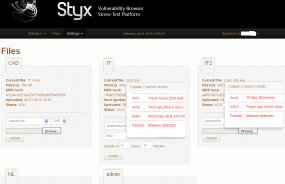
One of the challenges in malware research is separating the truly novel innovations in malcoding from new nasties that merely include nominal or superficial tweaks. This dynamic holds true for both malware researchers and purveyors, albeit for different reasons. Researchers wish to avoid being labeled alarmist in calling special attention to what appears to be an emerging threat that turns out to be old news; the bad guys just want to avoid getting scammed into paying for an old malware kit dressed up as the new next big thing.
On Tuesday, RSA Security somewhat breathlessly announced that it had spotted KINS, a ZeuS Trojan variant that looked like “a new professional-grade banking Trojan” that was likely to emerge as the “next Trojan epiphany” in the cybercrime underground. RSA said the emergence of KINS was notable because the reigning ZeuS Trojan derivative – the Citadel Trojan — had long ago been taken off the market, and that crooks were anxiously awaiting the development and sale of a new botnet creation kit based on the leaked ZeuS source code.
“Since December 2012, when the spokesperson of the Citadel team took the Trojan off the semi-open underground market, cyber criminals have been scrambling to find a replacement,” RSA’s Limor Kessem wrote. “In early February 2013, RSA fraud intelligence researchers began tracing hints about a new crimeware tool called ‘KINS’. At the time, the information about the Trojan just a rumor, but in sporadic comments, fraudsters were associating a Trojan named KINS with the Citadel source code, looking for its developer in order to reach out to him and purchase KINS. The rumors were soon hushed and ties to Citadel were denied, mostly in what appeared as a case of fearful fraudsters who did not want to be denied the possibility to buy the next Trojan.”
But according to Fox-IT, a security research and consulting group based in The Netherlands, KINS has been used in private since at least December 2011 to attack financial institutions in Europe, specifically Germany and The Netherlands. Fox-IT says KINS is short for “Kasper Internet Non-Security,” which is likely the malware author’s not-so-subtle dig at the security suite offered by Russian antivirus maker Kaspersky.
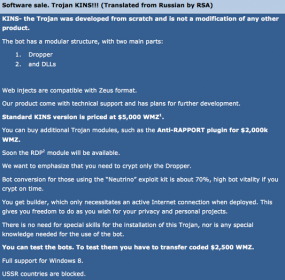
In its own analysis of the banking Trojan malware, Fox-IT said KINS is fully based on the leaked ZeuS source code, and includes only minor additions. What’s more, Fox-IT notes, many of the users of KINS have already migrated to yet another ZeuS variant, suggesting that perhaps they were unsatisfied with the product and that it didn’t deliver as advertised.
“While the technical additions are interesting, they are far from ground breaking,” wrote Michael Sandee, principal security expert at Fox-IT. “With an array of fairly standard features, and relatively simple additions to the standard ZeuS, such as reporting of installed security product information, the malware platform does not bring anything really new. There are however some features of this malware, not aimed at the functionality for the person using it, but aimed at complicating malware analysis.”
OLD MALWARE, NEW PAINTJOB?
From the bad-guy perspective, this infighting over malware innovation is on display in a new malware offering that surfaced today on a semi-private forum: The seller is pitching a resurrected and modified version of the DNSChanger Trojan, a global contagion that once infected millions of PCs. The DNSChanger botnet, which hooked into infected systems quite deeply and spread to both Windows and Mac computers, was eradicated only by a worldwide, concerted digital quarantine and vaccination effort — combined with the arrest of its creators.






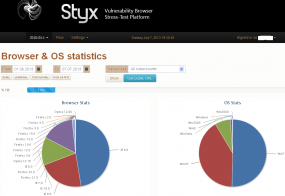
![Anonymous antivirus scanning service -- captain-checker[dot]com -- bundled with the Styx exploit pack.](https://krebsonsecurity.com/wp-content/uploads/2013/07/c-checker-285x93.png)