I recently wrote about an online service that was selling access to stolen credit and debit card data. That post received a lot of attention, but criminal bazaars are a dime a dozen. The real news is that few of these fraud shops are secure enough to keep their stock of stolen data from being pilfered by thieves.
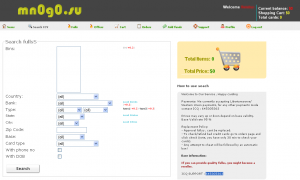
A prime example is the shop mn0g0.su (“mnogo” is a transliteration of много, which means “many” in Russian). This online store, launched in January 2011, lets customers shop for stolen card data by bank issuer, victim ZIP code, and card type. A source who enjoys ruining criminal projects said he stumbled upon mn0g0.su’s back-end database by accident; the site was backing up its cache of stolen card data to a third party server that was wide open and unencrypted.
Included in the database are more than 81,000 sets of credit and debit card numbers, along with their associated expiration dates and card security code. Each listing also includes the owner’s name, address and phone number and/or email address. The Social Security number, mother’s maiden name and date of birth are available for some cardholders. The site does not accept credit card payments; shopper accounts are funded by deposits from “virtual currencies,” such as WebMoney and LibertyReserve.
It’s not clear how or when these card numbers were stolen. Fraudulent card shops purchase data in bulk from multiple suppliers, most likely from small-time fraudsters who use automated tools to hack e-commerce stores. The data is inserted into the database in varying formats. For example, one batch of card information for sale includes email addresses in lieu of phone numbers, and all of the victim cardholders from that batch have physical addresses in the United Kingdom.
Just for amusement, I searched for my last name, and was surprised to find four people with the last name “Krebs” whose card information was included in the database (none are known relatives).
Not only did mn0g0.su leak all of the credit and debit cards it had for sale, but it also spilled its own “customer” list: The email addresses, IP addresses, ICQ numbers, usernames and passwords of more than 4,300 mn0g0.su shoppers were included in the exposed database backup. The customer passwords were better protected than the credit card numbers. The passwords are encrypted with a salted SHA256 hash, although a decent set of password-cracking tools could probably decipher 50-75 percent of the hashed passwords if given enough time.