A crude but effective online service that lets users deploy keystroke logging malware and then view the stolen data remotely was hacked recently. The information leaked from that service has revealed a network of several thousand Nigerian email scammers and offers a fascinating glimpse into an entire underground economy that is seldom explored.
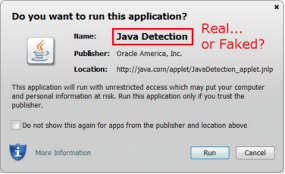
The login page for the BestRecovery online keylog service.
At issue is a service named “BestRecovery” (recently renamed PrivateRecovery). When I first became aware of this business several months ago, I had a difficult time understanding why anyone would pay the $25 to $33 per month fee to use the service, which is visually quite amateurish and kludgy (see screenshot at right).
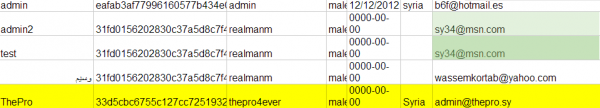
But that was before I shared a link to the site with a grey hat hacker friend, who replied in short order with the entire username and password database of more than 3,000 paying customers.
Initially, I assumed my source had unearthed the data via an SQL injection attack or some other database weakness. As it happens, the entire list of users is recoverable from the site using little more than a Web browser.
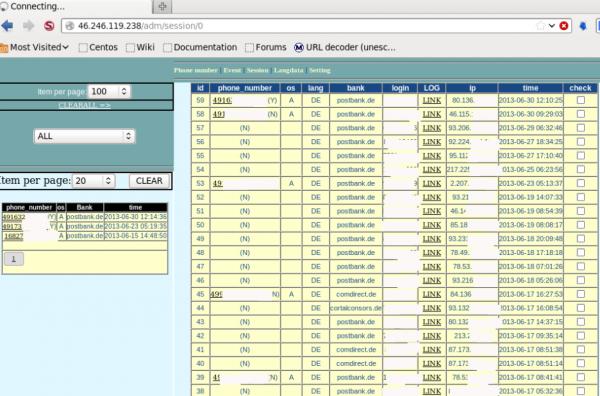
The first thing I noticed upon viewing the user list was that a majority of this service’s customers had signed up with yahoo.com emails, and appeared to have African-sounding usernames or email addresses. Also, running a simple online search for some of the user emails (dittoswiss@yahoo.com, for example) turned up complaints related to a variety of lottery, dating, reshipping and confidence scams.
The site was so poorly locked down that it also exposed the keylog records that customers kept on the service. Logs were indexed and archived each month, and most customers used the service to keep tabs on multiple computers in several countries. A closer look at the logs revealed that a huge number of the users appear to be Nigerian 419 scammers using computers with Internet addresses in Nigeria.

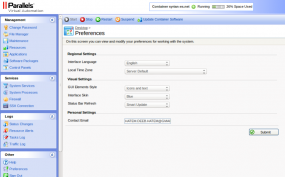
The seriously ghetto options page for BestRecovery web-based keylogger service.
Also known as “advance fee” and “Nigerian letter” scams, 419 schemes have been around for many years and are surprisingly effective at duping people. The schemes themselves violate Section 419 of the Nigerian criminal code, hence the name. Nigerian romance scammers often will troll online dating sites using stolen photos and posing as attractive U.S. or U.K. residents working in Nigeria or Ghana, asking for money to further their studies, care for sick relatives, or some such sob story.
More traditionally, these miscreants pretend to be an employee at a Nigerian bank or government institution and claim to need your help in spiriting away millions of dollars. Those who fall for the ruses are strung along and milked for increasingly large money transfers, supposedly to help cover taxes, bribes and legal fees. As the FBI notes, once the victim stops sending money, the perpetrators have been known to use the personal information and checks that they received to impersonate the victim, draining bank accounts and credit card balances. “While such an invitation impresses most law-abiding citizens as a laughable hoax, millions of dollars in losses are caused by these schemes annually,” the FBI warns. “Some victims have been lured to Nigeria, where they have been imprisoned against their will along with losing large sums of money. The Nigerian government is not sympathetic to victims of these schemes, since the victim actually conspires to remove funds from Nigeria in a manner that is contrary to Nigerian law.”
Oddly enough, a large percentage of the keylog data stored at BestRecovery indicates that many of those keylog victims are in fact Nigerian 419 scammers themselves. One explanation is that this is the result of scammer-on-scammer attacks. According to a study of 419ers published in the Dec. 2011 edition of Cyberpsychology, Behavior, and Social Networking (available from the Library of Congress here or via this site for a fee), much of the 419 activity takes place in cybercafes, where “bulk tickets are sold for sending spam emails and some systems are dedicated to fraudsters for hacking and spamming.”
