The U.S Federal Bureau of Investigation is warning about an uptick in online extortion scams that impersonate the FBI and frighten people into paying fines to avoid prosecution for supposedly downloading child pornography and pirated content. This post offers an inside look at one malware gang responsible for orchestrating such scams.
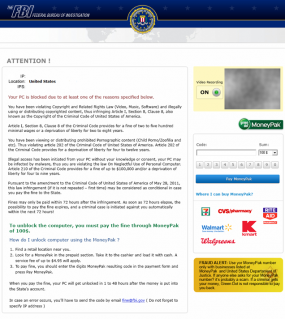
In an alert published last week, the FBI said that The Internet Crime Complaint Center — a partnership between the FBI and the National White Collar Crime Center — was “getting inundated with complaints” from consumers targeted or victimized by the scam, which uses drive-by downloads to hijack host machines. The downloaded malware displays a threatening message (see image to the right) and blocks the user from doing anything else unless he pays the fine or finds a way to remove the program.
The FBI alert said the attacks have surged with the help of a “new drive-by virus” called Reveton; in fact, Reveton and its ilk are hardly new. These types of attacks have been around for years, but traditionally have targeted European users. The scam pages used in the attacks mimic official notices from various national police or investigatory agencies, corresponding to the country in which the victim resides. For a breakdown of these Reveton-related ransomware scam pages by country, see this comprehensive gallery set up at botnets.fr.
Reveton.A is blamed in these most recent attacks, and the FBI said it appears Reveton is being distributed in conjunction with Citadel, an offshoot of the ZeuS Trojan that I have written about on several occasions. It is certainly possible that crooks are using Citadel to deploy Reveton, but as I’ll illustrate below, it seems more likely that the attackers in these cases are using exploit kits like BlackHole to plant both threats on victim PCs.
INSIDE A REVETON MALWARE GANG
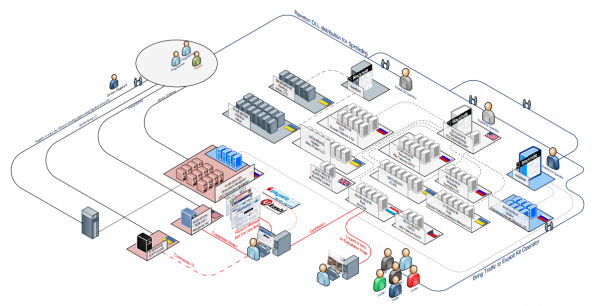
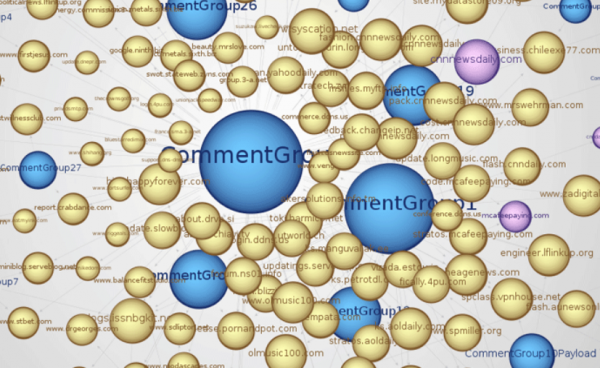
At least that’s the behavior that’s been observed by a ragtag group of researchers that has been tracking Reveton activity for many months. Some of the researchers are associated with botnets.fr, but they’ve asked to remain nameless because of the sensitivity of their work. One of them, who goes by the screen name “Kafeine,” said much of the Reveton activity traces back to a group that is controlling the operation using reverse proxies at dozens of servers scattered across data centers globally (see this PDF for a more detailed look at the image above).
Kafeine said the groups involved in spreading Reveton are constantly fine-tuning all aspects of their operations, from the scam pages to solidifying their back-end hosting infrastructure. The latest versions of Reveton, for example, serve the scam pages from an encrypted (https://) connection, and only cough up the pages when an infected machine visits and sends a special request. Continue reading