obfuscation. The malware does not compromise, or integrate with, any BMC products in any way.
The second reference was to a password that was possibly utilized as part of the attack, with the implication that it was a BMC password. BMC has confirmed that the password mentioned in the press is not a BMC-generated password.
At this point, there is nothing to suggest that BMC BladeLogic or BMC Performance Assurance has a security flaw or was compromised as part of this attack.
Malware is a problem for all IT environments. BMC asks all of our customers to be diligent in ensuring that their environments are secure and protected.
I parse their statement to mean that the “BackupU$r” password referenced in the Target malware is not their software’s secret password. But nothing in the statement seems to rule out the possibility that the attackers leveraged a domain user account installed by BMC software to help exfiltrate card data from Target’s network.
Original story:
According to a trusted source who uses mostly open-source data to keep tabs on the software and hardware used in various retail environments, BMC’s software is in use at many major retail and grocery chains across the country, including Kroger, Safeway, Home Depot, Sam’s Club and The Vons Companies, among many others.
A copy of the SecureWorks report is here (PDF). It contains some fairly detailed analysis of this and other portions of the malware used in the Target intrusion. What it states up front that it does not have — and what we still have not heard from Target — is how the attackers broke in to begin with….
Continue reading →
 Earlier this month, multiple sources in the banking industry began sharing data indicating that they were seeing a pattern of fraud on hundreds of cards that were all previously used at Marriott hotels from roughly March 23, 2013 on through the end of last year. But those sames sources said they were puzzled by the pattern of fraud, because it was seen only at specific Marriott hotels, including locations in Austin, Chicago Denver, Los Angeles, Louisville and Tampa.
Earlier this month, multiple sources in the banking industry began sharing data indicating that they were seeing a pattern of fraud on hundreds of cards that were all previously used at Marriott hotels from roughly March 23, 2013 on through the end of last year. But those sames sources said they were puzzled by the pattern of fraud, because it was seen only at specific Marriott hotels, including locations in Austin, Chicago Denver, Los Angeles, Louisville and Tampa. 







![A customer's purchases from fakeplastic[dot]net, which federal authorities secretly seized on Dec. 5, 2013.](https://krebsonsecurity.com/wp-content/uploads/2014/01/FakePlastic-600x319.png)





![A private message on cpro[dot]su between Rescator and a member interested in his card shop. Notice the ad for Rescator's email flood service at the bottom.](https://krebsonsecurity.com/wp-content/uploads/2013/12/rescator-pm-cpro-600x153.png)