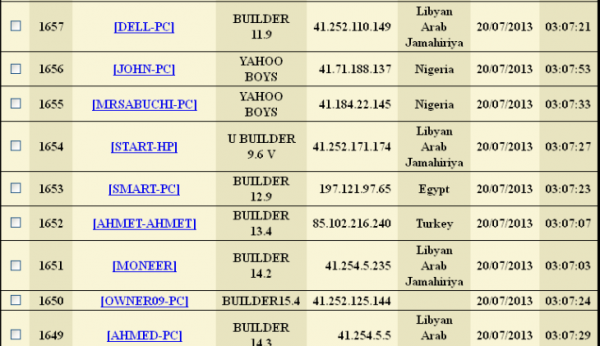
The keylog records available for the entries marked “Yahoo Boys” show that Nigerian 419 scammers were just as likely to use this service as to be targets of it.
Perhaps some enterprising Nigerian spammers simply infected a bunch of these cybercafe machines to save themselves some work. It is also possible that vigilante groups which target 419 scammers — such as Artists Against 419 and 419eater.com — were involved, although it’s difficult to believe those guys would bother with such a rudimentary service.
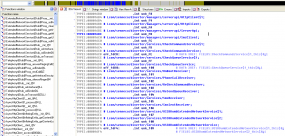
BestRecovery gives customers instructions on how to use a provided tool to create a custom Windows-based keylogger and then disguise it as a legitimate screensaver application. New victims are indexed by date, time, Internet address, country, and PC name. Each keylogger instance lets the user specify a short identifier in the “note” field (failing to manually enter an identifier in the note field appears to result in that field being populated by the version number of the keylogger used). Interestingly, many of the victim PCs have a curious notation: “Yahoo Boys”.
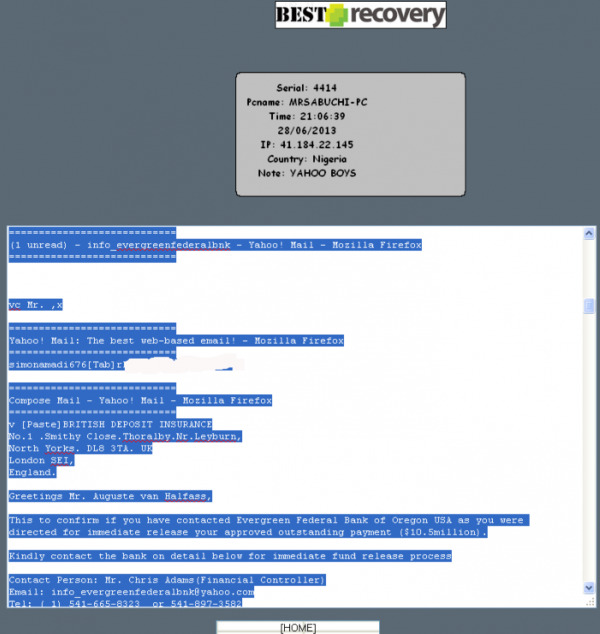
Keylog data [partially redacted] that was apparently collected from a Yahoo Boy.
As noted in the above-mentioned academic paper (“Understanding Cybercrime Perpetrators and the Strategies They Employ in Nigeria”), the term “Yahoo Boys” is the nickname given to categories of young men in Nigeria who specialize in various types of cybercrime. According to that paper, in which researchers spent time with and interviewed at least 40 active Yahoo Boys, most of the cybercrime perpetrators in Nigeria are between the age of 22 and 29, and are undergraduates who have distinct lifestyles from other youths.
“Their strategies include collaboration with security agents and bank officials, local and international networking, and the use of voodoo [emphasis added]. It was clear that most were involved in online dating and buying and selling with fake identities. The Yahoo boys usually brag, sag, do things loudly, drive flashy cars, and change cars frequently. They turn their music loud and wear expensive and latest clothes and jewelry. They also have a special way of dressing and relate, they spend lavishly, love material things, and go to clubs. They are prominent at night parties picking prostitutes at night. They also move in groups of two, three, and four when going to eateries. They speak different coded languages and use coded words such as “Mugun,” “Maga,” and “Maga don pay,” which all means “the fool (i.e., their victim) has paid.”
Continue reading →
 Four of the 13 bulletins Microsoft released today earned the company’s “critical” rating, meaning that on balance they address vulnerabilities that can be exploited by miscreants or malware to break into vulnerable systems without any help from users.
Four of the 13 bulletins Microsoft released today earned the company’s “critical” rating, meaning that on balance they address vulnerabilities that can be exploited by miscreants or malware to break into vulnerable systems without any help from users.